Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This recommended read contains the troubleshooting steps & possible solutions when there’s an issue with OTP authentication.
This includes the following common scenarios such as:
- Unable to Authenticate a user(s) with OTP.
- OTP Stopped working.
- User unable to login
- SSL VPN user not authenticating.
Pre-requisites
Verify the OTP is Enabled
Go to Authentication> Multi-factor Authentication> One-time password [OTP]
- If the “Specific users and groups” option is selected, ensure the User Portal is included.
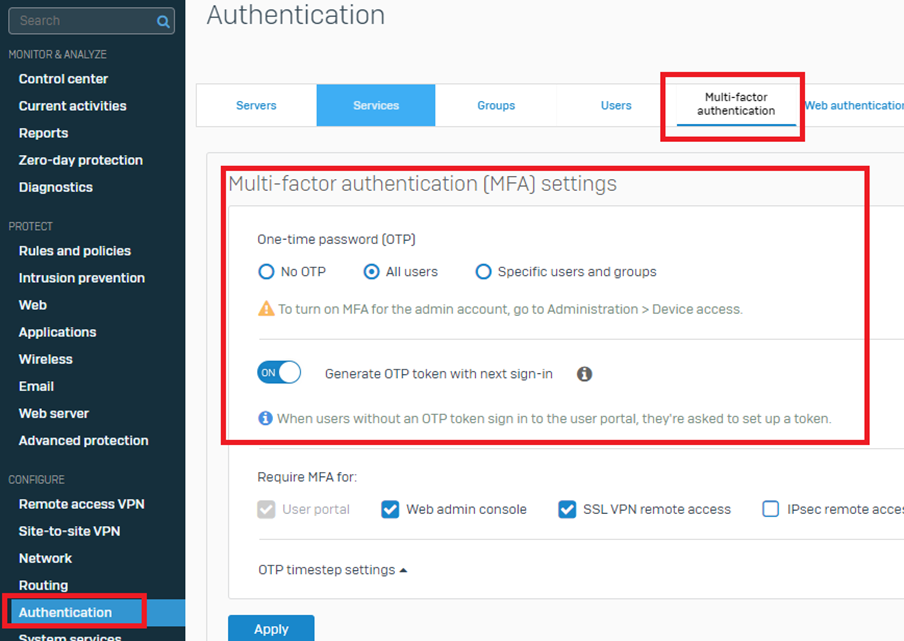
- Suppose the User has previously logged in to the user portal after enabling OTP. In that case, the User will be displayed under the issued token and auto-generated, as shown in the screenshot below.
Note: Make sure the status is turned on.
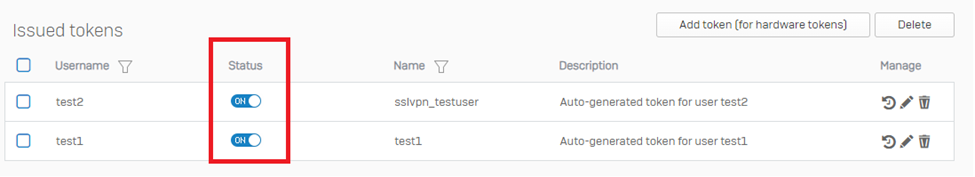
For additional Reference, kindly check the following KB
Troubleshooting Procedure
The User(s) is unable to authenticate using OTP
Step 1. Verify the QR Code
Once all the prerequisites for the OTP authentication are implemented, confirm whether you see a QR code upon logging into the user portal and use an authenticator application to generate the OTP.
