Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
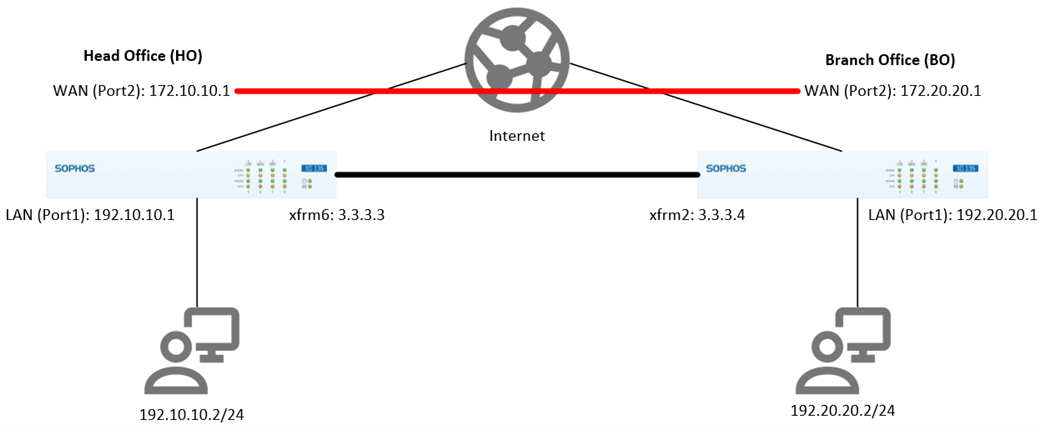
This article describes configuring OSPF (Open Shortest Path First) routing over a Route-Based VPN (RBVPN) tunnel using the Sophos Firewall with SFOS version 18 and above. This procedure will work between two Sophos Firewall devices and a third-party network device if it supports RBVPN.
Note: This article does not provide in-depth information regarding OSPF, RBVPN, or firewall technologies.
Table of Contents
This applies to the following Sophos products and versions
Sophos Firewall version 18 and above
Scenario
Establish OSPF routing via RBVPN tunnel between the Head Office (HO) and the Branch Office (BO).
Head Office (HO) configuration
The configurations provided here are just an example. You can configure it according to your organization's networks and requirements.
Configure the RBVPN tunnel.
- Go to VPN > IPsec connections. Under the IPsec Connections section, click Add and configure the RBVPN connection, as shown below.
The Listening interface is the HO's WAN IP, and the Gateway address is the BO's WAN IP.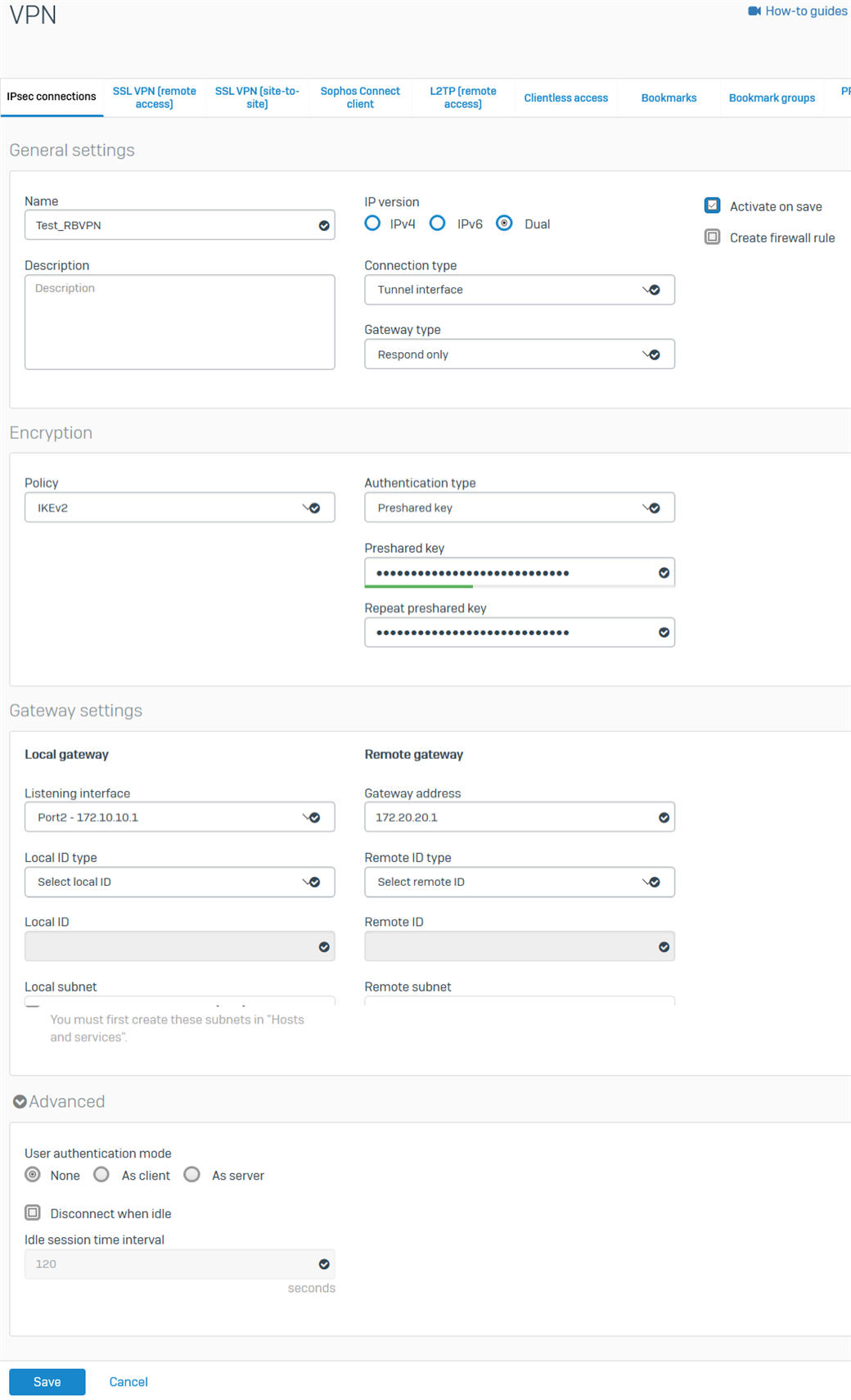
- Click Save. The RBVPN will be automatically activated and create an interface named xfrm followed by a number.
- Go to Network > Interfaces and click the xfrm interface that was created. In this example, it’s xfrm6.
- Enter the virtual IP address for this interface and then click Save.
