I am testing a new XGS 136 (SFOS 20.0.0 GA-Build222) offsite to replace an onsite XG 135 (SFOS 19.0.2 MR-2-Build472). The backup of the XG 135 was used to setup the XGS 136.
We have never used the IPsec Site-to-Site connection before but may have a use for it further down the line. Therefore, before I put the new unit into production I thought I would take the opportunity to test the Site-to-Site feature. However, I cannot initiate the connection. Here are the settings that I have (note that the local and remote ID are the same email address on both ends).
Head Office Settings on XG 135
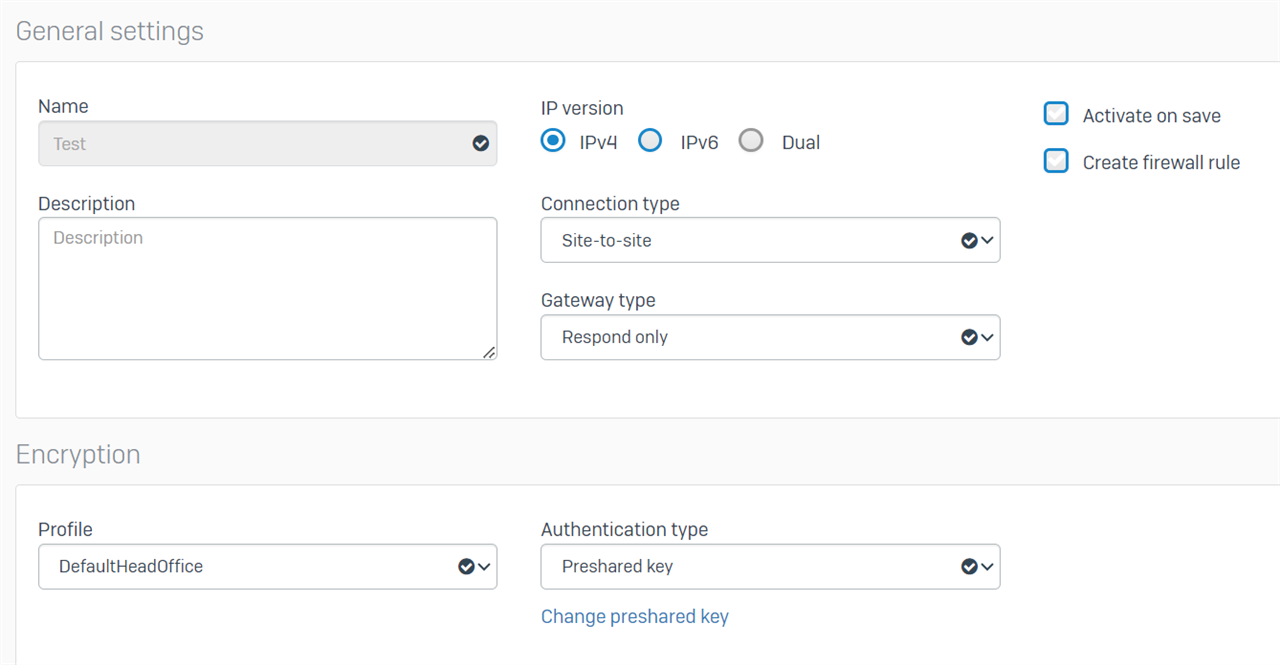
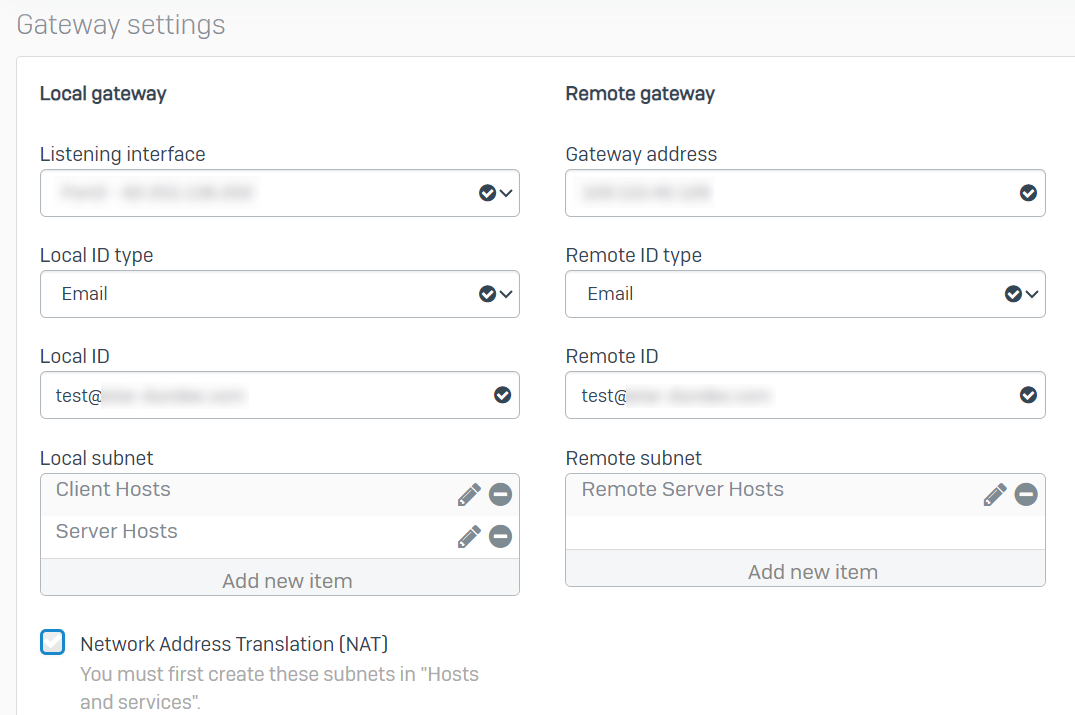
Branch Office Settings
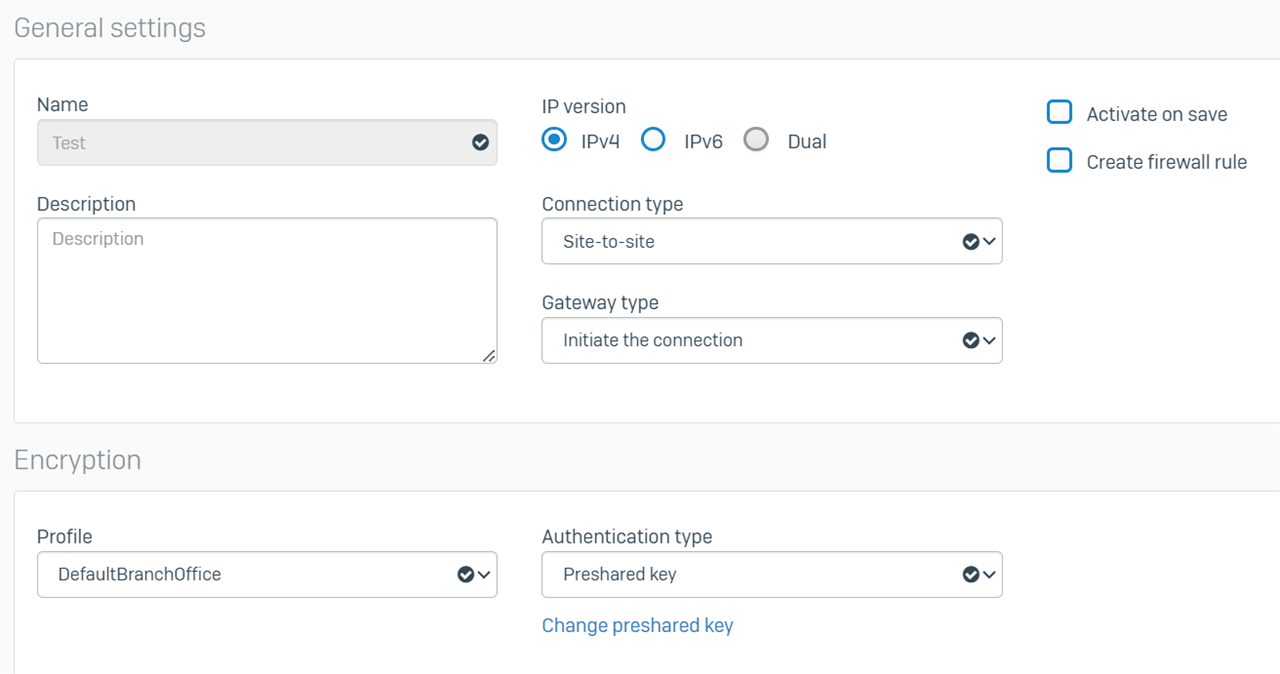
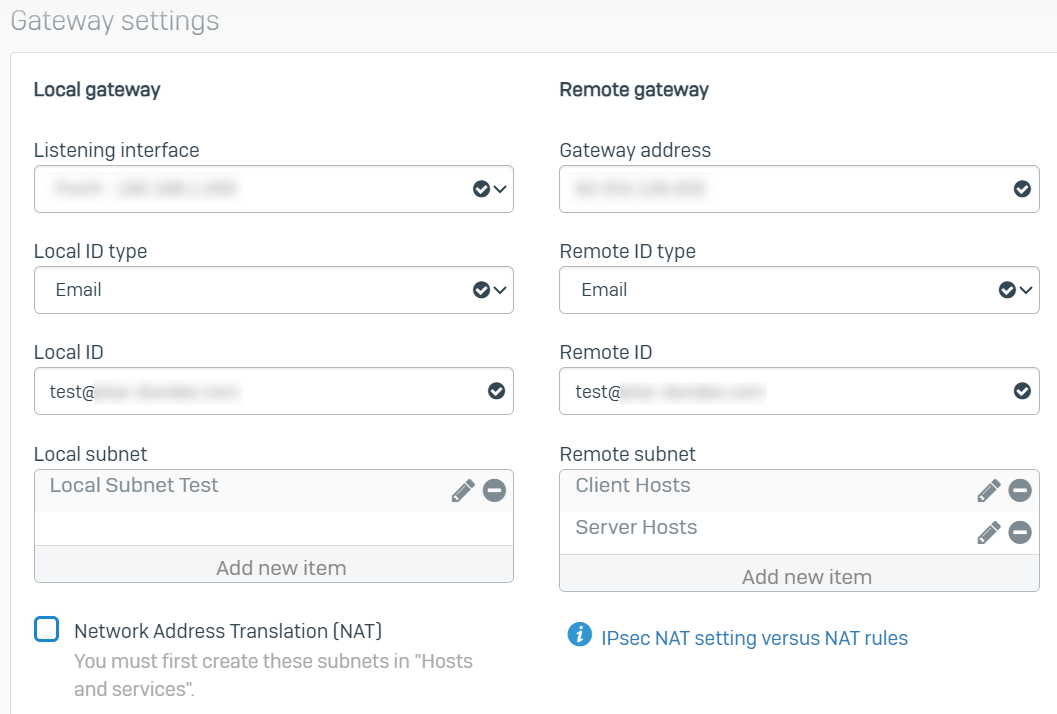
I can successfully activate both ends of the connection.
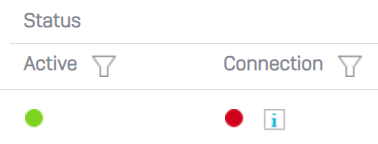
However, when I try to connect on either end, I get the following error.
