Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
Overview
This article describes how to deploy a Sophos XG Firewall in an existing VPC in AWS.
Note: In this case of deployment, the subnets, route tables, and Internet Gateway need to be created in advance.
Table of Contents
Pre-requisites
- A VPC pre-created.
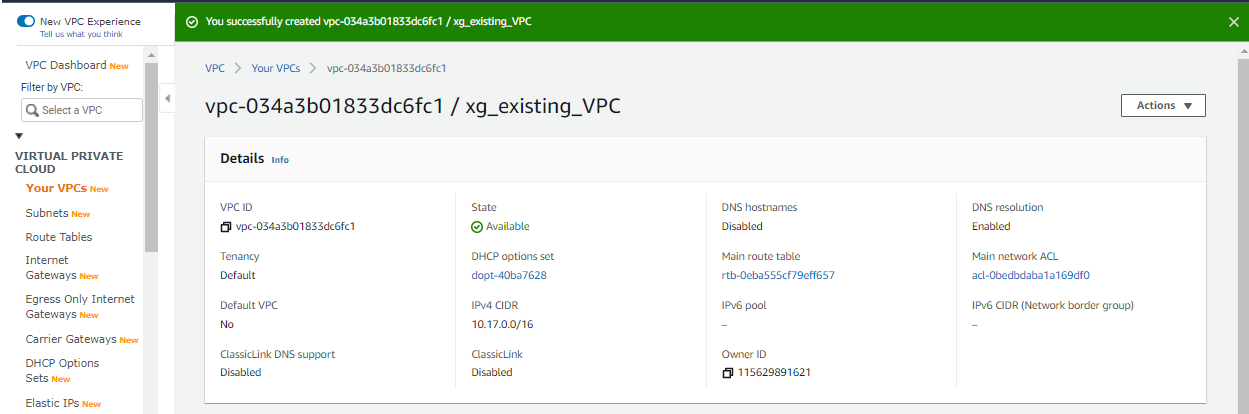
- Private subnet in the VPC.
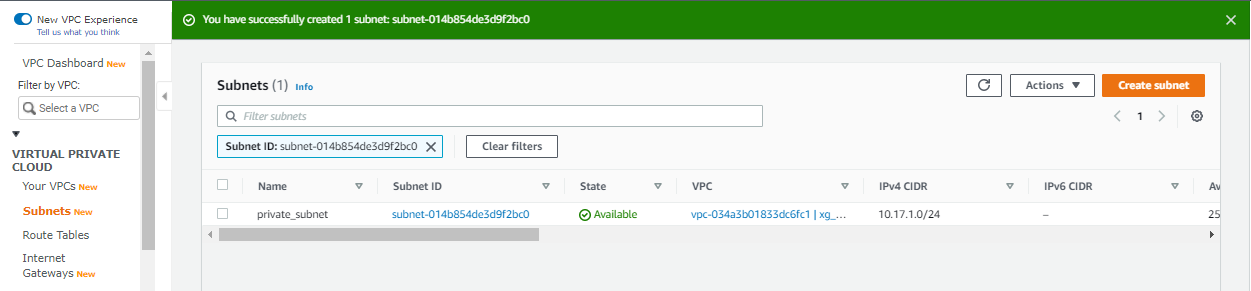
- Public subnet in the VPC.
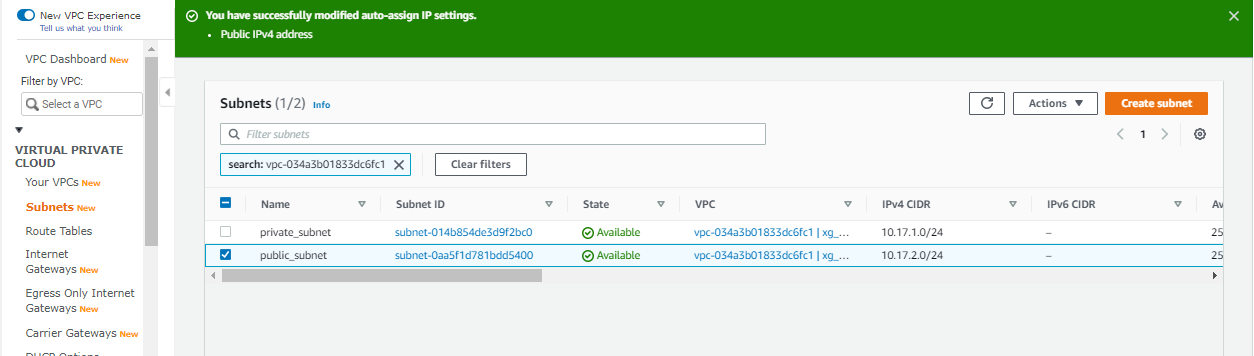
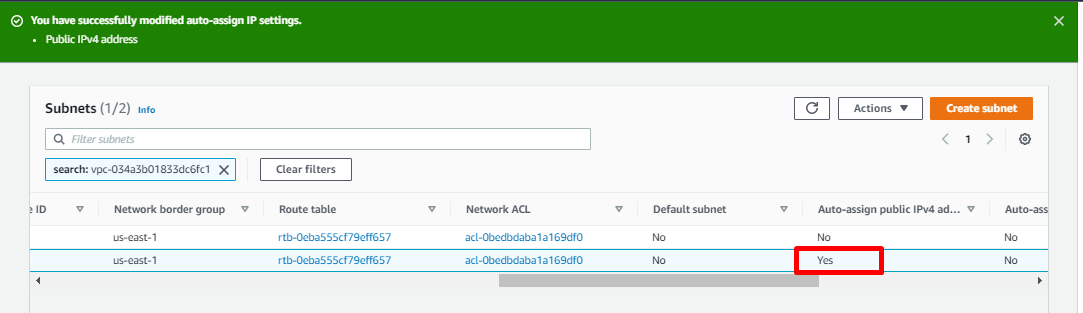
- Ensure that the Auto-assign public IPv4 address is set to Yes for the public subnet.