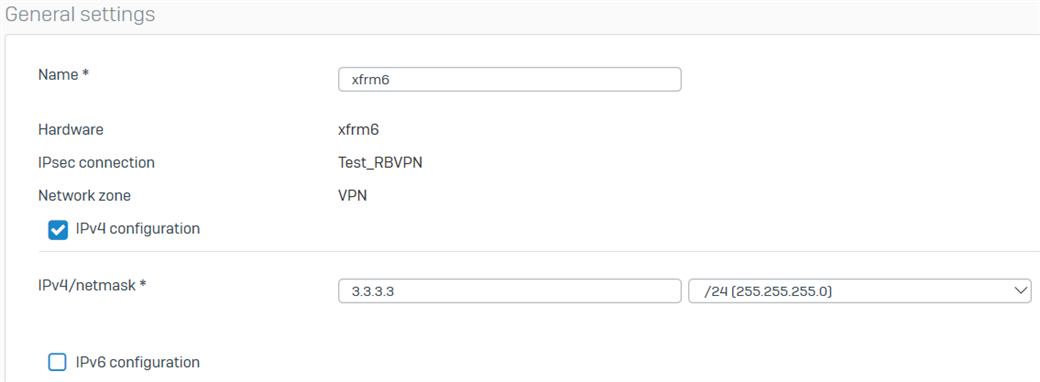
Configure the firewall rules
- Go to Rules and Policies> Firewall rules > Add firewall rule > New firewall rule. Configure the inbound firewall rule as shown below.
For the Source networks and devices and Destination networks, enter the BO's LAN networks and the HO's LAN networks, respectively. You can also create host definitions by clicking Add new item.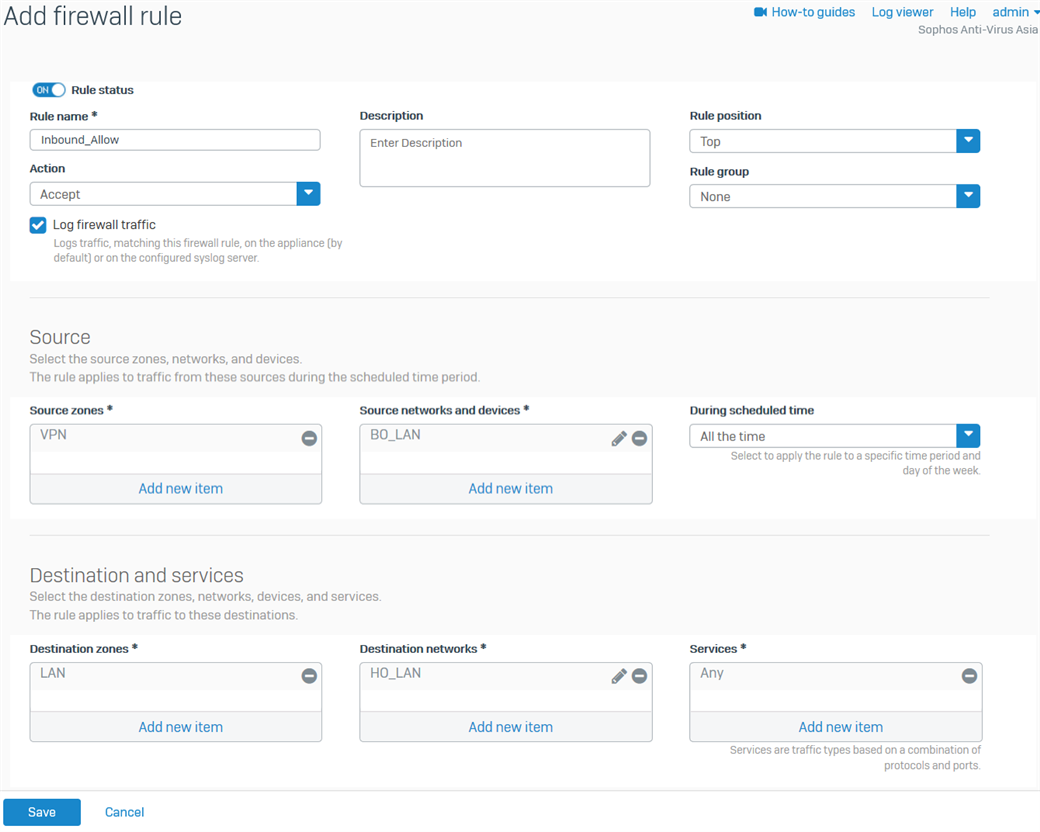
- Click Save.
- Create another firewall rule for the outbound traffic, as shown below.
For the Source networks and devices and Destination networks, enter the HO's LAN networks and the BO's LAN networks, respectively. You can also create host definitions by clicking Add new item.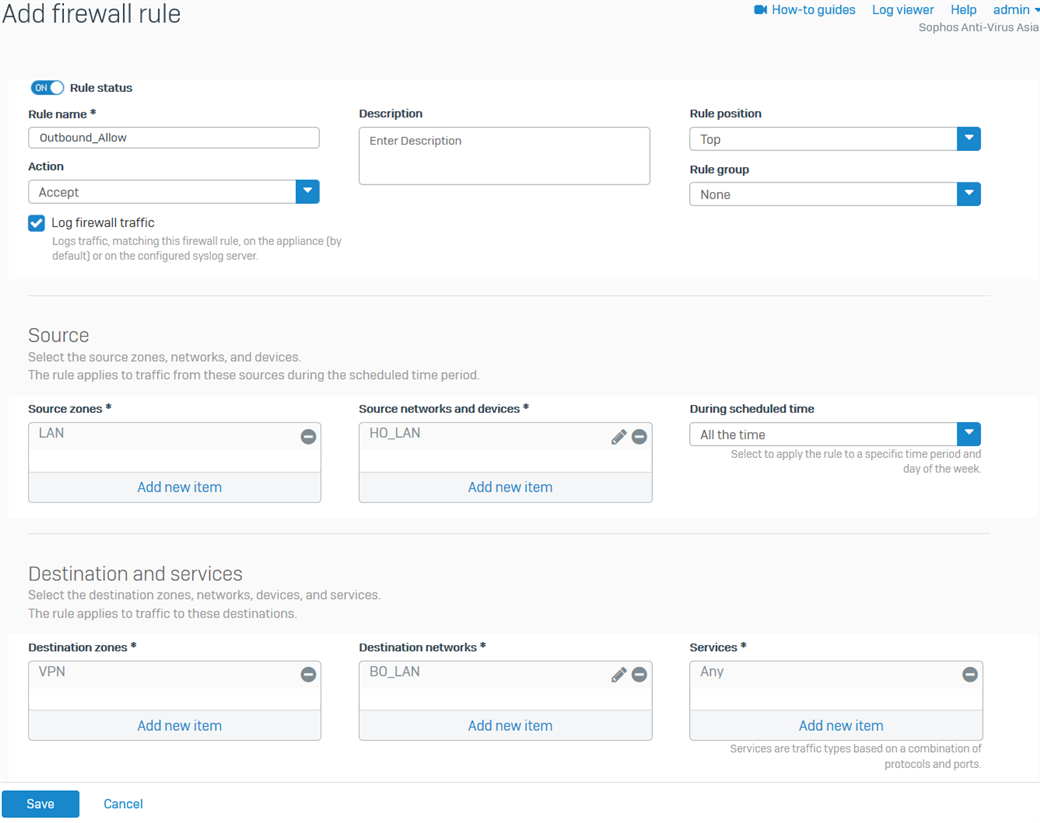
- Click Save.
