In fact, I had friends in university from Greece, but, yeah, languages, dialects and accents are a hobby.
No, just a Moderator, not an Administrator.
Saving authentication server definitions before testing is another one of those tricks that isn't documented. I hadn't noticed that the SSL option was added, but all of my clients use internal servers or connect to them via encrypted tunnels (RED/IPsec/SSL VPN). You might try creating a new server definition instead of changing from 389 to SSL 636 in an existing definition - did that work?
See #6 in Rulz for guidance on when users should be synced from the authentication server to the UTM. Configuring HTTP/S proxy access with AD SSO also applies to LDAP in most places. I think Douglas has a thread somewhere that delves more deeply into LDAP.
Cheers - Bob
Hi Bob,
then I guess we have the same hobby...
So, I created a "sophos" group and a "sophosuser" in freeipa.
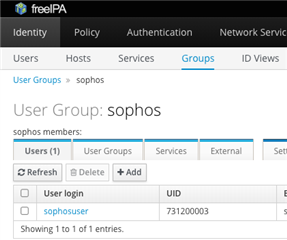
This user authenticates successfully under /authentication services/server/user authentication test
But when I try to log in to the firewall WebAdmin with this user I can't log in.
I have the feeling that I am missing something big here, so big that I can't see it :)
This is how ldap group in the firewall looks like: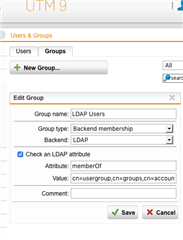
Should I create another group in the firewall? If yes, then how would that look like? The already existing "local" users would they be double then?
Thanx