- Ensure that an Internet Gateway is created and is attached to the VPC.
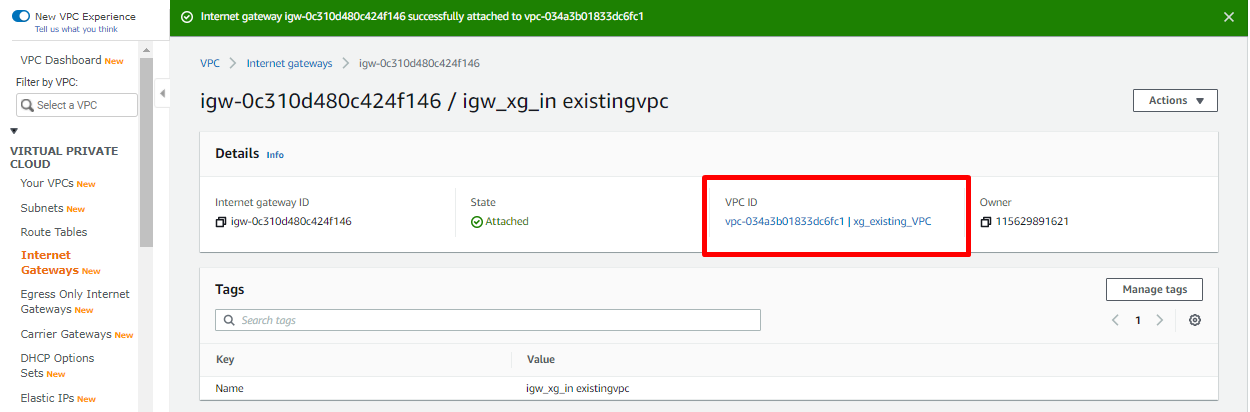
Information needed before the deployment
- Existing VPC ID in the format vpc-<random AWS generated number>
- Existing Subnet ID for Private Subnet in the format subnet-<random AWS generated number>
- Existing Subnet ID for Public Subnet the format subnet-<random AWS generated number>
Launch Sophos XG Instance from Marketplace
- Sign in to AWS console https://console.aws.amazon.com/.
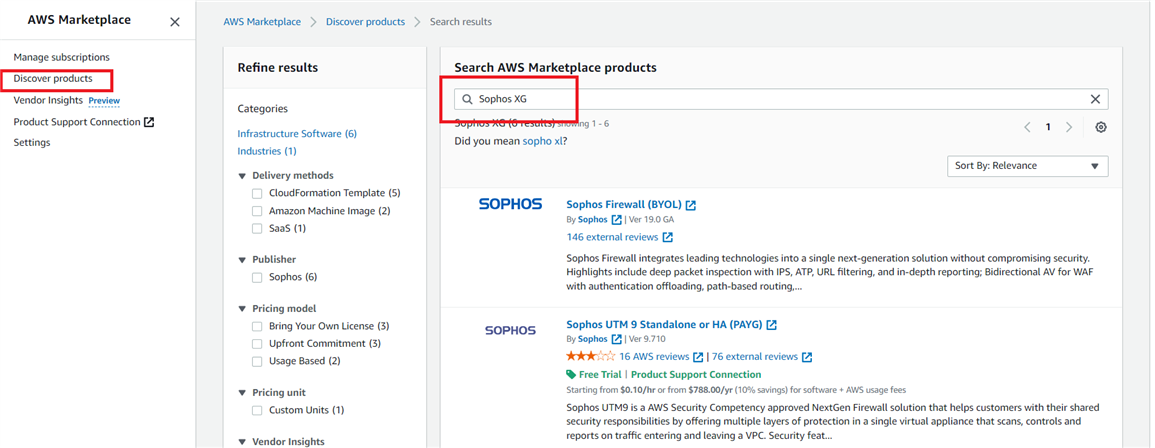
- From the Search bar, search for AWS marketplace and navigate to Discover products.
