Hi,
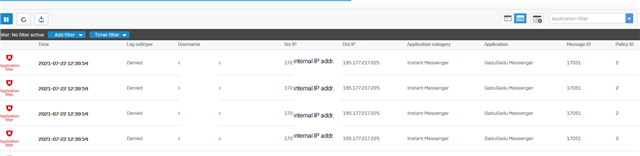
I'd think source and destination IP is wrong here.
It took me some time to help a user who reported he cannot download a file, we blocked because I could not find his computer with my query for source IP.
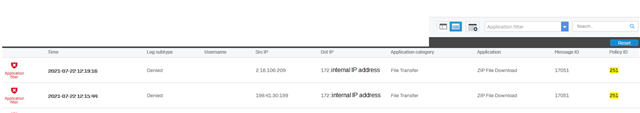
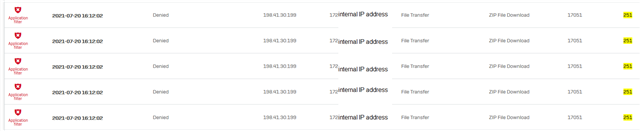
We block executabled here.
Other Application filter blocks look OK, eg. accessing blocked applications: