Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Sophos Factory offers a free Community Edition. Sophos Factory Sophos Factory Community Edition
Requirements for this HowTo:
Having a Factory Account (Community or Paid).
Having a AWS Account, which has access to Route53 and S3.
Having a single domain within Route53. For Pricing, see: https://aws.amazon.com/en/route53/pricing/
In this HowTo we are going to do the following steps:
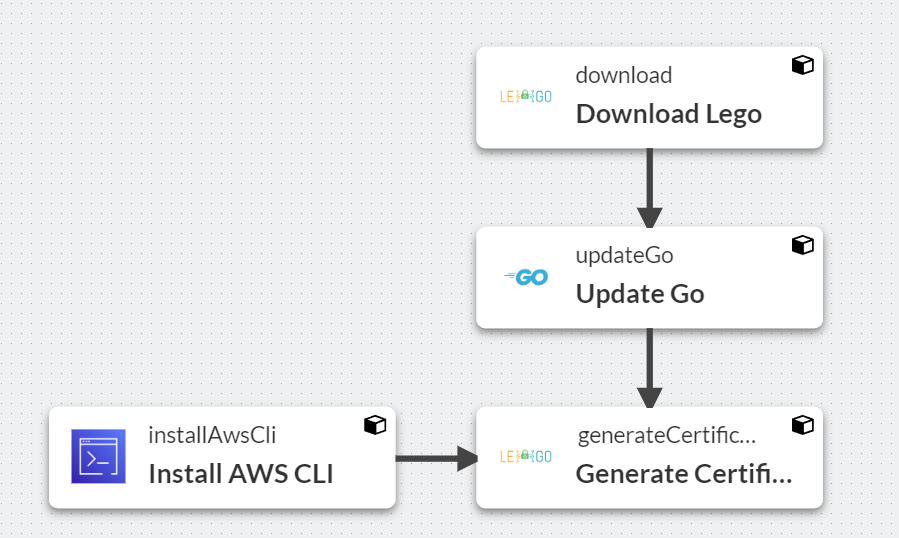
We build a Factory Pipeline, which renewals a LetsEncrypt (Wildcard or Single) Certificate with a tool called Lego using DNS Verification.
Lego gives us the opportunity to do it via DNS and with a CNAME Request. https://github.com/go-acme/lego
DNS Challenges are using a API of a DNS Provider, publishing the needed record on a "_acme-challange.customer.com" DNS record and fetching the certificate.
With Lego, we can do a CNAME Challenge as well - Meaning: You can point any Domain of X00 of domains via CNAME to a API capable DNS Provider (like Route53). See: https://letsencrypt.org/2019/10/09/onboarding-your-customers-with-lets-encrypt-and-acme.html
What to do:
1. Create your Factory Account, if not already available. Create your AWS Account, if not already available.
2. Create the AWS Route53 Domain, you want to use for Renewal. See Pricing for more information. See: https://docs.aws.amazon.com/Route53/latest/DeveloperGuide/domain-register.html
3. Create a CNAME in your Domain Provider of your Choice directly to your AWS Route53 Domain: 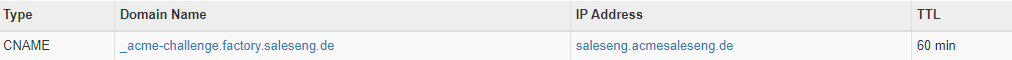
factory.saleseng.de is my LetsEncrypt Domain. saleseng.acmesaleseng.de is my Route53 Domain.
4. Create a AWS IAM User with the needed access to the S3 bucket and the Route53 Module. See: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_users_create.html
5. Generate the IAM User Access Keys for Factory: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_access-keys.html
6. Use the IAM Access Key in Factory:
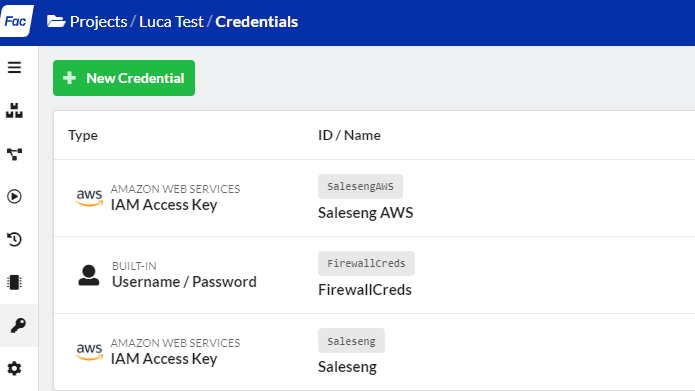
In Sophos Factory: You can copy/paste the code via editor into your setup.
