Overview
We’re excited to announce the launch of Maintenance Release MR-5 (Version 1.5.2167) for the AP6 Series access points! This update comes packed with new features and bug fixes to improve your experience, and we can’t wait for you to try it out. Here's everything you need to know:
The MR5 firmware will be released in two phases.
Phase 1:
The firmware will initially be available for AP6s managed by Sophos Central Wireless in the EU-West Region. If you're in this region, you're first to receive the update.
Phase 2 (Coming Dec 10, 2024):
On December 10th, we’ll roll out the MR5 firmware to all other Sophos Central Wireless regions.
No worries if you're not in the EU-West Region and don’t want to wait for phase 2. You can manually download the MR5 firmware from Sophos Central. Simply go to the Devices > Installers page and find it under Wireless.
For step-by-step installation instructions, follow this guide: https://docs.sophos.com/nsg/wifi/help/en-us/UserManual/Advanced/UpdateFirmware/index.html.
New Features
The new features require MR5 firmware to be installed on AP6 Series access points before the features can be configured from Sophos Central.
Wireless Guest Network (NAT Mode): AP6 Series access points now offer wireless guest network (NAT Mode) capabilities. When enabled, the guest network creates an isolated network that uses the same AP6 access point and enforces traffic restrictions on the local network. In this configuration, the Guest Network SSID uses the DHCP server from the AP6, DNS is set from Central, and all traffic that originates from wireless devices connected to this SSID will be NATed to the local LAN IP address of the AP6. The guest network feature provides access to the internet but enforces traffic restrictions for all traffic trying to access the local network.
For more information on how to enable the wireless guest network feature from Sophos Central for the AP6 Series access points.
Power Statistics for AP6 Series access points
In Sophos Central on the Access Points page, a new menu item has been added called “Available Power.” This displays the power details for the individual access points under management and shows when the access point has the correct power settings or if there is insufficient power that needs to be corrected. 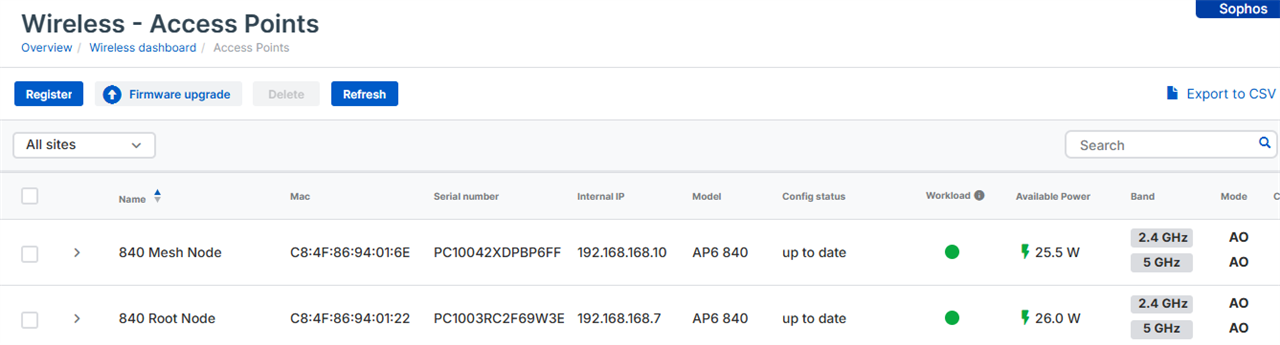
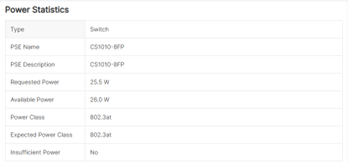
The power details are available in the local GUI for the AP6 Series access points and can be found on the Information>System Information page.
