Hello,
I am still relatively new with Sophos products. I've got a Radius server set up to authenticate users to the admin interface, but it's not working. I've reviewed the documentation several times and am unable to determine what I'm missing. I feel like there's one piece that I haven't enabled, yet I cannot find it.
This is on a Sophos XGS116 running SFOS 19.5.3 MR-3 Build 652.
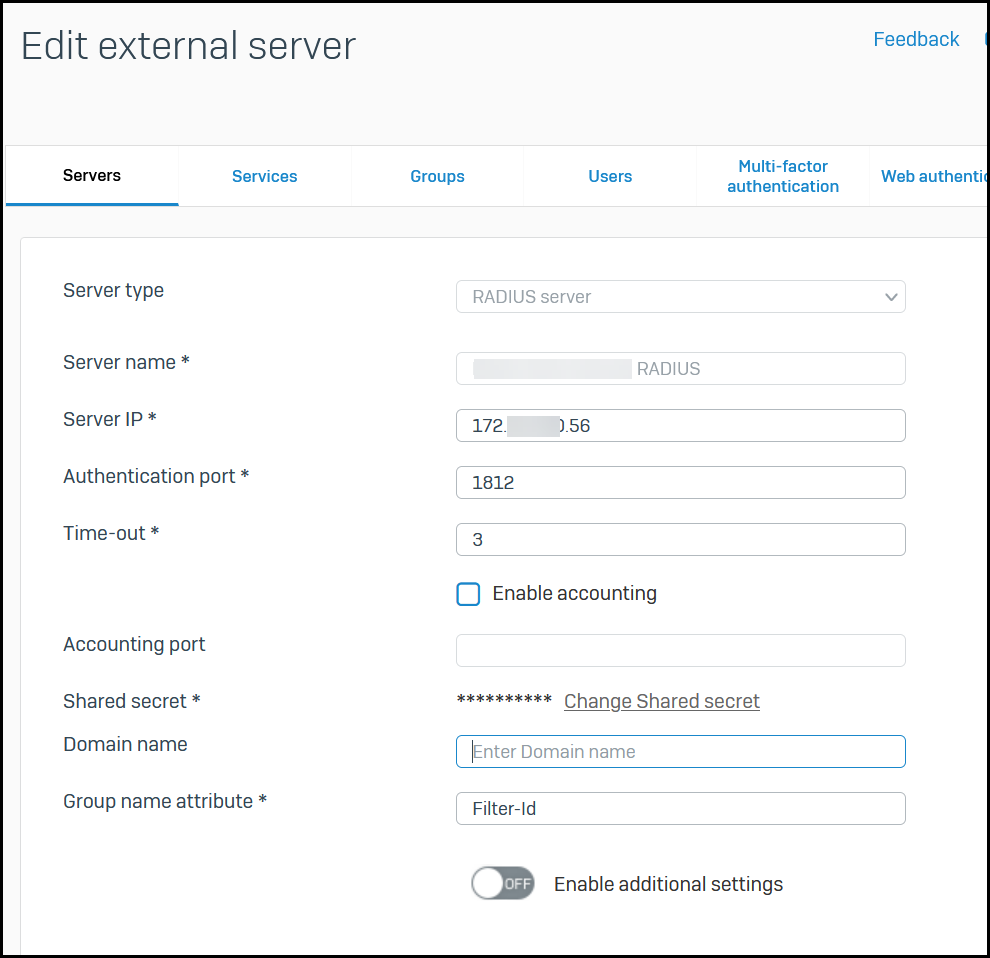
I went to Authentication -> Servers and
- Added a new authentication server - type RADIUS
- Provided a name
- IP address
- Authentication port (1812)
- Timeout is set to 3 seconds
- Accounting is not enabled
- Shared secret specified
- Domain Name is blank - this Radius server is not IAS and is not configured with Active Directory - it's a Steel Belted Radius server that's using a local database
- Group Name Attribute is set to "Filter-Id" (without the double quotes)
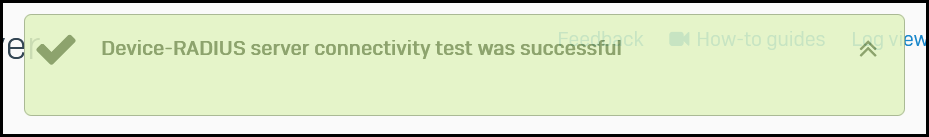
When I select Test connection, I see "Device-RADIUS server connectivity test was successful"
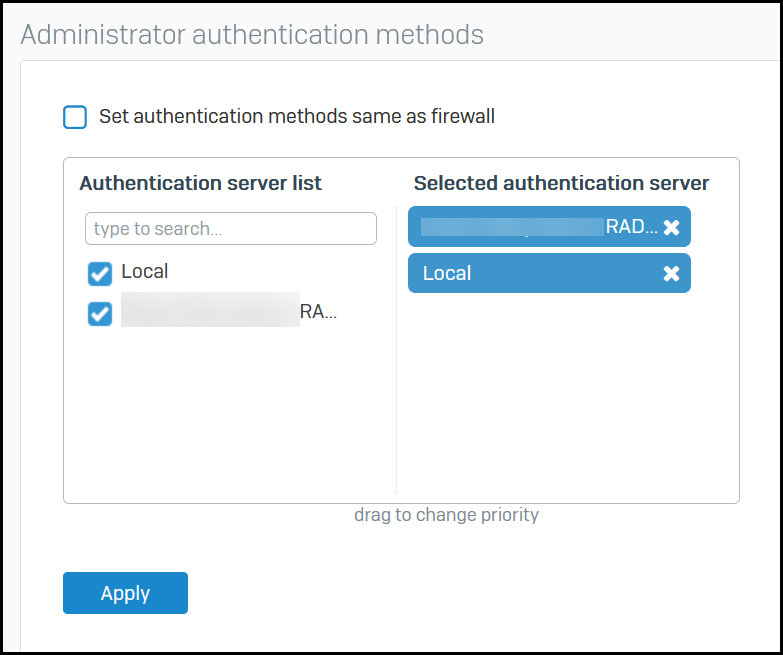
Next, I went to Authentication -> Services
Under Administrator Authentication Methods, I have both Local and the Radius server selected
Dragged and dropped the order of the auth servers such that the Radius server is first in the list
I attempted to log in with the same credentials I used when testing the connection.
