Sophos is aware of a new ransomware variant being seen in multiple countries today. Our investigation shows that this attack both encrypts files and the Master Boot Record (MBR) and can spread rapidly using several techniques, including the "EternalBlue" exploit of a vulnerability in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin. It can also spread by using a variant of the Microsoft PsExec tool in combination with admin credentials from the target computer.
Customers using Sophos Endpoint Protection are protected against all known variants of this ransomware. We first issued protection on June 27th at 13:50 UTC and have provided several updates since then to provide further protection against possible future variants.
In addition customers using Sophos Intercept X were proactively protected with no data encrypted, from the moment this new ransomware variant appeared. However customers may need to take further steps to reboot an infected computer.
What to do
Please ensure all of your Windows environments have been updated as described in Microsoft Security Bulletin MS17-010 - Critical.
To further reduce the risk of the infection spread, Sophos Endpoint customers can ensure that Adware/Potentially Unwanted Applications (PUA) detection is enabled and that the"PsExec" tool is not authorized or excluded.
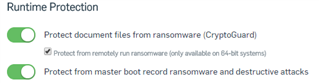
Sophos customers using Intercept X should ensure they have CryptoGuard and master boot record protection enabled as below.
Sophos Endpoint protection customers should ensure their computers are up to date and following best practices.
Sophos has issued protection against this threat:
| Threat Name | Sophos IDE | Protection Availability | |
| Publication Started | Publication Finished | ||
| Mal/Generic-S | LiveProtection | 2017-06-27 13:50 UTC | 2017-06-27 13:50 UTC |
| Troj/Ransom-EOB | rans-eob.ide | 2017-06-27 14:10:00 UTC | 2017-06-27 14:12:58 UTC |
| Troj/Petya-BF | petya-bh.ide | 2017-06-27 15:43 UTC | 2017-06-27 15:46 UTC |
| Troj/Petya-BH | petya-bh.ide | 2017-06-27 15:43 UTC | 2017-06-27 15:46 UTC |
| Troj/Petya-AP | petya-bh.ide | 2017-06-27 15:43 UTC | 2017-06-27 15:46 UTC |
| Troj/Petya-BG | petya-bh.ide | 2017-06-27 15:43 UTC | 2017-06-27 15:46 UTC |
| Troj/Petya-BI | petya-bi.ide | 2017-06-27 18:03 UTC | 2017-06-27 20:08 UTC |
| Troj/Petya-BK | petya-bk.ide | 2017-06-28 22:25 UTC | 2017-06-28 00:28 UTC |
| Troj/Ransom-EOC | miner-cp.ide | 2017-06-28 02:34 UTC | 2017-06-28 04:37 UTC |
| Mal/PetyaWr-A | recam-l.ide | 2017-06-28 08:00 UTC | 2017-06-28 10:03 UTC |
| Troj/Ransom-EOL | recam-l.ide | 2017-06-28 08:00 UTC | 2017-06-28 10:03 UTC |
| Troj/Petya-BL | petya-bl.ide | 2017-06-28 11:59 UTC | 2017-06-28 15:02 UTC |
Related information
Deconstructing Petya: how it spreads and how to fight back
Petya variants behind the global ransomware outbreak: here’s what we know so far