Additional Tool Tips, Alerts and Logs
The added tooltips are designed to inform the wireless administrators of different scenarios to be aware of before enabling specific features from Sophos Central. The added alerts and log messages improve reliability, troubleshooting, and general logging.
| Issue Key | Summary |
| WIFIX-7154 | In situations where radar interference is detected on one or more of the DFS channels broadcasting from the AP6, Central will provide an Alert recommending different channel selections to avoid Radar interference. The log messages are also generated and available on the local GUI of the AP6. |
| WIFIX-7153 | A new Tool Tip was added to Central for “Fast Roaming” to inform the administrator that wireless devices must support (802.11r/k/v) and adequate overlapping wireless cover across the area where the access points have been deployed is recommended. |
| WIFIX-7152 | A new Tool Tip was added to Central for “Band Steering” to ensure that the wireless administrator tunes the RSSI values to prevent wireless clients from getting discouraged from reconnecting to the access point automatically. |
| WIFIX-7148 | A new Tool Tip was added to Central for the AP6 420E manual channel selection to show that selecting channel 136 requires the AP6 420E to negotiate the LAN interface at 2.5 GbE vs 1 GbE. |
| WIFIX-6100 |
Local AP6 logging improvements. Added more log messages for Captive Portal. These messages include.
|
| WIFIX-5362 |
Local AP6 logging improvements. Added more log messages for LLDP. The messages include.
|
Power (LLDP) Enhancements
Enhancements to the LLDP power negotiation have been improved in MR5 to gracefully deal with power negotiation issues that may arise from using third-party PoE devices. Additionally, we’ve added power statistics to Sophos Central and the local AP6 GUI, while improving the local logging with additional LLDP log messages.
| Issue Key | Summary |
| WIFIX-6603 | We have had reports that LLDP power negotiation between AP6 access points and Aruba 6200M model Switches failed during the AP6 bootup process. |
|
WIFIX-5122 |
There was an LLDP negotiation issue between the AP6 420E and Aruba switch model Aruba-2540-48G-PoEP-4SFPP. |
Bug fixes
| Issue Key | Summary |
| WIFIX-7141 | When an SSID using WPA3 is configured from Central - it is mandatory that 802.11w is enabled on that SSID. In certain scenarios, Central would not set 802.11w, enabled. |
| WIFIX-6654 | Wireless clients that only support WPA2 are unable to roam successfully between access points where the SSID has 802.11r enabled and the encryption is set to WPA2/WPA3 mixed mode. |
| WIFIX-5212 | Wireless clients are unable to connect to SSIDs where the schedule availability has been configured, and the auto-scheduler has re-enabled the SSID. |
| WIFIX-5276 | Local AP6 GUI added the configuration options for encryption and authentication for SNMPv3. |
| WIFIX-5189 | We observed that framed IP is not sent in either accounting-start or accounting-update requests during radius AAA for radius-based accounting. |
| WIFIX-5057 | When Enterprise authentication (Radius) was enabled, we noticed the session timeout was causing wireless clients to drop from those SSIDs where this user authentication was used. |
| WIFIX-2927 | Radius server re-authentication is not working after the wireless user session timeout. |
| WIFIX-3645 | From Sophos Central if the administrator removes an IP address that has been configured in Walled Garden that IP is still displayed in the local GUI of the AP6. |
| WIFIX-3504 | From the local AP6 GUI, the WLAN client table displays the vendor’s name as unknown for Samsung devices. |
| WIFIX-3189 | From Sophos Central, if the administrator tries to set the channel bandwidth to 160 MHz on the AP6 840E, Central would return an error that it was unsupported. |
| WIFIX-5240 | SSIDs configured to use Captive Portal with social login with Google are not working. When a wireless user tries to authenticate with Google the web browser will display an error 400. |
| WIFIX-6674 | A roaming delay is seen when a wireless client roams between AP6 access points when using WAP-PSK as the authentication method. |
|
WIFIX-6729 |
We have seen an issue with DHCP IP assignment when multiple DHCP servers are set up to load balance DHCP requests. When multiple DHCP servers are set up to load balance the DHCP requests, load balancing does not happen because the "elapsed_time" parameter is not sent correctly by the AP6 access point. |
Known Issues
| Key Issue | Summary |
| WIFIX-7317 |
Guest Network SSIDs configured to use Guest Network NAT Mode and social login through Captive Portal are causing wireless clients to experience login failures. Workaround: Configure the Guest Network SSID to not use Guest Network NAT Mode and or select a different authentication method for Captive Portal authentication. |
| WIFIX-7286 |
When the AP6 is doing LLDP negotiation we have seen failures when the Power Sourcing Equipment (PSE) name/description is not configured. Workaround: Ensure the PSE has a valid name/description configured. |
For more known issues please visit https://doc.sophos.com/support/kil/index.html.
