If you're trying to configure Sophos ZTNA to enable connectivity to your Primary Domain Controller (PDC) for Active Directory (AD) services; including authentication, GPO processing, password changes, and LDAP queries, this guide is for you.
I faced challenges setting this up, and despite creating a support ticket and referencing the official Sophos article (KBA-000008481), I found that the provided instructions and video were incorrect. To save you hours of testing and troubleshooting, I’m sharing the correct configuration steps below.
First, create a ZTNA resource in Sophos Central to allow access to the required ports on your Primary Domain Controller. Ensure the RESOURCE TYPE is set to Other (not Web Application). The ports you need to open are:
You also need to create 17 ZTNA resources for the required SRV records that Active Directory relies on. Make sure to:
__SRV _ldap _tcp <DomainName>_ldap._tcp.<DomainName>_ldap._tcp.dc._msdcs.<DomainName>_ldap._tcp.<SiteName>._sites.<DomainName>_ldap._tcp.<SiteName>._sites.dc._msdcs.<DomainName>_ldap._tcp.DomainDnsZones.<DomainName>_ldap._tcp.ForestDnsZones.<DomainName>_ldap._tcp.pdc._msdcs.<DomainName>_ldap._tcp.gc._msdcs.<DomainName>_gc._tcp.<DomainName>_gc._tcp.<SiteName>._sites.<DomainName>_kerberos._tcp.<DomainName>_kerberos._udp.<DomainName>_kerberos._tcp.dc._msdcs.<DomainName>_kerberos._tcp.<SiteName>._sites.<DomainName>_kerberos._tcp.<SiteName>._sites.dc._msdcs.<DomainName>_kpasswd._tcp.<DomainName>_kpasswd._udp.<DomainName>After creating these 18 resources (1 for the PDC ports and 17 for the SRV records), your setup should work correctly, enabling full Active Directory functionality via Sophos ZTNA.
A big thanks to Nikita Sharma from Sophos Tech Support for her assistance during this process. I hope Sophos incorporates this guide into their official documentation to save others the frustration I experienced.
Let me know in the comments if this worked for you or if you have additional questions!
Hi Rafael, Thanks for your feedback and comments. We will review the KBA that was published, re-test and incorporate the suggestions made above.
Thank you Rafael for Sharing: this is what Community is for and i realy appricate That. We Used ad Connect since very First available and it‘s a Bad workaround - but it at least it is a workaround. Since now we have still issues with gpudate, But i will Update by policies as you discovered with Sophos and give you Feedback. Again, thanks for you work in that
Let me know if setting up all the SRV records fix your issues making gpupdate /force work. It does for me and we have out-of-the-box AD setup. If you have a custom or complex setup then you might need more SRV records (check on your PDC).
Follow-Up: Comprehensive Configuration for Sophos ZTNA with Active Directory Integration
This post builds on the initial guide by incorporating field-specific instructions for configuring resources in the Sophos ZTNA Add Resource window. It also provides detailed definitions and port requirements for all 17 SRV records, ensuring proper Active Directory (AD) functionality.
__SRV _ldap _tcp example com).srv01-pdc.example.com).example.com and <PDC name> with your actual domain name and Primary Domain Controller (PDC).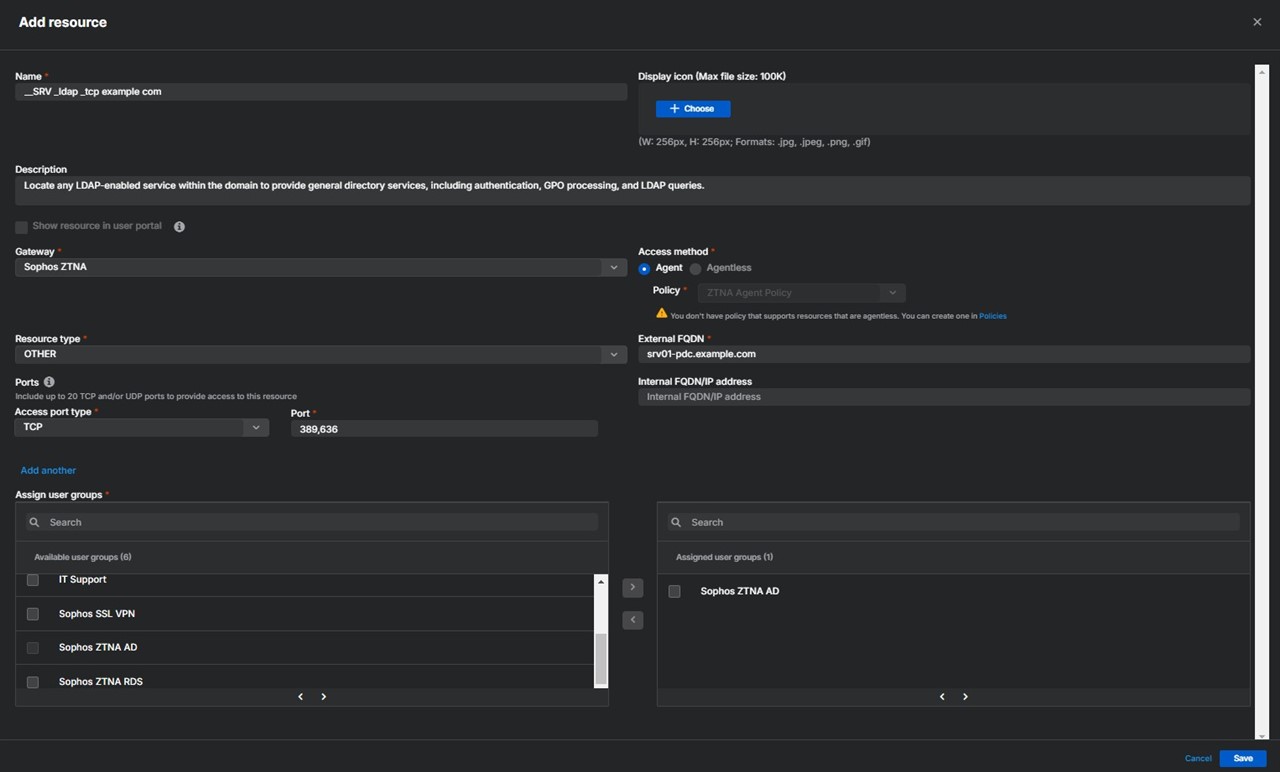
__SRV _ldap _tcp example com
srv01-<PDC name>.example.com__SRV _ldap _tcp dc _msdcs example com
srv02-<PDC name>.example.com__SRV _ldap _tcp Default-First-Site-Name _sites example com
srv03-<PDC name>.example.com__SRV _ldap _tcp Default-First-Site-Name _sites dc _msdcs example com
srv04-<PDC name>.example.com__SRV _ldap _tcp DomainDnsZones example com
srv05-<PDC name>.example.com__SRV _ldap _tcp ForestDnsZones example com
