What’s new
We have added a new type of policy in Sophos Email called Secure Message Policy. This feature brings under one policy all types of encryption/decryption and signing/verification capabilities. The policy lends a more granular control over each one of them than the previous configurations under global settings. Furthermore, the policy allows for assignment of Portal Encryption license.
Watch the video attached at end of this post to familiarize yourself with the Secure Message Policy and other policy enhancements.
Applies to the following Sophos products
Sophos Email Advanced
Sophos Email Portal Encryption
Migration from settings to policy
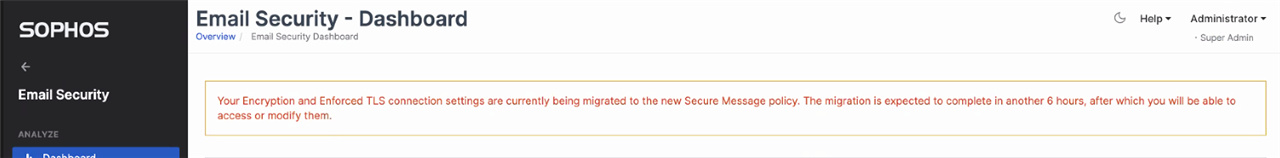
You may have noticed the following banner on your dashboard, when we migrated your encryption related global settings to the new policy.
The Encryption and Enforced TLS Connection settings (highlighted in the screenshot below) have been migrated to the new policy.
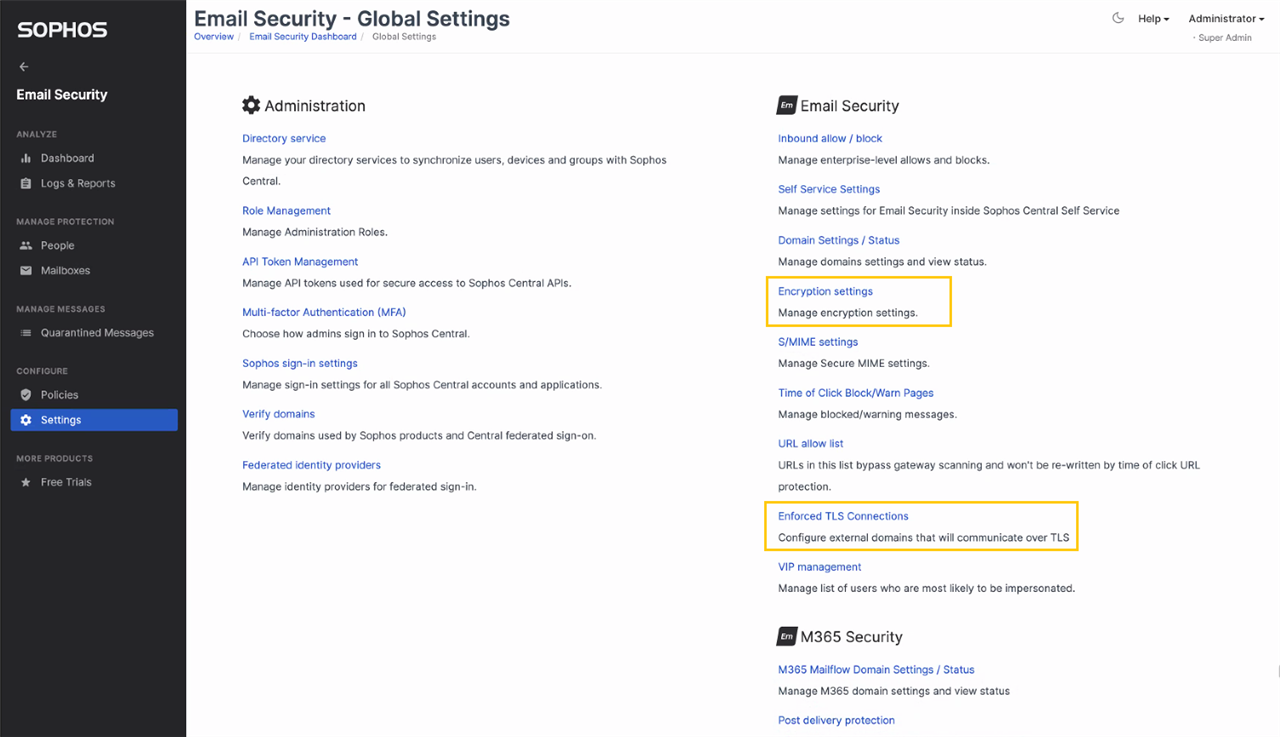
The S/MIME settings from your Email Security policy are also migrated to the Secure Message Policy. As highlighted in the screenshot below, you will notice one or more policy in your new Secure Message Policy, whose names are self-explanatory and start with “Migrated …”. The policies created depends on the settings migrated. After migration the product performs the same as it did before the migration.