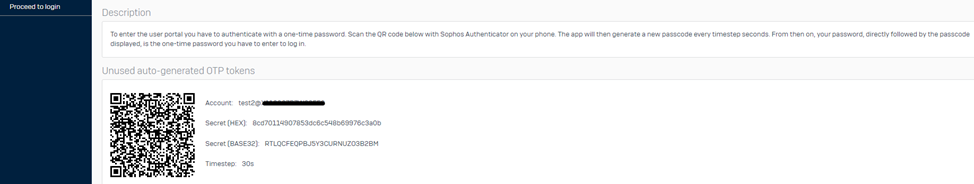
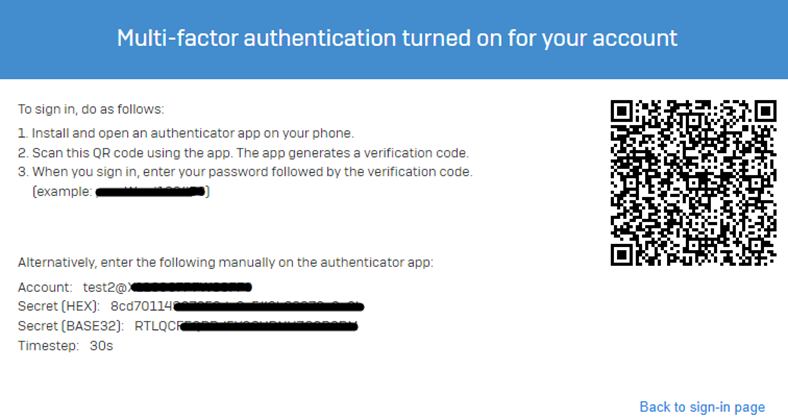
- If it displays a QR code, that means OTP isn’t yet registered to an Authenticator Application
For authenticator and MFA authentication, kindly see the reference:
Note: Sophos Authenticator reached the End of Life (EOL) on July 31, 2022. Users must use another authenticator application, such as the authenticator feature of Sophos Intercept X, Google Authenticator, or any other third-party application.
- Upon next login, proceed if you observe a failed Login error.

Step 2. Check Authentication Logs
- Verify on the authentication logs from Log Viewer> Set to Authentication.
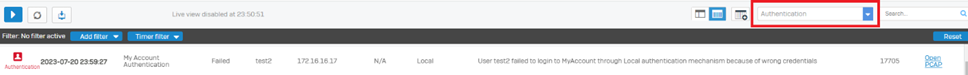
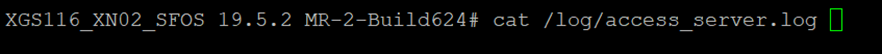
Log in via CLI> 5. Device Management > 3. Advance Shell> cat /log/access_server.log
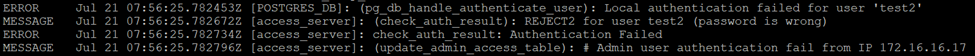
- Verify the authentication logs from Log Viewer> VPN.
SSL VPN Authentication Error
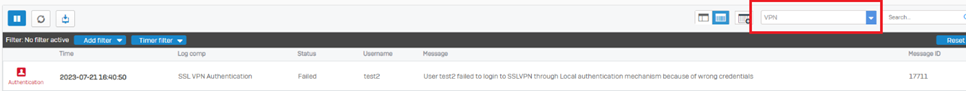
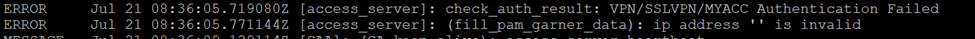
For Additional reference, kindly see Log Viewer.
- MAC Binding
Remove/Add MAC Binding on the user from Authentication>User>Username.
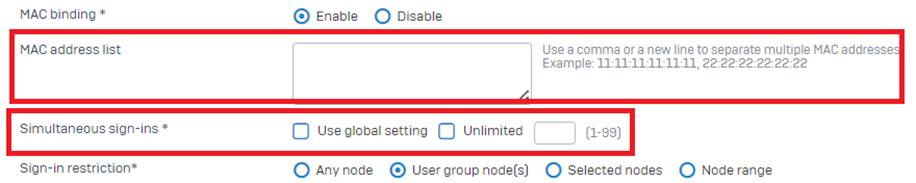
- Max Simultaneous Sign-in limit has been reached.
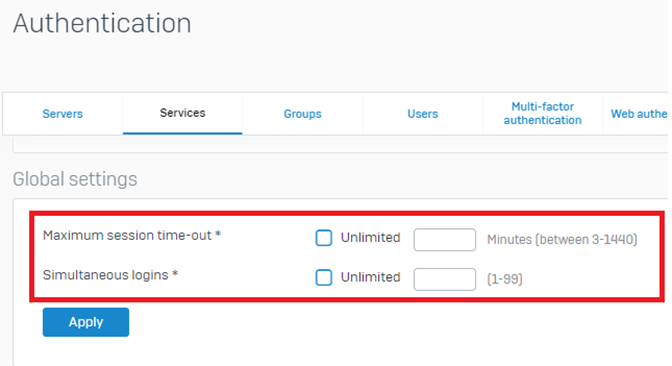
Increase the Simultaneous Login from Authentication>user>Username
Global Settings can be changed from Authentication>Services>Global Settings
Step 3. Time Differences
Verify if there’s any time difference between the device and Sophos Firewall.
