With the November update to NDR we have added the ability to generate an NDR detection directly from the Appliance manager console.
VIDEO: https://vimeo.com/884426639?share=copy
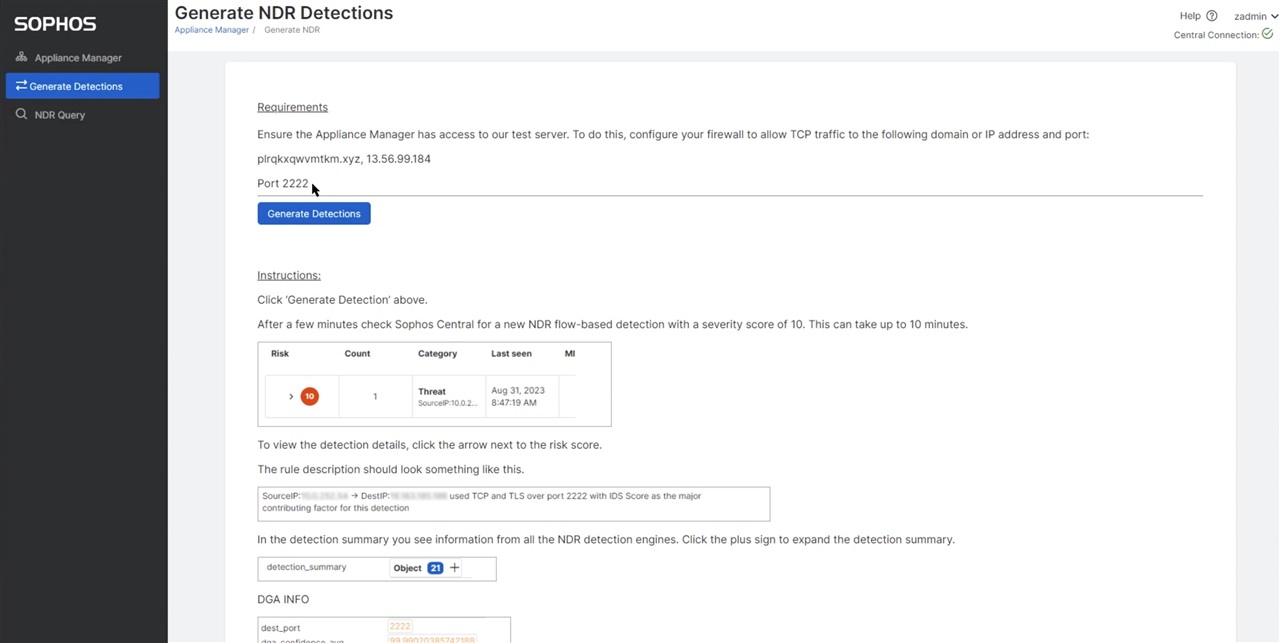
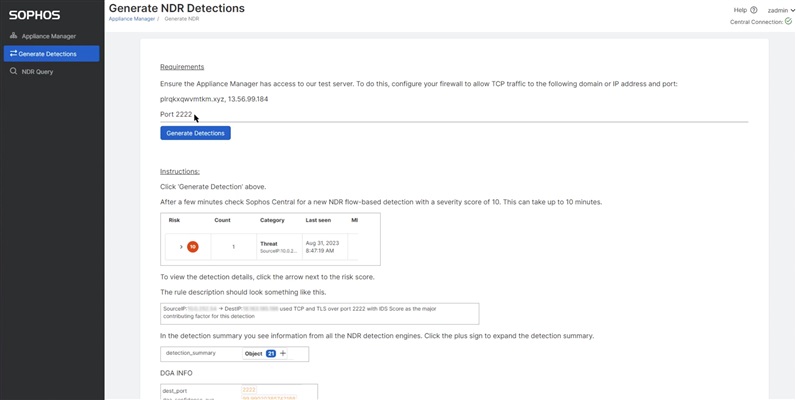
The Generate Detections option on the left side navigation bar will generate the network traffic for the NDR Sensor and each of the detection engines will contribute to an overall detection score.
DGA – Domain Generation Algorithm Engine Domain Generation Algorithms (DGA) are used by malicious actors to generate domain names that can be used for Command-and-Control (C2) purposes without being blacklisted. Using these algorithms, malware can generate a list of potential domain names that the C2 server might be hosted on. After numerous attempts, the algorithm will find a domain that exists and establish a connection
EPA – Encrypted Payload Analytics Engine and Machine Learning [ML] Machine learning is increasingly being used in network detection and response (NDR) solutions to detect suspicious traffic on enterprise networks. NDR tools continuously analyze raw traffic and/or flow records, such as NetFlow, to build models that reflect normal network behavior, according to Gartner. Deep learning takes this approach further by allowing for the detection of patterns across multiple attributes, enabling detections without IOC-based threat intelligence.
For the test we have trained a model to detect the communication pattern and classify it as Friendly Chameleon.
SRA – Session Risk Analytics Engine The SRA engine detects when network traffic deviates from documented protocol standards, which could indicate suspicious or risky network activity. This is important in a threat hunt because it helps identify nonstandard behavior that may indicate an attack. When the SRA engine observes such activity, it adds information about the behavior to the flow metadata. These flow risks are not considered indicators of compromise on their own, but when combined with detections from other engines, they can help in identifying malicious activity.
In the test scenario you will see three session risks identified.
- KNOWN_PROTOCOL_ON_NON_STANDARD_PORT - This risk indicates a known protocol used on a non standard port. Example HTTP is supposed to use TCP/80, and in case it is detected on TCP/1234 this risk is detected.
- TLS_SELFSIGNED_CERTIFICATE - This risk is triggered when a self-signed certificate is used.
- TLS_UNCOMMON_ALPN - This risk is set when the ALPN (it indicates the protocol carried into this TLS flow, for instance HTTP/1.1) is uncommon with respect to the list of expected values.
IDS – Intrusion Detection System Engine This proprietary IDS engine is a streamlined, more efficient engine with the capability to identify Indicators of Compromise (IOC)s in unencrypted traffic. Many security vendors continue to use overly robust content matching systems even with the loss of visibility, due to encryption.
For the test case we have added the IOC to our black list for the detection engine to match on. As a known 'malware' (in our case test site) this will be the primary contributor to the overall flow risk score.
For more information on how NDR works see the white paper: NDR White Paper