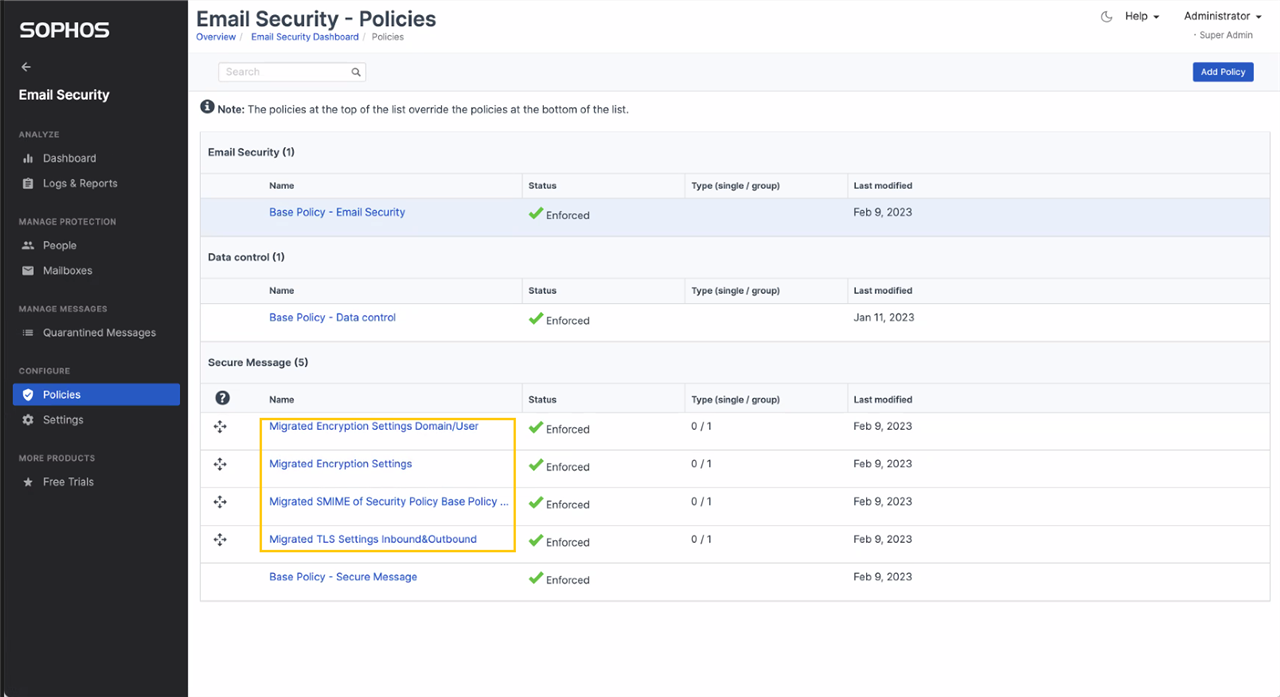
Other policy enhancements
In October last year, we released a policy enhancement, which made it possible to apply any policy to external domains and mailboxes. We have enhanced the experience further by grouping the users, groups, and domains under a new tab, “Internal”. This change makes it easy to comprehend that either of the three – users, groups, or domains – apply to the policy in an “and” combination with the mailboxes or domains listed under External tab.
