Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
All Sophos Firewall (XGS, Virtual, Software, Azure, AWS) Firmware v18.0+
Sophos Firewall > Admin UI > Protect>Rules and Policies >
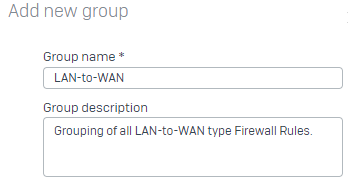
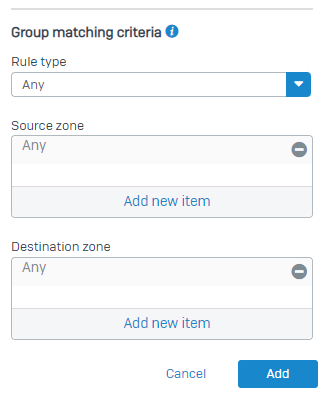 |
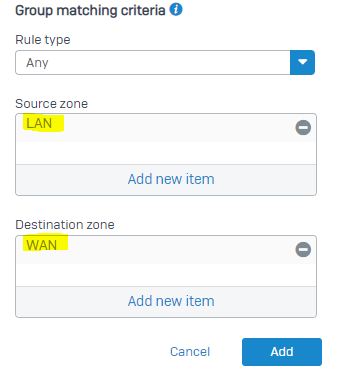 |
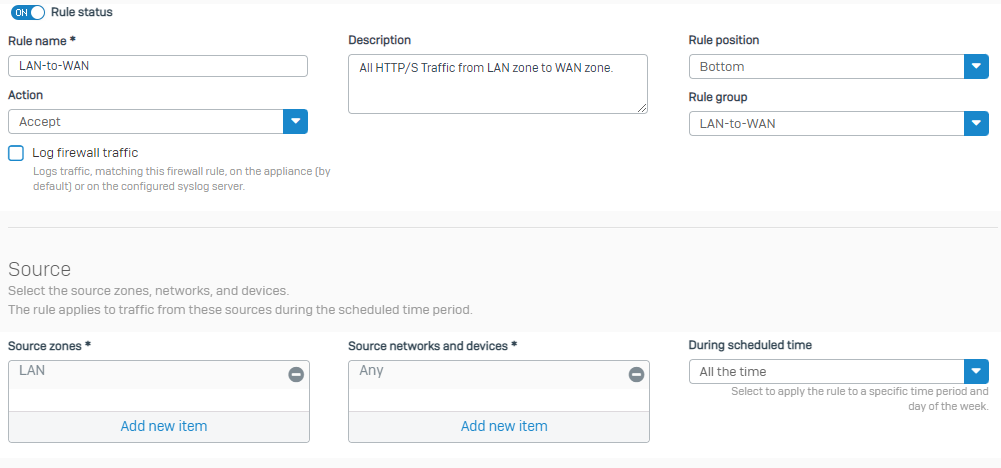
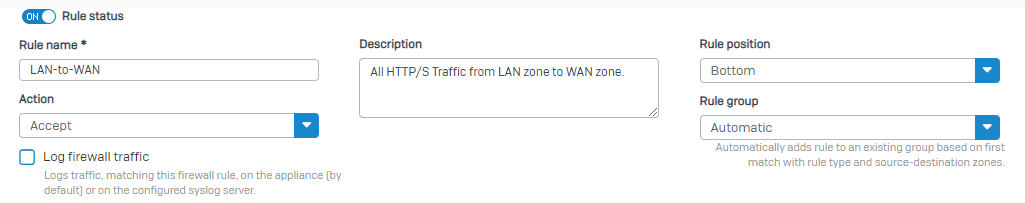
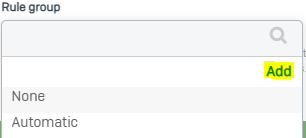
+1. Basically, a group for each Zone-Zone interaction that makes sense. (So Guest-to-WAN makes sense, but Guest-to-LAN doesn't.)
Definitely agree with you that there would never be a use case or rare for Guest-to-LAN, but there are times where a DMZ-to-LAN rule may be necessary, perhaps a maintenance window for access to a resource, zone separated backups, even a pinhole for accounting or authentication. In any situation, you weigh the need for the ability to do something like that, though vs how it impacts security.
In relation to the Rule Groups, at minimum if a rule was created like this, let's say by accident, it would ensure you had a group that gave you quick ability to identify and disable or modify as needed.
Thank you Matthew Ritchie for sharing!