Hi, we have a Sophos XG210, SFOS 19. We set a site-to-site VPN tunnel to SAP with the parameters they gave us.
Locally, we have the network 10.X.X.X and 192.168.X.X (we are migrating to all class A), and SAP 10.100.0.0/22 & 10.100.4.0/27.
The tunnel works OK. We have connection between local hosts and remote servers in the SAP cloud. But, after some hours the tunnel goes down (I don´t know if it is important, but we are implementing SAP, there is only test traffic, not working officialy with SAP).
The status apears ACTIVE (green) but CONNECTION in YELLOW. If I restart the connection, the tunnel goes up and works OK.
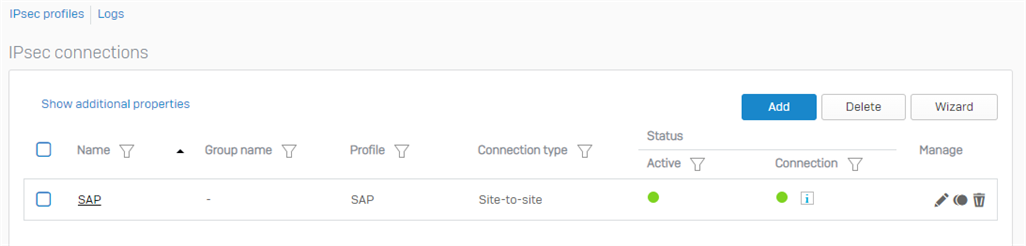
If click in the information appears near "connection" item, I see that:
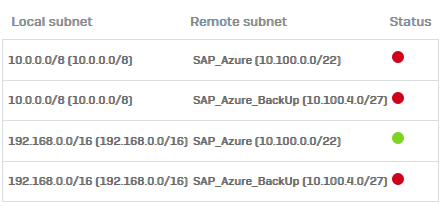
The problem is only with network class A. In the log console appers this message:
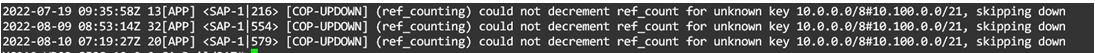
I don´t know if the problem is in SAP side, or maybe I need to configure a more specific network in my site (no /8)
Hello Daniel Zulian,
Thank you for reaching out to the community, can you share the following:
1.) Screenshot of the Gateway settings on XG
2.) Screenshot of the Gateway settings on SAP Azure
======================================================
Log file details: https://docs.sophos.com/nsg/sophos-firewall/19.0/Help/en-us/webhelp/onlinehelp/AdministratorHelp/Logs/LogFileDetails/index.html
1.) tail -f /log/strongswan.log
*Note: Capture this logs when you toggle the tunnel off/on !!
*Note: Before the capture enable the debugging on the SFOS with the following command: service strongswan:debug -ds nosync
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.

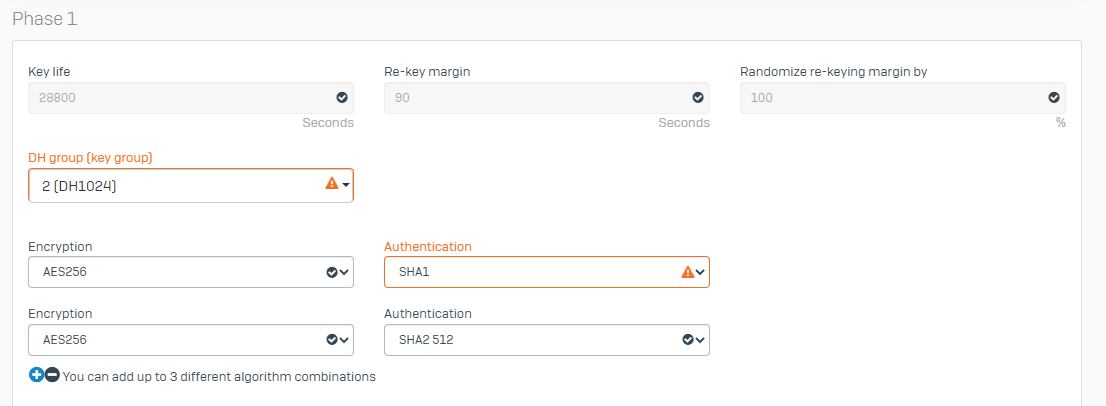
It is important to ensure that the encryption and authentication settings on both site are the same.
