Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Hello, I work at a school and we use an XGS 2100 to manage our internet. We have our networks divided for staff, students, etc.
We recently changed our connections from LAN to VLAN, so we can run distinct profiles on each SSID. Since then our VLAN WiFi connected devices (laptops, chromebooks etc.) haven't been able to see the LAN connected printers or print anything from anything on the VLAN. The only exceptions are devices that are directly connected.
We also moved the connections over the Central since switching to VLAN. Same goes with our AP's.
VLAN can't ping LAN, and LAN can't ping VLAN.
Any help would be greatly appreciated.
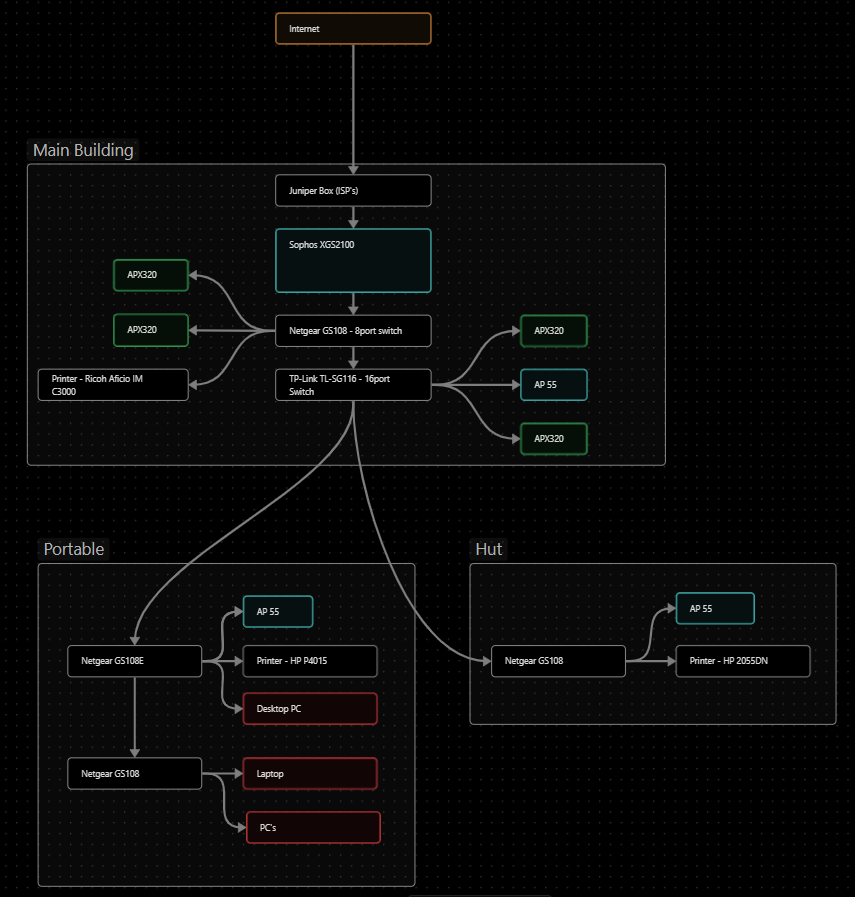
Here's our layout
1. AP55? How do you manage these devices?
2. XGS is the default gateway for all VLAN's? Are the devices able to Ping their gateway?
Create a "Drop & log" rule at the end of your Firewall-ruleset and check the logviewer for accepted or dropped packets
3. use packetcapture with the filter "host 1.2.3.4 and host 2.3.4.5" (IPs of source and destination device when trying to ping) ... feel free to post the results.
Dirk
Systema Gesellschaft für angewandte Datentechnik mbH // Sophos Platinum Partner
Sophos Solution Partner since 2003
If a post solves your question, click the 'Verify Answer' link at this post.
Apologies but I am fairly new to this so not everything will make sense to me.
1. We manage them through Central.
2. Yes and yes.
- I tried creating the drop and log rule like you suggested, but It didn't give me any results. Maybe I'm missing something or doing something wrong.
3. It just tells me "no records found". Again, I might be missing something or doing something wrong.
Your printers might advertise themselves via mDNS, which uses multicasts. Multicasts are not transmitted across networks, which includes between subnets or VLANs. I WISH that Sophos would support multicast forwarding for such cases, but it doesn't.
