Hi Support,
I hope someone can assist me. I've recently encountered an issue where some websites fail to load, displaying the error "ERR_CONNECTION_RESET."
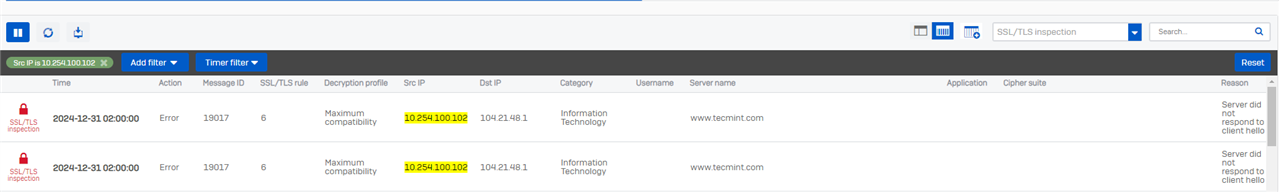
Upon reviewing the log viewer, the issue is tagged under SSL/TLS Inspection with the following details:
ACTION: Error
Reason: Server did not respond to client hello
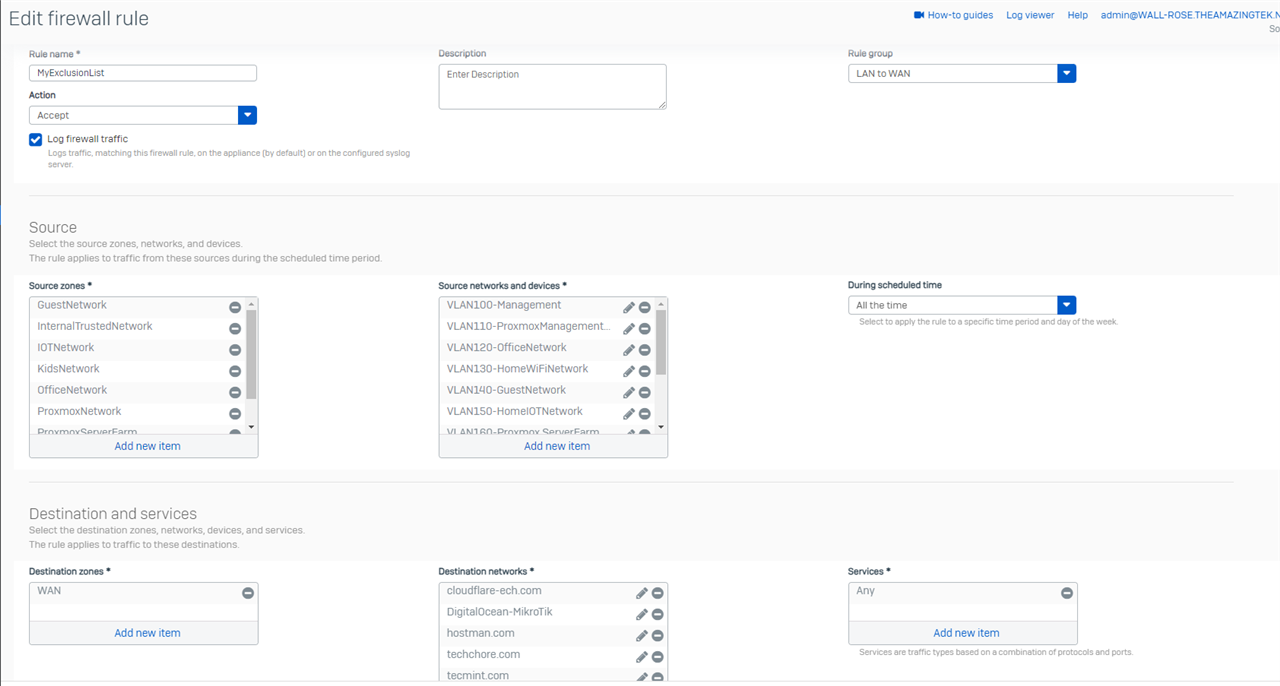
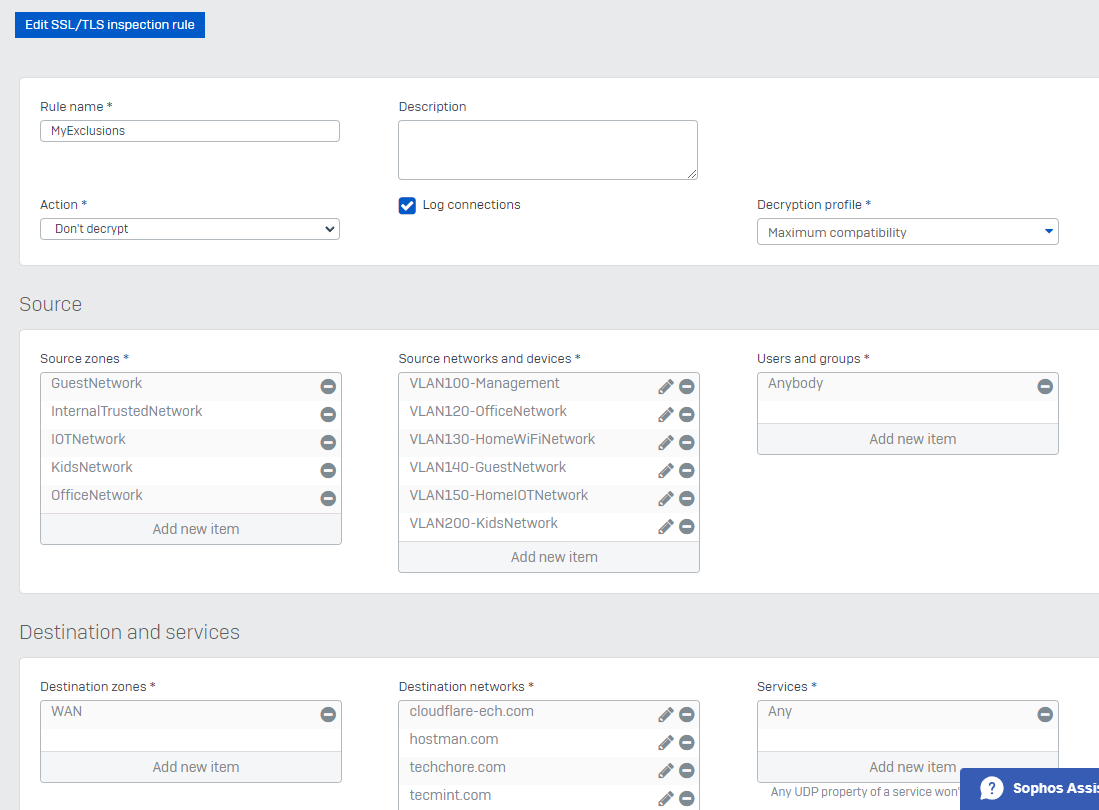
I have tried exempting these sites in the Firewall Rules and SSL/TLS settings, but the error "ERR_CONNECTION_RESET" persists.
Firewall Rules:
SSL/TLS:
Below are the affected sites:
I'm using Sophos Home Firewall running SFOS 21.0.0 GA-Build169
Looking forward to your guidance.