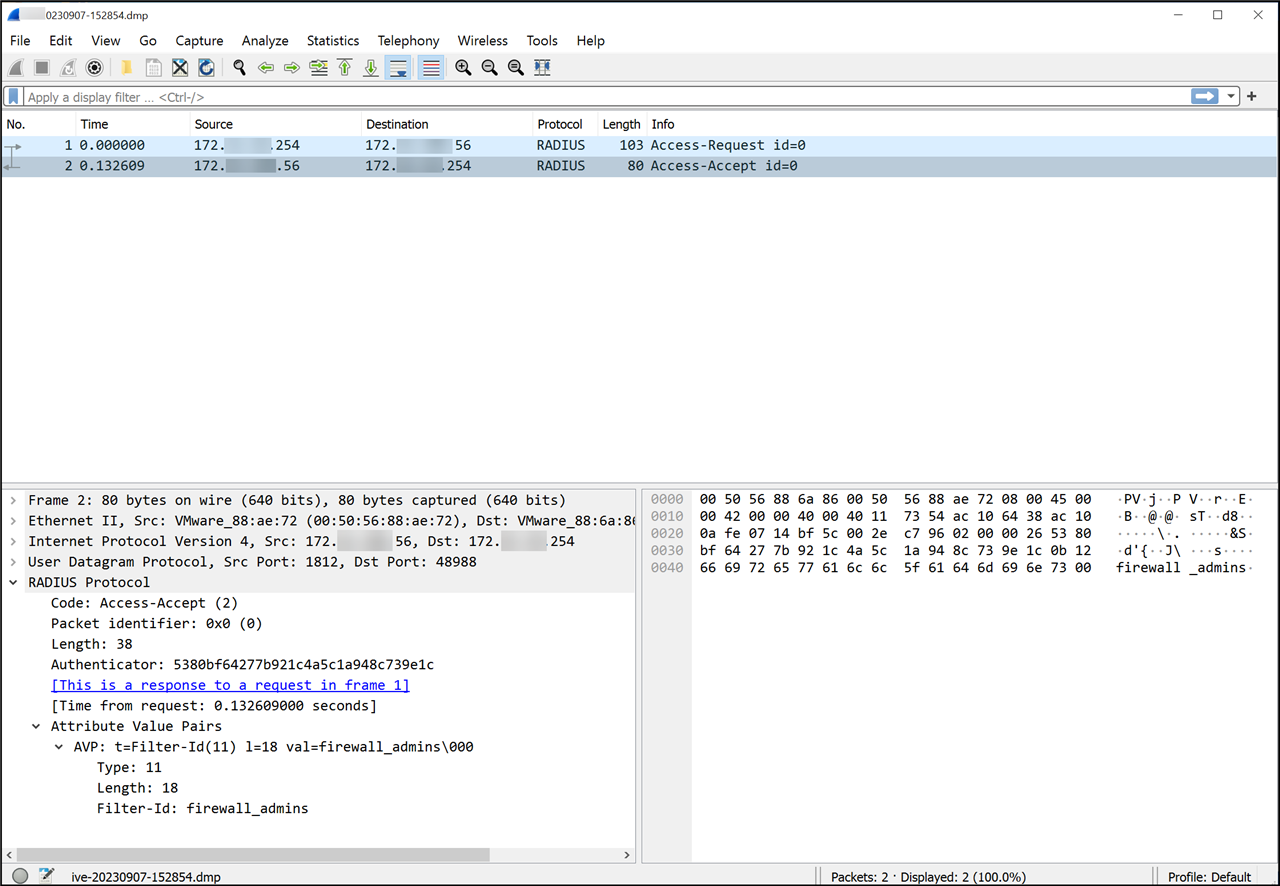
I ran a policy trace on the Radius server and can see the Access Request from the Sophos appliance, along with an Access Accept and I can see the value I have set for "Filter-ID" sent back as part of the Access-Accept message.
Can someone please advise?
Thanks in advance!
This thread was automatically locked due to age.