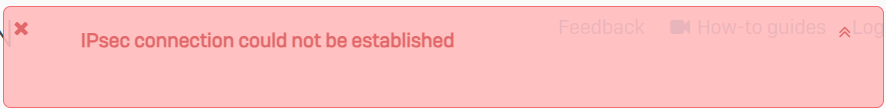
I checked /log/strongswan.log on the branch end and got the following "KE payload missing in message" and UNSUPPORTED_CRITICAL_PAYLOAD errors:
2024-04-10 07:55:02Z 06[CFG] vici initiate 'Test-1'
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> ### queue_child invoking quick_mode_create
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> ### quick_mode_create: 0x7fe3a4002650 config 0x7fe3bc0038c0
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> initiating Main Mode IKE_SA Test-1[55] to HEAD_OFFICE_IP_ADDRESS
2024-04-10 07:55:02Z 15[ENC] <Test-1|55> generating ID_PROT request 0 [ SA V V V V V V ]
2024-04-10 07:55:02Z 15[NET] <Test-1|55> sending packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (548 bytes)
2024-04-10 07:55:02Z 17[NET] <56> received packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (548 bytes)
2024-04-10 07:55:02Z 17[ENC] <56> parsed ID_PROT request 0 [ SA V V V V V V ]
2024-04-10 07:55:02Z 17[IKE] <56> received XAuth vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received DPD vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received Cisco Unity vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received FRAGMENTATION vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received NAT-T (RFC 3947) vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> BRANCH_IP_ADDRESS is initiating a Main Mode IKE_SA
2024-04-10 07:55:02Z 17[ENC] <56> generating ID_PROT response 0 [ SA V V V V V ]
