Disclaimer: Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This article explains the steps to capture decrypted TCP dumps.
Product and Environment
Not product specific
Information
To capture decrypted dumps, do as follows:
-
Make sure Decryption is disabled on the endpoint from SophosCentral.
Note: For reference on how to disable the HTTPS Decryption, go to Turn decryption on or off. -
Put the script where you have write access to, right-click on it, and select Run with PowerShell. If there is any message about the execution policy, Select [Y] Yes to continue:

-
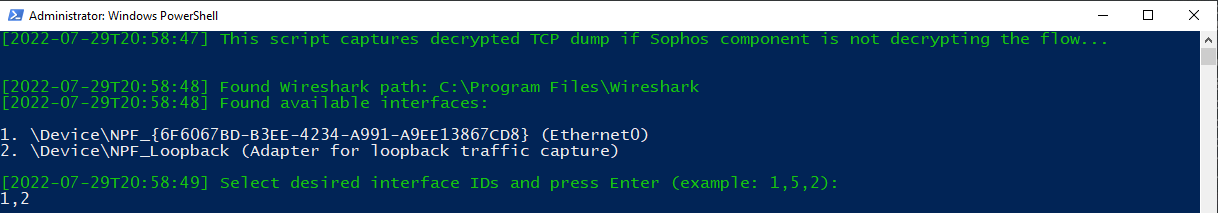