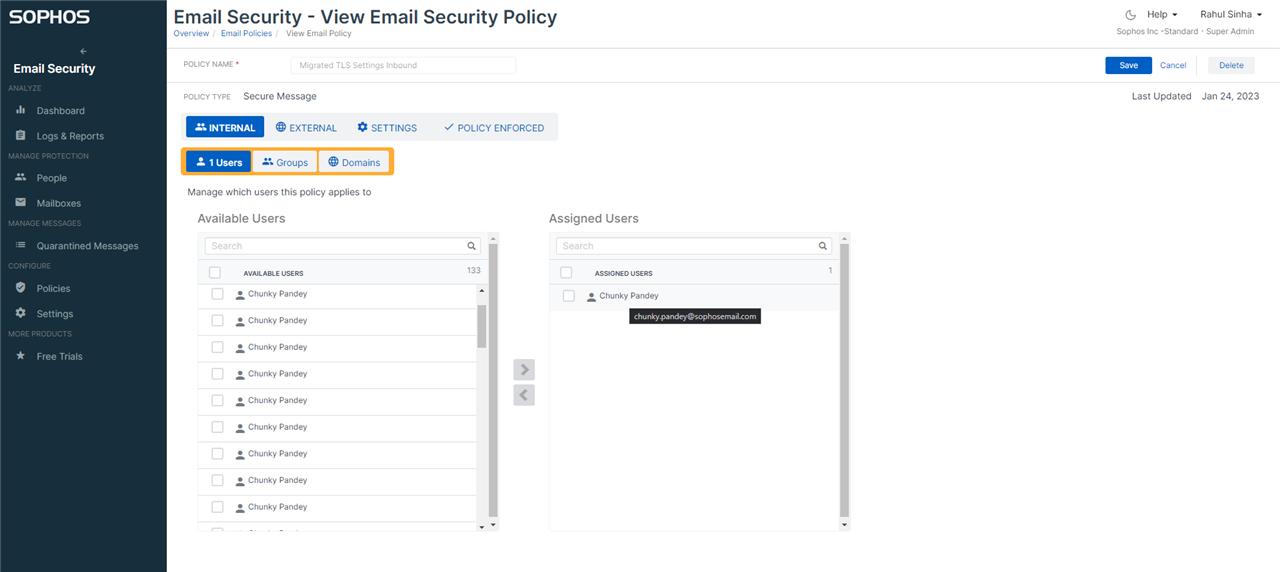
Furthermore, hovering over the name of the user shows the email address of the user, making it easy to distinguish between same or similar names.
Improvements in encryption methods
TLS encryption
Secure message policy gives you many more options with TLS enforcement. You can also enforce TLS v1.3 now. We recommend that you apply “Preferred TLS 1.3” on both inbound and outbound in your base secure message policy.
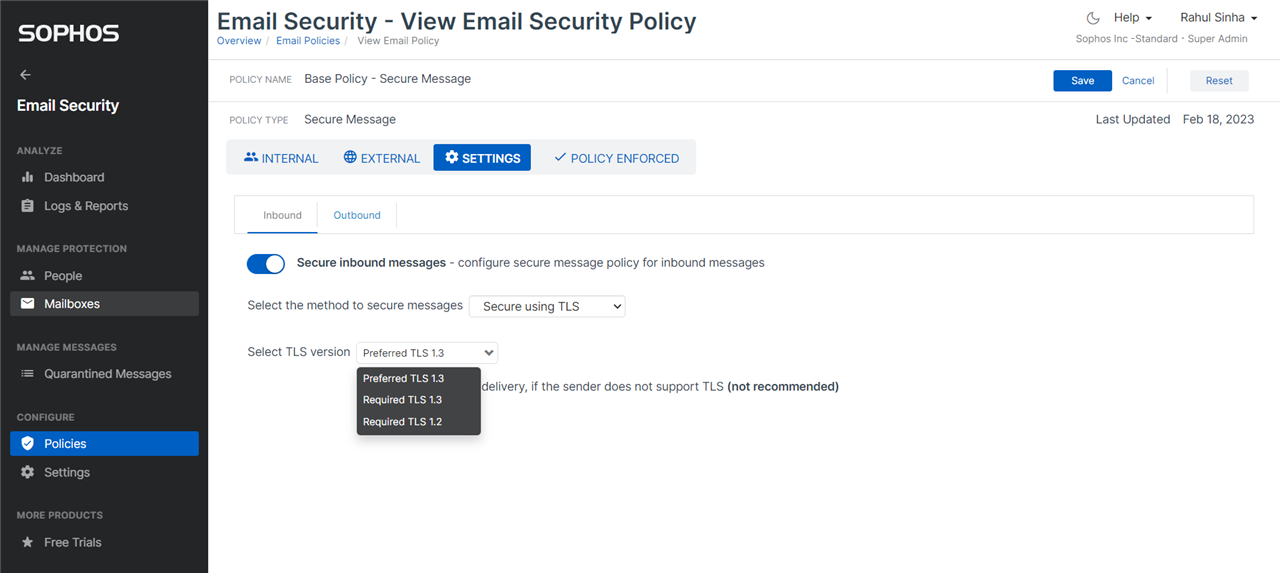
We do not recommend allowing unencrypted transport, because it is not secure. However, if you do not want to disrupt exchange of emails, then you will need to choose the option. Likewise, the options “Required TLS 1.3” and “Required TLS 1.2”, which do not allow transport of any TLS version other than the one selected, can disrupt exchange of emails. Please exercise caution, when you choose those options.
