Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Table of Contents
Overview
This Recommended read informs about proactive measures to prevent attacks on AWS S3 buckets.
Cybersecurity breaches can be avoided by having visibility, early detection, and compliance checks in place. Gone are the times when targeting an organization demanded an extensive toolkit and in-depth scripting expertise. A few years back, the malicious actors focused on ransomware attacks targeted at servers and databases. Still, as businesses shift to the cloud, cyberattacks have also evolved by targeting storage accounts that contain confidential files and Personally Identifiable Information (PII), the exposure of which can pose a significant risk to individuals and organizations.
Amazon Web Services (AWS)
Amazon Simple Storage Service (Amazon S3) is a versatile and highly scalable object storage service offered by AWS. It’s widely used for storing and retrieving large amounts of data, ranging from application backups and analytics data to multimedia files.
However, the convenience of storing data in S3 comes with the responsibility of ensuring robust security measures to safeguard your information from unauthorized access and data breaches. Moreover, the presence of advanced tools capable of scanning S3 buckets for public accessibility and evaluating permission levels within individual files simplifies the reconnaissance task for hackers.
Hackers have found multiple ways to aim at s3 buckets. In some cases, the attacker downloads the contents of s3 buckets or encrypts them using their cryptographic key. In contrast, others gain access to the organization’s s3 bucket and upload a malicious file into the bucket. When an employee accesses this file, it triggers a payload that leads to a ransomware/malware attack in the network. These attempts can go undetected and unaddressed without comprehensive monitoring and compliance assessments.
AWS MFA Delete
In some cases, hackers also tend to download and then delete critical files that are important to an organization. As an Additional Layer of Security, AWS has implemented MFA Delete. This ingenious method ensures that the person trying to delete a bucket has a physical or virtual MFA device with a code.
This helps prevent accidental deletions and adds more security to the process.
Cloud Optix
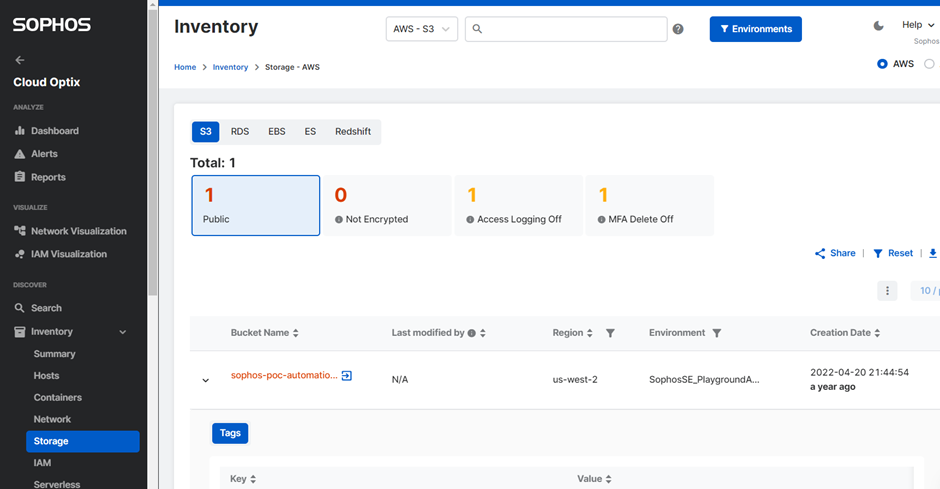
As a fundamental part of safeguarding an organization's sensitive and confidential contents, keeping the buckets private is advisable unless there’s a specific need for public access.
How does Sophos help mitigate attacks on s3 buckets?
With Sophos Cloud Optix
- Detecting public buckets in your organization is quick and effortless.
- It prominently identifies public buckets, immediately guiding you to assess the privileges.
- Highlight the public buckets with MFA delete OFF
- Alert Customer of unencrypted bucket
- Use the principle of least privilege to ensure that only relevant roles have access to the buckets.
Reviewing the permissions assigned to roles ensures that granular permissions lead to better security practices for the account.
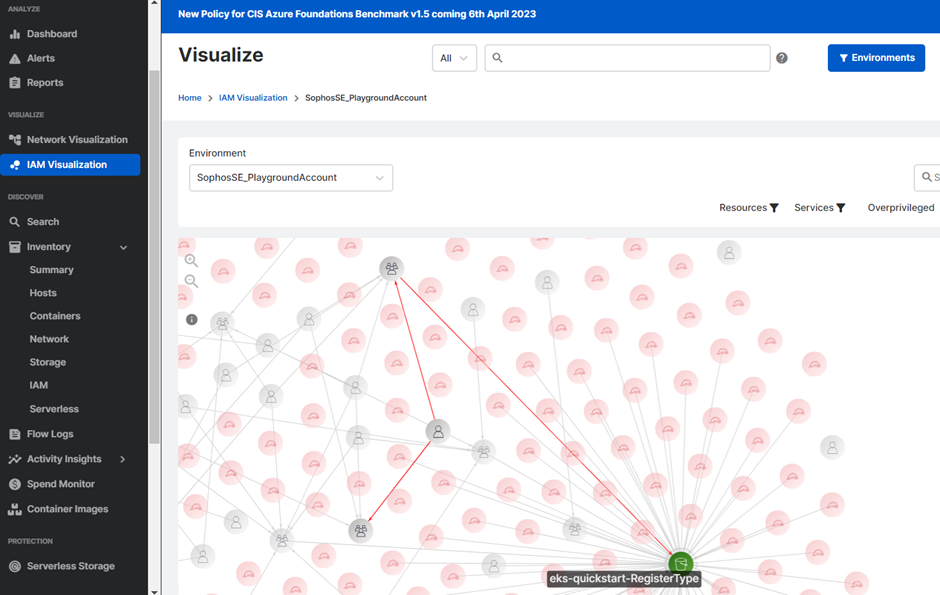
IAM Visualization
This feature in Cloud Optix shows all the permissions associated with the s3 service and helps understand if a user or group has been directly granted access to the bucket.