Configure OSPF
- Go to Routing > OSPF. Enter the HO's WAN IP as the Router ID, click Apply, and click OK when prompted.
- Under the Networks & areas section, in the Networks field, click Add. Enter the xfrm interface's network and the HO's LAN as shown in the table below, and then click Save for each. This will allow these interfaces/networks to participate in the OSPF process.
Parameter Value IPv4/netmask 3.3.3.0/24 Area 0.0.0.0 Parameter Value IPv4/netmask 192.10.10.0/24 Area 0.0.0.0 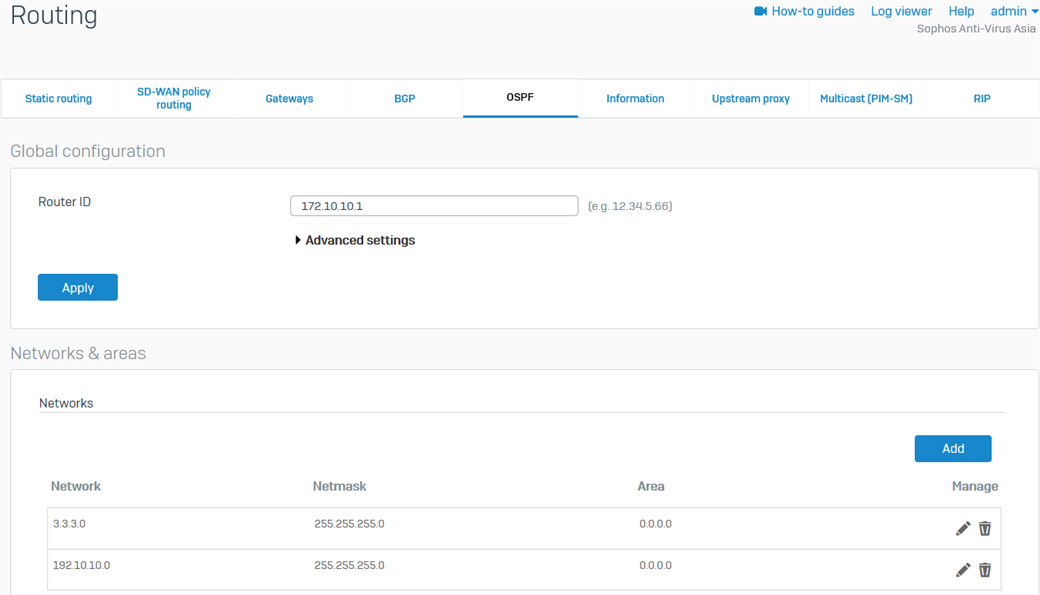
Configure the device access.
- Go to Administration > Device access and enable Ping/Ping6 and Dynamic Routing for the VPN Zone.
- Click Apply.
Branch Office (BO) configuration
Configure the RBVPN tunnel
- Go to VPN > IPsec connections. Under the IPsec Connections section, click Add and configure the RBVPN connection as shown below.
The Listening interface is the BO's WAN IP and the Gateway address is the HO's WAN IP.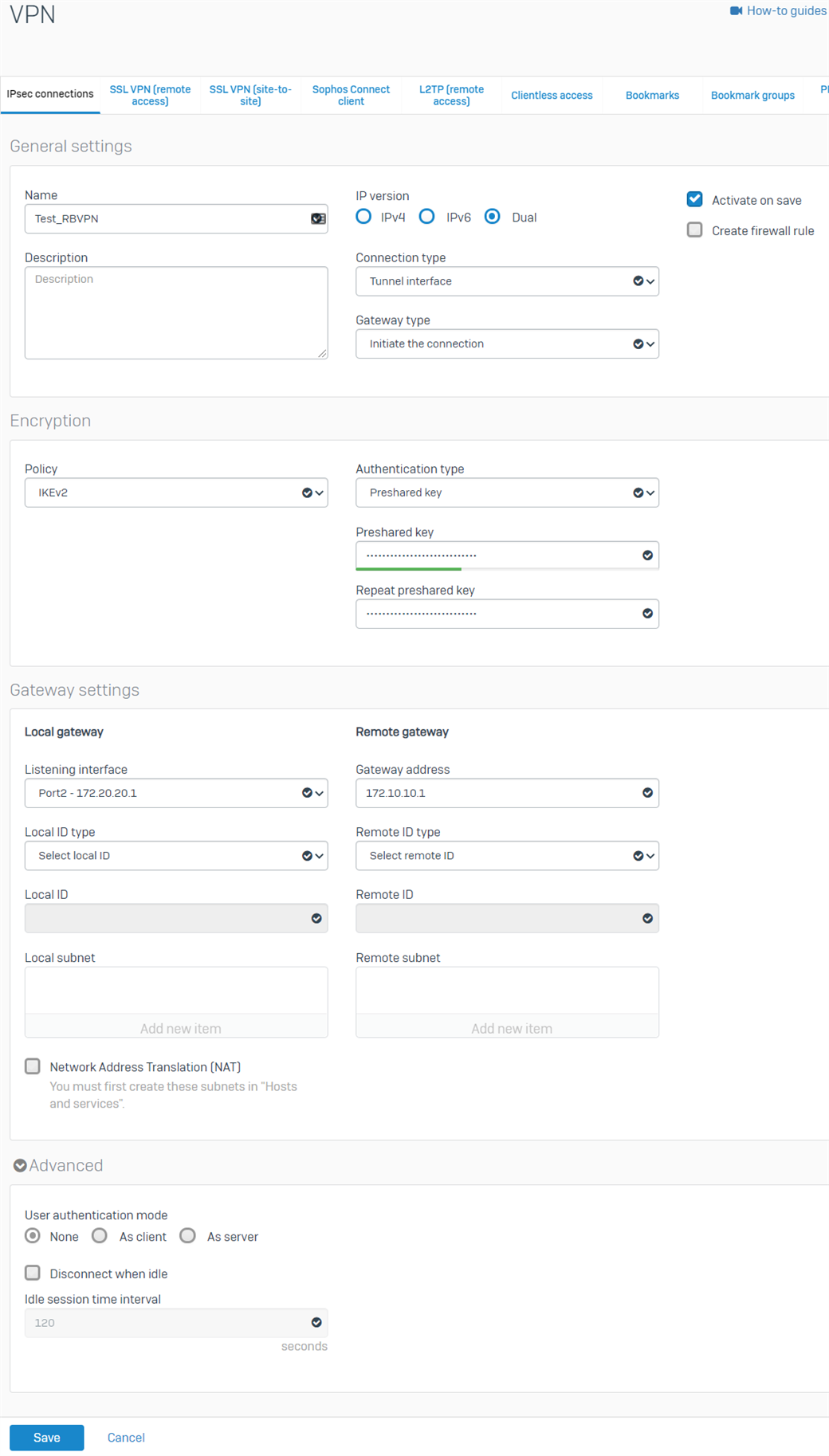
- Click Save. The RBVPN will be automatically activated and create an interface named xfrm followed by a number.