Information related to the following:
- Default token timestep in seconds
- Maximum passcode offset steps
- Maximum initial passcode offset steps
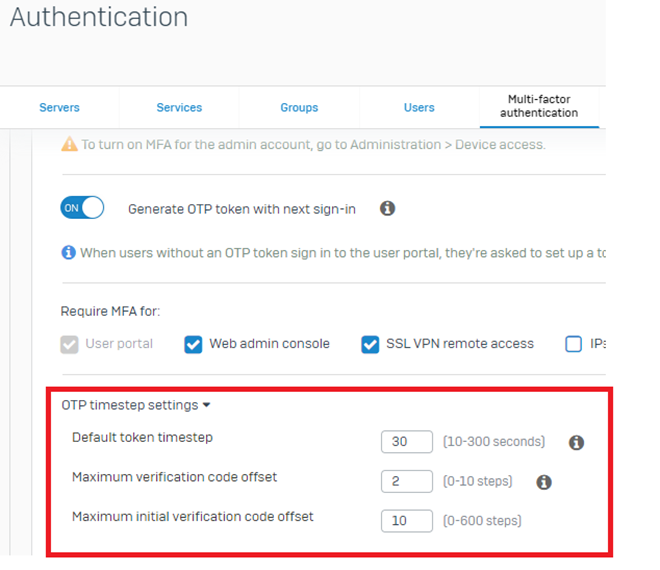
Kindly see the reference: Multi-factor authentication (MFA) settings
For Singe/few Users affected, the following steps are recommended.
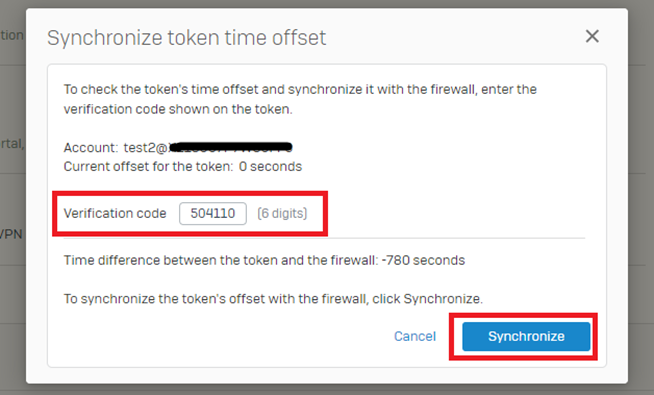
Synchronize the user(s) current token time offset as shown in the screenshot.
Under Authentication> Multi-factor Authentication> Issued Tokens> Click Synchronize token time offset.
Input the OTP passcode currently showing in the Authenticator, then click Synchronize.
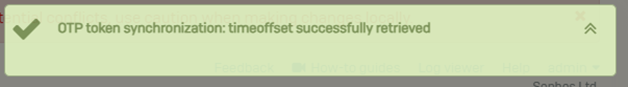
Upon successful synchronization, the following screenshot will appear on the upper portion of the screen.
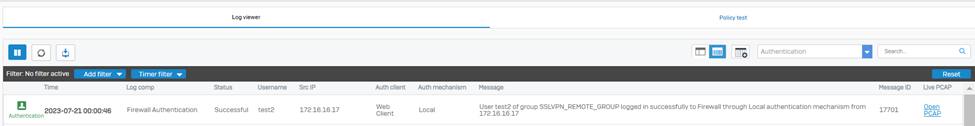
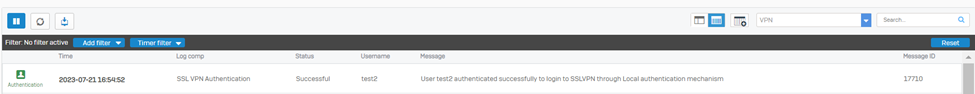
Successful Authentication Logs
- Authentication Log via Log Viewer
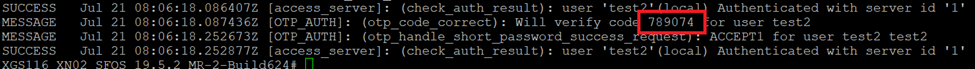
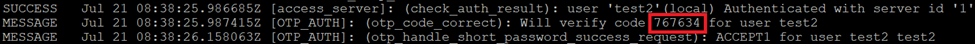
- Authentication Log via CLI
- OTP From Authenticator
Successful SSL VPN Authentication Log
- Authentication Log via Log Viewer
- Authentication Log via CLI
- OTP From Authenticator
Successful Login
updated links to latest
[edited by: Raphael Alganes at 10:41 AM (GMT -8) on 31 Dec 2024]