For more reference, kindly see IAM Visualization.
Live Discovery
Moreover, using Sophos Threat Analysis Center in Sophos Central, DataLake queries can be run to identify all the AWS services with IAM policies attached to users/groups instead of IAM roles.
,
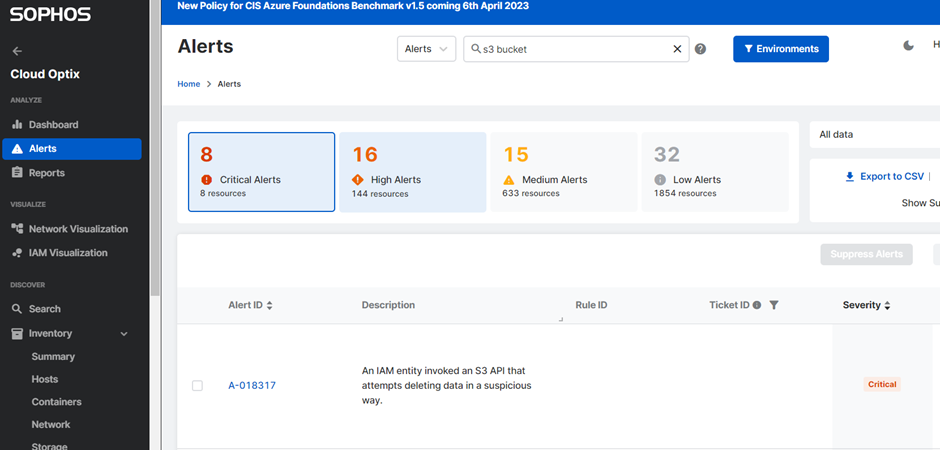
Misconfigurations can get lost in the noise of AWS service prompts. Cloud Optix can help you identify and draw your attention towards misconfigurations and potentially suspicious activity about your s3, using color-coded alerts that help prioritize critical elements of misconfigurations in AWS.
Alerts
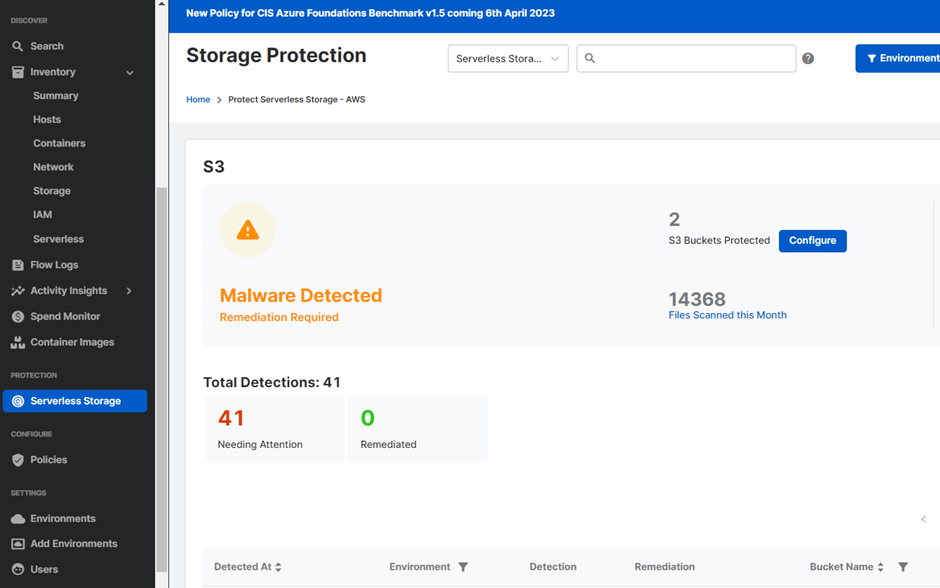
The newly launched feature of Storage protection ensures that the buckets configured for protection offer malware scanning for files within the customer's cloud environment, supporting up to 2.5 TB sizes. If any threats are identified within an S3 bucket, these instances are displayed within the Cloud Optix console, triggering an alert for immediate attention. For streamlined security, automatic remediation measures can also be configured, enabling the deletion or quarantine of malicious files. This feature is accessible to all Cloud Optix users, licensed based on Cloud Asset consumption.
Storage Protection
Turning on S3 protection with GuardDuty is recommended as it monitors object-level API operations to identify potential security risks for data in S3 buckets. To consolidate all the AWS findings in one place and add Cloud Optix intelligence to the obtained information, Optix can aggregate and integrate with Guard Duty among other AWS, Azure, GCP, and other third-party tools. More on integrations with Optix can be found here.
For 24/7 Cloud infrastructure monitoring, you may contact our MDR experts to assist you with response and identifying threats.
Revamped RR
[edited by: Erick Jan at 5:50 AM (GMT -7) on 18 Apr 2024]