- In the AWS marketplace search bar, search for Sophos XG and click on Sophos XG Firewall Standalone (BYOL), if using the BYOL model of licensing.
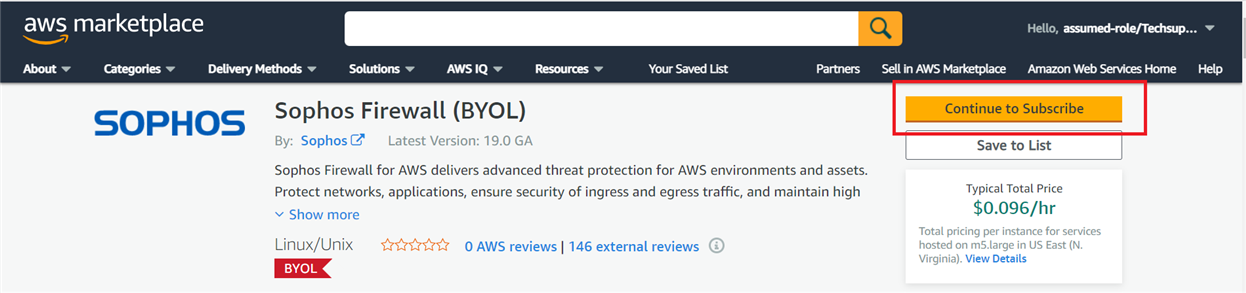
- In the marketplace page that opens in a new tab, click on Continue to Subscribe.
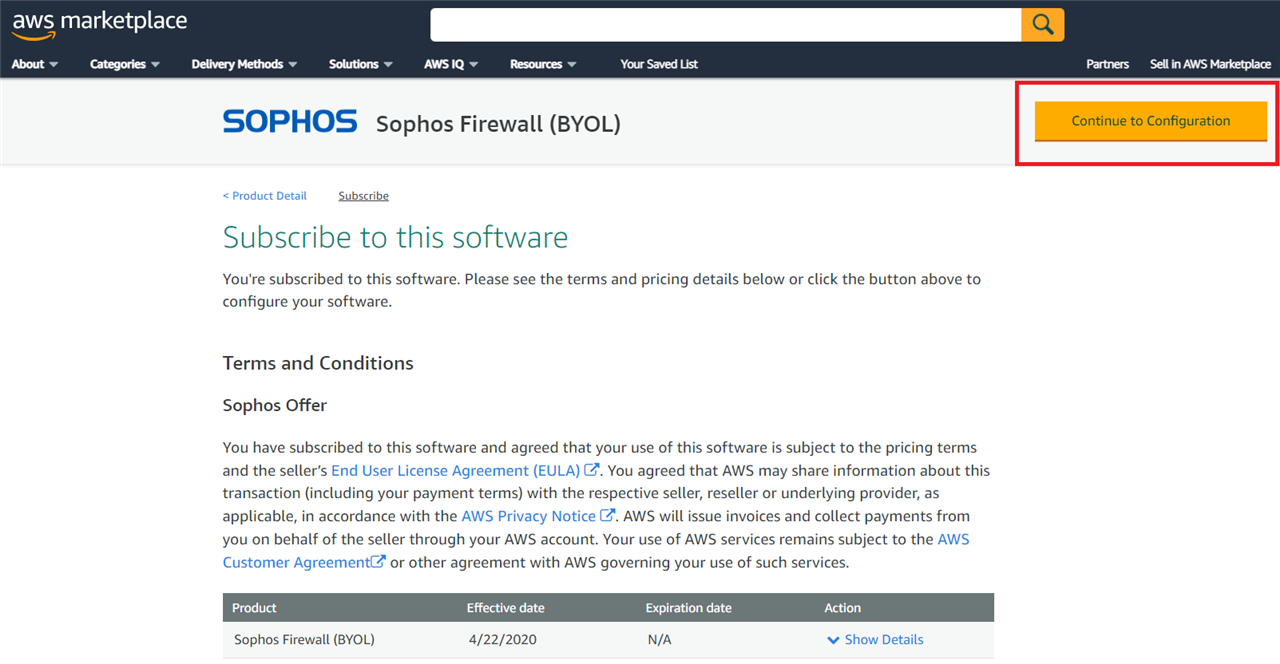
- On the subsequent page, click on Continue to Configuration.
- Select the relevant region from the drop-down and click on Continue to Launch.
