Overview
Version 2.2.0-19 is an AP firmware release which provides the support on the access point for some upcoming new features.
Please note:The following new features will not be visible in the user interface until the Sophos Central update has been released. This is currently scheduled for December 2019.
- Social login as an authentication type for captive portals
- Captive portal customization options
New Feature/Enhancement:
1. Hotspot (captive portal) customization:
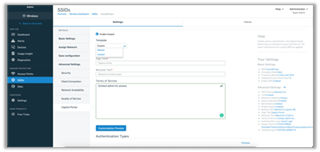
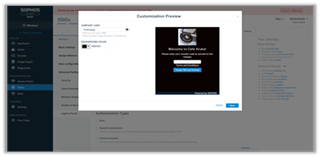
We’ve added a drop-down on the captive portal page where you can select a template: Default or Custom, as shown in Image-1 below. Once you select Custom, the customization preview page appears, and you can then choose an image/logo to upload (max. size 1 MB) and the background color as shown in Image-2. Once your users connect to the hotspot SSID, they will be redirected to your customized page.
Image 1
Image 2
2. Social Login:
Using this feature, you can allow your users to authenticate using their social media accounts. As the admin, you select to let them use their Facebook or Google accounts to authenticate with your hotspot.
Note: You will need to do some setup in your Google and/or Facebook Developer account (see help for further information).
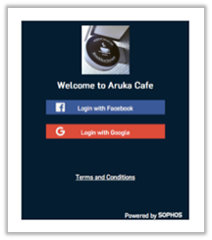
After connecting to your hotspot SSID, users will be redirected to be authenticated through the selected social media account and the landing page will look similar to the one shown in Image-3.
Image 3
Note: Google authentication through embedded browsers (captive portal pop-ups) will not work on iOS devices as Google has stopped their support for this (as can be seen by their announcement here). The workaround is for wireless users to use device browsers such as Chrome and Firefox.
This firmware release includes a number of bug fixes to improve the stability and reliability overall.
Bug Fixes
|
Issue Key |
Summary |
|
CWIFI-11183 |
Enhanced Synchronized Security policies in the event of a radio interface change |
|
CWIFI-11163 |
Improved stability on APX 530 |
|
CWIFI-10602 |
Addressed edge case where station doesn't connect to root access point when the non-root access point is offline (not powered up) |
|
CWIFI-10579 |
TCP SACK PANIC - Kernel vulnerabilities |
|
CWIFI-11069 CWIFI-11101 |
Enhanced proxy ARP and LLDP implementation |
Known Issues
|
Issue Key |
Summary |
|
CWIFI-11155 |
Rogue AP: Scanning the network for neighborhood access points in Rogue Access Point Detection may vary based on access point model (Due to limitations with memory) |
|
CWIFI-11202 |
Captive portal roaming across access points might not have auto pop-up from the embedded browser both in android and IOS powered devices Limitation: This is a limitation with the captive portal embedded design and applies to all Wi-Fi vendors. |
|
CWIFI-10343 |
Interoperability connection issues with Intel-8265 chipset (Windows 10) clients when “Fast Roaming” is enabled. Awaiting Intel driver updates for the clients |
|
CWIFI-10695 |
Captive Portal: iOS-based clients don't get captive portal auto pop-up for custom logo configuration. Limitation: as per Captive Portal Network Assist (CAN in iOS). Workaround: User should open the browser and try browsing to any http website to get the captive portal authentication page. |
| CWIFI-10648 | Social Login: Redirect to social login page is not supported by embedded browser support in Chrome in legacy Android devices.
Limitation: It is observed across all vendors. Workaround: User can authenticate to captive portal through other browsers like Mozilla Firefox, Opera, etc. |