I am pleased to announce significant enhancements to the detection and response capabilities for Linux server workloads and containers in the cloud, on-premises and virtual deployments. The new functionality, made available through the integration of Capsule8 technology, will be available to all Intercept X Advanced for Server with XDR and Server MTR customers at no additional cost on 14 April 2022.
This release delivers a large number of new detections to the Sophos XDR Detections dashboard. Enabling organisations with visibility into Linux host and container workloads, accelerating the identification of exploits and anomalous behaviors before they get a foothold.
A sample of Sophos Linux and container detections include:
- Container escapes: Identifies attackers escalating privileges from container access to move across to the container host
- Cryptominers: Detects program names or arguments commonly associated with cryptocurrency miners
- Data destruction: Alerts that an attacker may be trying to delete indicators of compromise that are part of an ongoing investigation
- Kernel exploits: Highlights if internal kernel functions are being tampered with on a host
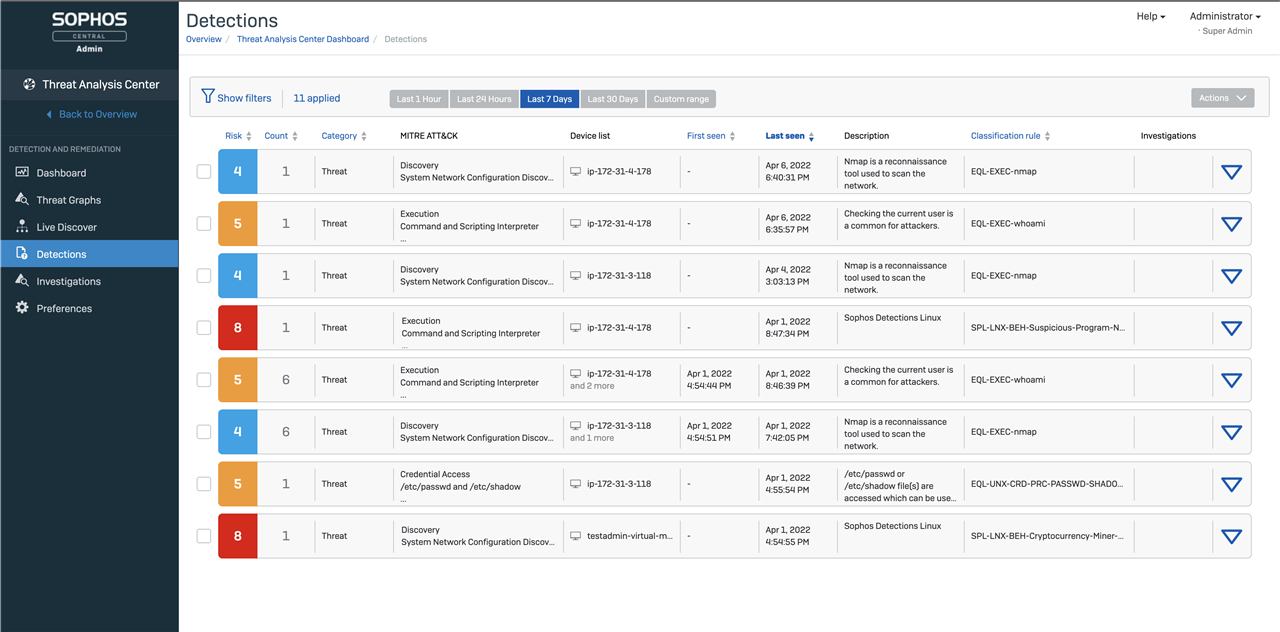
The detections from the updated Linux agent form part of the existing Threat Analysis Centre to enable investigation and response across all of your Endpoints, be they Windows, macOS, Linux or Mobile. You can use existing Live Discover capabilities to query detection data from either specific devices, or across all of your estate by using the Sophos Data Lake.
https://support.sophos.com/support/s/article/KB-000039257?language=en_US
Live Response lets you connect to devices to investigate and remediate possible security issues: https://docs.sophos.com/central/Customer/help/en-us/central/Customer/tasks/LiveResponse.html
In addition to Detections, all XDR customers benefit from Investigations in their Threat Analysis Center. The Investigations Dashboard will help analysts quickly dive into any recent investigations that were created. They will be able to manually create investigations and associate multiple detections with an investigation.