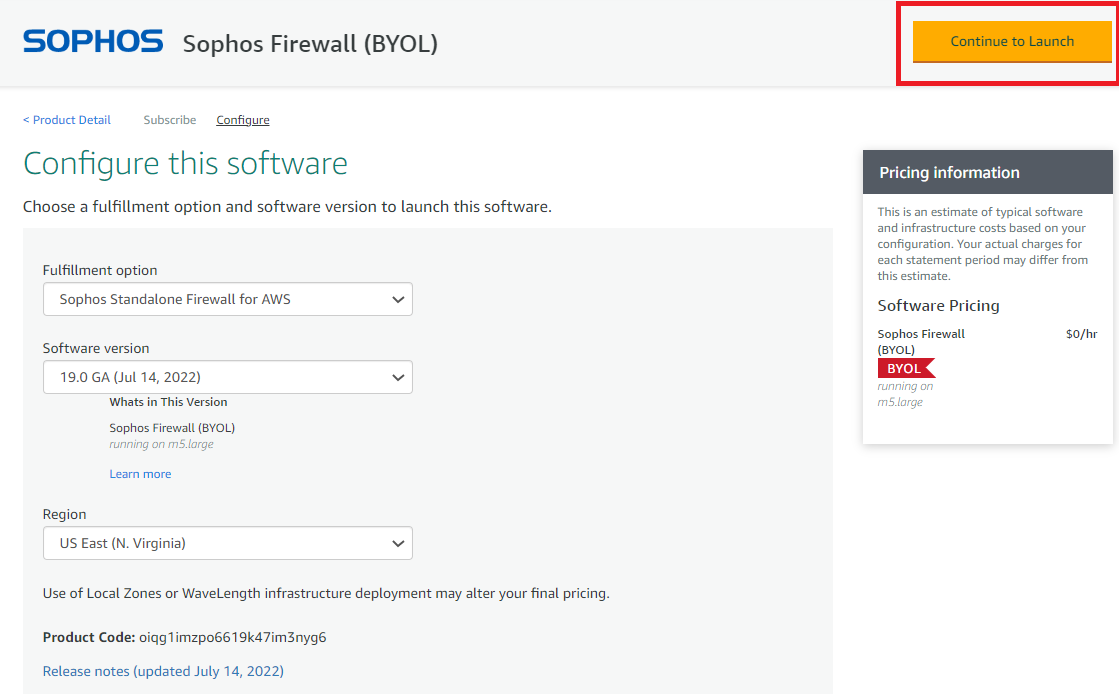
- Choose Action as Launch CloudFormation and click on Launch.
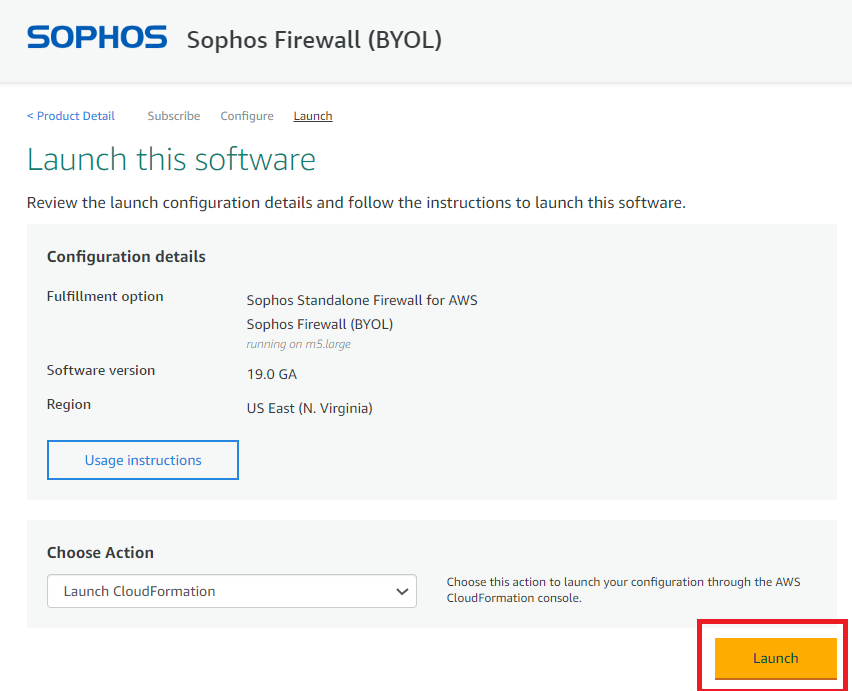
CloudFormation template deployment process
- On clicking the Launch button, you’ll automatically be redirected to CloudFormation>Stacks>Create stack page, with a pre-populated Amazon S3 URL. Click Next.