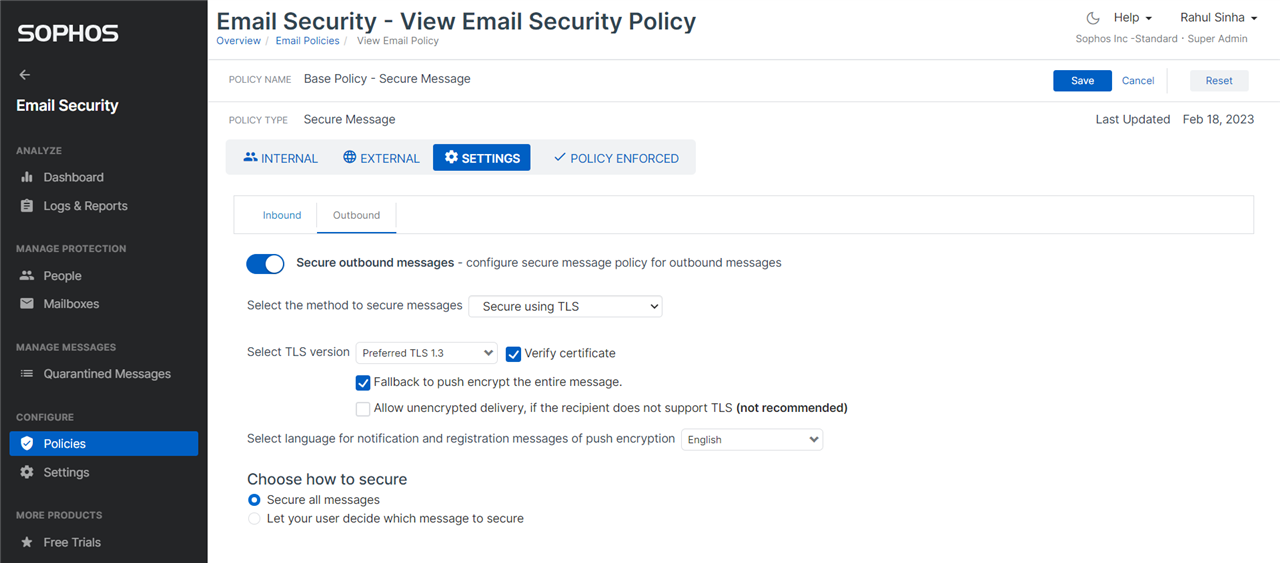
On outbound, you can opt to fallback to push encryption rather than allowing unencrypted transport, to ensure exchange of emails with recipient(s) who do not support TLS. You can also opt to verify the TLS certificate.