2024-04-10 07:55:02Z 17[NET] <56> sending packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (180 bytes)
2024-04-10 07:55:02Z 16[NET] <56> received packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (180 bytes)
2024-04-10 07:55:02Z 16[ENC] <56> parsed ID_PROT request 0 [ SA V V V V V ]
2024-04-10 07:55:02Z 16[IKE] <56> received XAuth vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received DPD vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received Cisco Unity vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received FRAGMENTATION vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received NAT-T (RFC 3947) vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> KE payload missing in message
2024-04-10 07:55:02Z 16[ENC] <56> generating INFORMATIONAL_V1 request 102214803 [ N(CRIT) ]
2024-04-10 07:55:02Z 16[NET] <56> sending packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (56 bytes)
2024-04-10 07:55:02Z 27[NET] <Test-1|55> received packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (56 bytes)
2024-04-10 07:55:02Z 27[ENC] <Test-1|55> parsed INFORMATIONAL_V1 request 102214803 [ N(CRIT) ]
2024-04-10 07:55:02Z 27[IKE] <Test-1|55> informational: received UNSUPPORTED_CRITICAL_PAYLOAD error notify
2024-04-10 07:55:02Z 27[IKE] <Test-1|55> ### destroy: 0x7fe3a4002650
Can anyone spot any obvious issues?
Hey Alan Spark ,