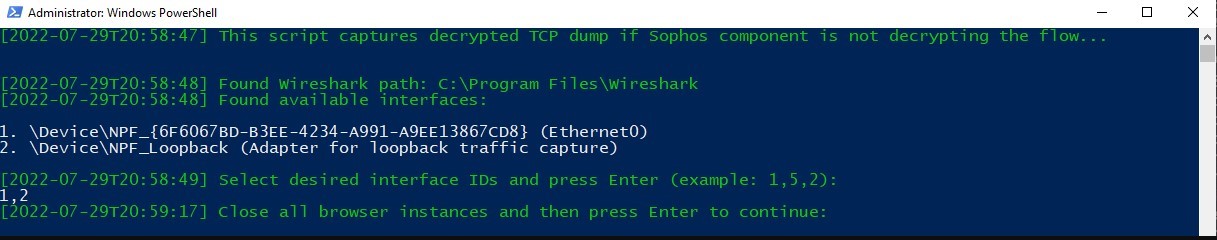
The scripts starts by reminding the user again that Sophos endpoint should not decrypt the flow. It then shows the Wireshark installation path and the available interfaces to capture packets. Select the desired interface IDs and press Enter:
-
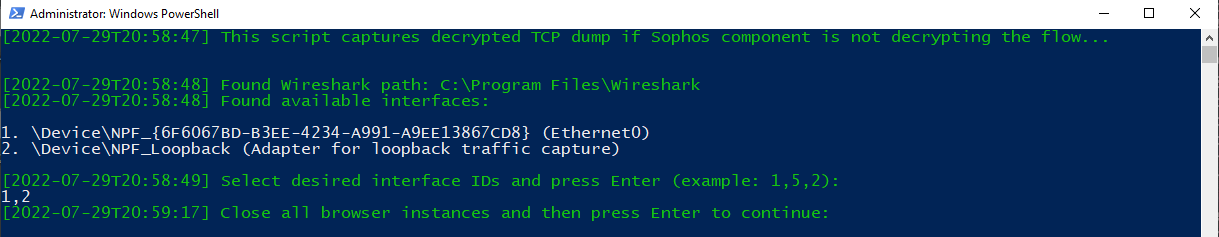
Close all browser instances and press Enter to continue:
-
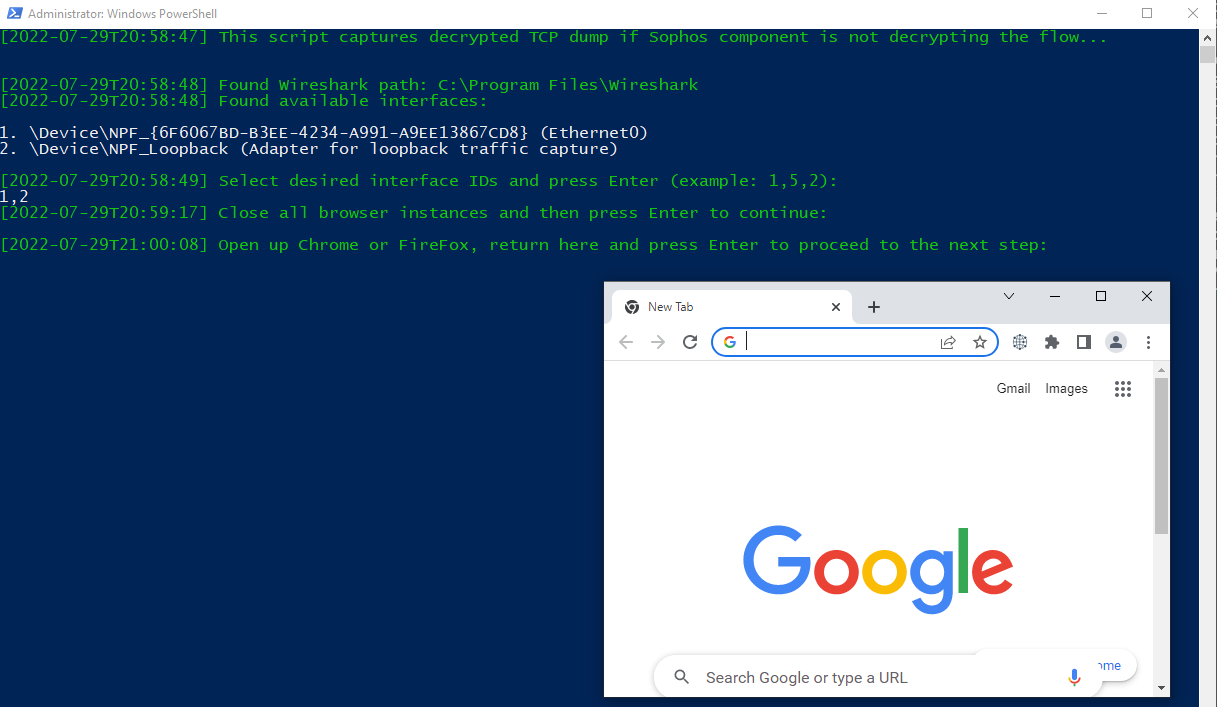
Open up a new instance of Google Chrome, Mozilla Firefox, or Microsoft Edge. When the browser is up, go back to the script and press Enter to proceed. A temporary key log file will be created next to the script.
