Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
Important note about SSL VPN compatibility for 20.0 MR1 with EoL SFOS versions and UTM9 OS. Learn more in the release notes.
I notice many firewall denied firewall logs created by a rule, that is an allow rule only.
Even more strange is, that the port 1027 logged is not contained in the rule.
Watching the traffic with drppkt shows no blocked packets.
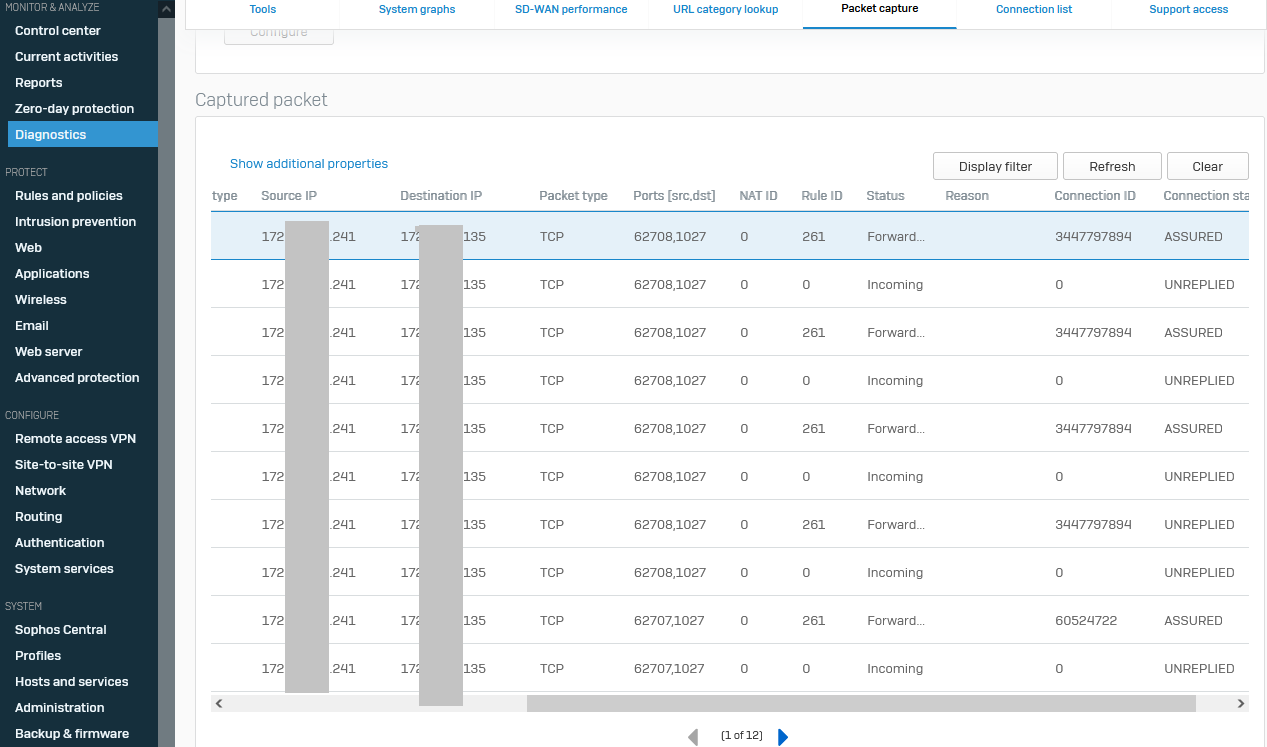
Tcpdump shows the packets on CLI and WUI
I think I need some help to understand what is happening here.