Thank you for reaching out to the community, here it seems we are receiving from the remote end site, maybe the peer wasn't able to decrypt the message properly, or it didn't like one of the payloads (e.g. because it was configured not to use PFS and didn't expect a KE payload). Can you please share the IPsec policy being used both at the local and remote end here ?
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Hi Vivek,
Thanks for your quick response. I assume by policy, you mean profile? Here are the settings of the DefaultHeadOffice and DefaultBranchOffice profiles that I am using at each end.
Head Office
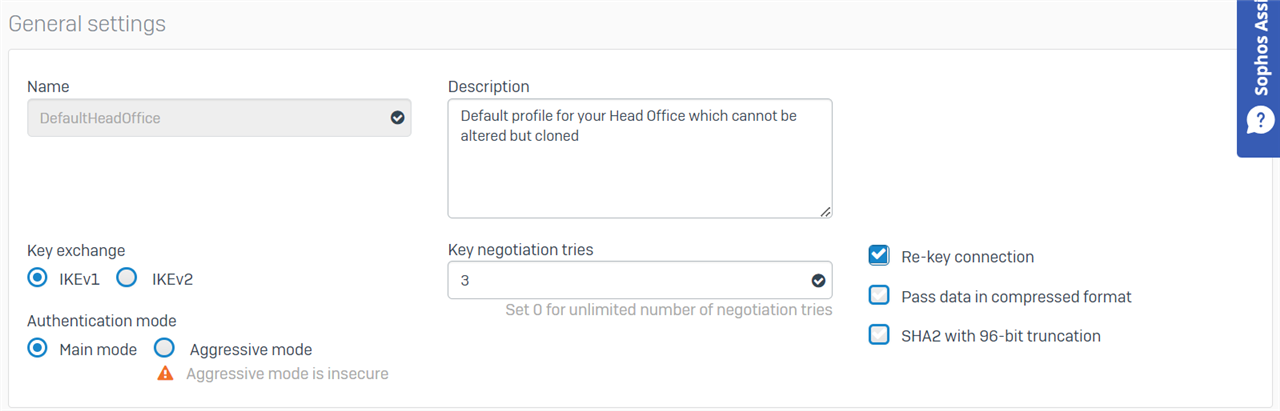
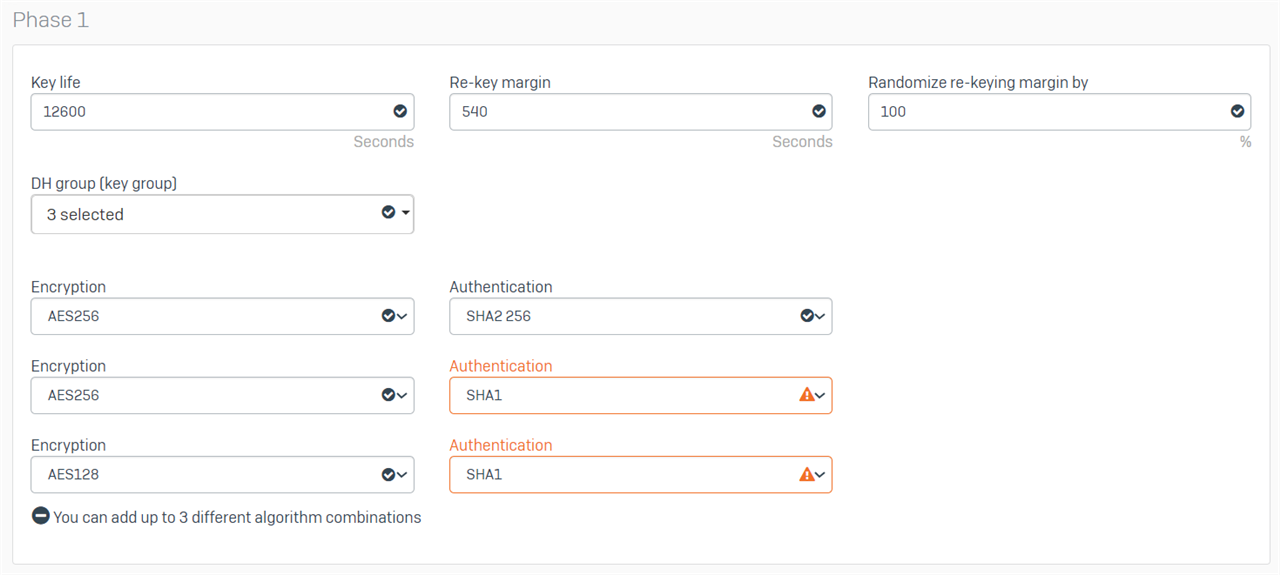
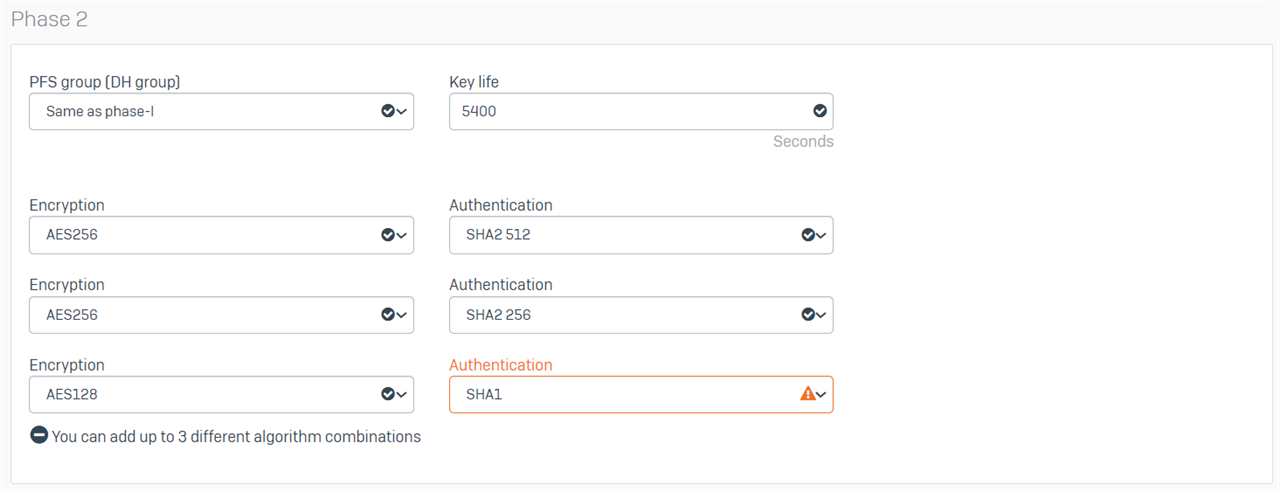
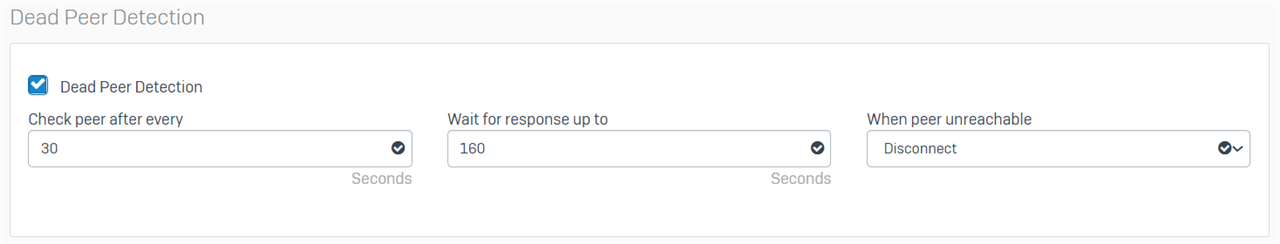
Branch Office
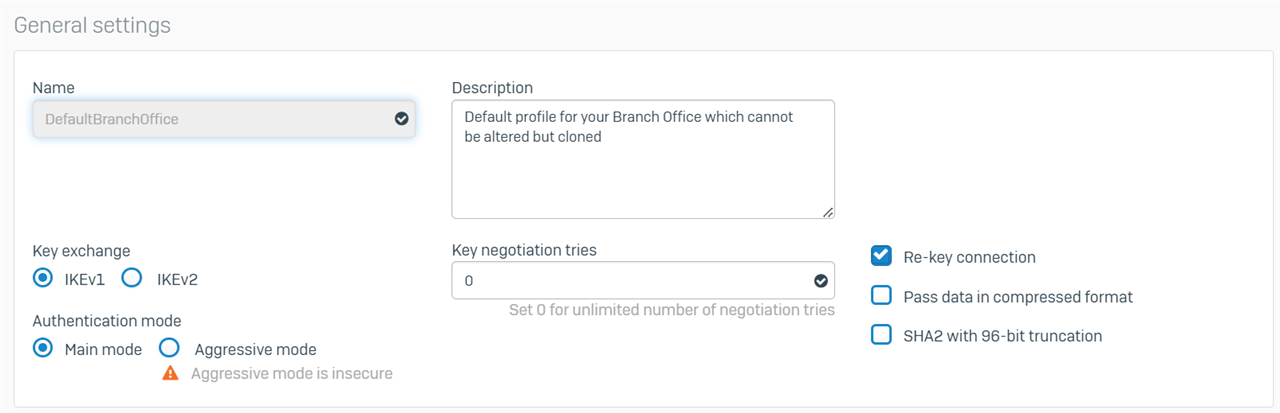
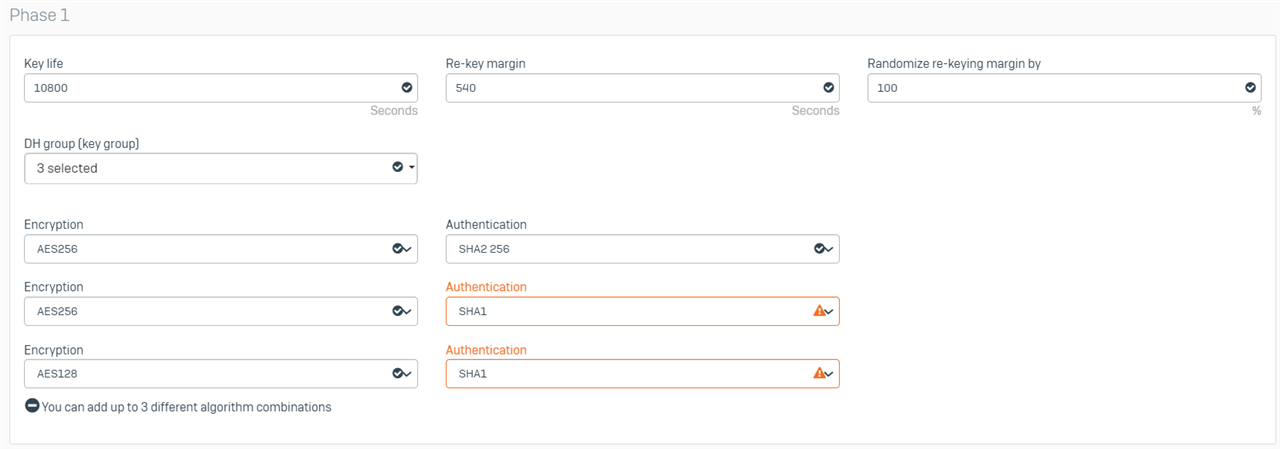
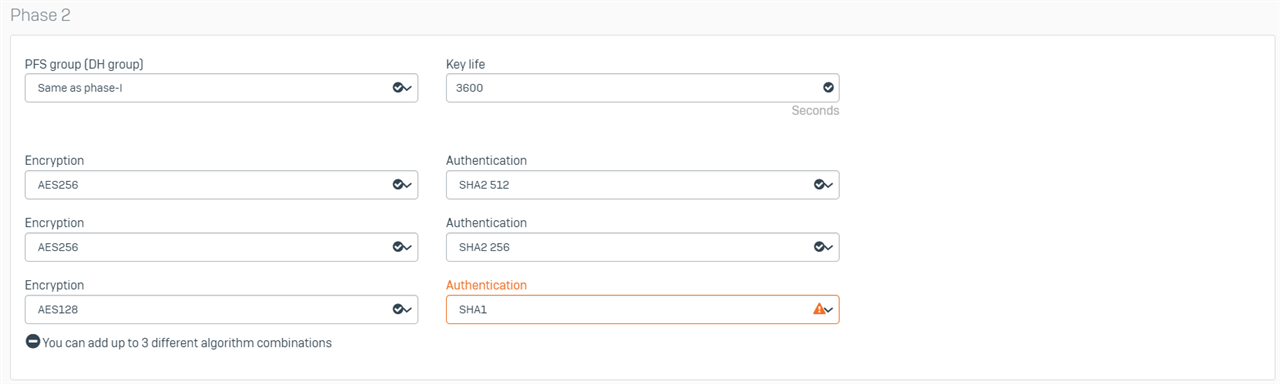
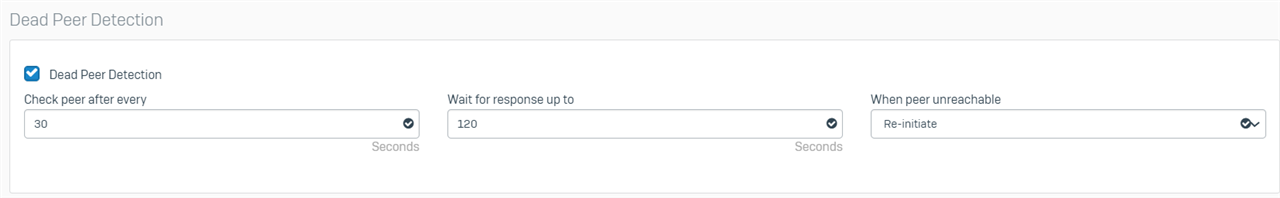
Regards,
Alan
Yea that's correct Alan Spark , instead of using default profiles, use the following custom at both the ends and let us know if this helps: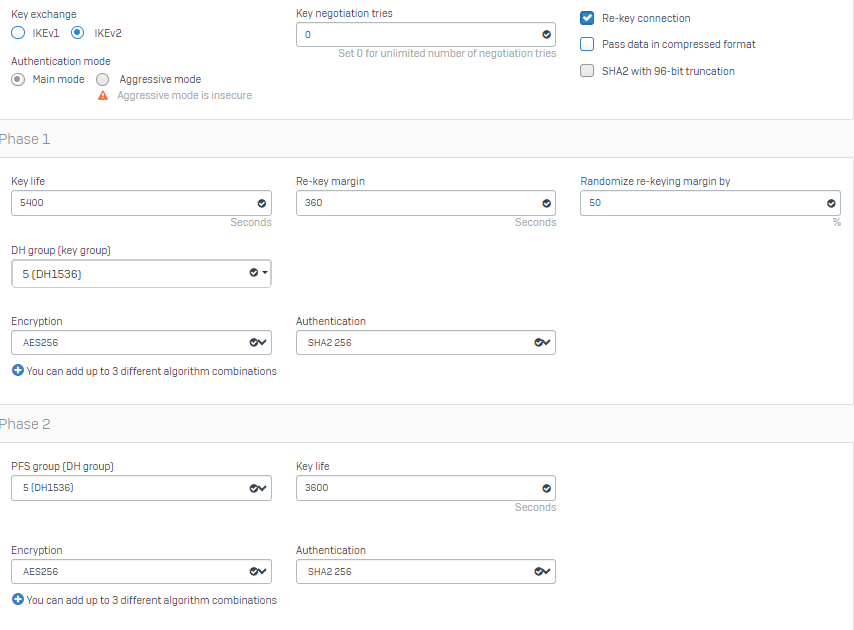
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Seems port 500 is blocked from ISP router
please check tcpdump with SSH option 4
console>tcpdump ‘port 500
run the above command on both sophos xg firewall
"Sophos Partner: Networkkings Pvt Ltd".
If a post solves your question please use the 'Verify Answer' button.
Hi Vivek,
I have configured the custom profiles and that seemed to get a bit further.
Head Office
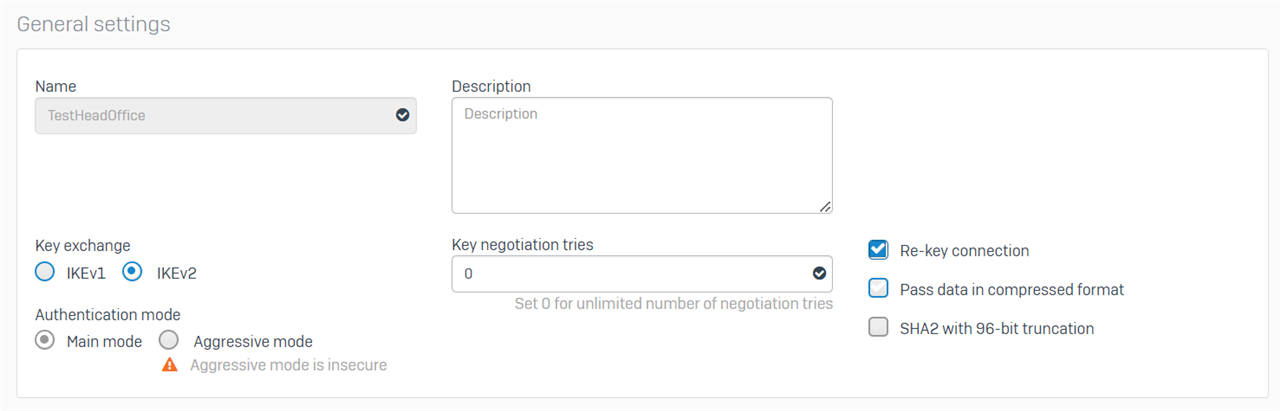