-
Press Enter to start capturing packets. A child process
tshark.exewill be opened that shows the captured packets.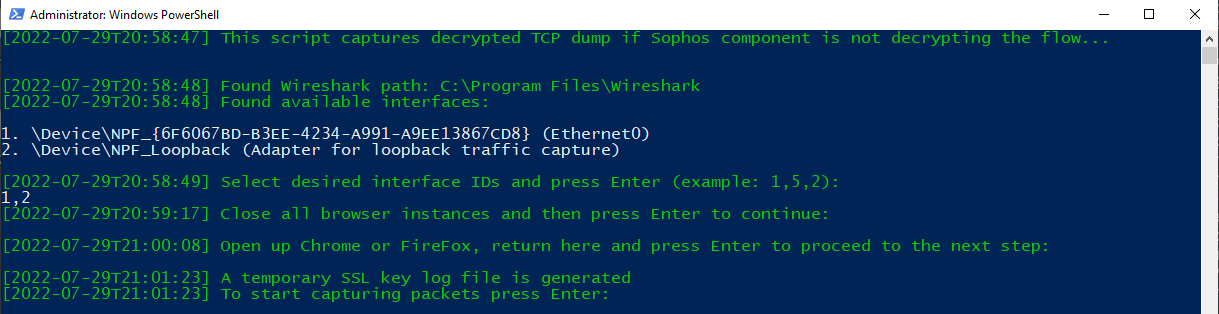
-
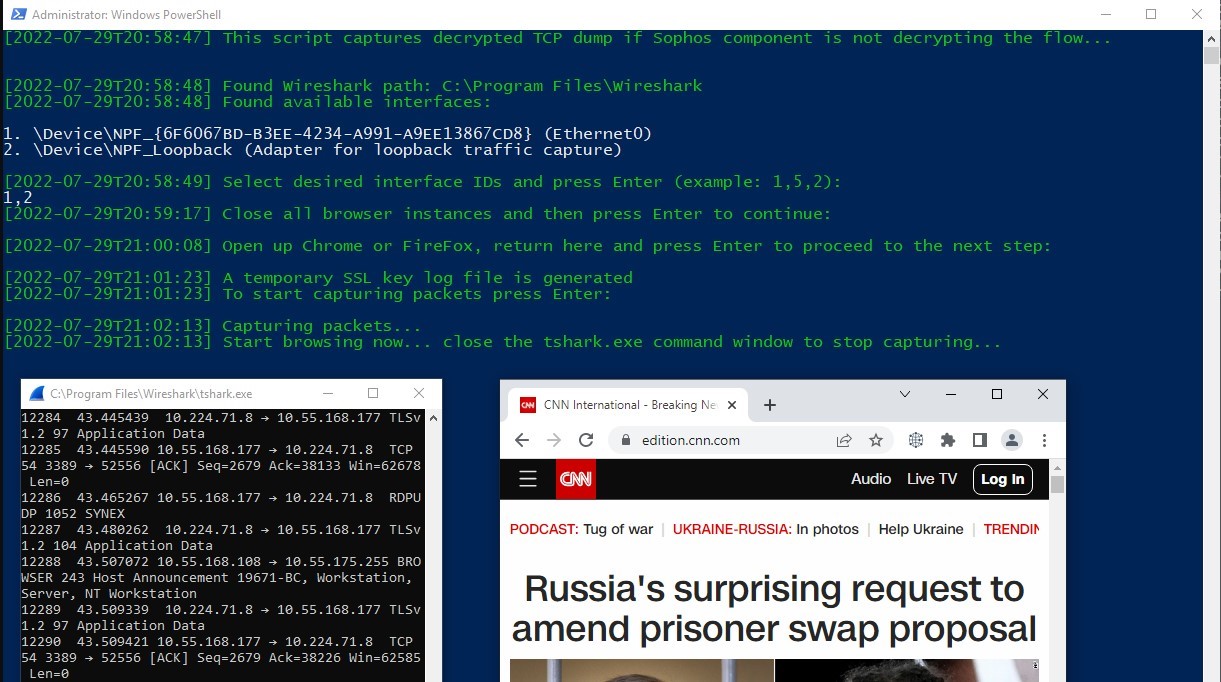
Browse HTTPS websites in the browser we already opened.
