Hey together,
A short follow up to my questions regarding the AD sync issues. The original thread MR3 was closed.
So I checked the behaviour at our XG once again, now with MR3. I can add a user in our AD group and i'm able to connect the ssl vpn. After that I removed the user from the group and tried to reconnect.
It was also possible. I checked the Users Group, it was now "Open Group" as mentioned from ddcool.
Checked the assigned remote access of "Open Group" --> no policy applied. So I checked the user configuration, were the vpn configuration of the AD group was still applied. That's nuts?
Next try, I set up a new default group where all settings are denied or not set. Not able to connect to ssl vpn but still able to login at the user portal. If I remove a user from their corresponding AD groups, there shouldn't be any further access to the systems.
What am I missing? Any Ideas? LuCar Toni Heinz Göth
Regards and thanks in advance,
Jonny
User portal access should be possible, as the user is existing. SSLVPN should not be possible, if the certificate is removed. The certificate should be removed, if the user is removed from the configuration.
__________________________________________________________________________________________________________________
Thanks for your explanation.
A) I understand that a user are able to access the user portal as long as he is existing. But why? If I understand it correctly I have technically no chance to lock out a user from xg per group assignment until I delete him? A hard coded default group with "Deny all" would be great, or just an "active" checkbox ?
B) What excatly do you mean with " is the user is removed from the configuration" ? Also delete him from the XG?
C) Can you please give me a best-practise how to setup the XG, that I'm able to control which user is allowed to connect with ssl vpn per AD group assignment and also if I remove the user from AD group that the user is not able to connect? Without any further configurations by hand. That would be awesome.
Did some testing. Hope this helps:
User:
InactiveUser
Groups (In AD): SEAdmin, VPN
Sync with AD (logged into User Portal):
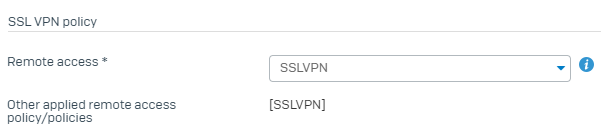
Everything is working as expected.
Now i disabled the User in AD.
Tried to login into the User Portal:
ERROR Oct 19 14:57:58 [ADS_AUTH]: adsauth_bind: bind failed: Invalid credentials
ERROR Oct 19 14:57:58 [ADS_AUTH]: adsauth_authenticate_user: 'IP': bind failed for User: 'Domain\inactive'
ERROR Oct 19 14:57:58 [ADS_AUTH]: adsauth_authenticate_user: ADS Authentication Failed for User:'inactive'
DEBUG Oct 19 14:57:58 [ADS_AUTH]: adsauth_parse_error_msg: message received from ldap server:"80090308: LdapErr: DSID-0C090453, comment: AcceptSecurityContext error, data 533, v3839"
ERROR Oct 19 14:57:58 [ADS_AUTH]: adsauth_parse_error_msg: ad error no: 1331
NOTICE Oct 19 14:57:58 [ADS_AUTH]: adsauth_handle_authrequest: ADS_AUTH: user authentication failed
https://stackoverflow.com/questions/10586546/error-533-in-active-directory-ldap/24360340
As i still have the certificate, lets try to use SSLVPN (Sophos Connect 2.0) to connect.
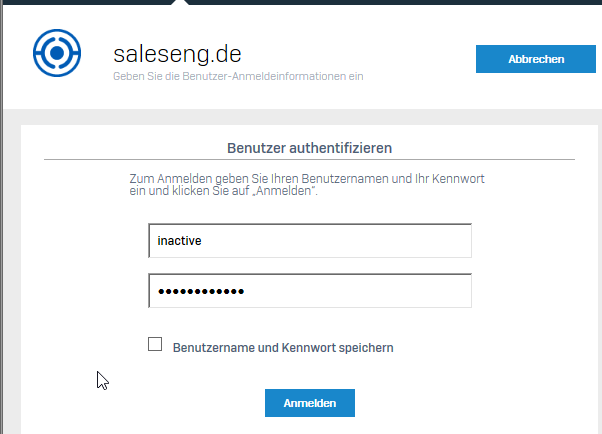
Same notification (not working anymore):
ERROR Oct 19 15:01:05 [ADS_AUTH]: adsauth_bind: bind failed: Invalid credentials
ERROR Oct 19 15:01:05 [ADS_AUTH]: adsauth_authenticate_user: '': bind failed for User: '\inactive'
ERROR Oct 19 15:01:05 [ADS_AUTH]: adsauth_authenticate_user: ADS Authentication Failed for User:'inactive'
DEBUG Oct 19 15:01:05 [ADS_AUTH]: adsauth_parse_error_msg: message received from ldap server:"80090308: LdapErr: DSID-0C090453, comment: AcceptSecurityContext error, data 533, v3839"
ERROR Oct 19 15:01:05 [ADS_AUTH]: adsauth_parse_error_msg: ad error no: 1331
NOTICE Oct 19 15:01:05 [ADS_AUTH]: adsauth_handle_authrequest: ADS_AUTH: user authentication failed
Access not possible anymore.
How to delete this user from XG?
There are two different approaches.
You can delete this user from AD and use the "Purge AD Users" in XG. This will ultimately look for users, "NOT existing" in AD. Disabled users are not covered by this feature.
(Deleted my User and purge AD Users).
If you disable a user in XG, you cannot authenticate him anymore, therefore he will not apply via Live users. So he cannot use the Firewall anymore.
__________________________________________________________________________________________________________________