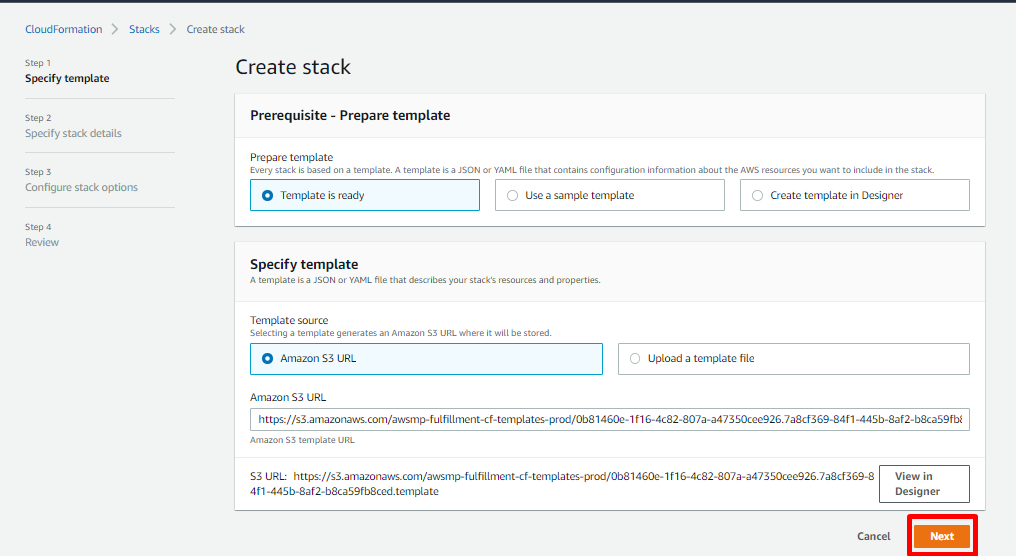
- In the specify stack details page, fill in the deployment as follows.
Stack nameDescriptionValues in current scenario setupStack name Enter an account name unique to the AWS account <Any unique descriptive name> Parameters Description Values in current scenario setup AMI ID (required) Leave the value as-is.
autodetect Instance Size (required) Enter the EC2 size of your choice-https://aws.amazon.com/ec2/instance-types/ (The size must support a minimum of 2 NICs) E.g. m5.large m5.large AvailabilityZone for deployment (required) Select the same Availability Zone where the private and public subnets are also deployed. us-east-1a Network Address Prefix for new VPC (required) Leave the value as-is. This parameter is not considered while deploying in existing VPC 10.15 Deploy to an existing VPC The existing VPC ID vpc-<random AWS generated number> The existing public subnet ID The existing Public Subnet ID subnet-<random AWS generated number> The existing private subnet ID The existing Private Subnet ID subnet-<random AWS generated number> Trusted Network CIDR (required) The public network from which Sophos XG firewall will be accessible on port 4444 and port 22 x.x.x.x/24
(cannot be 0.0.0.0/0)
Using Elastic IP (required) Select yes to allow public access to Sophos XG on the WAN elastic Network Interface Interface. yes Existing Elastic IP Allocation ID Enter existing Elastic IP ID or leave the field as is <blank> XG Firewall Configuration XG Firewall Name (required) Provide a name tag of choice. XG-Firewall Pricing Option (required) Select BYOL if you're using a license that you bought from Sophos. Select PAYG if you'll be paying for the license as part of your AWS charges. BYOL XG License Serial Number Enter the serial number if the license is purchased as part of BYOL <blank> Admin Password (required) Enter a secure password of at least 10 characters.( At least 1 lowercase and 1 uppercase letter. At least one numeric character. At least one special character) <any secure password > SSH KeyPair Name (required) Select an existing KeyPair from the drop-down. <key-pair available in your account> Other Configuration
I accept the Sophos End User License Agreement and acknowledge the Sophos Privacy Policy (required) Read and accept the EULAR to proceed with the deployment. yes Opt in to the customer experience improvement program (required)
Details on the use of Sophos XG firewall by the users. on - Leave the Configure stack options page as-is and click on Next.
-
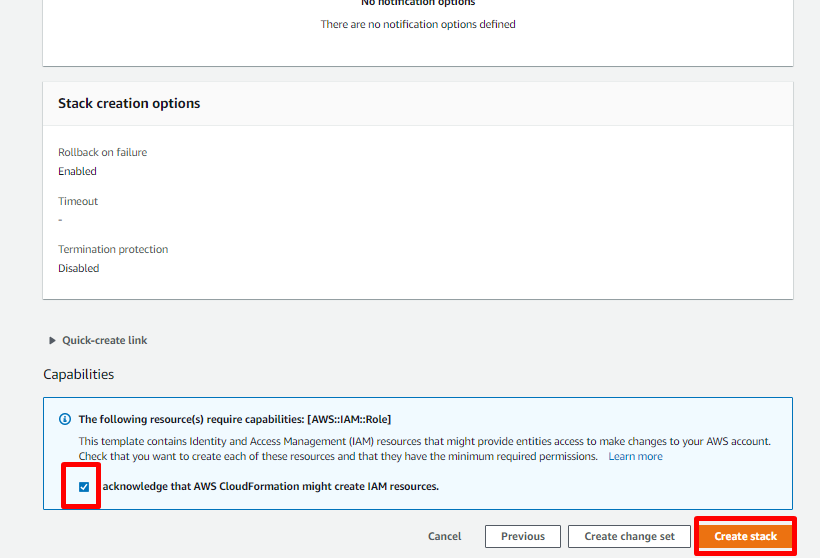
On the Review page, review the parameters configured. Tick on the check box to authorize the creation of IAM resources and click on Create stack.