-
Close
tshark.exe. after browsing.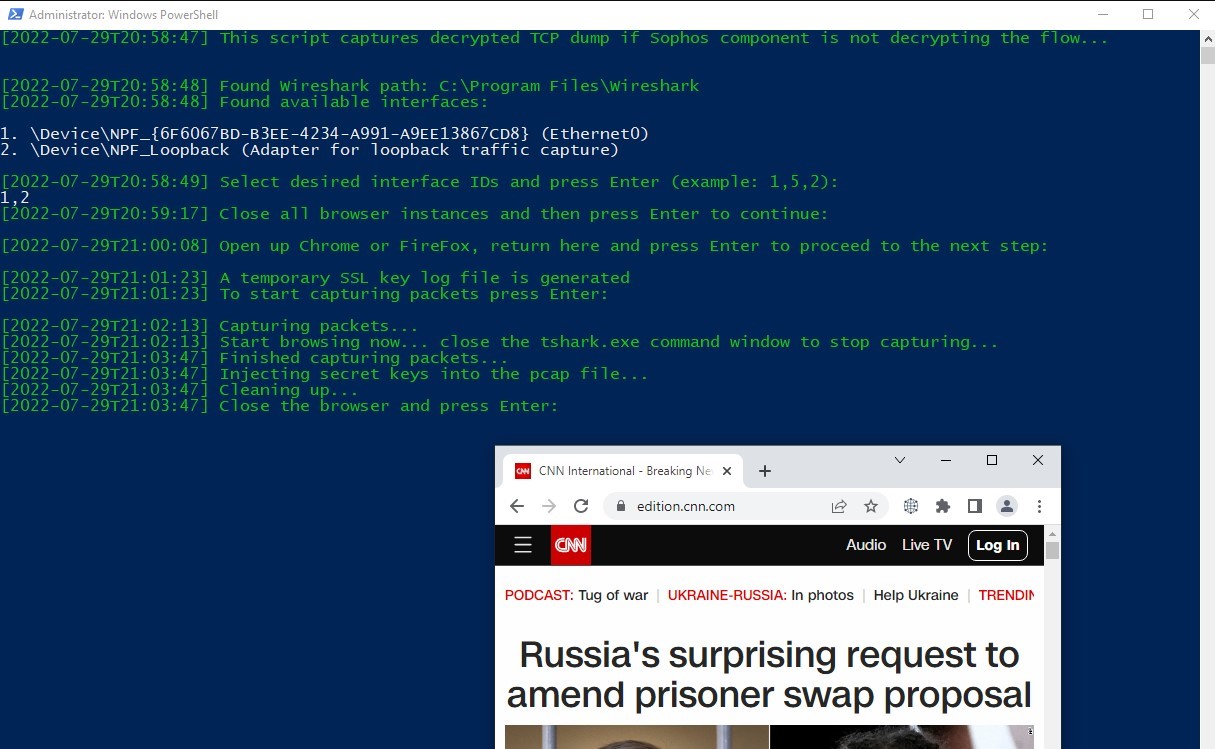
-
Close the browser. This deletes the temporary SSL key log file and writes the
pcapfile to the disk: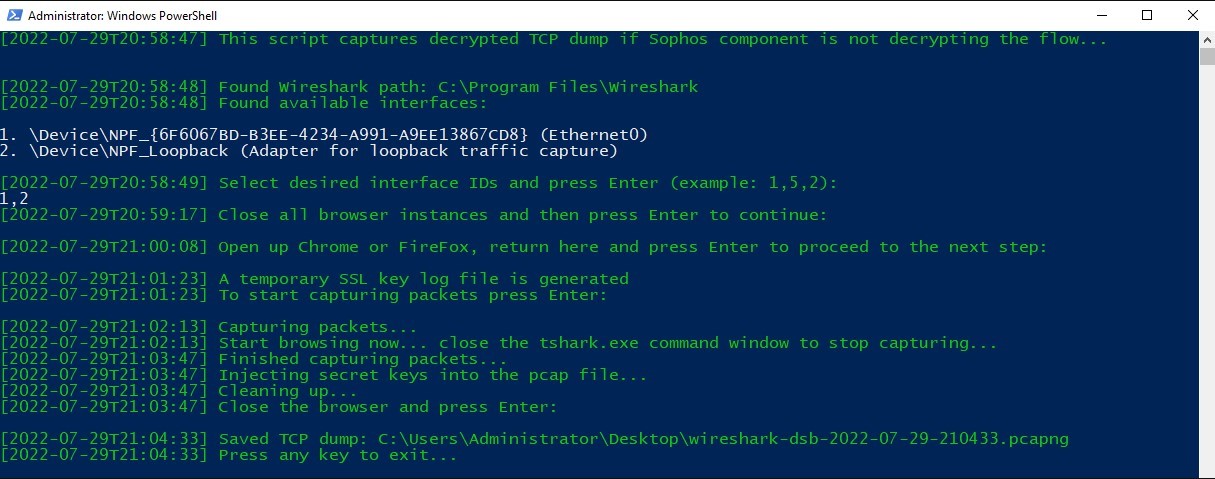
-
If we open the
pcapfile in Wireshark, we can see the decrypted traffic, which is also highlighted at the bottom bar: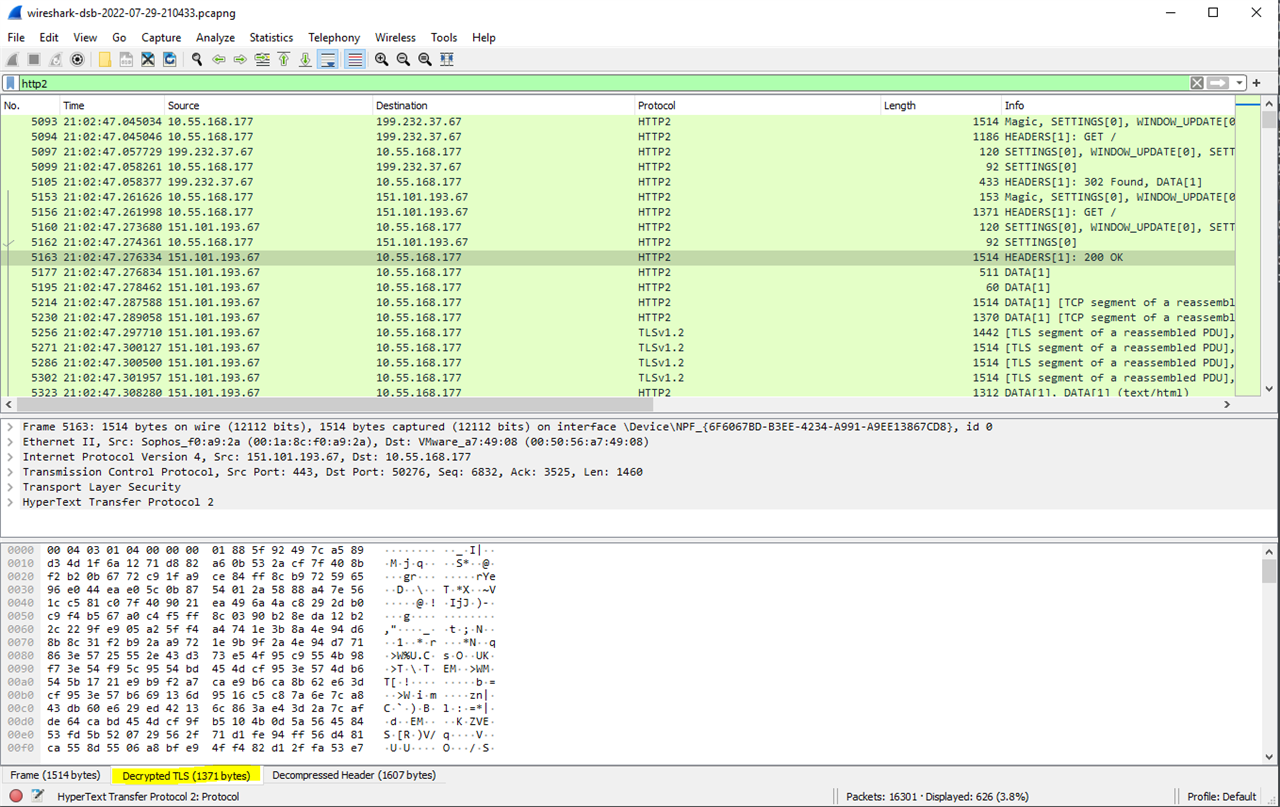
# Copyright 2022 Sophos Limited. All rights reserved. # Script for automating TCP dump capturing via Wireshark function GetTimestamp { $timestamp = Get-Date -Format s return "[$timestamp]" } # Find installation path even if it's not in system PATH function FindProgramInstallationPath { Param( [string]$programName, [string]$processorName ) $path = Get-ChildItem HKLM:\Software\Wow6432Node\Microsoft\Windows\CurrentVersion\Uninstall\* | % { Get-ItemProperty $_.PsPath } | Select DisplayName,InstallLocation | Select-String $programName if ($path -eq $null) { $path = Get-ChildItem HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\* | % { Get-ItemProperty $_.PsPath } | Select DisplayName,InstallLocation | Select-String $programName } if ($path -eq $null) { $path = Read-Host -Prompt "`nNo installation of $programName was found; enter absolute installation path" } else { $path = [regex]::Match($path, 'InstallLocation=(.*)}').captures.groups[1].value } Write-Host "`n" $processorPath = "$path\$processorName.exe" if (-not (Test-Path -Path $processorPath)) { Write-Host (GetTimestamp)"Failed to find $programName. Press any key to exit..." -ForegroundColor Red Read-Host exit 1 } Write-Host (GetTimestamp)"Found $programName path: $path" -ForegroundColor Green return $path } function GetInterfaceIds { Param( [string]$program ) Write-Host (GetTimestamp)"Found available interfaces:`n" -ForegroundColor Green