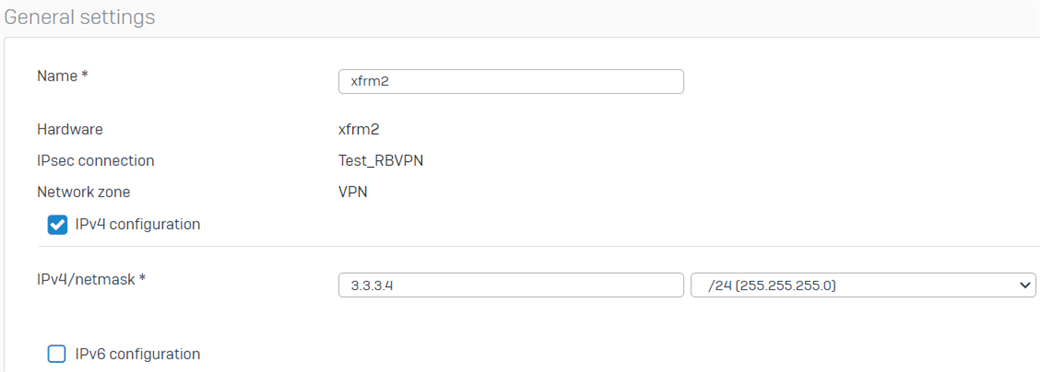
- Go to Network > Interfaces and click the xfrm interface that was created. In this example, it is xfrm2.
- Enter the virtual IP address for this interface and then click Save.
Configure the firewall rules.
- Go to Rules and Policies> Firewall rules > Add firewall rule > New firewall rule. Configure the inbound firewall rule as shown below.
For the Source networks and devices and Destination networks, enter the HO's LAN networks and the BO's LAN networks, respectively. You can also create host definitions by clicking Add new item.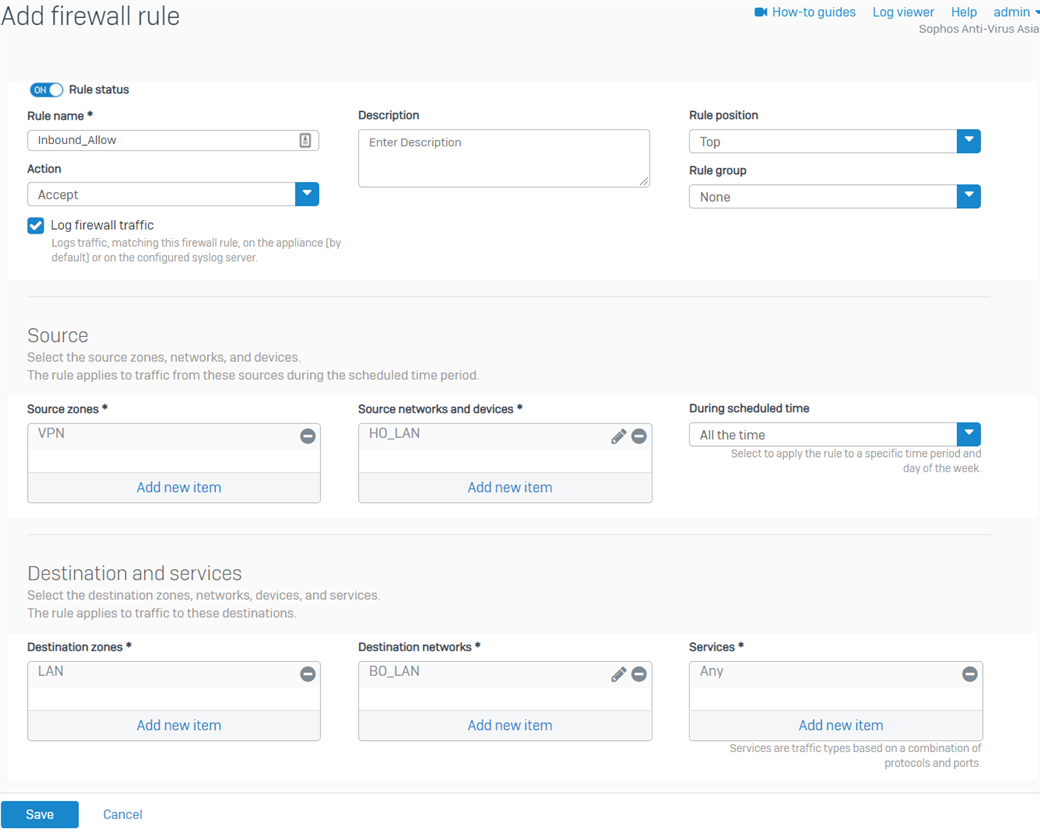
- Click Save.
- Create another firewall rule for the outbound traffic, as shown below.
For the Source networks and devices and Destination networks, enter the BO's LAN networks and the HO's LAN networks, respectively. You can also create host definitions by clicking Add new item.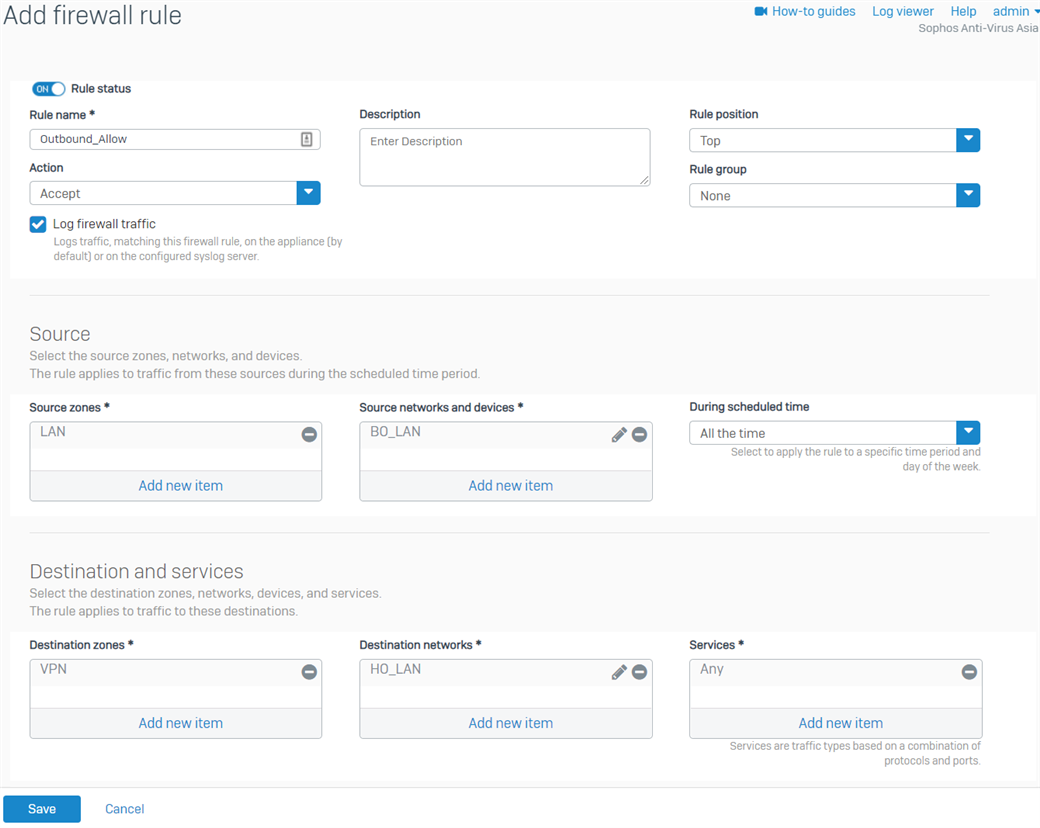
- Click Save.