Post-deployment process
- After the CloudFormation deployment completes, navigate to VPC>VIRTUAL PRIVATE CLOUD >Route Tables. Filter the VPC to check for the route tables created.
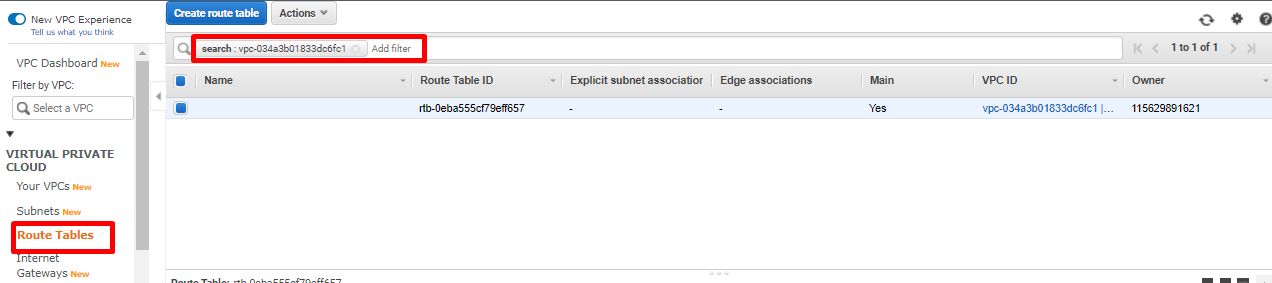
- We will now create two route tables that will be explicitly associated with the Public and Private subnet.
Route table for public subnet
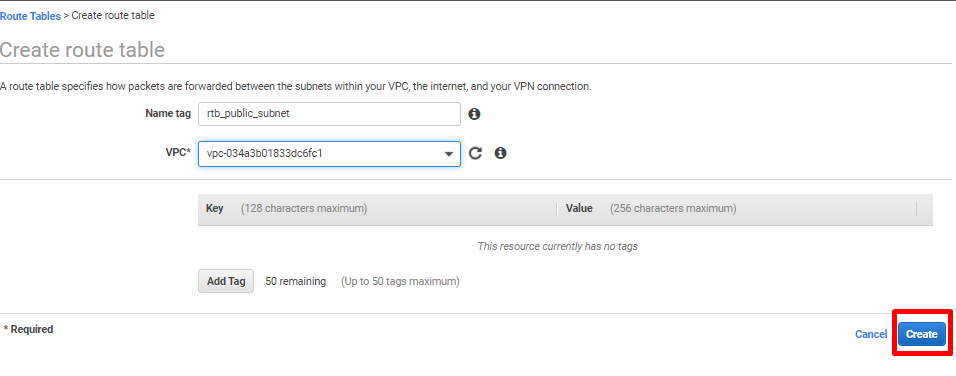
- Click on Create route table.
- Provide a descriptive Name tag as this route table will be associated with the public subnet. Select the existing VPC used for deployment purposes. Click on Create.
