In addition to the option to generate test detections from the NDR management console we have a test executable that can be downloaded from Sophostest.com. Below are the details:
Overview
The NDR team has created an 'EICAR' test that can be used by anyone to show that their NDR product is properly setup and working. This EICAR test can be triggered one of two ways; from the NDR sensor itself using the Appliance Manager or by running the EICAR test client file on another machine in the network. This guide will walk you through both scenarios and talk about the pros/cons of each. As you read through the guide be sure to remember that no matter how you run the EICAR test, the network traffic needs to be included in the current port mirror/span setup.
How it works
In order to properly test all five detection engines in NDR, we had to create a client/server communication that looks malicious, but really isn’t. We did this by looking at network flow data from real malware, and doing our best to emulate what we were seeing in a non-malicious way that would produce a severity score high enough to be case creating. On a high level, this meant we needed a client that reaches out to a server and downloads a file. By creating a server application that runs on a non-standard port, using a fishy TLS setup, and provides the file download, we were able to achieve this.
We have deployed this server to five different zones in AWS all over the world (us-west-1, eu-central-2, ap-east-1, ap-southeast-1, and sa-east-1). After we deployed the servers, we ran the client on networks being monitored by NDR and collected the SPLIT data we needed to train our ML model. In addition to the ML model update, we also created IDS rules using the TLS certificate hashes for each of servers. We also did the following to ensure the network traffic looked suspicious.
-
The server is listening on a non-standard TLS port, 2222.
-
The domain name used for each server is a DGA
-
The server uses a self-signed certificate to encrypt the traffic.
-
We changed the ALPN to something that is uncommon.
-
The TLS certificate is valid for 10 years
With all of these things combined, you should see information for each one of these engines in your detection flow data. If you are running the EICAR for the first time, or if it hasn’t been run in a while, you will also see that the flow is marked as unpopular. This means that the destination IP address hasn’t been seen on the network before. We use this unpopular indication in our score engine to help raise the score.
NDR EICAR from Appliance Manager
Starting with version 1.4.0 of the NDR Appliance we have added a new menu option called, Generate Detections. See the demo video that shows how to generate a detection the NDR Appliance Management console. This option can be a quick and easy way to verify everything is setup properly and quickly see a flow-based threat detection in Central. The minor downsides to triggering the detection this way are that it will always hit the same server in AWS (us-west-1), and if you don’t already have network traffic actively flowing to the sensor the flow information won’t make into the database in time to be scored.
NDR EICAR using client file
The NDR EICAR client file is a small 64-bit Golang application that we provide for Windows, Linux, and both Intel-based and M-based MacOS architectures. If you are going to use the Windows version, it is digitally signed and hopefully will not be blocked by antivirus applications. Anyone can download these client files using the Sophos Test website.
If the client is going to be run on a network with a strict firewall setup, then a rule (or rules) allowing the client traffic to reach the server will most likely need to be needed. Below is a list of the domains, ip’s, ports, and regions. Because you can specify which server the client reaches out to using a CLI option, not all of them need to be whitelisted.
|
Domain Name |
IP Address |
TCP Port |
AWS Region |
|---|---|---|---|
|
plrqkxqwvmtkm.xyz |
13.56.99.184 |
2222 |
us-west-2 (California, US) |
|
erqcmuydfkzzw.org |
16.62.124.9 |
2222 |
ea-central-2 (Zuerich, Switzerland) |
|
lypwmxbnctosa.net |
18.142.20.211 |
2222 |
ap-southeast-1 (Singapore) |
|
xbmwsfgbphzvn.com |
18.167.138.38 |
2222 |
ap-east-1 (Hong Kong, China) |
|
qwpoklsdvxbmy.com |
177.71.144.35 |
2222 |
sa-east-1 (Sao Paulo, South America) |
After downloading the zip file from Sophos Test, feel free to compare the file hash with the one listed. Once you have extracted the zip file, feel free to compare the client file hash with the one listed on Sophos Test or the text file/s that are part of the zip archive. If you run the CLI application using the --help CLI flag you will see all of the available options.