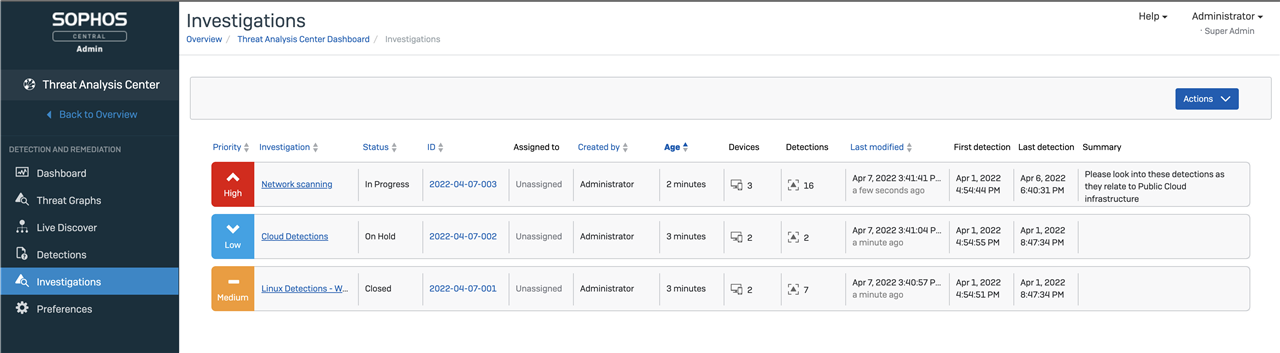
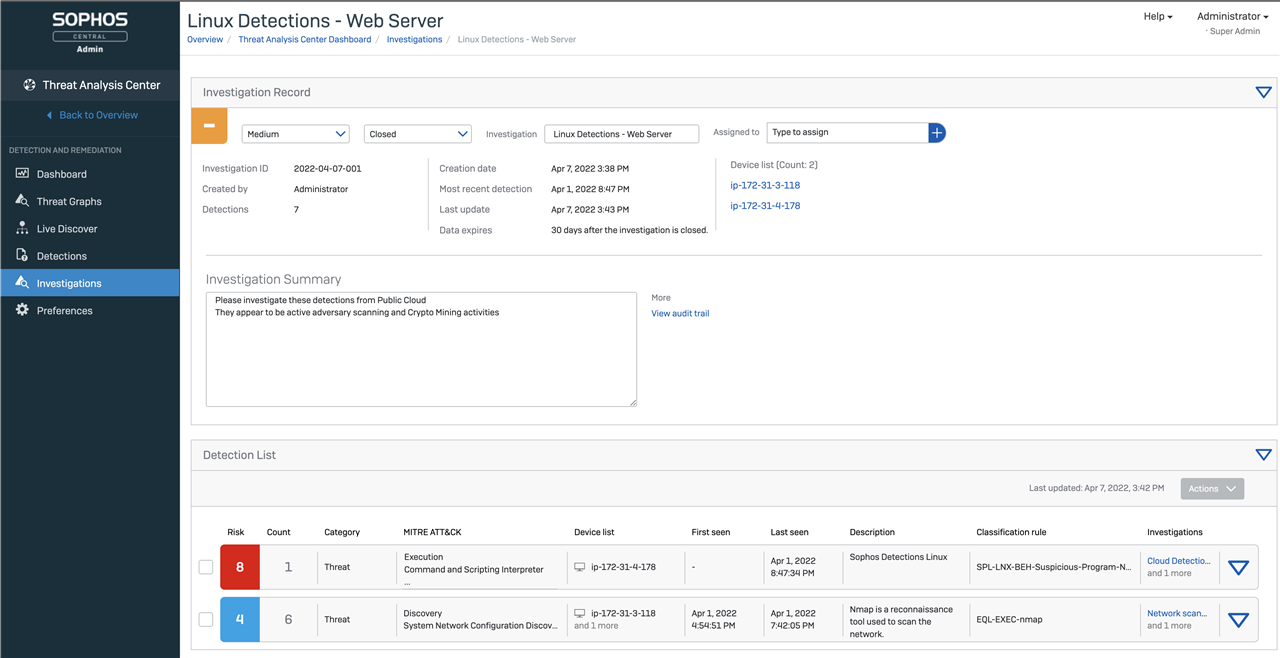
The lightweight Linux agent gives security teams critical information to investigate and respond to behavioral, exploit, and malware threats in one place. This option allows customers to manage all their Sophos solutions from a single pane of glass, seamlessly moving between threat hunting, remediation, and management.
There are two known UI bugs that will be fixed in the next month:
- MITRE ATT&CK column will not always be correctly populated
- Description column will sometimes contain 'Sophos Detection Linux' in the summary
Later this quarter we will be releasing a Linux threat sensor, fine-tuned for performance, using APIs to integrate runtime threat detections into your existing threat response tools. providing maximum visibility of workloads with minimal impact on performance.