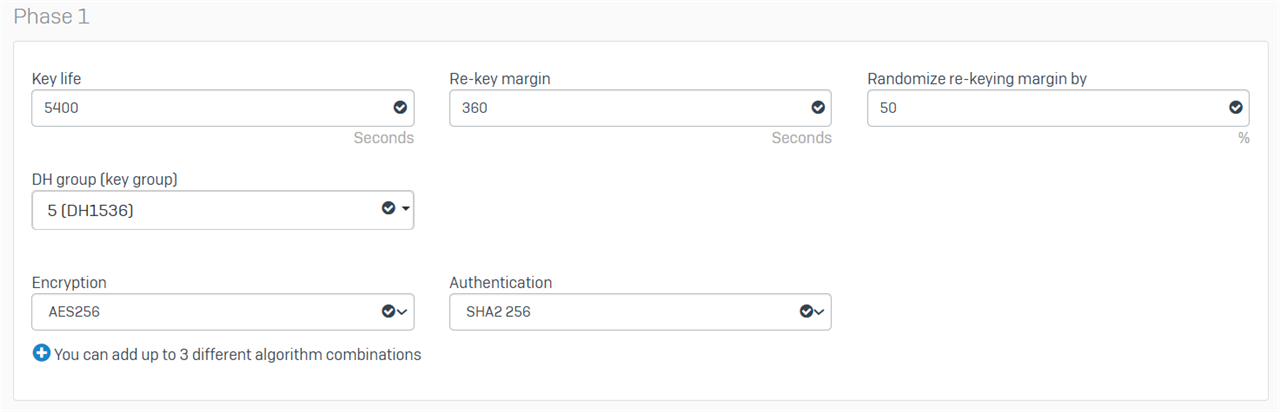
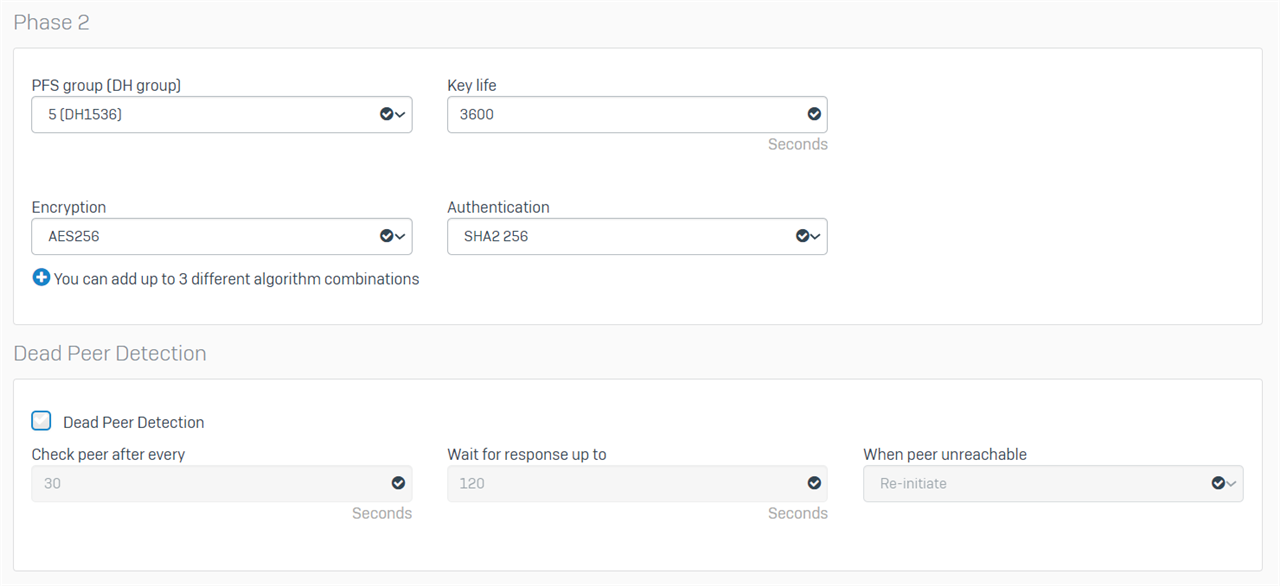
Branch Office
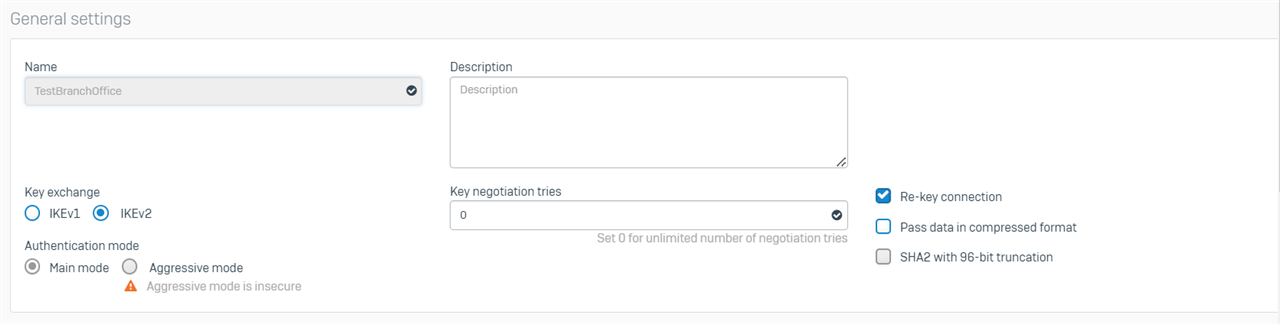
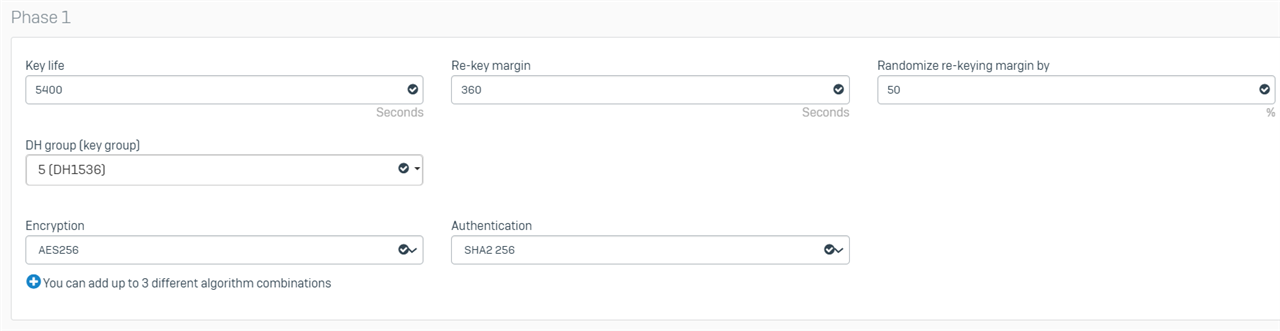
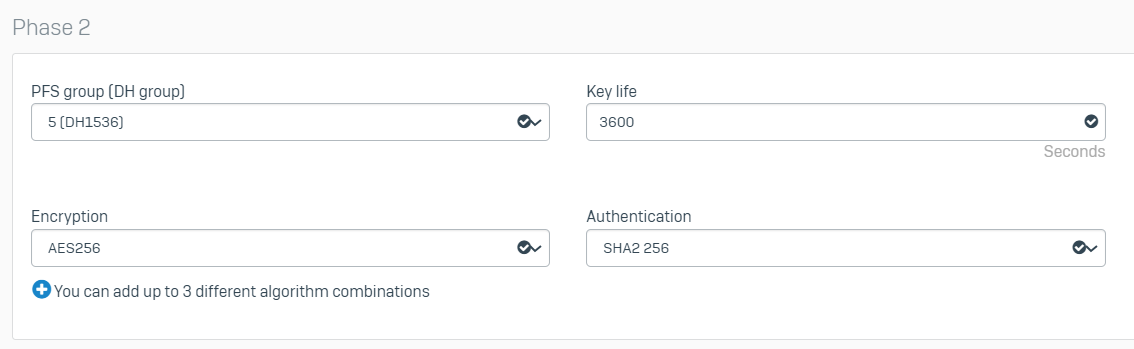
Here is the latest strongswan.log from the branch:
2024-04-10 09:45:31Z 06[CFG] vici initiate 'Test-1'
2024-04-10 09:45:31Z 04[IKE] <Test-1|14> initiating IKE_SA Test-1[14] to HEAD_OFFICE_IP_ADDRESS
2024-04-10 09:45:31Z 04[ENC] <Test-1|14> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
2024-04-10 09:45:31Z 04[NET] <Test-1|14> sending packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (858 bytes)
2024-04-10 09:45:31Z 13[NET] <15> received packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (858 bytes)
2024-04-10 09:45:31Z 13[ENC] <15> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
2024-04-10 09:45:31Z 13[IKE] <15> no IKE config found for HEAD_OFFICE_IP_ADDRESS...BRANCH_IP_ADDRESS, sending NO_PROPOSAL_CHOSEN
2024-04-10 09:45:31Z 13[ENC] <15> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
2024-04-10 09:45:31Z 13[NET] <15> sending packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (36 bytes)
2024-04-10 09:45:31Z 15[NET] <Test-1|14> received packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (36 bytes)
2024-04-10 09:45:31Z 15[ENC] <Test-1|14> parsed IKE_SA_INIT response 0 [ N(NO_PROP) ]
2024-04-10 09:45:31Z 15[IKE] <Test-1|14> received NO_PROPOSAL_CHOSEN notify error
