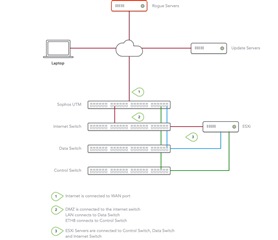
I have a lab set up in a data center that is used for research (think software engineering, DevOps, infrastructure automation, and such). With that, I have a Gbps internet connection and a /64 IPv6 space available. The lab is used for software engineering, in particular, as it pertains to infrastructure automation (or DevOps if you must). This involves testing firewalls and other infrastructure from different vendors. Most of that research is done on vSphere hosts, which have physical network cards dedicated for control (aka management, IPMI, Power), data (internal traffic between various networks), and internet traffic. Each of those network cards connects to dedicated switches for each purpose, namely a control, data, and internet. Those switches connect to the Sophos UTM.
I am curious how to make the Sophos UTM act as a transparent firewall for the "internet" traffic, meaning that a firewall deployed on any of the vSphere hosts can listen to one of the many public IPv6 addresses without having to change the configuration of the Sophos UTM. At the same time, I can still connect via VPN to a bastion host within the network via the Sophos UTM, and have the Sophos UTM control the data and control planes (act as a DHCP, DNS, NTP server).
I understand I can achieve something like this by bridging the WAN and DMZ ports, but I have had endless problems with that configuration (I'll contribute that to user error). In the past, I would NAT the public IP to a private IP, which worked great for a small number of public IP addresses. For /64 IPv6 addresses, this isn't feasible.
What is important to me is that the Sophos UTM protects the lab against known threats and that I can apply country blocking.
I previously connected the internet connection from the data center to the internet switch and connected a port thereon to the Sophos UTM. That worked, in that any firewall, virtual or physical connected to the internet switch could receive internet traffic, but excluded any kind of protection. Any kind of amplification attack will render the lab inaccessble.
Also one side note, is that there's a choas monkey running in the lab which will power off vSphere servers from time to time to test redundancy etc. This is why I don't want to use a virtualized firewall as my primary firewall.
This thread was automatically locked due to age.