The lack of pings could indicate a total lack of routing/permission between them, but if your printers are like my printers, mDNS could be a problem with your new setup, even if you solve the ping issue.
We can assume that you added appropriate firewall rules to allow traffic between the various VLANs?
Do the printers and the WiFi connected devices have the Sophos firewall at their default gateway?
If not, you need to change the configuration of the LAN-printers to point at the firewall as their gateway.
Then you need "Allow"-rules for the traffic from the WiFi devices to the LAN-printers.
Once this is done, you should be able to ping the printers.
Mit freundlichem Gruß, best regards from Germany,
Philipp Rusch
New Vision GmbH, Germany
Sophos Silver-Partner
If a post solves your question please use the 'Verify Answer' button.
Yes, our printers are all pointing towards the Sophos firewall.
As well as all our WiFi connected devices.
We have made an Allow rule many times with many variations but still nothing is coming through.
Here's what our allow rule looks like.
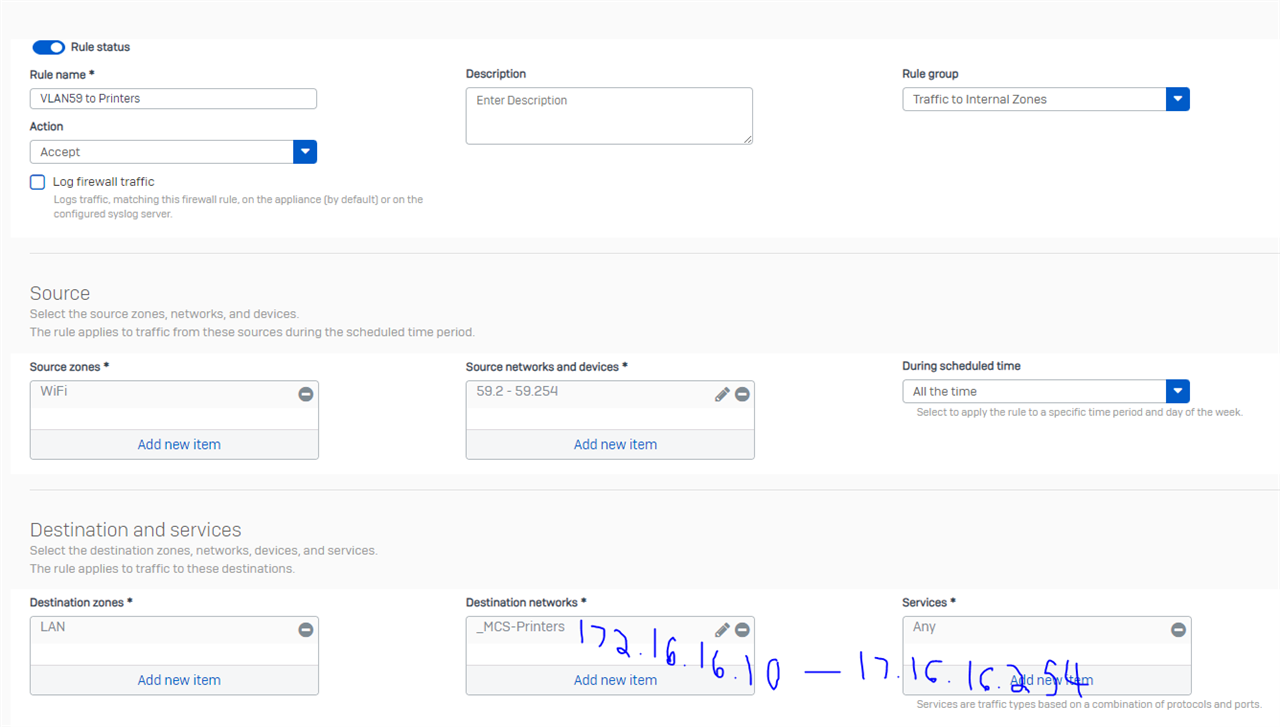
We have another rule but the sources and destinations are switched around.
Any suggestions? Thanks for your help.
I suspect a VLAN transport problem here.
But let's start troubleshooting: can you ping each VLAN from the Sophos firewall? At the firewall you go to "Diagnose" then "Ping"
Can you show us the network/interface definitions at your firewall? (Screenshots)
Mit freundlichem Gruß, best regards from Germany,
Philipp Rusch
New Vision GmbH, Germany
Sophos Silver-Partner
If a post solves your question please use the 'Verify Answer' button.
