Hi to all,
I have a lot of connections attempts for the IPsec service:
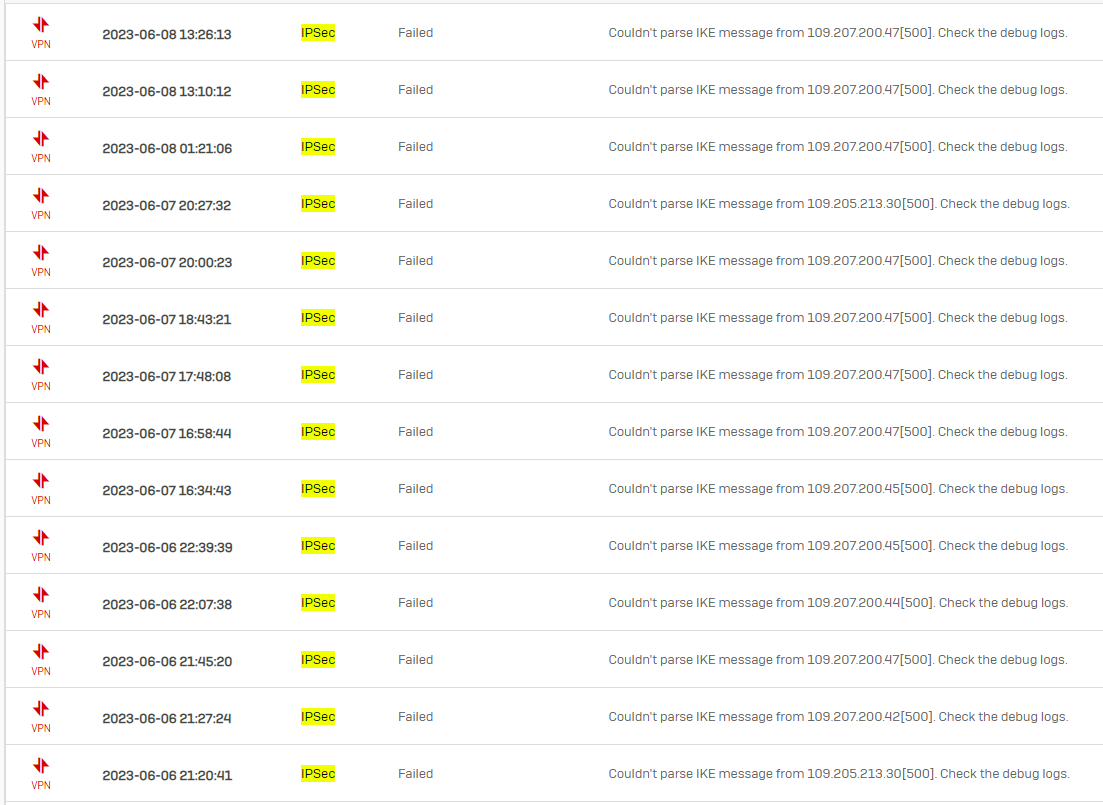
Always from the same two or three IPs.
Is there any way to block all for IPsec except the remote IP of the tunnel?
Thanks in advance.
Best regards.
This thread was automatically locked due to age.