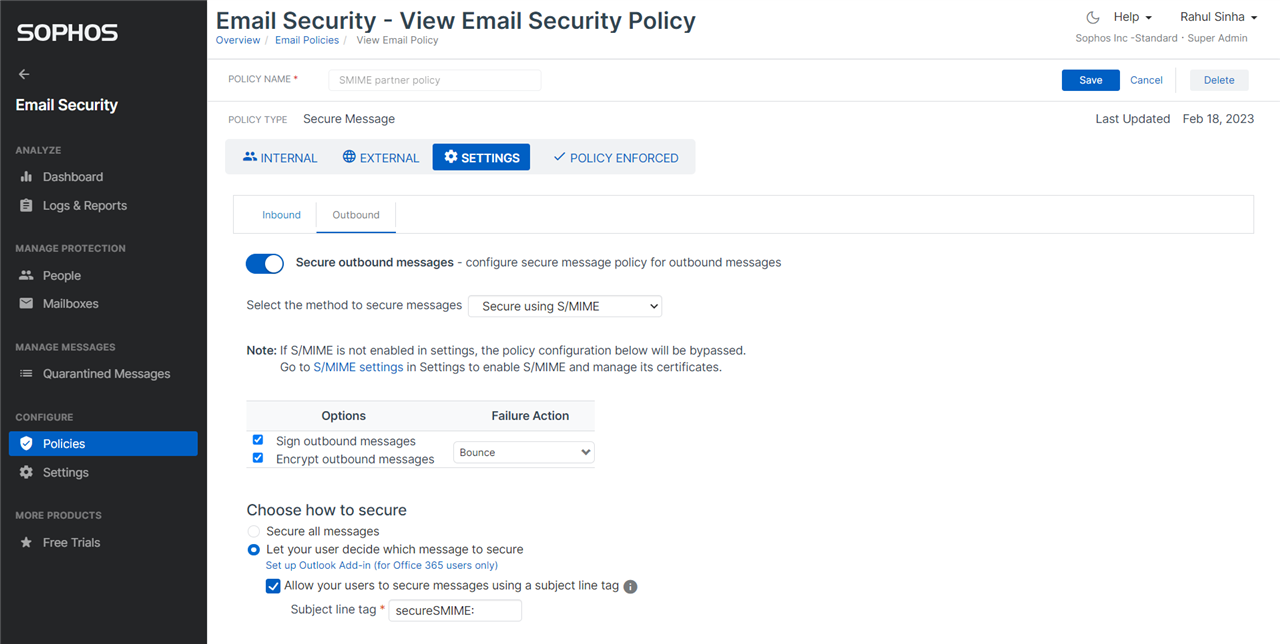
S/MIME
The secure message policy makes it convenient to apply the policy on inbound and outbound for a combination of internal and external mailboxes and domains – refer the screenshots below.
Furthermore, on outbound, you can now allow your users to trigger S/MIME by subject tagging.
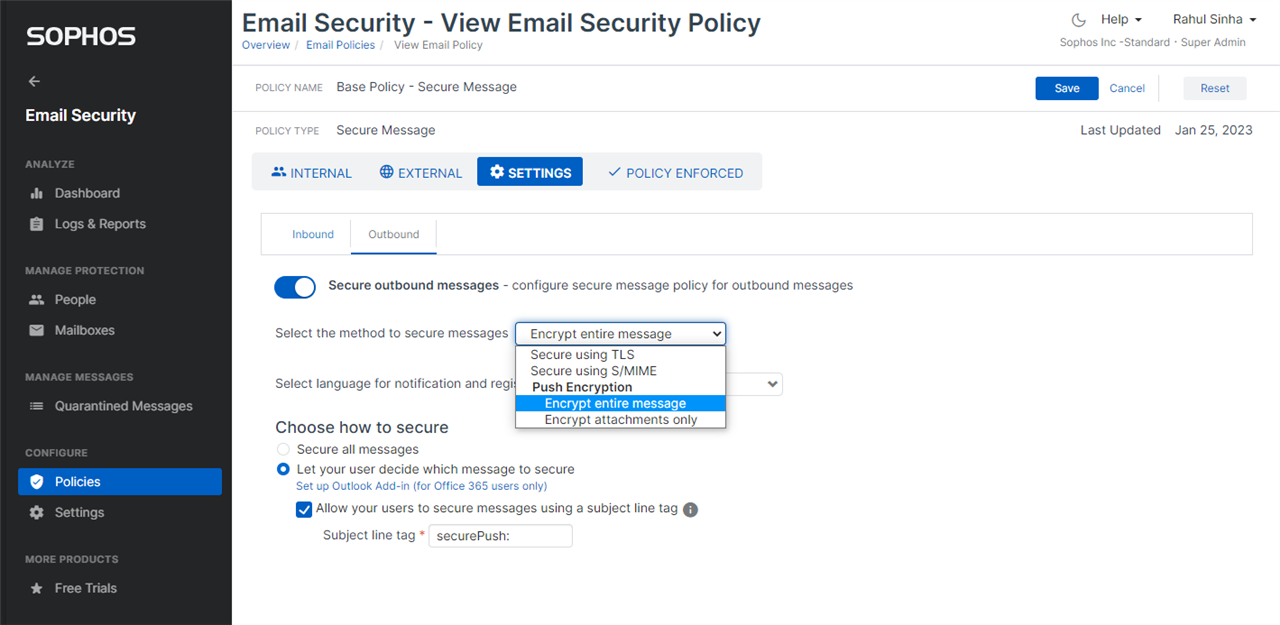
Push encryption
The secure message policy makes it convenient to apply push encryption on outbound by allowing to pick different subject tags for different policies.
