Hallo,
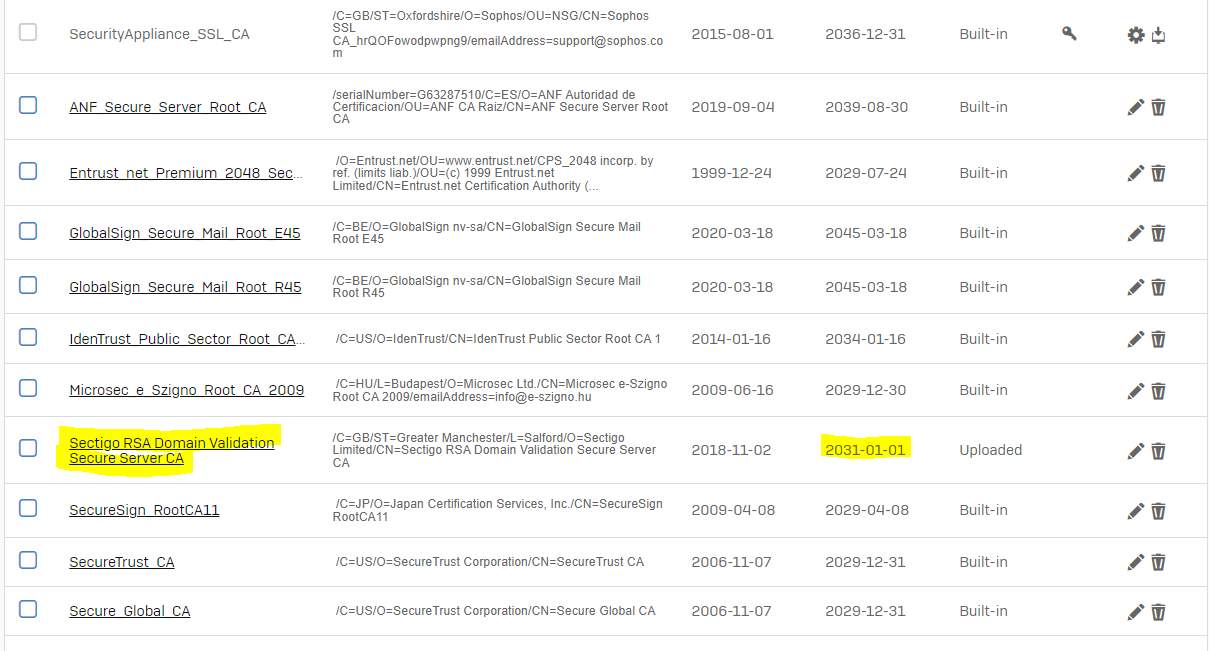
any reason why the (build-in) CA cert from Sectigo RSA Domain Validation Secure Server CA was removed the last days? Is that normal or a bug, pattern updates? Anyone else has this CA on the firewall? Had to add it again manual by hand to work again...
Essentially, there was a topic about Sectigo:
https://nakedsecurity.sophos.com/2020/06/02/the-mystery-of-the-expiring-sectigo-web-certificate/
And SFOS does have the UserTrust CA, which is the parent CA of your Sectigo.
Do you had a problem?
__________________________________________________________________________________________________________________
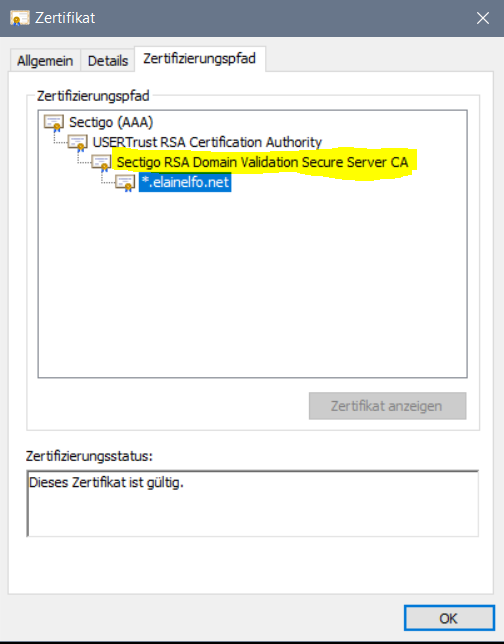
Because the Sectigo RSA Domain Validation Secure Server CA was not on the firewall anymore (worked last week, that why I opened the thread), it can not verify all certs that are using it. USERTrust RSA is on the firewall (but seems firewall need all certs in chain to work).
Hello Quallensaft,
How have you realized your firewall lost "Sectigo RSA Validation Secure Server CA"? is that during any firmware migration ? which SFOS version you're using ? It's unlikely that SFOS have added and removed this certificate.
Could you IM with support access ? to check what might have happened here.
Regards,
Saurabh
Well would be cool to know if Sectigo RSA Validation Secure Server CA is default on the firewall in first place?
And if the firewall needs the complete CA chain to verify certs issued by Sectigo RSA Validation Secure Server CA?
I did nothing regarding certs. Since today I got cert validation errors because Sectigo RSA Validation Secure Server CA is missing.
XGS 3300 latest firmware.
I uploaded Sectigo RSA Validation Secure Server CA by hand to get the issued enduser-certs working.
Without I get a cert-error that it's not trusted "Blocked due to invalid TLS certificate".
I just wonder because a lot of websites using certs issued by RSA Validation Secure Server CA and until today I got no errors. It was also not necessary to upload it before.
So I assumed that it was on the firewall before…
Could this certificate be issued by the old CA?
Can you link us the link of the URL, you saw the problem?
__________________________________________________________________________________________________________________
https://lforr.elainelfo.net/nr243/go/xc0a8rx8k7ekfjejhvi86rg6di2zkohldz74s0s0s1cl/7?t_id=4265649570
(web-content of an paket tracing mail)
https:// lforr . elainelfo . net/nr243/go/xc0a8rx8k7ekfjejhvi86rg6di2zkohldz74s0s0s1cl/7?t_id=4265649570
(the filter here really sucks!)
Something is odd with this website in general.
See: https://www.ssllabs.com/ssltest/analyze.html?d=lforr.elainelfo.net&s=78.35.37.39
Seems like the hoster of this website made a mistake and used not "the full chain" of the CA.
Or see: https://www.sslshopper.com/ssl-checker.html#hostname=lforr.elainelfo.net
__________________________________________________________________________________________________________________
Essentially most client will have a problem with such a Webservice. It is bad practice to build a website like that. You should always include the full chain PEM to the certificate and not forgetting one certificate.
sslshopper gives you the workaround, you could do on the firewall - But essentially this is a problem of the website owner and his responsibility to fix.
You can also check here: https://medium.com/@superseb/get-your-certificate-chain-right-4b117a9c0fce
__________________________________________________________________________________________________________________
That’s true but you have no choice if external websites are not publishing the full chain.