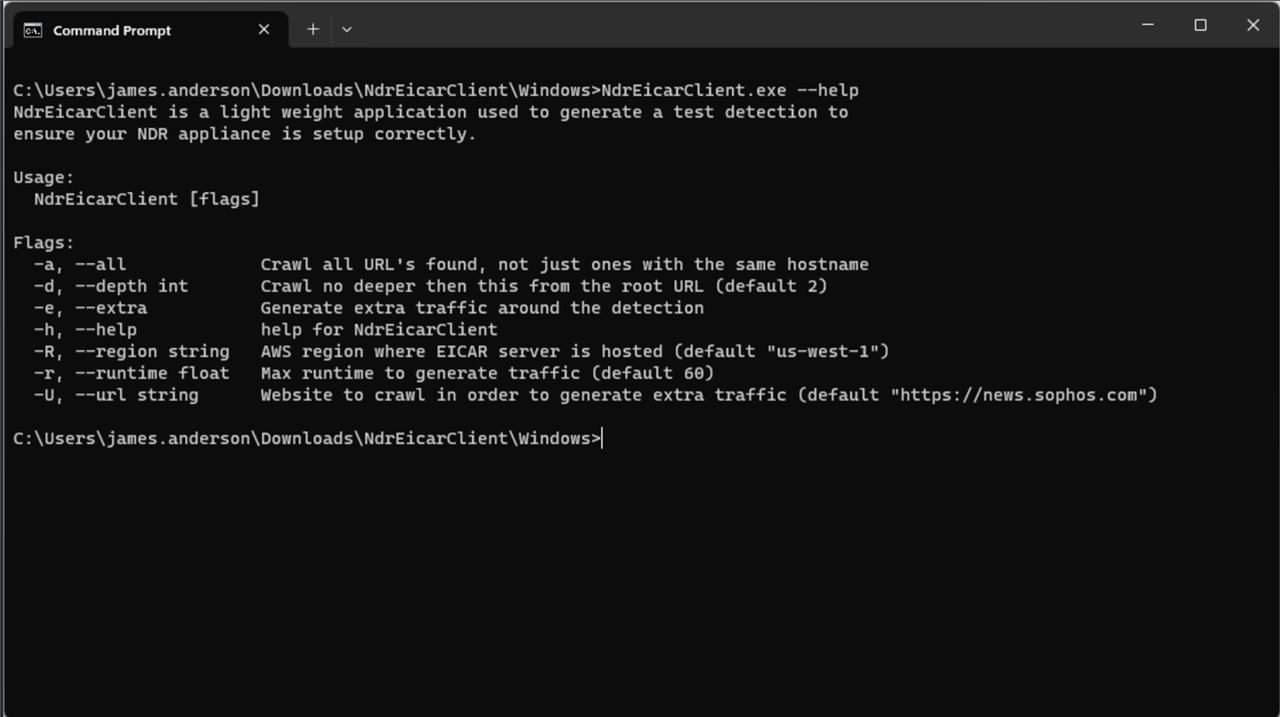
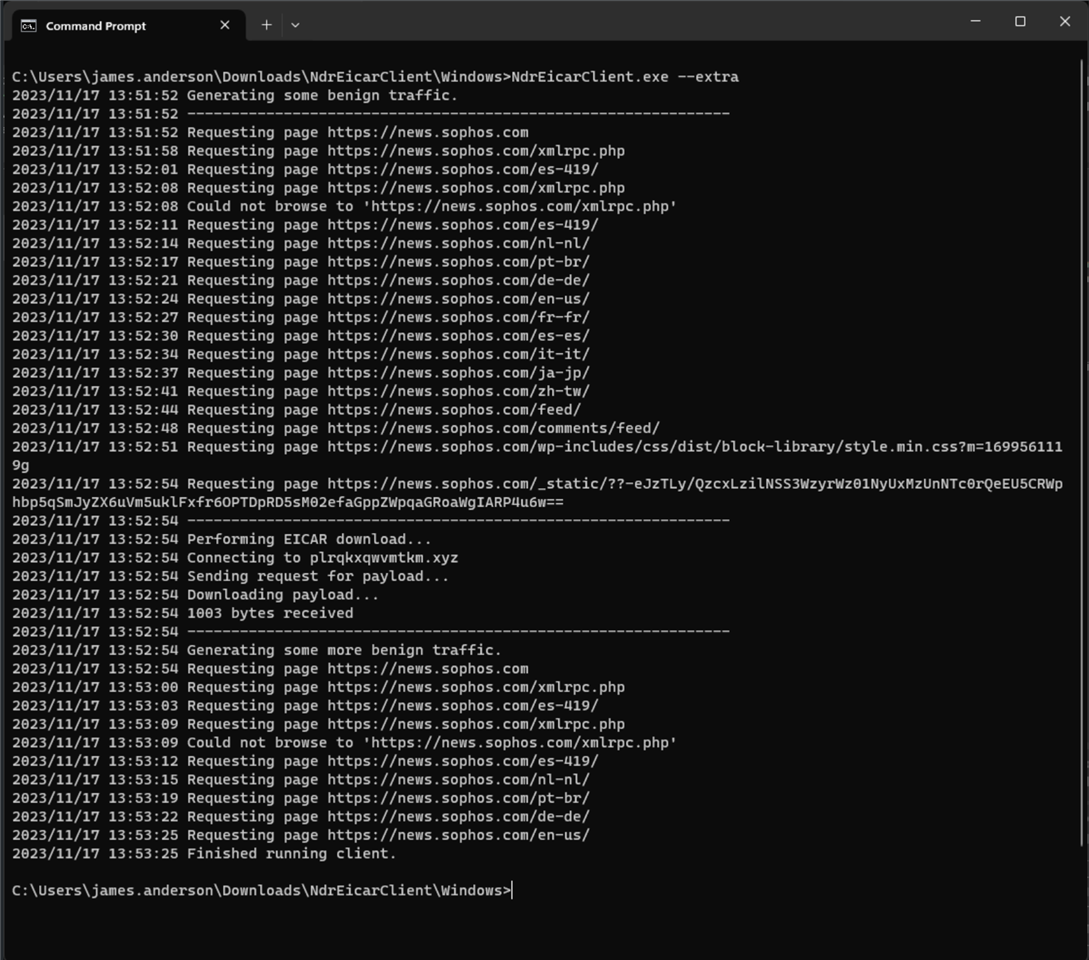
As you can see, there are few options here. Most of them belong to the applications ability to crawl a website in order to help generate traffic before and after the actual EICAR detection. This feature can be used on networks with little to no traffic that are having an issue of the flow information not making it to the scoring engine in time. The