Configure OSPF
- Go to Routing > OSPF. Enter the BO's WAN IP as the Router ID, click Apply, and then click OK when prompted.
- Under the Networks & areas section, in the Networks field, click Add. Enter the xfrm interface's network and the BO's LAN as shown in the table below and then click Save for each. This will allow these interfaces/networks to participate in the OSPF process.
Parameter Value IPv4/netmask 3.3.3.0/24 Area 0.0.0.0 Parameter Value IPv4/netmask 192.20.20.0/24 Area 0.0.0.0 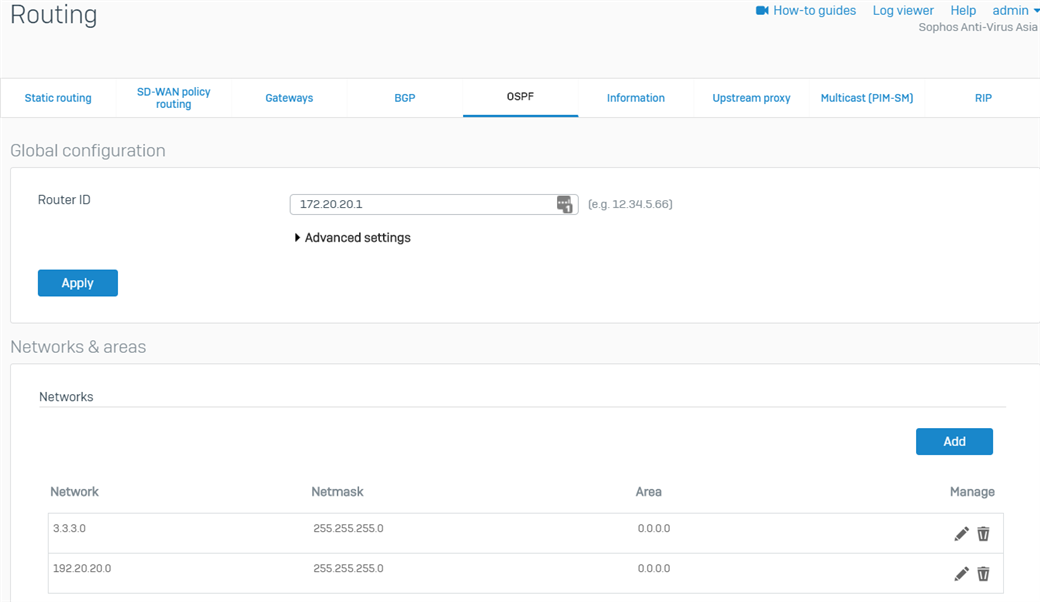
Configure the device access.
- Go to Administration > Device access and enable Ping/Ping6 and Dynamic Routing for the VPN Zone.
- Click Apply.
Verification
RBVPN
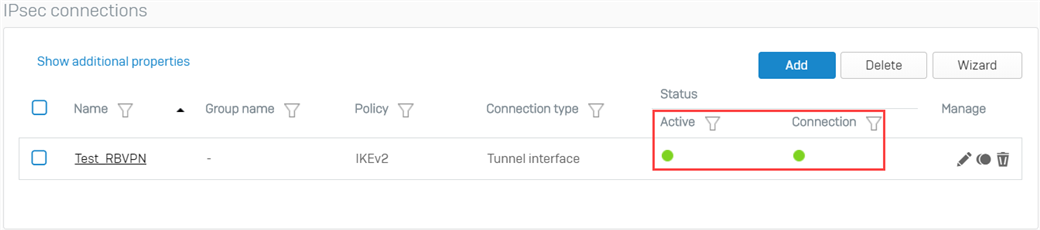
- In the BO Sophos Firewall, go to VPN > IPsec connections and enable the created tunnel by clicking the red button under the Connection column. It should turn green, meaning that the RBVPN tunnel has been established.
OSPF
- Sign in to the CLI of the HO Sophos Firewall as an administrator.
- Select 3. Route Configuration > 1. Configure Unicast Routing > 2. Configure OSPF.