2024-04-10 09:45:31Z 15[DMN] <Test-1|14> [GARNER-LOGGING] (child_alert) ALERT: IKE SA proposals don't match. Check the phase 1 policy settings on both devices: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048
2024-04-10 09:45:31Z 15[IKE] <Test-1|14> IKE_SA NO_PROPOSAL_CHOSEN set_condition COND_START_OVER
2024-04-10 09:45:31Z 15[IKE] <Test-1|14> IKE_SA has_condition COND_START_OVER retry initiate in 60 sec
Hi, I'm not sure this is the case. As Vivek Jagad said above, it seems there is a response from the remote end and changing to the custom profiles has made a difference. Port 500 is definitely open in my home router but I don't have any control over the remote end.
However, I did try your tcpdump command but saw no output and it took me to a > console that I couldn't Ctrl+C from.
based on the logs - NO_PROPOSAL_CHOSEN : looks there is a mismatch of proposals during phase 1 or phase 2 negotiation between a site-to-site VPN.
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Thanks Vivek Jagad . What do you think could be the cause of the mismatch? I am sure I made the profiles exactly the same.
what about the pre-shared key, can you double check that too ?
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Vivek Jagad I re-entered the preshared key at both ends and double checked that they match. No difference.
Still it shows the same error in the strongswan logs ?
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Yes, still the same:
2024-04-10 13:07:40Z 09[CFG] vici initiate 'Test-1'