web crawling feature was mostly added to help with QA testing and SE test environments, but could also be used by a customer if needed.
Using default options
If you want to use the client with all of the default options, then just run executable with no CLI flags.
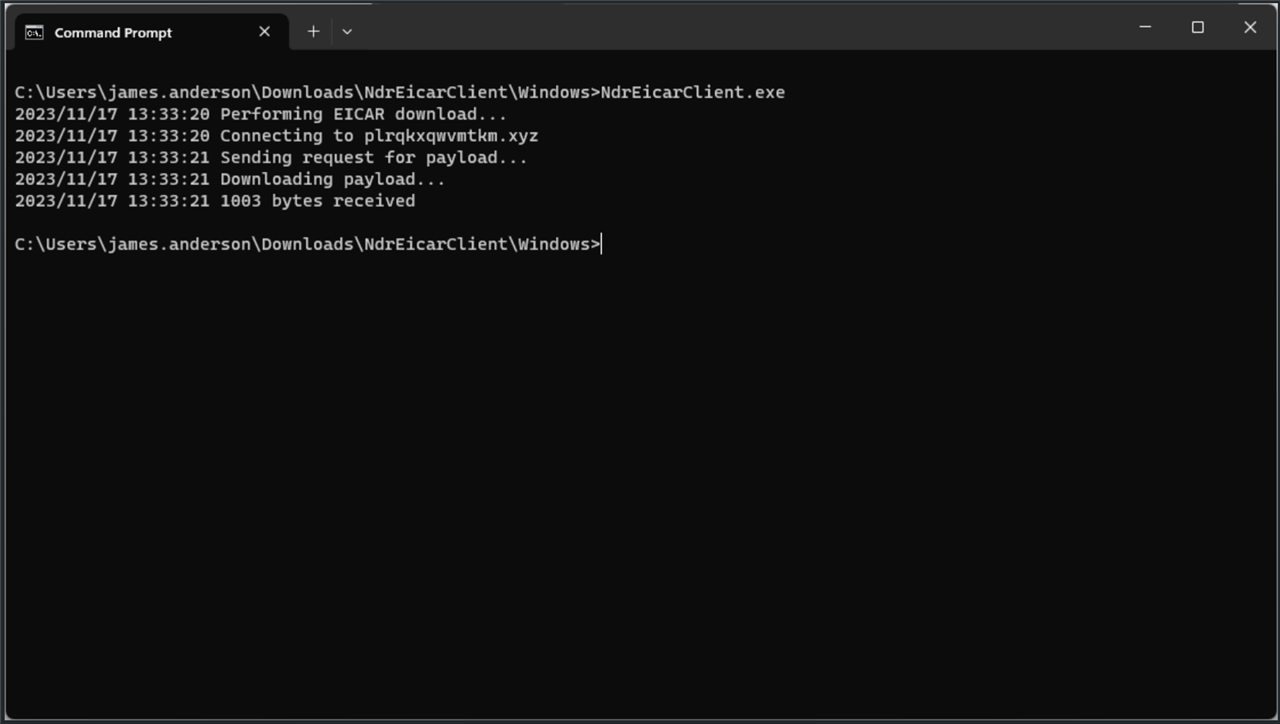
When using the default options, the client will reach out to the us-west-1 server and perform the file download one time.