That is the log:
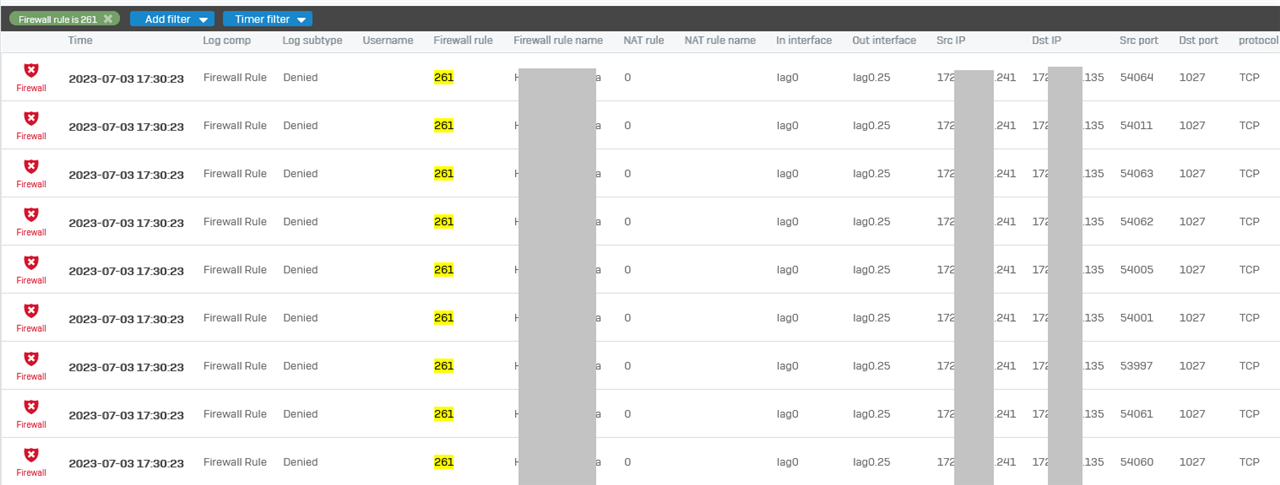
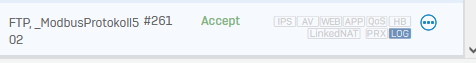
And the the Firewall Rule:

WUI tcpdump:
cli tcpdump
17:37:39.583731 lag0, IN: IP 172.xxx.xxx.241.56228 > 172.xxx.xxx.135.1027: Flags [.], ack 458, win 63784, length 0 17:37:39.583744 lag0.25, OUT: IP 172.xxx.xxx.241.56228 > 172.xxx.xxx.135.1027: Flags [.], ack 458, win 63784, length 0 17:37:39.583745 lag0, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56228 > 172.xxx.xxx.135.1027: Flags [.], ack 458, win 63784, length 0 17:37:39.583745 PortA3, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56228 > 172.xxx.xxx.135.1027: Flags [.], ack 458, win 63784, length 0 17:37:39.796507 PortA3, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [S], seq 1846860113, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:37:39.796507 lag0, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [S], seq 1846860113, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:37:39.796578 lag0.25, OUT: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [S], seq 1846860113, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:37:39.796581 lag0, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [S], seq 1846860113, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:37:39.796582 PortA3, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [S], seq 1846860113, win 8192, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0 17:37:39.796659 PortA3, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [S.], seq 0, ack 1846860114, win 1460, options [mss 1460], length 0 17:37:39.796659 lag0, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [S.], seq 0, ack 1846860114, win 1460, options [mss 1460], length 0 17:37:39.796659 lag0.25, IN: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [S.], seq 0, ack 1846860114, win 1460, options [mss 1460], length 0 17:37:39.796697 lag0, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [S.], seq 0, ack 1846860114, win 1460, options [mss 1460], length 0 17:37:39.796699 PortA3, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [S.], seq 0, ack 1846860114, win 1460, options [mss 1460], length 0 17:37:39.796864 PortA3, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 1, win 64240, length 0 17:37:39.796864 lag0, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 1, win 64240, length 0 17:37:39.796898 lag0.25, OUT: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 1, win 64240, length 0 17:37:39.796900 lag0, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 1, win 64240, length 0 17:37:39.796901 PortA3, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 1, win 64240, length 0 17:37:39.797710 PortA3, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [P.], seq 1:457, ack 1, win 1460, length 456 17:37:39.797710 lag0, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [P.], seq 1:457, ack 1, win 1460, length 456 17:37:39.797710 lag0.25, IN: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [P.], seq 1:457, ack 1, win 1460, length 456 17:37:39.797736 lag0, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [P.], seq 1:457, ack 1, win 1460, length 456 17:37:39.797737 PortA3, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [P.], seq 1:457, ack 1, win 1460, length 456 17:37:39.797854 PortA3, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [F.], seq 457, ack 1, win 1460, length 0 17:37:39.797854 lag0, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [F.], seq 