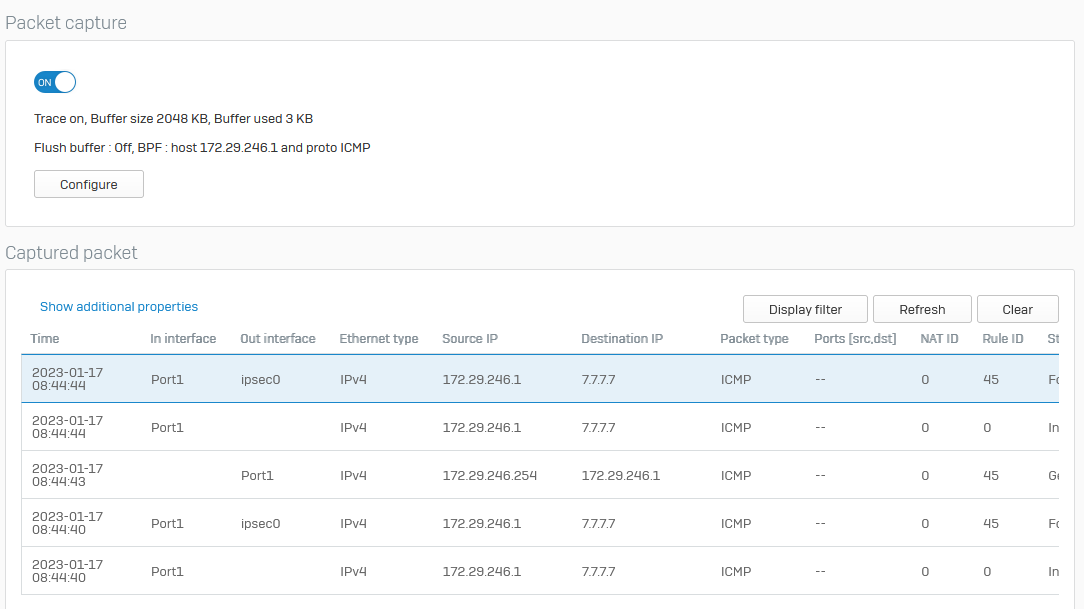
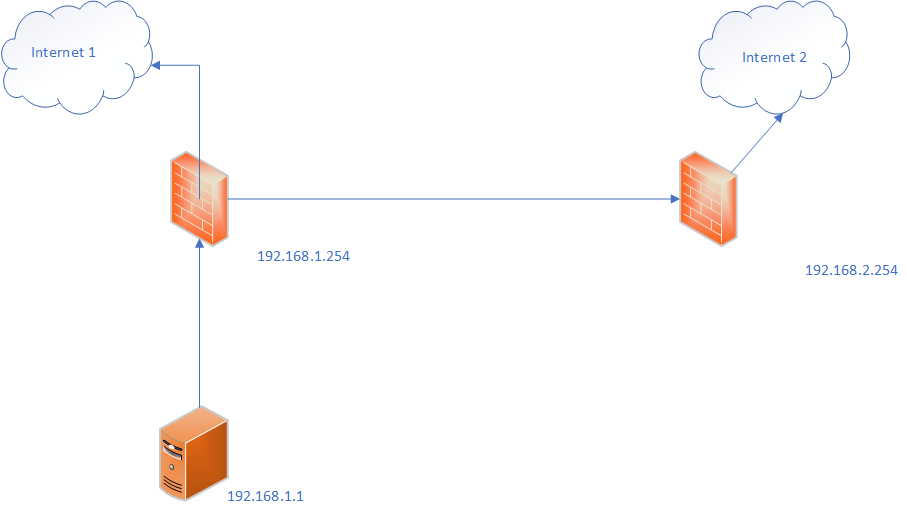
I have the following setup with an IPSEC tunnel between the two Sophos XG firewalls.
Internet traffic from 192.168.1.1 goes out through Internet 1
I want to say that for traffic with a destination of 8.8.8.8, go across the IPSEC tunnel and out through Internet 2 - all other traffic remains on Internet 1
I've tried:
system ipsec_route add host 8.8.8.8 tunnelname <tunnel>
set advanced-firewall sys-traffic-nat add destination 8.8.8.8 snatip 192.168.1.1
Packet capture shows traffic is being sent to the IPSEC tunnel correctly on Sophos (192.168.1.254) but the traffic never arrives at the other end.
What am I missing?
This thread was automatically locked due to age.