- Enter the following commands:
enable
show ip ospf interface <xfrm interface>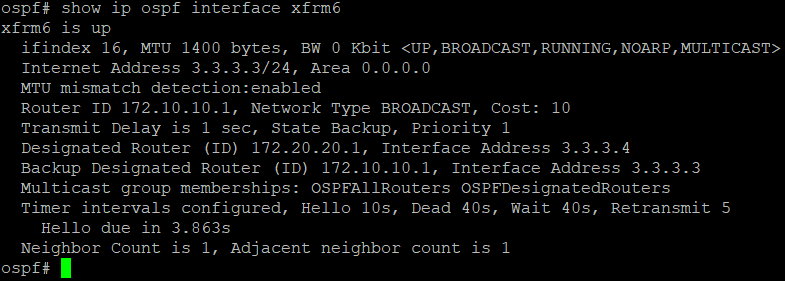
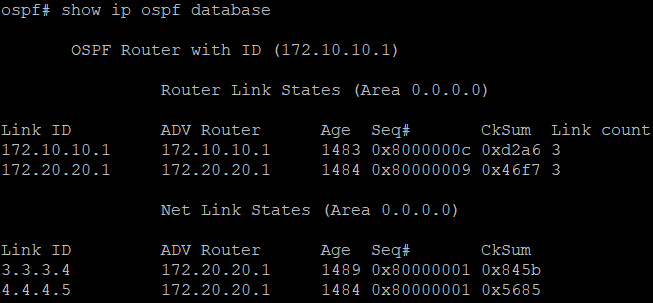
show ip ospf database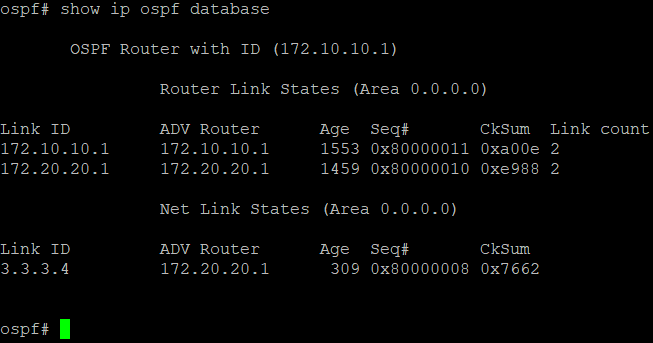
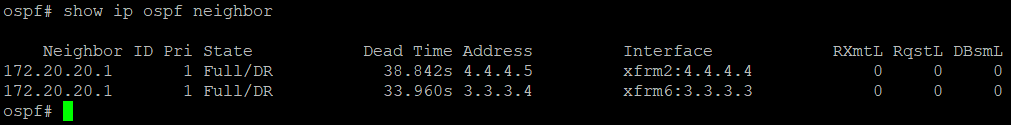
show ip ospf neighbor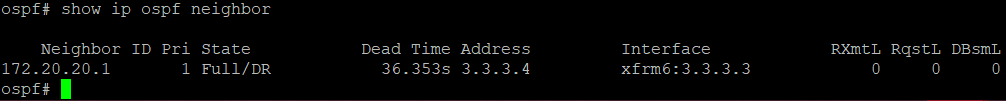
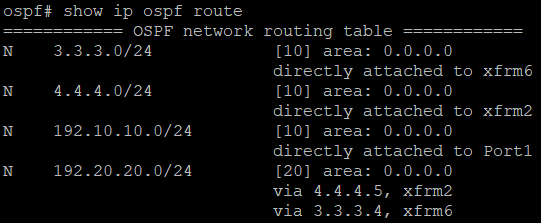
show ip ospf route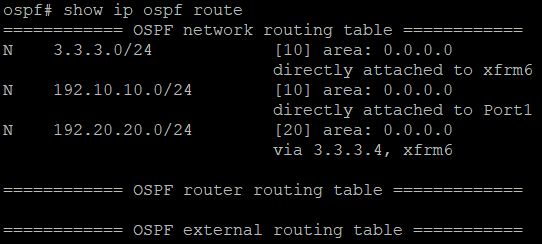
- Go to 5. Device Management > 3. Advanced Shell.
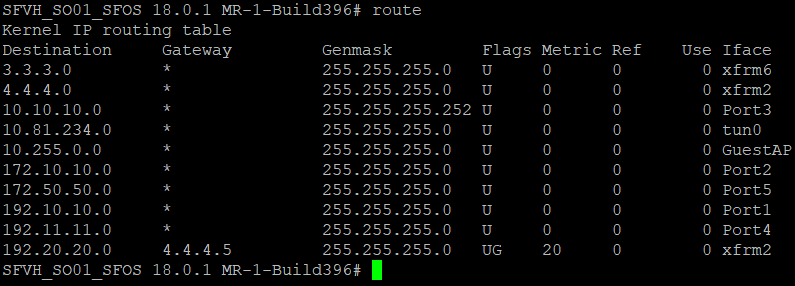
- Enter the following command to see that the routes have been advertised.
route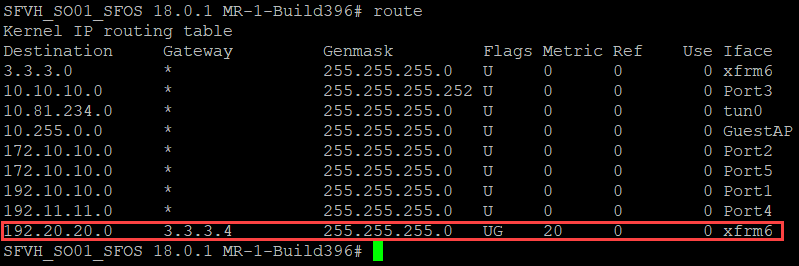
Traffic flow
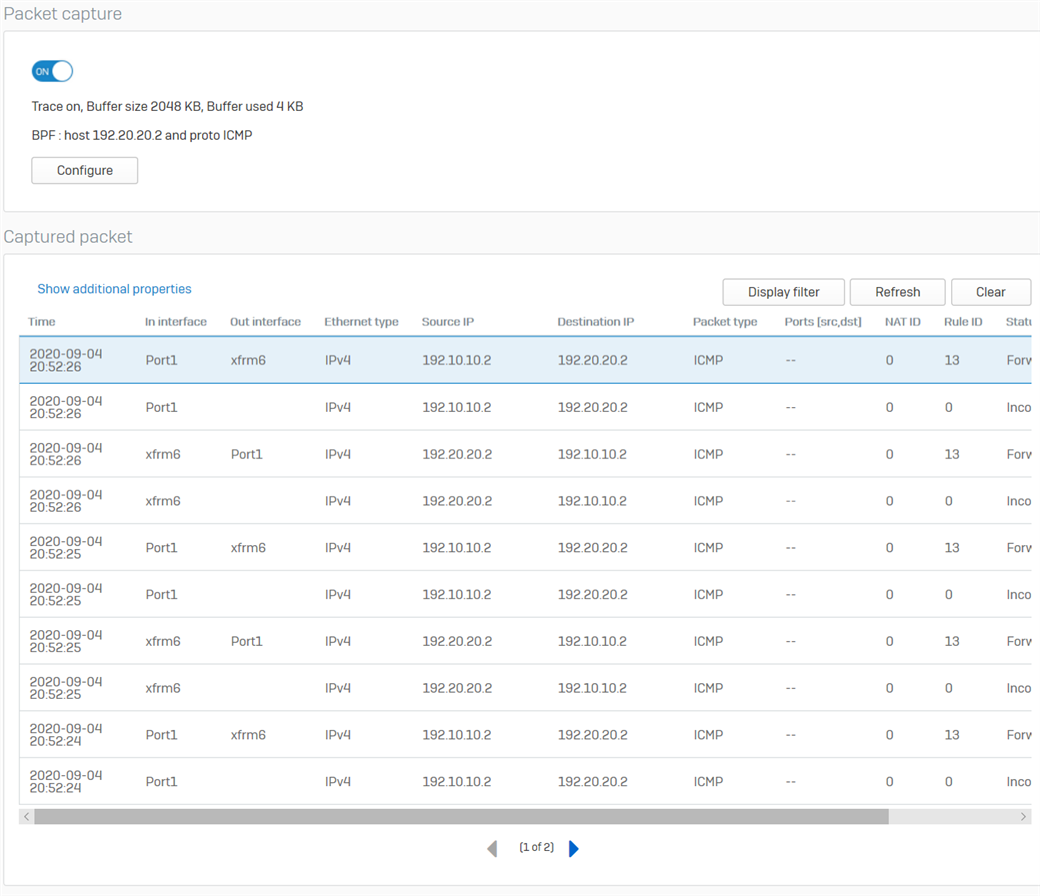
- From the HO Sophos Firewall, go to Diagnostics > Packet capture and then click Configure.