457, ack 1, win 1460, length 0 17:37:39.797854 lag0.25, IN: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [F.], seq 457, ack 1, win 1460, length 0 17:37:39.797880 lag0, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [F.], seq 457, ack 1, win 1460, length 0 17:37:39.797882 PortA3, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [F.], seq 457, ack 1, win 1460, length 0 17:37:39.798042 PortA3, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [F.], seq 1, ack 457, win 63784, length 0 17:37:39.798042 lag0, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [F.], seq 1, ack 457, win 63784, length 0 17:37:39.798062 lag0.25, OUT: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [F.], seq 1, ack 457, win 63784, length 0 17:37:39.798064 lag0, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [F.], seq 1, ack 457, win 63784, length 0 17:37:39.798065 PortA3, OUT: ethertype IPv4, IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [F.], seq 1, ack 457, win 63784, length 0 17:37:39.798121 PortA3, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [.], ack 2, win 1460, length 0 17:37:39.798121 lag0, IN: ethertype IPv4, IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [.], ack 2, win 1460, length 0 17:37:39.798121 lag0.25, IN: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [.], ack 2, win 1460, length 0 17:37:39.798138 lag0, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [.], ack 2, win 1460, length 0 17:37:39.798139 PortA3, OUT: IP 172.xxx.xxx.135.1027 > 172.xxx.xxx.241.56229: Flags [.], ack 2, win 1460, length 0 17:37:39.798168 PortA3, IN: IP 172.xxx.xxx.241.56229 > 172.xxx.xxx.135.1027: Flags [.], ack 458, win 63784, length 0
drppkt: nothing
Can you show the mouse over of this drop in logviewer?
__________________________________________________________________________________________________________________
Hi LuCar Toni of course: here the screenshot
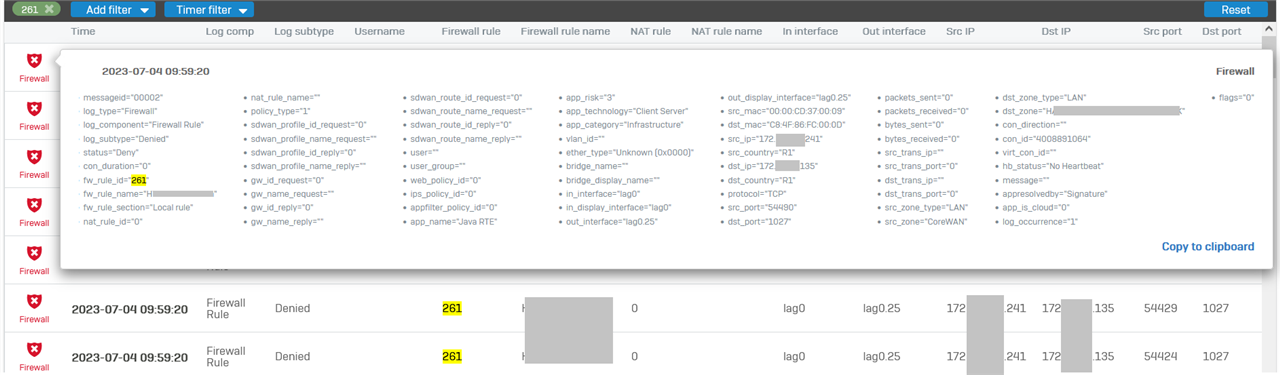
So essentially: There is a already fixed Bug in V19.5 MR1/2, which will be addressed in V19.5 MR3, which fixes this Logviewer behavior.
It is only "false logged", the traffic is actually not dropped.
Caused by the "Child Session" behavior: Means, if you have something like FTP or anything, which opens another connection related to a already allowed session, it will not be logged as "Allowed" based on the master connection, instead SFOS uses the denied section. Therefore you see it only for your FTP and other app firewall rule - correct?
__________________________________________________________________________________________________________________
Thanks for reporting a known issue.
This is happening for a few fireall rules here. Several other applications. Is there a NC# to share?
Hey LHerzog ,
I am suspecting it to be the following - NC-117063. Which is planned to be fixed in v19.5.3 MR-3.
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Thank you for sharing the NC ID Vivek Jagad I hope the Tech support can find a way how to stop the (false) logging for this rule until MR3 release.
Sure, Additionally I have updated the engineer, to expedite on the support case and help resolve the matter at the utmost priority if there is a patch available.
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
fine, it's in the release notes "Fixed" section..
| NC-117063 | Firewall | Allowed child connection is logged as dropped. |