If possible you an also share the encryption and authentication settings on both site and the error message you get if any when the connection drops.
Regards,
Kingsley
Hi Daniel Zulian -
Thanks all for your answers. I don´t allowed to access the console, only the web interface. The other side is managed by SAP, I only have the parameters they send us. The remote device is a Cisco ISR 2511. They sent us this documentation as a guide (I assume they have the same configuration, actually does, because it works).

I configured a profile with this data as a guide (with IKEv2)
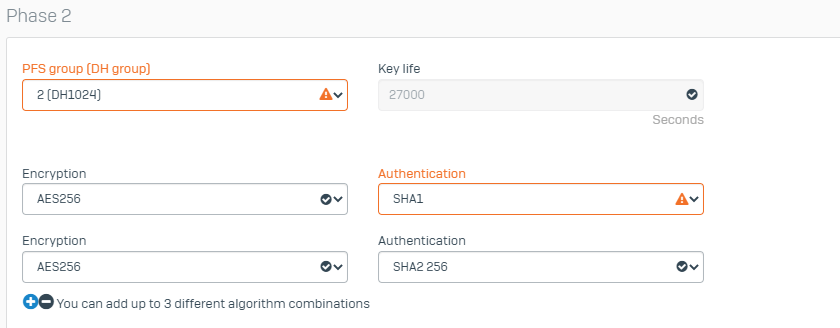
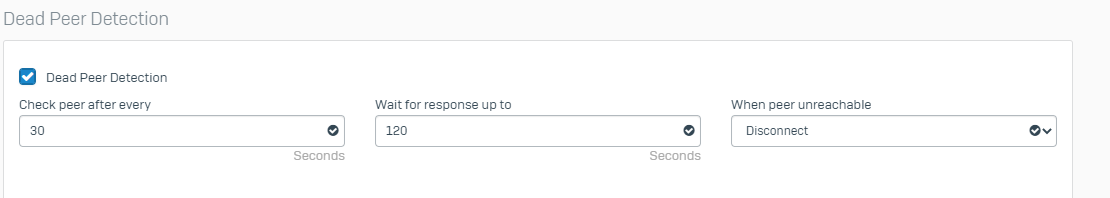
Then, in the Site-to-Site VPN I configured the tunnel
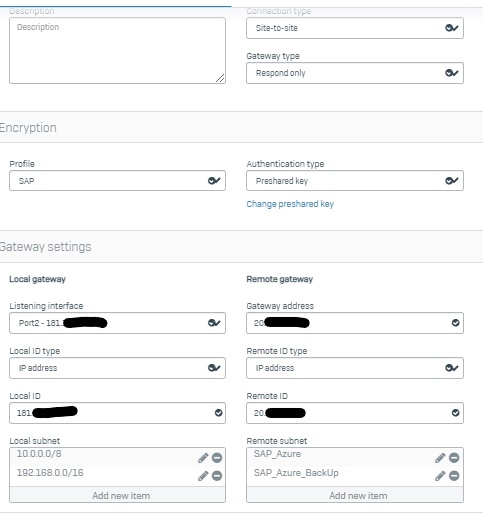
Sorry for not gathering all the requested data, but I don't have access to all devices. The local technicians said it's all OK, and SAP technicians said the same. So, we are in the same. With a few things to do. Thanks all
the tunnel goes up and works OK.
Try to delete the tunnel and re-create the tunnel and check tunnel works properly. Please Go to System-->Admininstration --->Backup and Firmware -->Firmware and share the status of the firmware shown on GUI?
I would suggest you go through the latest firmware version release notes available :
docs.sophos.com/.../index.html
Thanks and Regards
"Sophos Partner: Networkkings Pvt Ltd".
If a post solves your question please use the 'Verify Answer' button.
Hi, sorry for the delay. This is the status of the firmware
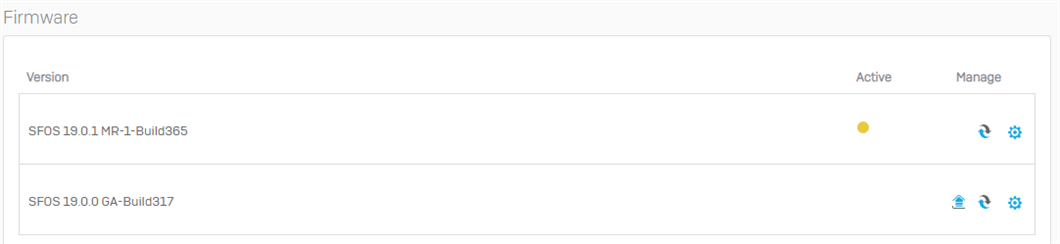
I got a meeting with an Azure technician. He saw the Sophos configuration and didn´t find problems. But, apparently, Azure side receives "integrity=SHA256" (that´s good) and other times Sophos sends it as "unknown". And Azure don´t accept it, and finish the negotiation.