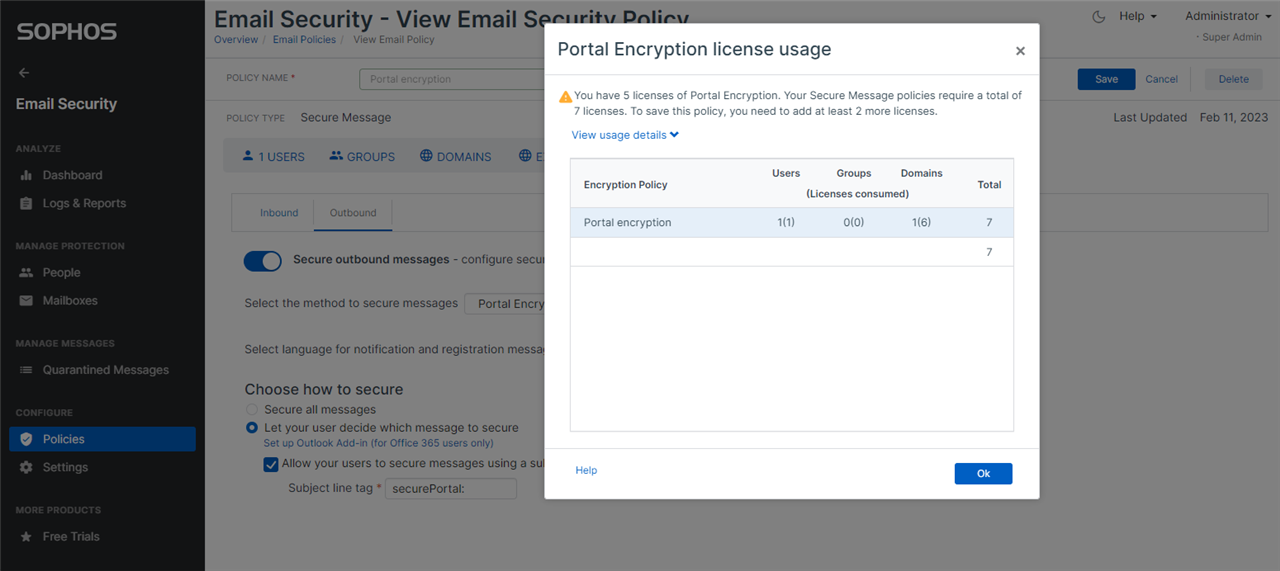
Portal encryption
The secure message policy makes it possible to assign Portal Encryption licenses to internal users, groups and domains. In the screenshot below, only 5 Portal Encryption licenses are available, whereas the policy being configured for 1 user and 1 domain is trying to consume 7 licenses – of which 6 licenses will be required for the users in the domain.
Lastly, as announced previously, all the methods of encryption/decryption require that TLS be configured on your email server or hosted email service. Before you configure secure message policy, please ensure that the TLS is enabled on your email server or hosted email service to prevent disruption in exchange of emails. We recommend that you use TLS v1.3 on your email server or hosted email service.
Watch the demo video