Hi,
I recently went through and updated some of my older LetsEncrypt certs and when I imported them they were showing up as Untrusted. The rest I had were still trusted. Unsure as to why, I removed the LetsEncrypt R3 Intermediate and the ISRG Root X1 Certs and re-installed the ones from the LetsEncrypt website, in theory completing the trust chain.
Unfortunately even with these certs installed, Sophos XG still doesn't trust those certs for use as Service certs, and now doesn't trust the original LetsEncrypt certs I had installed. Anyone seen this behaviour before?
I am running the latest XG build (SFOS 18.5.1 MR-1-Build326), and have rebooted the firewall as a test to see if it recovered. No success.
Thanks.
I have the same problem, Tried a fresh install of Sophos 18.5.1 MR-1, tried multiple times generate a new certificate from lets encrypt alos with new certbot instalation but no luck. I downloaded all root CA of lets encrypt en uploaded them on the sophos but still the same as above.
I used the new certification on a web server protection rule and the clients are working with a valid certificate but i can't chose this new certification on the webadmin or portal because it is not valid.
Have had the same issue. Be sure that ISRG Root X1 is used as the preferred chain when generating the LE certifcate.
Yes i have the ISRG Root X1. as you can see everything is good only not on the sophos. I tried multiple combinations with my certificate
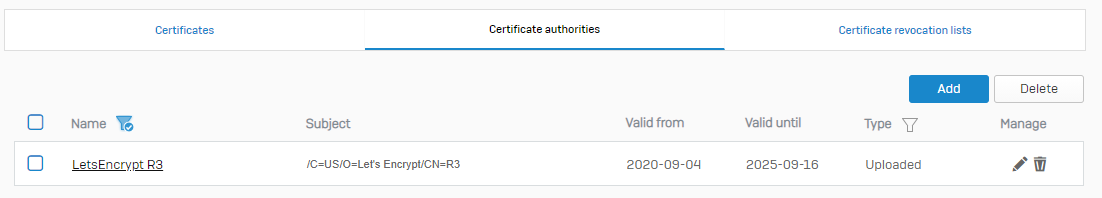
I see the R3 certificate uploaded to your certificates area. Did you actually upload it to the Certificate authorities section?
Same goes for aother certificates in the trust chain (X1 etc.).
If so delete it as regular certificate...
Sorry i used a confused name, i tried testing to create a pfx12 with my certificate en private with R3 as chain and called it R3.
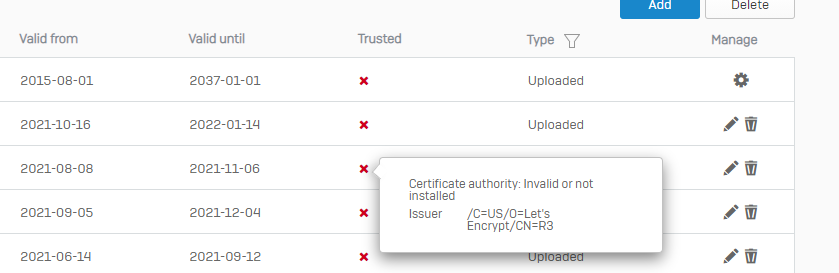
Below some test screenshot with X1 en R3 in my Certificate Authorities section
This is with auto imported Certificate Authorities from PFX12 file.
here i removed the auto imported certificate and manualy uploaded the r3, X1 and X1 cross CA certificate.
I also removed all my Certifciates which i used for testing so there are not any confusing names.
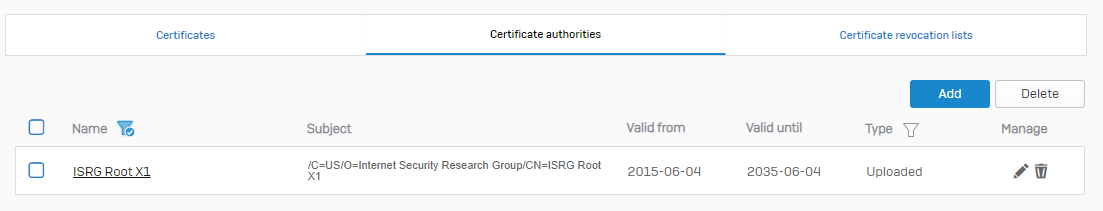
I have only uploaded the R3 and the ISRG Root X1 tot my XG / Certificate authorities.
All my LE (5) certificates are trusted.
Lets hope that sophos will bring a fix. I see more people with this new issue but nobody with a solution yet. a couple month ago this came because the expired X3 certificate but this seems to be a new one.
I had the same problem and it seems to be connected if the pfx file contains the full chain or only the cert itself.
When the pfx contains the full chain (ISRG Root X1 and R3) the chain is uploaded to the "Certificate authorities" as well and the Cert is shown as not valid.
Uploading the R3 certificate from the Lets Encrypt Website to the Authorities (ISRG Root X1 is already buildin) and uploading the pfx containing only the cert itself without chain result in a valid certificate.
I don't know where the bug is located but i presume something is going wrong with the pfx chain import.
I cannot reproduce your workaround. Even though I followed all steps it is still showing my certificate not being trusted.
Even worse, I got a second firewall where the problem does not occur at all. All certificates are valid and trusted.
Make 3 month ago a new install of the XG because untrusted Certificate, with blank installation certificate are trust, when i upload a backup it overwrites certificate space and trusted Certificate are lost, make new config without backup from scratch....
3 month later trusted certifcate will expire in one week. I renew the certificate with certboot load the certificate up and here we go "untrust"...!
let's Encrypt/CN=R3 installed
ISRG Root X1/CN=X1 installed
Does that mean for me I have to configure firewall from scratch every 3 months?
Okay, I finally figured out the workaround by Geoff Anderson.
First: Delete all previously uploaded Let's Encrypt certificates. The problem is related to the certificate name, which doesn't matter as long as you choose a name, you didn't use before. And it's important to upload BOTH certificates, the X1 and the R3 one.
https://letsencrypt.org/certs/isrgrootx1.der
https://letsencrypt.org/certs/lets-encrypt-r3.der
Name them LEX1 and LER3 and you will see, all your certificates will appear as trusted again.And it also solved the problem for LuCar Toni in post #2, because he also uploaded the certificate using a different name.