Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended Read demonstrates the following
- How to turn on and configure multifactor authentication,
- Using Sophos Intercept X as an authenticator and list of 3rd-Party Authenticator
- How the OTP timestep settings can be configured.
Enabling Multifactor Authentication
Step1: Enabling Multi-factor authentication (MFA) settings
Under CONFIGURE > Authentication > Multi-factor authentication, then select the following
- One-time password (OTP): Specific users and groups
- Require MFA for User Portal

Step2: Initial Login
To get the Multi-Factor code, access the "User Portal" page, then log in with the user account that was used in the previous step.
Upon Login, you’ll receive a QR code that needs to be scanned by the User's Authenticator.
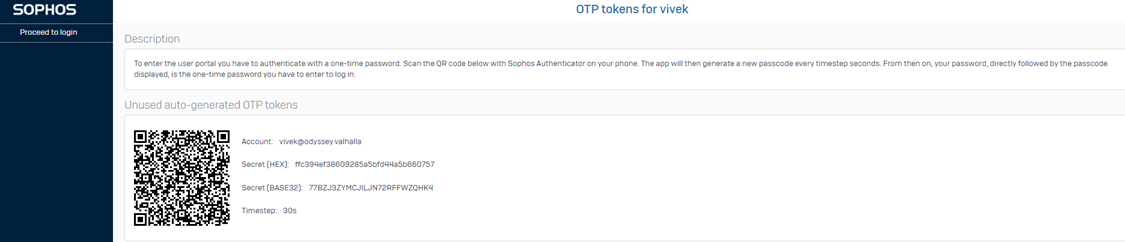 3rd-Party Authenticators
3rd-Party Authenticators
Kindly see the reference for a List of 3rd-Pary Authenticators
Sophos Intercept X for Mobile
Note: Sophos Authenticator reached the End of Life (EOL) on July 31, 2022. Users must use another authenticator application, such as the authenticator feature of Sophos Intercept X, Google Authenticator, or any other third-party application.
Step1: Download and install Sophos Intercept X for Mobile
On Playstore, search for the application – “Sophos Intercept X for Mobile” and install
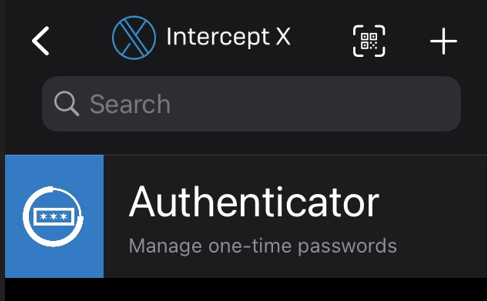
Step2: Using Intercept X as Authenticator
Once installed, open the application and swipe from left to right. You'll see the first option, " Authenticator."
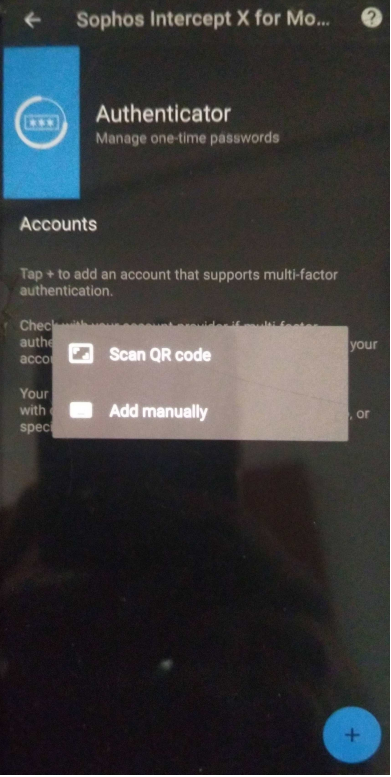
Click Authenticator, and on the bottom right, you can add > Scan QR code > on the user portal QR code page.