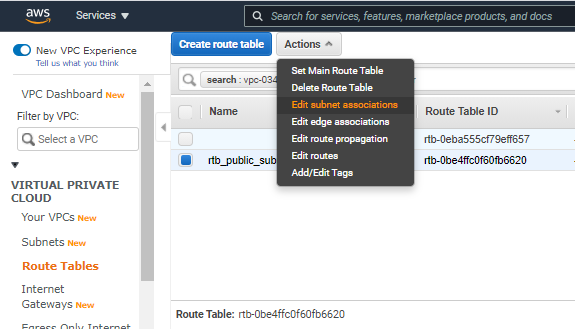
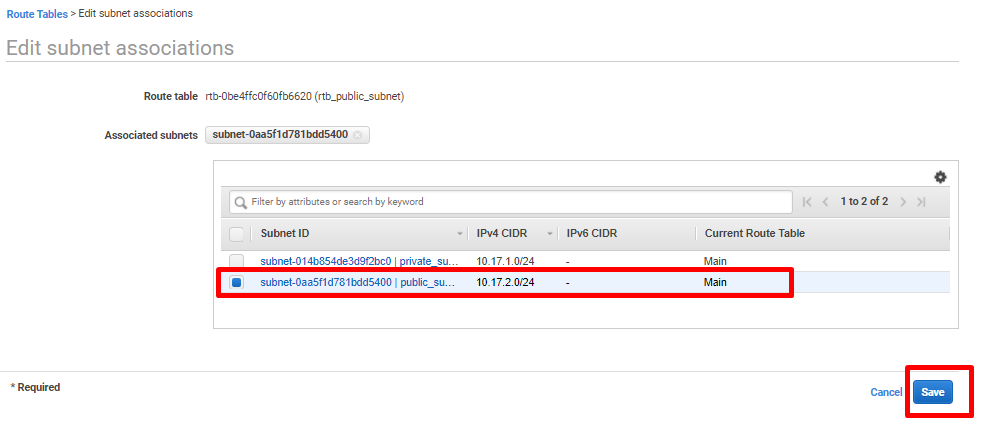
- Select the newly created route table and click on Actions>Edit subnet associations.
- Select the pre-created public subnet and click Save.
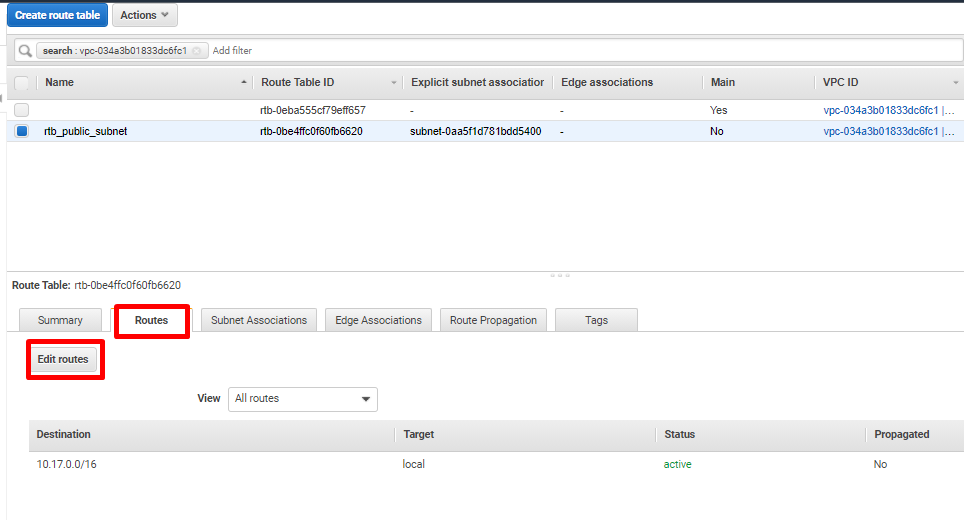
- Select the route table associated with the public subnet and navigate to Routes from the bottom menu. Click on Edit routes.
- Click on Add route.
Destination: 0.0.0.0/0
Target: igw-<AWS generated random number> (Select the pre-created Internet Gateway)
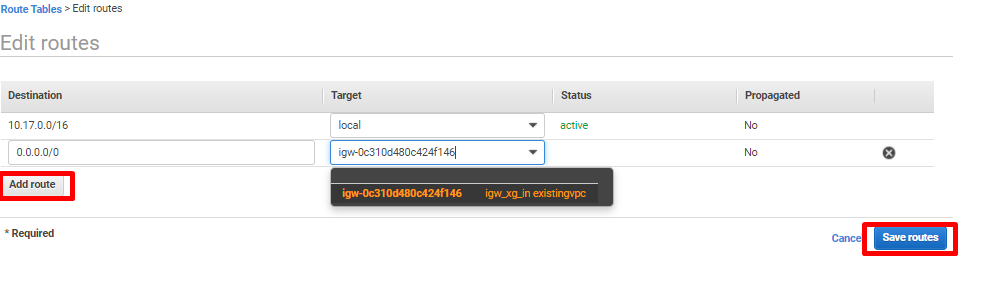
- Click on Save routes.
Route table for private subnet
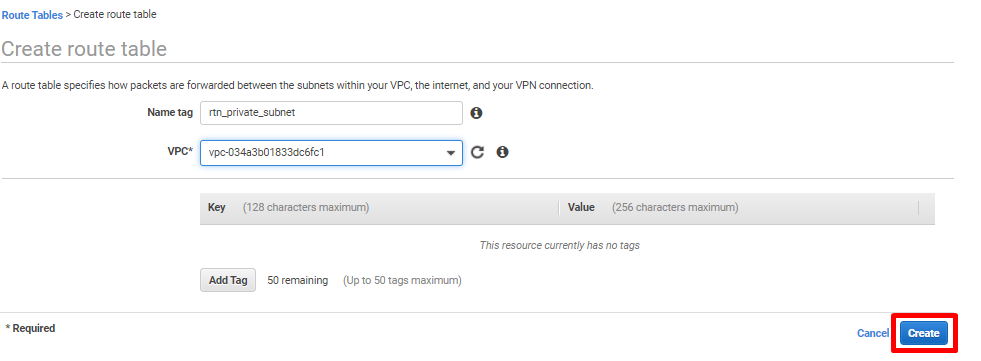
- Click on Create route table.
