Users may observe intermittent issues with our ticketing system, which may cause delays in processing case updates. While our teams actively work on a fix, please contact our Technical Support Hotline for any critical issues.
Users may observe intermittent issues with our ticketing system, which may cause delays in processing case updates. While our teams actively work on a fix, please contact our Technical Support Hotline for any critical issues.
Hello,
I am using an SSL certificate purchased from a provider for my SSL VPN configuration. This certificate is renewed annually, but when the certificate is renewed, the configuration is updated, and as a result, my users need to re-download the VPN configuration. Since the number of users is very high, this process significantly slows down my workflow.
What is the solution to avoid requiring users to re-download the VPN configuration each year after the certificate renewal? Is there a way to automate this process or handle configuration updates without impacting users?
Thank you for your assistance!
You could replace the VPN Portal Certificate with the public cert - do not replace the SSLVPN Signing cert - There is no benefit in doing it.
__________________________________________________________________________________________________________________
When I change the portal certificate, there is no need to download the configuration. But if I don't replace the VPN app's certificate with a new one, the VPN doesn't work.
What do you mean, the VPN does not work with the appliance certificate?
__________________________________________________________________________________________________________________
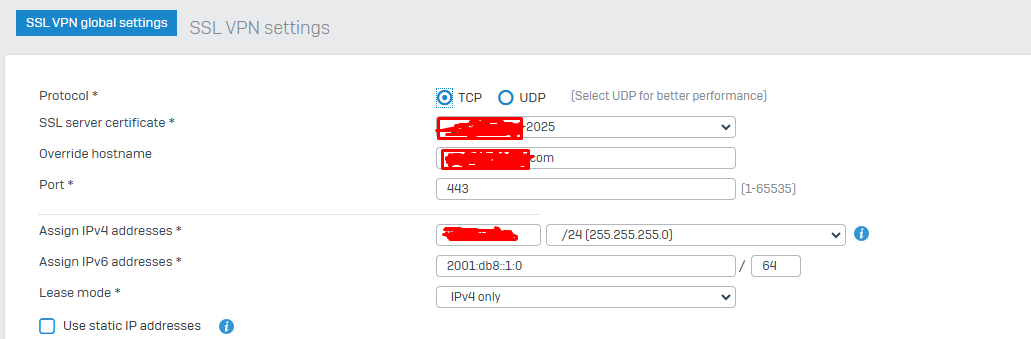
I'm talking about changing the certificate in this field.
Yes - Do not do this. It should work "forever" with the appliance default certificate, you are using. That is the basic settings for 99% of the customers.
__________________________________________________________________________________________________________________
Should I choose the Appliance Certificate one? If I choose this, will users need to add it manually to their computers?
Yes they will have to reload the certificate, it will break all existing VPNs, but this is a one time change, you would do and not be an yearly change.
By the way: Sophos Connect supports a provisioning file: https://docs.sophos.com/nsg/sophos-firewall/21.0/help/en-us/webhelp/onlinehelp/AdministratorHelp/RemoteAccessVPN/IPsecSSL/SophosConnect/RAVPNSConProvisioningFile/index.html
__________________________________________________________________________________________________________________
Having approximately 1000 users install certificates creates a lot of problems. :) there must be another solution
Again: Using the yearly certificate creates a profile, which is usable only a year - And there is no real benefit of doing it with a public signed certificate.
You need to switch it back to the appliance certificate, which is valid for a long time (15 years or so) and redeploy it. You could redeploy it by using the Provisionen file above.
If needed, you can also contact your Sophos Partner for more insights.
__________________________________________________________________________________________________________________
I understand, but it is not possible for me to distribute the device's CA private certificate (i.e. Appliance Certificate) to users' computers. Because users are customers working outside my network. Therefore, it is not possible for me to publish the certificate.
Why would you publish this?
Let me recap what is important:
1 User logins to VPN Portal: Here you use your public cert, as it is only the VPN Portal via HTTPS.
2 User downloads the OVPN File: Here you get the public key of the self-signed cert + a User cert + private key for user cert. (That is included in the OVPN).
3 User imports this OVPN into a VPN Client.
If you use Sophos Connect VPN Client, you could replace the step 1 & 2 with the provisioning file.
__________________________________________________________________________________________________________________
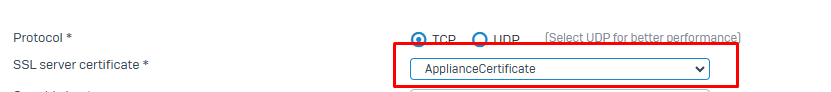
I repeat my question. When I choose this, do I need to manually add this CERTIFICATE to user computers?