Other problem Technician found, is Sophos is not accepting the Azure's reply of SHA256.
I let you the Azure's logs

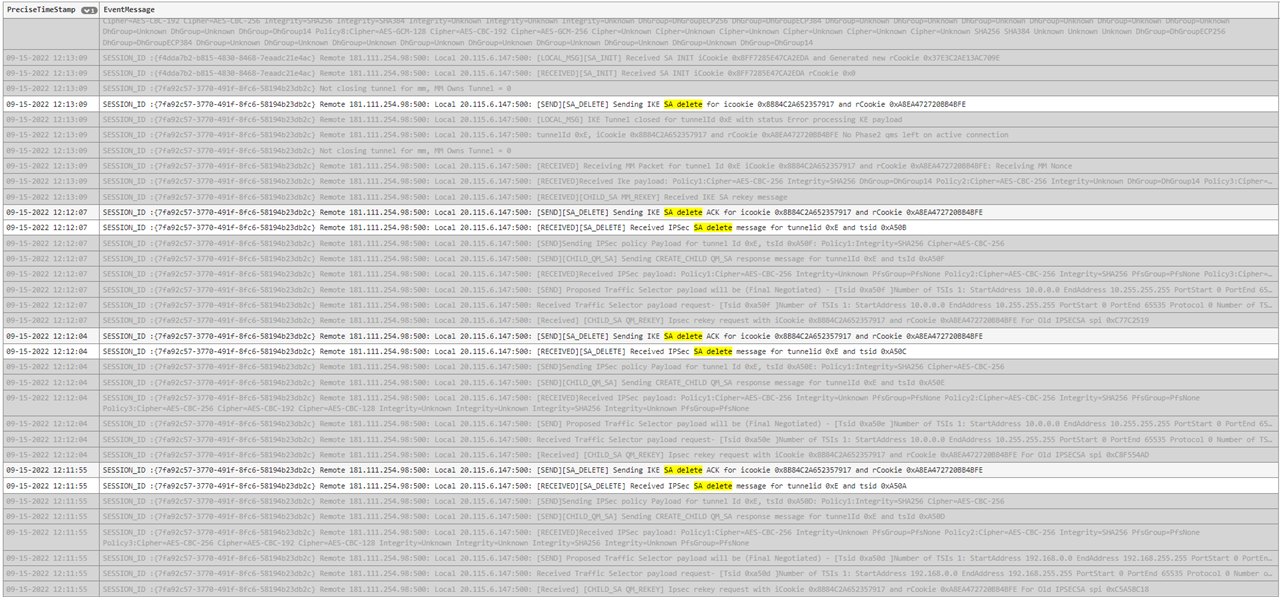
We have to check with IPSec VPN Policy and later overlapping subnets
Please share the logs from Sophos XG with SSH and make sure you hide the Public IP.
Login to SSH of Sophos XG firewall go to option 5>3 share the output
#cish
console>show vpn IPSec-logs
console>exit
#tail -f /log/strongswan.log
On the other end, I found Cisco ISR 2511 end of life.
Regards
"Sophos Partner: Networkkings Pvt Ltd".
If a post solves your question please use the 'Verify Answer' button.
Daniel Zulian , I see that phase1 and phase2 rekey timers are set to same value (3600 seconds) on Cisco ISR; please set phase1 value hither than phase2 ( by an hour or more) and reinitiate the tunnel from ISR side; I assume ISR is set as Initiator of the tunnel; please monitor if the reported issue occurs;
Hi Sreenivasulu Naidu, as Azure's technician has recommended, I set the timers phase1 = 28800 and phase2 = 27000. (the snapshots are before this change). But the problem still persists.
Thanks Bharat J, I try to get the credentials to SSH console and get the log.
Hello everyone.
I update the case: the official Sophos support remmended us to create a ROUTED VPN, not a policy vpn. I did it, and the problem was solved.
I let the link with the documentation, in case someone in the future has the same problem.
thanks all for your time