Hello everybody,
I'm currently trying the Web Protection. I understood how it works, transparent/standard mode, etc.
However, I noticed that lots of things don't work in case HTTPS is configured on "URL filtering" only (download scanning, download checks for blocking, etc). This is logic seems nearly everything now is working with HTTPS.
Our company has a lot of testing/development computers which must have Internet and there are not in a domain and not well secured. Since they are on WORKGROUP, it is annoying to have the need of a certificate to allow "Decrypt & Scan" feature on HTTPS.
1. Is there a way to have HTTPS configured on "Decrypt & Scan" mode without having the need of pushing the CA certificate on clients computers ?
I read the following KB: support.sophos.com/.../KB-000034334
What about this: "In 9.2, SNI-based HTTPS filtering is possible, which allows you to filter HTTPS content without installing a certificate, but does not allow in-stream antivirus scanning of web traffic."
2. Is it a solution ? What must be done ?
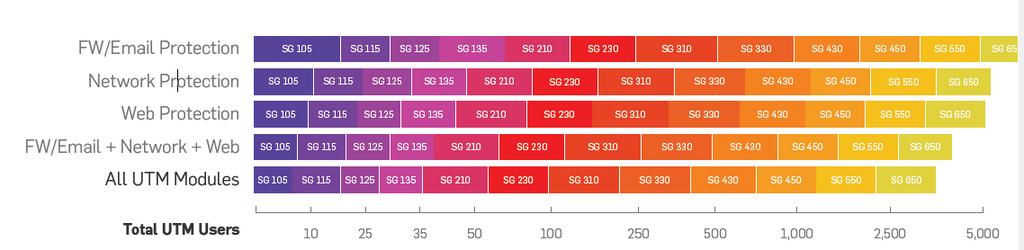
So far, I'm testing the Web Protection in a lab environment with few machines. I'm a little bit afraid of the resources consumption with a production environment. We have two SG 210 on active-passive HA with around 150 computers.
3. Will it be ok with Web Protection for this company/computers sizes ?
4. Eventually, about transparent mode and SSO, is there a way to allow authentication immediately when a computer is booting ? Any workaround ? For the moment I have to do a HTTP request to make it work (as said in the documentation). I tried with a Powershell script (Invoke-WebRequest) but it didn't work.
Thank your for your time & help !
DeltaSM
This thread was automatically locked due to age.