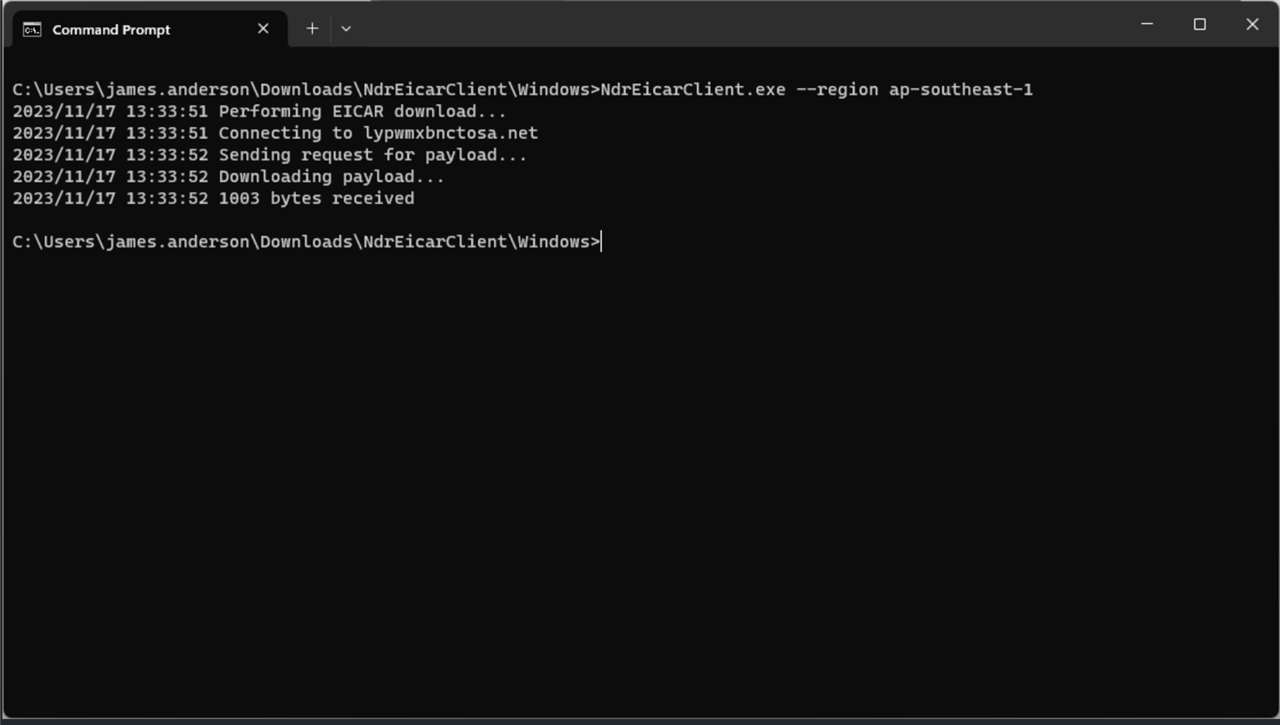
Specifying a region
If you want the client to reach out to a specific AWS region, then you will need to run the application with the --region CLI flag.
Generating traffic around the detection
As mentioned before, if you need to generate traffic around the detection then the client file includes a web crawling capability to help with that. By default, the web crawler will start with the news.sophos.com website and only crawl other sophos.com websites. By limiting the web crawler in this fashion, hopefully the traffic won’t be blocked by the firewall. If for some reason the firewall (or a web proxy) doesn’t allow this then you can specify a different website to start with. The default run time for the web crawler is one minute before the EICAR traffic, and 30 seconds afterwards. You can use the --runtime CLI option to change this. Whatever you time you provide in seconds will be run before the EICAR traffic, and then it will run for half that time afterwards. We have included a pause between web pages so this tool can not be used to DoS a website.