- Enter the following as the BPF string, then turn ON the packet capture.
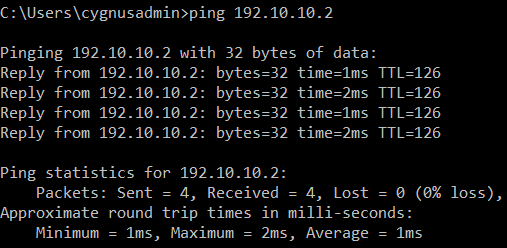
host 192.20.20.2 and proto ICMP - From the host 192.20.20.2 in the Branch Office, ping the host 192.10.10.2 in the Head Office.
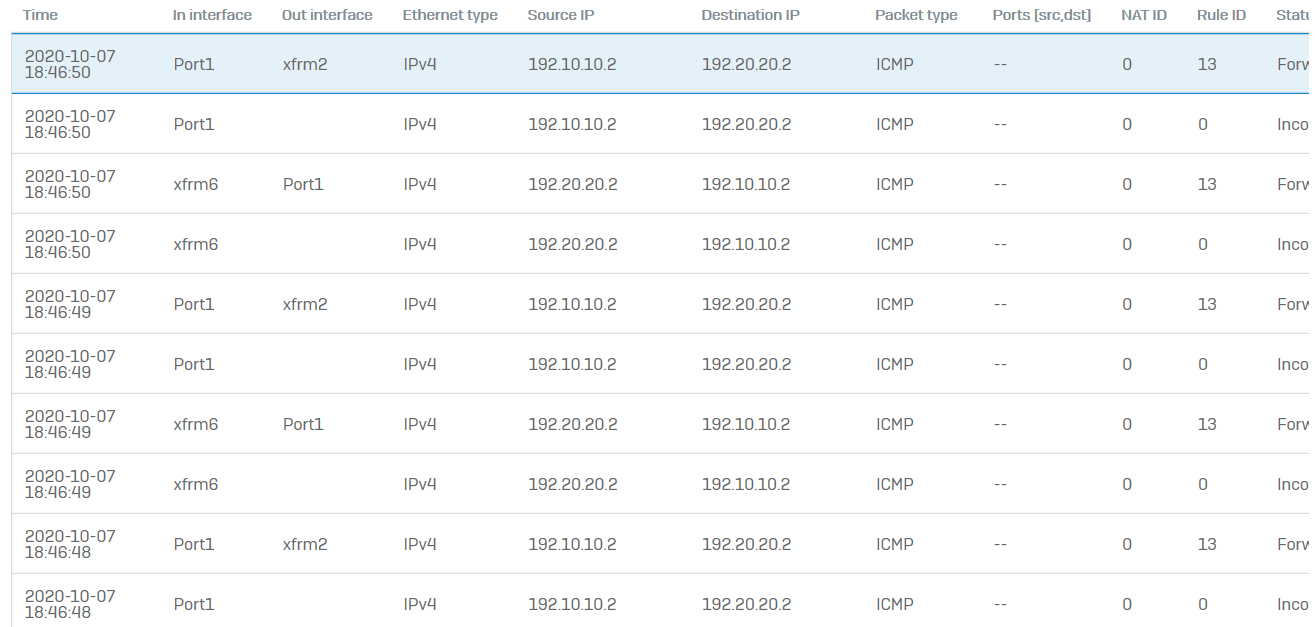
- The following will be displayed in the packet capture. It shows that the traffic is going in and out of the xfrm6 interface which is the RBVPN tunnel. Traffic can also be checked in the Log Viewer.
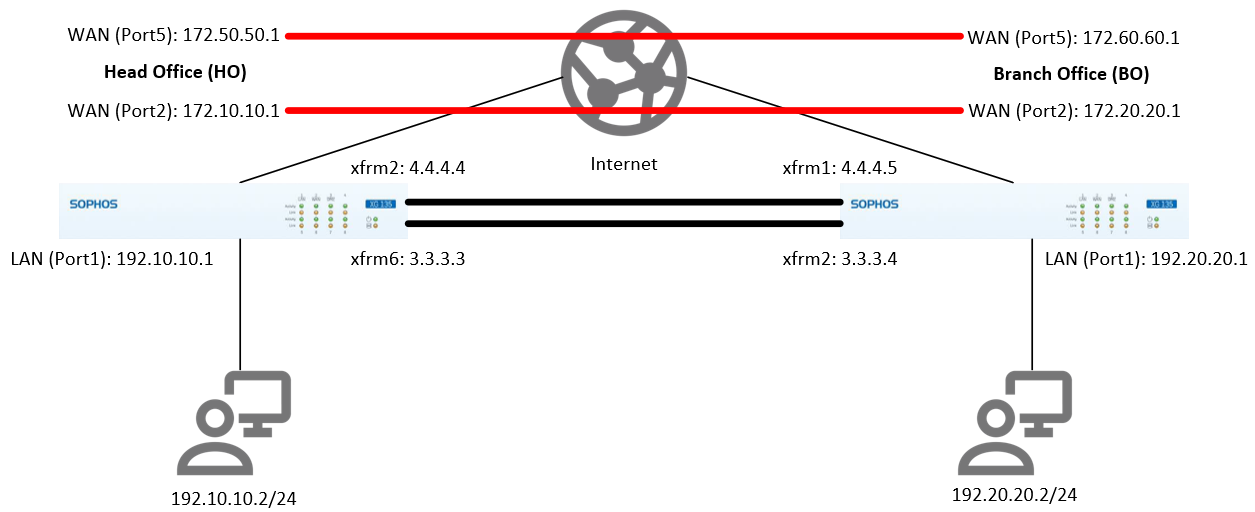
Scenario: OSPF over RBVPN with ECMP
This scenario shows two OSPF over RBVPN connections with an equal cost. It shows the basic concept of the ECMP feature of OSPF and does not cover complex scenarios.
Configuration
To achieve the scenario shown above, follow the same procedure to configure OSPF over RBVPN using the data shown in the network diagram above for each of the WAN connections and xfrm interfaces of the HO and BO. Once configured, there should be two RBVPN connections two xfrm interfaces each for the HO and BO; the firewall rules can remain the same, and the LAN and xfrm networks should participate in the OSPF process. Please see the screenshots below for the HO as an example.