srv06-<PDC name>.example.com__SRV _ldap _tcp pdc _msdcs example com
srv07-<PDC name>.example.com__SRV _ldap _tcp gc _msdcs example com
srv08-<PDC name>.example.com__SRV _gc _tcp example com
srv09-<PDC name>.example.com__SRV _gc _tcp Default-First-Site-Name _sites example com
srv10-<PDC name>.example.com__SRV _kerberos _tcp example com
srv11-<PDC name>.example.com__SRV _kerberos _udp example com
srv12-<PDC name>.example.com__SRV _kerberos _tcp dc _msdcs example com
srv13-<PDC name>.example.com__SRV _kerberos _tcp Default-First-Site-Name _sites example com
srv14-<PDC name>.example.com__SRV _kerberos _tcp Default-First-Site-Name _sites dc _msdcs example com
srv15-<PDC name>.example.com__SRV _kpasswd _tcp example com
srv16-<PDC name>.example.com__SRV _kpasswd _udp example com
srv17-<PDC name>.example.comAfter configuring all 18 resources (17 SRV records + PDC ports), validate the setup by checking:
Let me know if you have additional questions or need further clarification!
I was able to perform all 4 tasks below after adding all resources to ZTNA
Also able to perform gpupdate /force without errors, the only thing that did not work was the login script that was defined in AD Users and Computers > user profile. Any suggestion what I could be missing?
No idea. I also had some issues with AD pushed scripts thru ZTNA and never figured out a way to resolve them.
This is a brilliant write up thank you so much, we desperately want to get this working to get line of site of our field-based technicians and users!
I have additional queries please with regard to the setup of these 18x resources...
For resource #1 to allow all the ADDS protocols and service ports, I'm assuming the External & Internal FQDN configured in the resource will simply be the FQDN of my PDC...e.g. contosodc01.contoso.com
For resources #2-18 I'm confused...how the ZTNA adapter knows to intercept this traffic and redirect it at the PDC?
Must I additionally add all the 17x External FQDN names listed in the 17x ZTNA resources to my internal DNS zone file and point them at my PDC as CNAME records or something?
Replace example com for your local domain contoso com
You don't need to put the name of the PDC. AD does all the magic behind the scenes including resources 2-18.
I found in my case I had to add all 18 resources to ZTNA to make everything work. Some are extra and you can make it work with less but I wanted a full redundant solution so ZTNA would switch to the Secondary DC in the event the PDC was down.
Btw after almost a year using ZTNA I decided to go back to Sophos SSL VPN using our XGS firewall. Our users have sporadic issues with ZTNA when working remotely and our 3rd party IT support company cannot troubleshoot ZTNA issues, so I end up having to troubleshoot the problems myself. VPN is older technology but it is 100% reliable. ZTNA is awesome when it works but people get frustrated when it doesn't work (which is at least once a month for us).
Hi Rafael Telles Heath Durrett, We have rolled out a fix which would make this configuration easier and more user-friendly than the suggested workaround. More details can be found here https://community.sophos.com/zero-trust-network-access/b/announcements/posts/sophos-ztna-updates-for-june-2025 . Please do try that out and let us know if that helps.
Hello Tejas, thank you for the update.
I see the new "Domain Controller (DC)" resource type now and that it includes all the SRV records auto-populated based on the External FQDN name you supply in the resource.
Looking forward to testing this out, will revert once I've had a chance to test.
Thanks!
That is great news that Sophos added DC for the ZTNA. Creating all those records was painful.