---
variables:
- type: Credential
name: AWS Credential
key: credential
required: true
visible: true
default: false
allowed_types:
- aws_access_key
description: AWS Credential with permissions to upload to S3 Bucket and Route53.
- type: StringArray
name: Domains
key: domains
required: true
visible: true
default: false
description: |-
One or more domains for certificate.
Format: Domain.com
Or Wildcard Certificate: *.Domain.com.
If you add multiple Domains, only one Certificate will be generated. See: https://github.com/go-acme/lego/issues/228
- type: String
name: Email Address
key: email
required: true
visible: true
default: false
description: Email address for Certificate
- type: String
name: Lego Download URL
key: url
required: true
visible: true
default: true
description: |-
URL to download Lego. The Current version.
Format: github .tar.gz
See: https://github.com/go-acme/lego/releases
value: 'https://github.com/go-acme/lego/releases/download/v4.10.0/lego_v4.10.0_linux_386.tar.gz'
- type: String
name: DNS Provider
key: provider
value: route53
required: true
visible: true
default: true
description: DNS API Provider. For AWS add "Route53".
- type: String
name: DNS Resolvers
key: resolvers
value: 8.8.8.8
required: true
visible: true
default: true
description: Resolvers for the lego module. Add Google.
- type: Boolean
name: Accept Terms of Service
key: tos
value: true
required: true
visible: true
default: true
description: By setting this flag to true you indicate that you accept the current Let's Encrypt terms of service
steps:
- id: download
name: Download Lego
type: shell_script
depends: []
properties:
content: |-
{|[
"wget",
vars.url,
"&& tar xf",
(vars.url | split('/')) | last()
] | join(" ")|}
- id: updateGo
name: Update Go
type: shell_script
depends:
- download
properties:
content: |-
git clone https://github.com/udhos/update-golang
cd update-golang
sudo ./update-golang.sh
- id: generateCertificate
name: Generate Certificate
type: aws_cli
depends:
- updateGo
- installAwsCli
properties:
script_content: |-
{|[
"./lego",
"--email=" + vars.email,
"--domains=" + (vars.domains | join(" --domains=")),
"--dns=" + vars.provider,
"--dns.resolvers=" + vars.resolvers,
"-accept-tos" if vars.tos == true else undefined,
"run"
] | join(" ")|}
credential: '{|vars.credential|}'
args: LEGO_EXPERIMENTAL_CNAME_SUPPORT=true
- id: installAwsCli
name: Install AWS CLI
type: aws_install
depends: []
properties:
version: latest
- id: shell1
name: Rename CRT to PEM
type: shell_script
depends:
- generateCertificate
properties:
content: |-
{|[
"cd .lego/certificates/ && cp " + vars.domains + ".crt " + vars.domains + ".pem"
] | join(" ")|}
outputs:
- key: presignedUrl
value: '{|steps.generateUrl.result.output.presignedUrl|}'
layout:
elements:
- id: download
position:
x: -235
'y': -445
links: []
image_id: 1e948e6a-dbc0-41e3-aa52-e964674b617a
- id: updateGo
position:
x: -235
'y': -365
links:
- sourceId: download
sourcePort: bottom
targetPort: top
vertices: []
image_id: 6396ec88-90bf-4ddb-8749-fbb45d733fd1
- id: generateCertificate
position:
x: -235
'y': -285
links:
- sourceId: updateGo
sourcePort: bottom
targetPort: top
vertices: []
- sourceId: installAwsCli
sourcePort: right
targetPort: left
vertices: []
image_id: 1e948e6a-dbc0-41e3-aa52-e964674b617a
- id: installAwsCli
position:
x: -425
'y': -285
links: []
- id: shell1
position:
x: -235
'y': -205
links:
- sourceId: generateCertificate
sourcePort: bottom
targetPort: top
vertices: []
This code will generate a Wildcard Certificate in your setup. You can do more with this LetsEncrypt Certificate like described here: Sophos Factory: Upload LetsEncrypt Certificates on SFOS via Factory
Updated
[bearbeitet von: LuCar Toni um 12:31 PM (GMT -8) am 6 Nov 2023]