AFAIK the Netgear GS-108 switch is an unmanaged switch which is only able to transport the default VLAN=1 (aka "default VLAN" or "AdminVLAN").
The TP-Link SG116 is unmanaged as well, but it should be able to pass VLAN-Tags through to the other ports, when it receives those tagged packets.
So I really wonder how you managed to "configure VLANs".
Can you give us some more details on this, please?
Mit freundlichem Gruß, best regards from Germany,
Philipp Rusch
New Vision GmbH, Germany
Sophos Silver-Partner
If a post solves your question please use the 'Verify Answer' button.
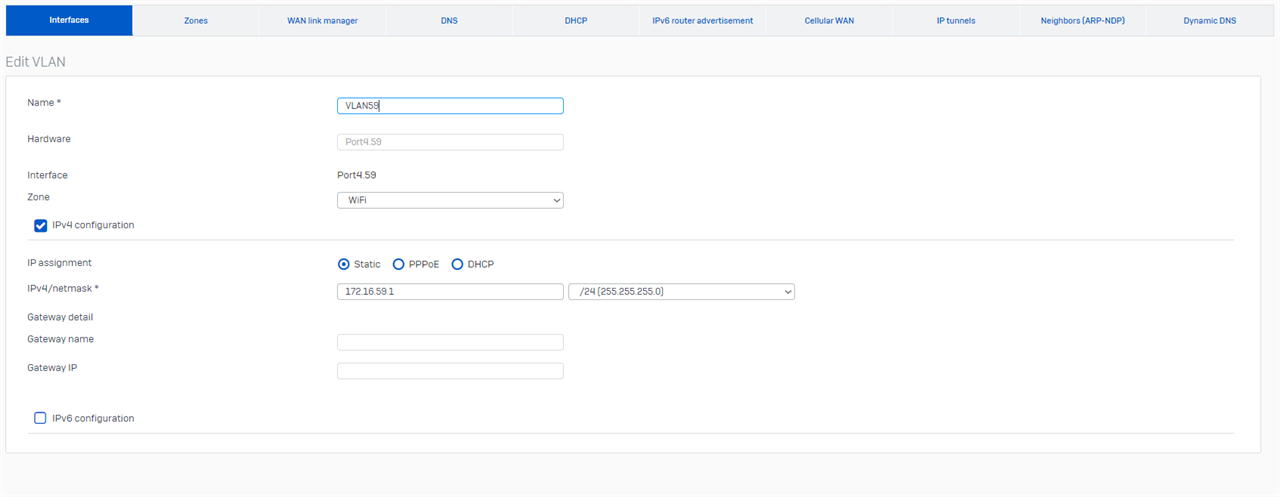
I can ping the VLANs from the firewall, If I pick the right interface. Which would be Port4.59 for VLAN59 and so on.
I believe this is what you asked for.
Hi,
as Philip advises there is nothing on your network to seperate the traffic from the various devices eg everything is on the same network none of the switches can differentiate VLAN traffic. You need some smart switches.
Ian
XGS118 - v21.0.1 MR1
XG115 converted to software licence v21.0.1 MR-1
If a post solves your question please use the 'Verify Answer' button.
So switches that aren't managed at all are is what is preventing the traffic between VLANs and printers?
That seems unlikely to me. Why and how would the switches be the ones that are preventing traffic from VLANs to Printers?
All our switches in the building are unmanaged and empty, so there's nothing going on when passing through the switch.
So switches that aren't managed at all are is what is preventing the traffic between VLANs and printers
Some unmanaged switches remove the VLAN tagging when passing traffic, at the same time breaking inter-VLAN connections. (This depends on each switch vendor implementation.)
This could be the reason why it's not working correctly.
If a post solves your question use the 'Verify Answer' button.
Ryzen 5600U + I226-V (KVM) v21 MR1 @ Home
Sophos ZTNA (KVM) @ Home
What do you mean by default VLAN? Is there somewhere in the firewall that allows me to change the default VLAN so it points the traffic the way I want to?
If your switches are unmanaged, they most likely don't tag traffic, so it is not actually TAGged.
The Default VLAN is always VLAN 1 in all switches, you can't change the default VLAN in the Sophos Firewall.
Regards,