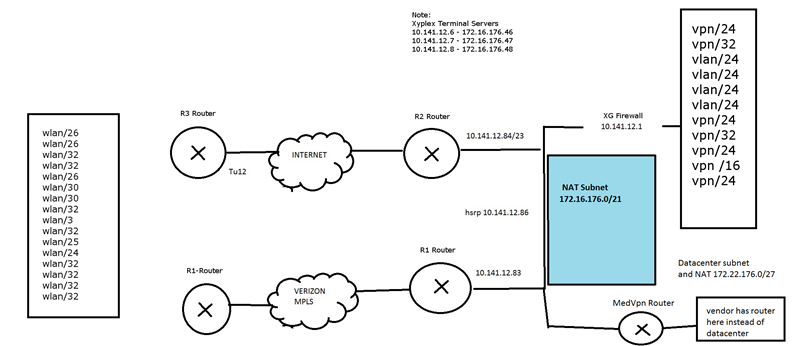
On this diagram we have several objects to look at
WAN IP = 12.12.12.35
LAN IP of UTM = 8.8.8.8
WAN IP of Router behind firewall = 12.12.12.36
LAN IP of Router behind firewall 8.8.8.4
How would you configure Port 4 to plug a cable from the UTM to the WAN Port of the Router?
I plan to configure interface X4 = 12.12.12.36/32 proxy-arp enabled
now granted if the firewall rules are correct to allow full ip from 12.12.12.36 to get out through the internet to connect to defined router (10.10.10.10)
I think the Utm will see traffic from defined router (10.10.10.10) from any source (port 2 wan 12.12.12.35), permit it to pass to port 4 12.12.12.36. Transparent traffic ???
In theory this should work right?
If the router because of vpn tunnel policies didn't need the wan ip configured a nat rule would be sufficient.
Other alternative create dmz ip for the interface and have the router's wan ip changed to avoid messing up the routing table.
This thread was automatically locked due to age.