*For Apple Devices, Kindly download on AppStore and Install
Token Code Management
Once Scanned, it’ll immediately generate a 6-digit PIN, as displayed in the screenshot below: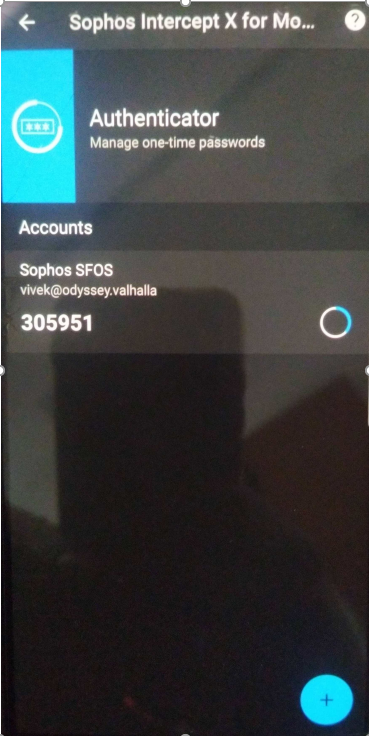
Then click Proceed to login option on the top left on the user portal page: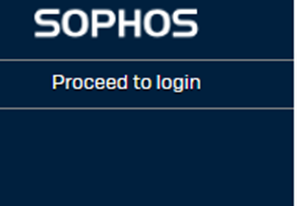
Log in with your credentials, and on the password, follow with the 6-digit pin displayed on your authenticator app, as illustrated in the screenshot below: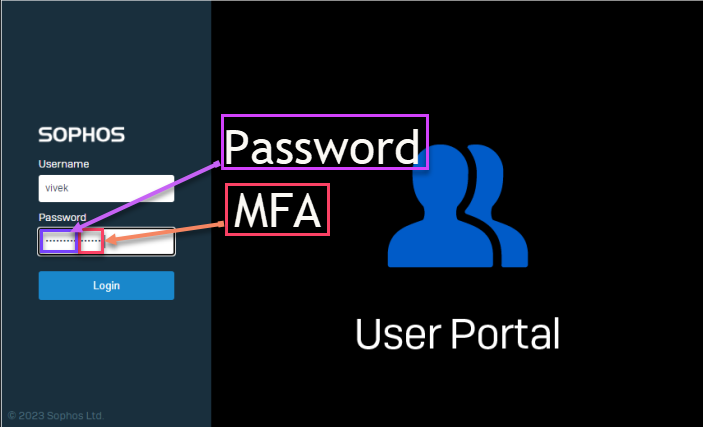
You’ll be logged into the user portal: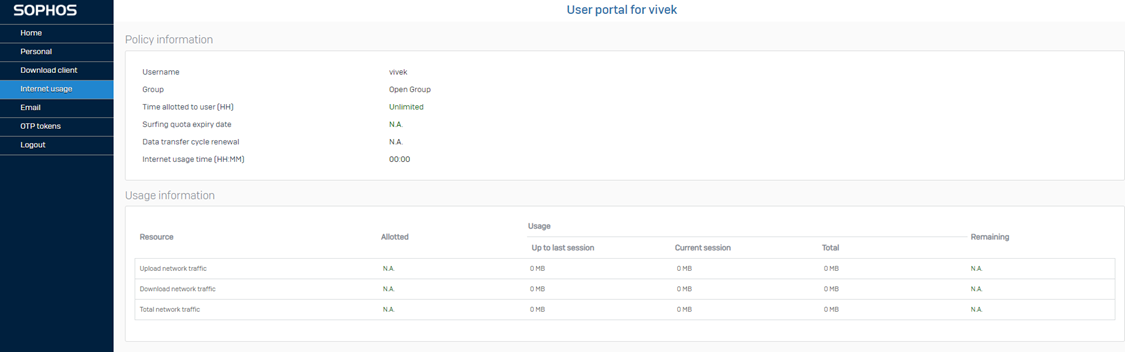
You can also check Issued tokens under the MFA section > Issued tokens.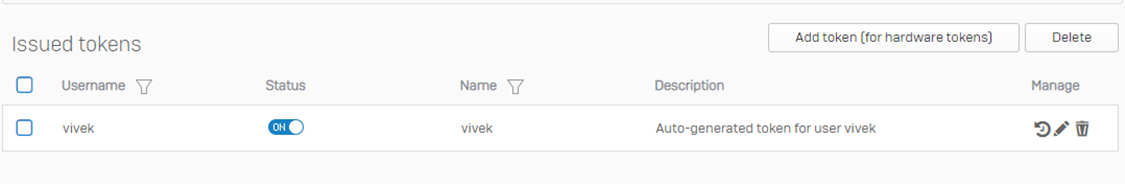
Understanding the OTP Timestep Settings
Considering the following settings:
#Default token timestep - 30s -->> This is a token/OTP validity before regenerating on your Sophos, G-Auth, or Microsoft authenticator.
#Maximum verification code offset - 3 -->> timesteps an earlier or later verification code remains valid. For example, if you specify a value of 3 and the timestep is 30 seconds, the client can use any passcode from the previous 90 seconds or the subsequent 90 seconds if the code wasn’t already used. [Number of passcodes outside of defined timestep that will be accepted]
#Maximum initial verification code offset: - 10.>> The maximum number of timesteps by which the clock of a token can drift between clients and server for the first sign-in only. This means if you set 10 steps, you'll restrict the clock of a token to drift no more than 10 seconds between two logins.
In the first authentication process, the token will be out of sync in an extreme way. Here, the admin can configure how many offset passcodes can be accepted. After successful authentication, the offset is aligned, which means that the next passcode of the token will be in sync.
Revamped
[edited by: Erick Jan at 3:23 AM (GMT -7) on 7 Oct 2025]
