[Update - 7/08/2020]
All Central regions have been updated with the AP firmware 2.3.0-7 to resolve the issue that caused APX 120 devices to become unresponsive and non-functional. New APX 120s can now be registered. Previously registered APX 120s can now also be upgraded to the latest firmware.
Customers with unresponsive APX 120 access points should contact support for further assistance.
Overview
Sophos Wireless v2.3.0-6 introduces a number of new features to improve the Synchronized Security functionality. You can now activate synchronized security for Endpoint and Mobile/UEM separately, create a synchronized security SSID for managed devices only, and also create your own custom URL whitelist for the walled garden when a device has a red security heartbeat status. Additionally, there are a few UI enhancements as we have added the user identity to the ‘Devices’ list and to the hotspot feature where there will be seamless device roaming for users connected to a captive portal enabled SSID. This release also contains few bug fixes which will enhance the overall user experience.
Please note: The following new features will not be visible in the user interface until the Sophos Central update has been released. This is currently scheduled for June 29th 2020.
New Feature/Enhancement:
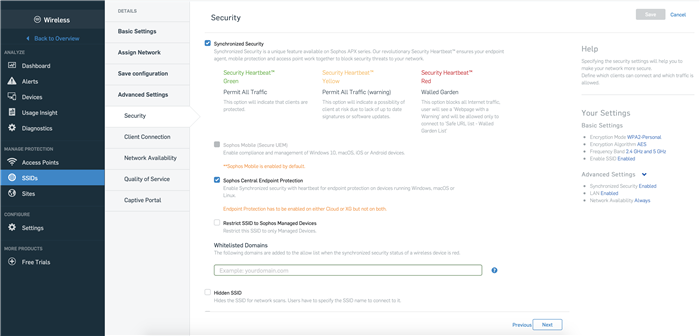
1. Separate Activation of Synchronized Security Sophos Central Endpoint Protection and Sophos Mobile (UEM):
This feature allows an admin who is using synchronized security with their managed endpoints and XG Firewall, to deactivate synchronized security for endpoint in Central Wireless. This option is enabled by default and the security heartbeat will be processed by Central Wireless. Once disabled, a Sophos endpoint will start sending the security heartbeat to XG Firewall instead. From a Central Wireless perspective, these devices become "unmanaged" devices and the security heartbeat status on the ‘Devices’ page will show ‘No Security Heartbeat’. Synchronized security with Sophos Mobile (UEM) is enabled by default and so can now be used even if the feature is deactivated for Sophos Endpoint. For Mobile, this option cannot be disabled as Sophos Mobile is only able to send a synchronized security heartbeat status to Central Wireless, as shown in the image below.
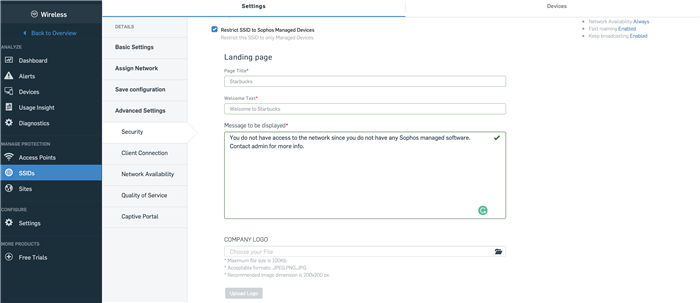
2. Restrict SSID to Sophos Managed Devices:
This option can be used to restrict a particular SSID to Sophos managed devices only. This would typically be used in BYOD and potentially zero-trust environments where an IT administrator would like to enforce compliance amongst the devices that are accessing the network. If an unmanaged device connects to the SSID, it is put in a walled garden state and treated the same as a device with a ‘red’ security heartbeat status. Once the device is put in the walled garden, a warning page is displayed to the user. By default, these devices can access "*.sophos.com" sites. Additionally, the admin can whitelist further URLs for a device to access. More details about this feature are mentioned in the following section.
Additionally, an administrator can customize the page that is displayed on unmanaged devices. To do this, the admin needs to first enable the option and save the SSID. On editing the saved SSID, the admin will see the custom company logo upload option as shown in the image below.
Limitation: This feature can only be enabled when both Sophos Mobile and Endpoint devices are being managed through the same Sophos Central account. If an admin chooses to send the security heartbeat of Endpoints to XG Firewall, this option will be greyed out.
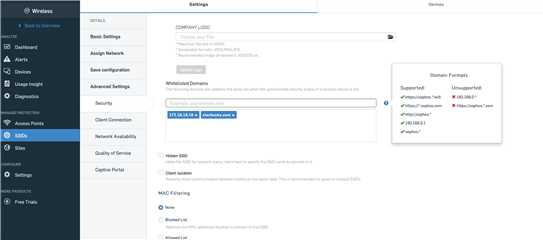
3. Whitelisted Domains for Synchronized Security walled garden:
This feature provides more flexibility to an admin to define the level of network access for devices which have a red security heartbeat status. Previously, these devices could access only "*.sophos.com" sites. Now, an admin can add either a domain name or an IP Address that can be accessed by devices with a red health status, as shown in the image below.
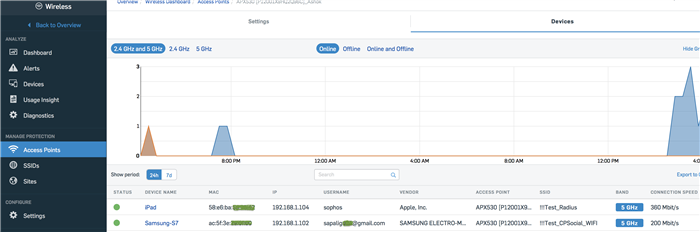
4. User Identity:
The user identity of unmanaged devices based upon the authentication mode is displayed on the ‘Devices’ page. The authentication modes through which the user identity can be retrieved are:
- WPA2-Enterprise
- Captive Portal:
- Social Login
- Backend Authentication
5. Seamless Device roaming for captive portal enabled SSID
This enhancement will provide uninterrupted device roaming when a device connected to a captive portal enabled SSID roams between access points in a network, meaning the user will not need to re-enter the credentials after roaming.
Bug Fixes
|
Issue Key |
Summary |
| CWIFI-10519 | Captive portal is not working with the combination of Guest network and VLAN |
| CWIFI-11330 | Access point was reporting incorrect security heartbeat status for managed devices |
| CWIFI-11387 | Sites: User can create duplicate Site on Sites page |
| CWIFI-11438 | Sites: Some Access points are not getting the country code based on the geolocation |
| CWIFI-11412 | Synchronized Security AP certificate is being generated on every bootup |
Known Issues
| Issue Key | Summary |
| CWIFI-11871 | Captive Portal -Social media login issue in some browser versions |