2024-04-10 13:07:40Z 29[IKE] <Test-1|85> initiating IKE_SA Test-1[85] to HEAD_OFFICE_IP
2024-04-10 13:07:40Z 29[ENC] <Test-1|85> generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
2024-04-10 13:07:40Z 29[NET] <Test-1|85> sending packet: from BRANCH_OFFICE_IP[500] to HEAD_OFFICE_IP[500] (858 bytes)
2024-04-10 13:07:40Z 02[NET] <86> received packet: from BRANCH_OFFICE_IP[500] to HEAD_OFFICE_IP[500] (858 bytes)
2024-04-10 13:07:40Z 02[ENC] <86> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ]
2024-04-10 13:07:40Z 02[IKE] <86> no IKE config found for HEAD_OFFICE_IP...BRANCH_OFFICE_IP, sending NO_PROPOSAL_CHOSEN
2024-04-10 13:07:40Z 02[ENC] <86> generating IKE_SA_INIT response 0 [ N(NO_PROP) ]
2024-04-10 13:07:40Z 02[NET] <86> sending packet: from HEAD_OFFICE_IP[500] to BRANCH_OFFICE_IP[500] (36 bytes)
2024-04-10 13:07:40Z 06[NET] <Test-1|85> received packet: from HEAD_OFFICE_IP[500] to BRANCH_OFFICE_IP[500] (36 bytes)
2024-04-10 13:07:40Z 06[ENC] <Test-1|85> parsed IKE_SA_INIT response 0 [ N(NO_PROP) ]
2024-04-10 13:07:40Z 06[IKE] <Test-1|85> received NO_PROPOSAL_CHOSEN notify error
2024-04-10 13:07:40Z 06[DMN] <Test-1|85> [GARNER-LOGGING] (child_alert) ALERT: IKE SA proposals don't match. Check the phase 1 policy settings on both devices: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048
2024-04-10 13:07:40Z 06[IKE] <Test-1|85> IKE_SA NO_PROPOSAL_CHOSEN set_condition COND_START_OVER
2024-04-10 13:07:40Z 06[IKE] <Test-1|85> IKE_SA has_condition COND_START_OVER retry initiate in 60 sec