Hello,
I'm trying to create a simple allow list (whitelist) in in the SOPHOS UTM Firewall for a particular site, leaving all other sites unaffected.
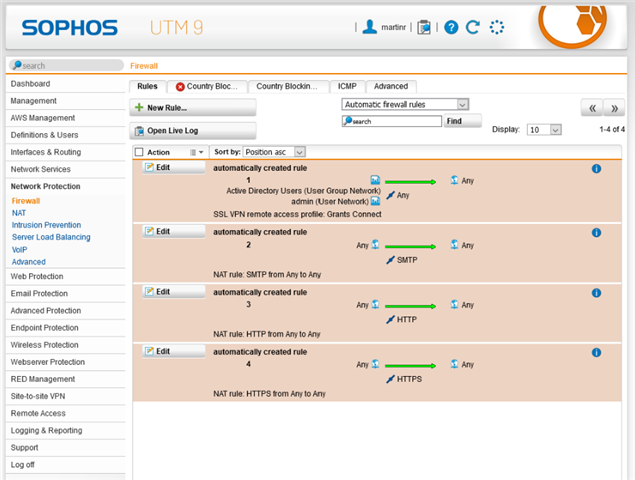
See the following configuration screen;

Rules 9 and 10 are the ones of interest.
Rule 9 is attempting to define a set of IPs to allow to the given network.
Rule 10 is attempting to block anything that does not match rule 9.
All simple stuff, but why is it completely ignored?
My first thought was that the source IP being tested is the local IP (rather than the external, which would be rather disappointing). So I also disabled rule 9 to simply block everything from that site. But still nothing.
I also don't understand the automatically created rules 1-4 which basically allow everything everywhere and can not be modified in any way. It would make more sense to me to have my two new rules in front of 1-4 as they would appear to short circuit anything following.
Any help appreciated.
Thanks.
This thread was automatically locked due to age.