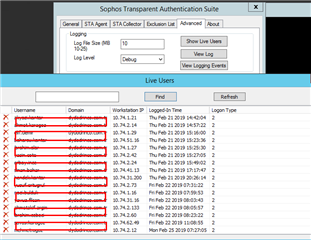
Hi,
I am having very interesting problem. I have setup web filtering with active directory group and members of these groups can go to internet. I also set block action for the others who are not member of these groups. Some of my users which are members of these groups, blocked and when i checked the logs, i have found out that there is no user information for this users but only computer$ account. Those users are blocked and cannot use the internet now because of the block action.
I didnt set any proxy to my client yet. I have checked couple of article and i couldnt find anything regarding to this either. When I set proxy on a client it comes with right information but otherwise keeps coming with computer$ account.
Has anyone ever struggle with this?
Regards,
This thread was automatically locked due to age.