Write-Host ((& $program\tshark -D) | Out-String) Write-Host (GetTimestamp)"Select desired interface IDs and press Enter (example: 1,5,2):" -ForegroundColor Green $interfaces = Read-Host return "-i " + ($interfaces -replace ',', ' -i ') } function SetSslKeyLogFilePath { Param( [string]$path ) if ($Env:SSLKEYLOGFILE -ne $null) { $keyLogFilePath = $Env:SSLKEYLOGFILE Write-Host (GetTimestamp)"SSL key log file path: $keyLogFilePath" -ForegroundColor Green Write-Host (GetTimestamp)"Warning: It is recommended to remove the environment varialbe SSLKEYLOGFILE and start again in a new Poweshell instance" -ForegroundColor Yellow Write-Host (GetTimestamp)"Do you want to remove the environment varialbe SSLKEYLOGFILE? (Y/N)" -ForegroundColor Green $response = Read-Host if (($response -eq "Y") -or ($response -eq "y")) { [System.Environment]::SetEnvironmentVariable('SSLKEYLOGFILE', $null, "User") Write-Host (GetTimestamp)"Successfully removed the environment variable. Start again in a new Poweshell instance." -ForegroundColor Green } Write-Host (GetTimestamp)"Press any key to exit..." -ForegroundColor Green Read-Host exit 1 } else { $temporaryKeyLogFile = $path + '\tempKeyLog.txt' [System.Environment]::SetEnvironmentVariable('SSLKEYLOGFILE', $temporaryKeyLogFile, "User") # needs to be set for the browser Write-Host (GetTimestamp)"Close all browser instances and then press Enter to continue:" -ForegroundColor Green $ignoredInput = Read-Host Write-Host (GetTimestamp)"Open up Chrome or FireFox, return here and press Enter to proceed to the next step:" -ForegroundColor Green $ignoredInput = Read-Host $keyLogFilePath = $temporaryKeyLogFile if (-not (Test-Path -Path $keyLogFilePath)) { Write-Host (GetTimestamp)"Error: Unable to create a temporary SSL key log. Close all browser instances, start