RBVPN
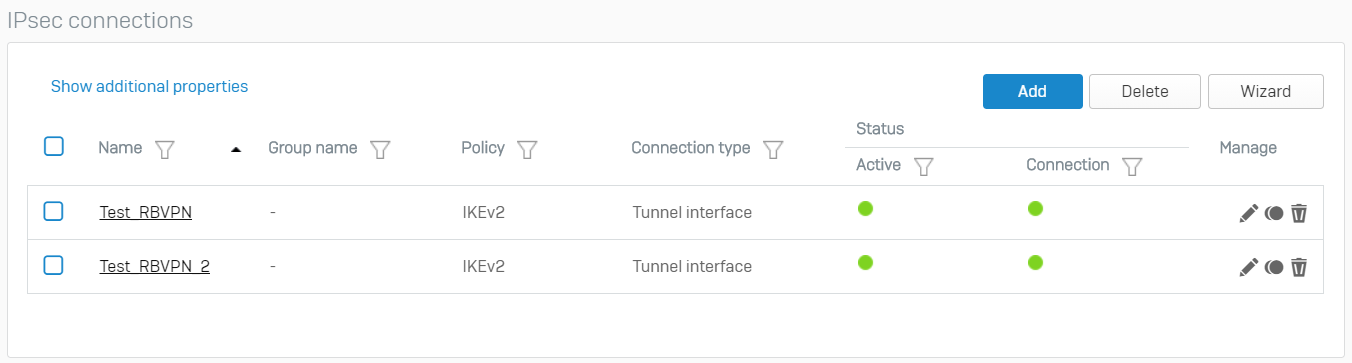
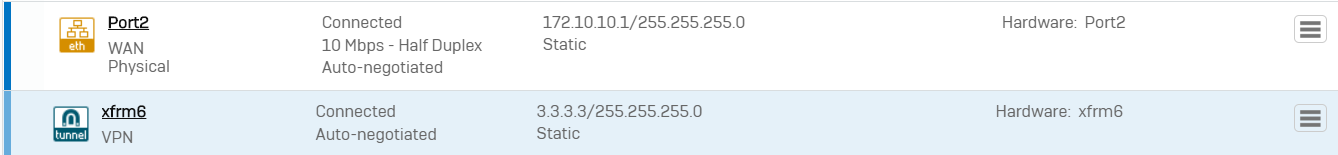
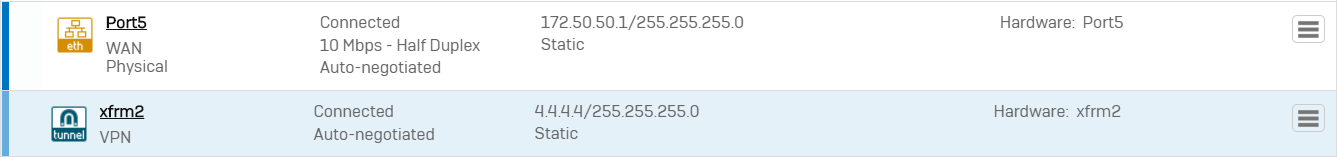
xfrm interfaces
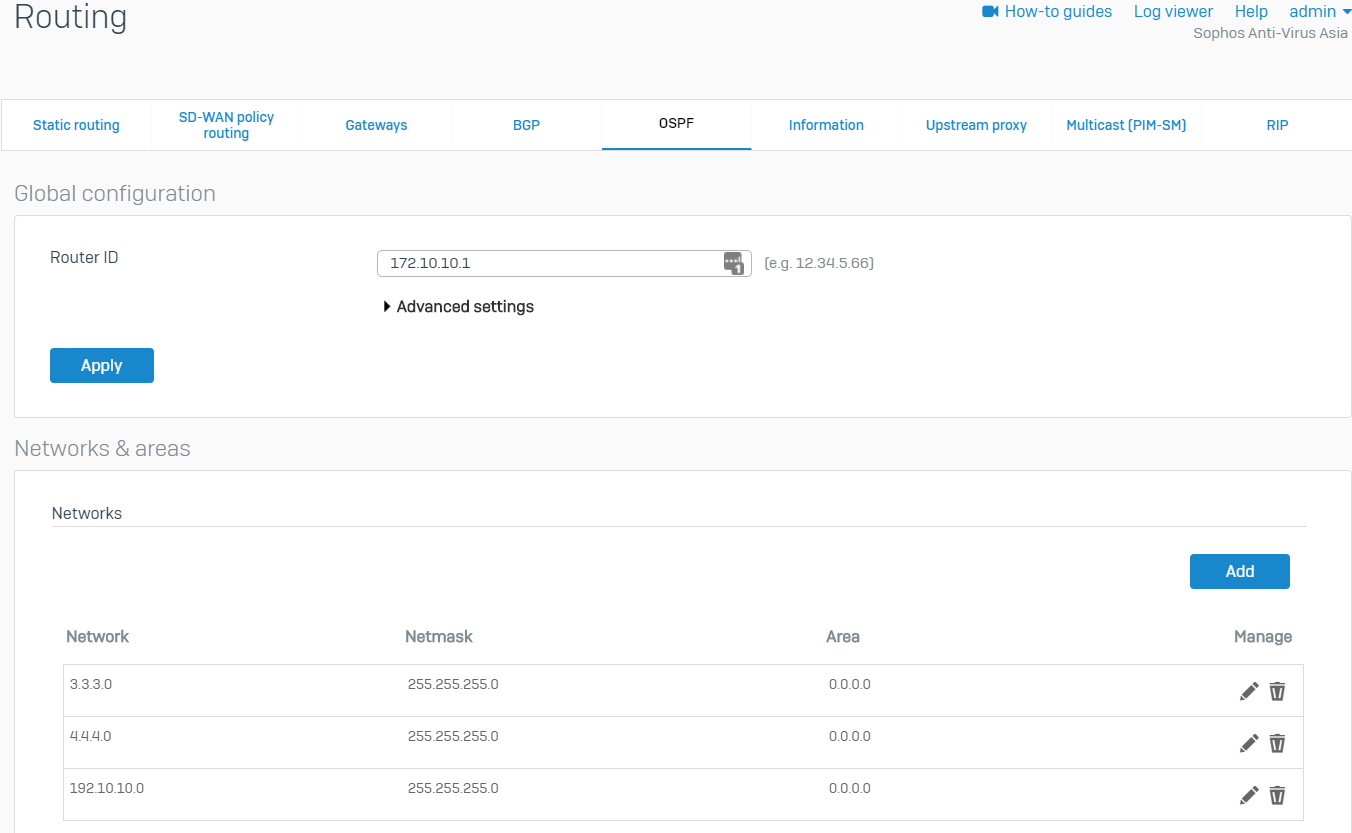
OSPF
Verification
Follow the same procedure in the Verification section.
RBVPN

OSPF
Traffic flow
The packet capture shows the two xfrm interfaces.
Related information
Updated links to latest
[edited by: Raphael Alganes at 9:57 AM (GMT -8) on 18 Dec 2024]