I'm getting one CRITICAL and two HIGH finding related to the version of Apache that Sophos is running. Is Sophos UTM 9 going to get an upgrade version of Apache anytime soon to clear these? Is there a safe way for me to upgrade myself? Here are the CVE's it cites:
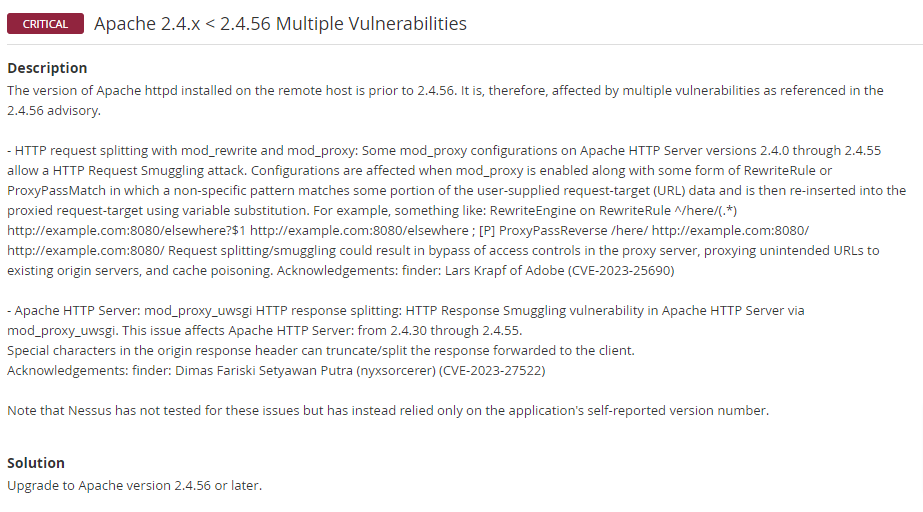
CVE-2023-25690
CVE-2023-27522
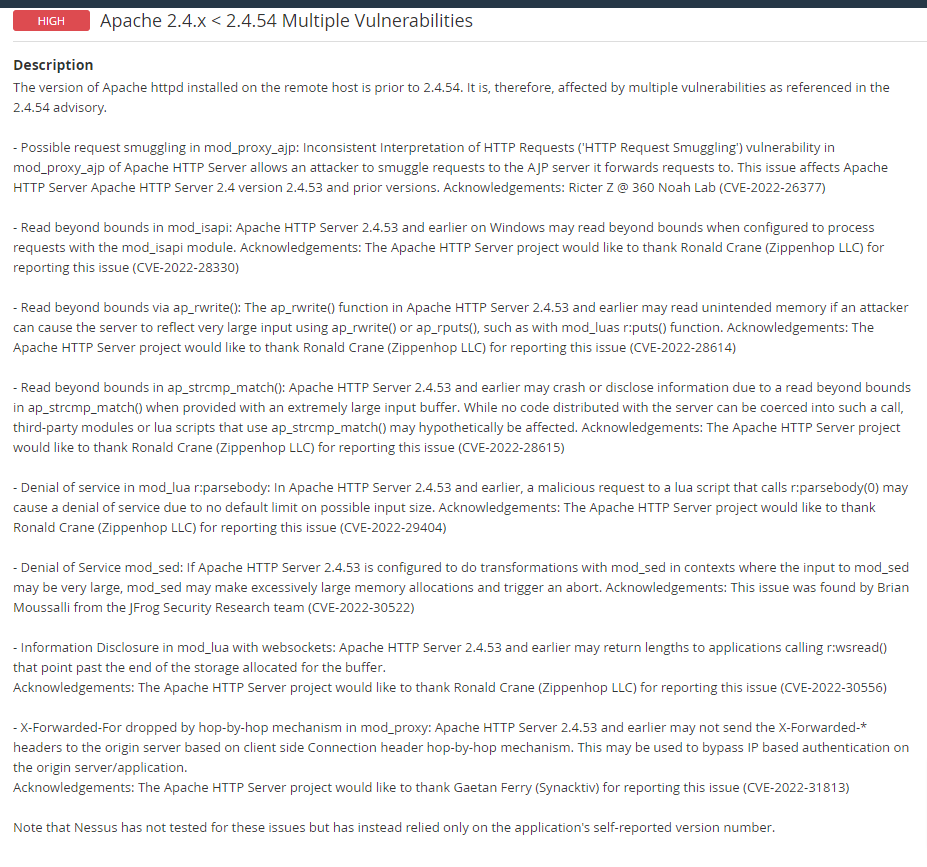
CVE-2022-26377
CVE-2022-28330
CVE-2022-28614
CVE-2022-28615
CVE-2022-29404
CVE-2022-30522
CVE-2022-30556
CVE-2022-31813
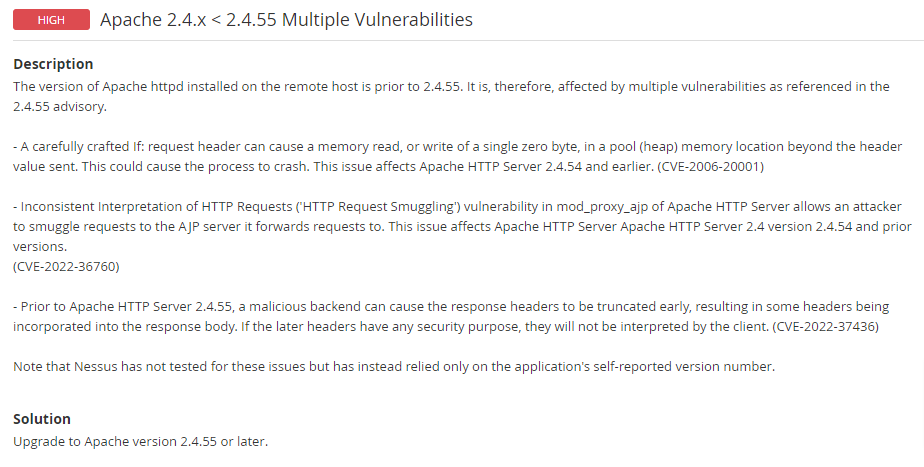
CVE-2006-20001
CVE-2022-36760
CVE-2022-37436
Hello Tim,
Good day and thanks for reaching out to Sophos Community
-CVE-2023-25690, CVE-2023-27522 - it only affects mod_proxy and mod_proxy_uwsgi, which we don’t use.
-CVE-2006-20001 - Not affected, UTM doesn’t use mod_dav
CVE-2006-20001 - Not affected, UTM doesn’t use mod_dav
CVE-2022-36760 - Not affected
CVE-2022-37436 - UI not affected, WAF affected which will resolve in 9.716 firmware
Further, the vulnerability is "Apache 2.4.x < 2.4.55 Multiple Vulnerabilities". All versions prior to 2.4.55 should have vulnerabilities as of the Nessus Scan. Apache Upgrade to 2.4.56+ is included in UTM 9.7 MR16 (9.716)
Raphael Alganes
Global Community Engineer, Support & Services
Are you a Sophos Partner? | Product Documentation | @SophosSupport | Sign up for SMS Alerts
If a post solves your question, please use the 'Verify Answer' button.
The award-winning home for Sophos Support videos! - Visit Sophos Techvids