again, and use Chrome or FireFox." -ForegroundColor Red [System.Environment]::SetEnvironmentVariable('SSLKEYLOGFILE', $null, "User") Write-Host (GetTimestamp)"Press any key to exit..." -ForegroundColor Red Read-Host exit 1 } else { Write-Host (GetTimestamp)"A temporary SSL key log file is generated" -ForegroundColor Green } } return $keyLogFilePath } function InjectSessionKeys { Param( [string]$installationPath, [string]$outputPath, [string]$keyLogFilePath, [string]$dumpFile ) Write-Host (GetTimestamp)"Injecting secret keys into the pcap file..." -ForegroundColor Green $decryptedDump = $outputPath + "\decrypted.pcapng" $tempKeyLog = "$outputPath\tempKeyLog.txt" if (-not (Test-Path -Path $tempKeyLog)) { $tlsKeyLogFile = "tls.keylog_file:$keyLogFilePath" $keyFile = $outputPath + "\tls.keys" $secrets = "tls,$keyFile" (& $installationPath\tshark -Q --export-tls-session-keys $keyFile -r $dumpFile -o $tlsKeyLogFile) if ((Get-Content $keyFile) -ne $null) { (& $installationPath\editcap --inject-secrets $secrets $dumpFile $decryptedDump) } } else { $secrets = "tls,$keyLogFilePath" (& $installationPath\editcap --inject-secrets $secrets $dumpFile $decryptedDump) } } function CleanUp { Param( [string]$path ) Write-Host (GetTimestamp)"Cleaning up..." -ForegroundColor Green # Revert back possible changes to environment variables $tempKeyLog = "$path\tempKeyLog.txt" if (Test-Path -Path $tempKeyLog) { Write-Host (GetTimestamp)"Close the browser and press Enter:" -ForegroundColor Green $ignoredInput = Read-Host [System.Environment]::SetEnvironmentVariable('SSLKEYLOGFILE', $null, "User") Remove-Item -Path $tempKeyLog if (Test-Path -Path $tempKeyLog) { Write-Host (GetTimestamp)"Close the browser and press Enter:" -ForegroundColor Green $ignoredInput = Read-Host Remove-Item -Path $tempKeyLog } } else { Remove-Item -Path "$path\tls.keys" } Remove-Item -Path "$path\encrypted.pcapng" $newName = "wireshark-dsb-" + (Get-Date -Format 'yyyy-MM-dd-HHmmss') + ".pcapng" Rename-Item -Path "$path\decrypted.pcapng" -NewName $newName Write-Host (GetTimestamp)"Saved TCP dump: $path\$newName" -ForegroundColor Green } Write-Host (GetTimestamp)"This script captures decrypted TCP dump if Sophos component is not decrypting the flow..." -ForegroundColor Green $wiresharkInstallationPath = FindProgramInstallationPath -programName Wireshark -processorName tshark $interfaces = GetInterfaceIds -program $wiresharkInstallationPath $currentPath = (Get-Location).ToString() $encryptedDump = $currentPath + "\encrypted.pcapng" $sslKeyLogFilePath = SetSslKeyLogFilePath -path $currentPath Write-Host (GetTimestamp)"To start capturing packets press Enter:" -ForegroundColor Green $ignoredInput = Read-Host Write-Host (GetTimestamp)"Capturing packets..." -ForegroundColor Green Write-Host (GetTimestamp)"Start browsing now... close the tshark.exe command window to stop capturing..." -ForegroundColor Green Start-Process -FilePath $wiresharkInstallationPath\tshark -ArgumentList($interfaces, '-w', $encryptedDump, '--print') -Wait Write-Host (GetTimestamp)"Finished capturing packets..." -ForegroundColor Green InjectSessionKeys -installationPath $wiresharkInstallationPath -outputPath $currentPath -keyLogFilePath $sslKeyLogFilePath -dumpFile $encryptedDump CleanUp -path $currentPath Write-Host (GetTimestamp)"Press any key to exit..." -ForegroundColor Green Read-Host exit 1 Sign up for the Sophos Support Notification Service to receive proactive SMS alerts for Sophos products and Sophos Central services.
Added link to Central documentation
[edited by: Gladys at 10:06 AM (GMT -7) on 22 Mar 2024]