- Provide a descriptive Name tag as this route table will be associated with the private subnet. Select the existing VPC used for deployment purposes. Click on Create.
- Select the newly created route table and click on Actions>Edit subnet associations.
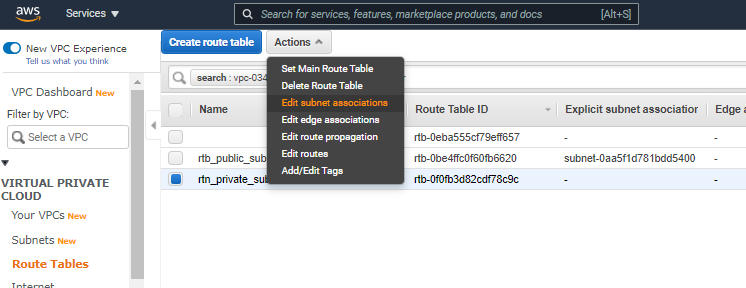
- Select the pre-created private subnet and click Save.
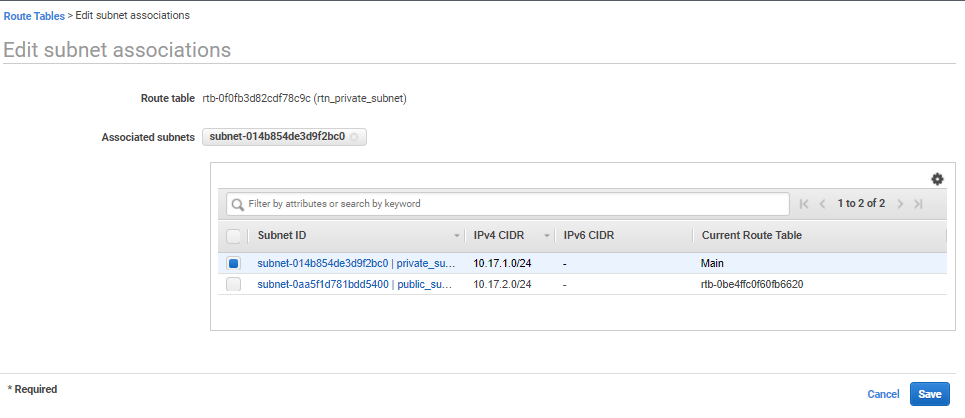
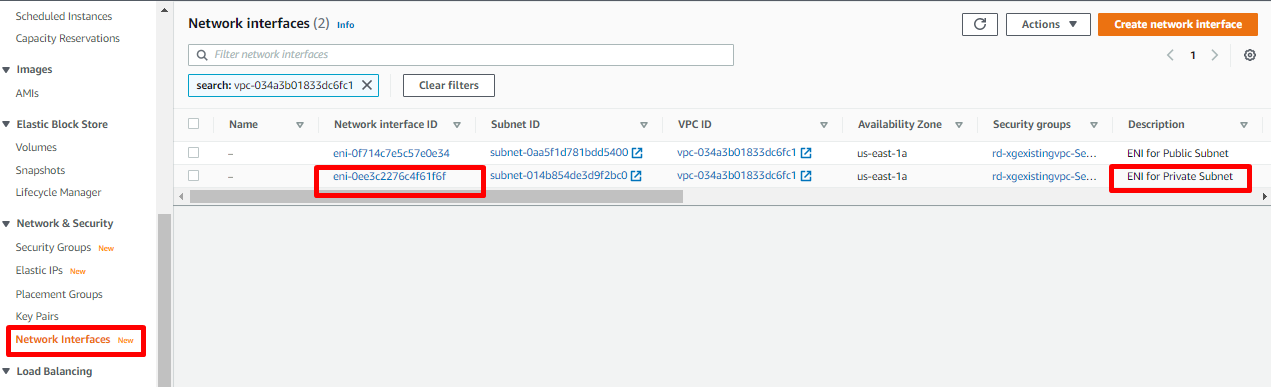
- Navigate to EC2>Network & Security>Network Interfaces. On the Network interfaces page, filter network interfaces using the VPC ID. Copy the Network Interface ID, with Description as ENI for Private Subnet.
- Select the route table associated with the public subnet and navigate to Routes from the bottom menu. Click on Edit routes.
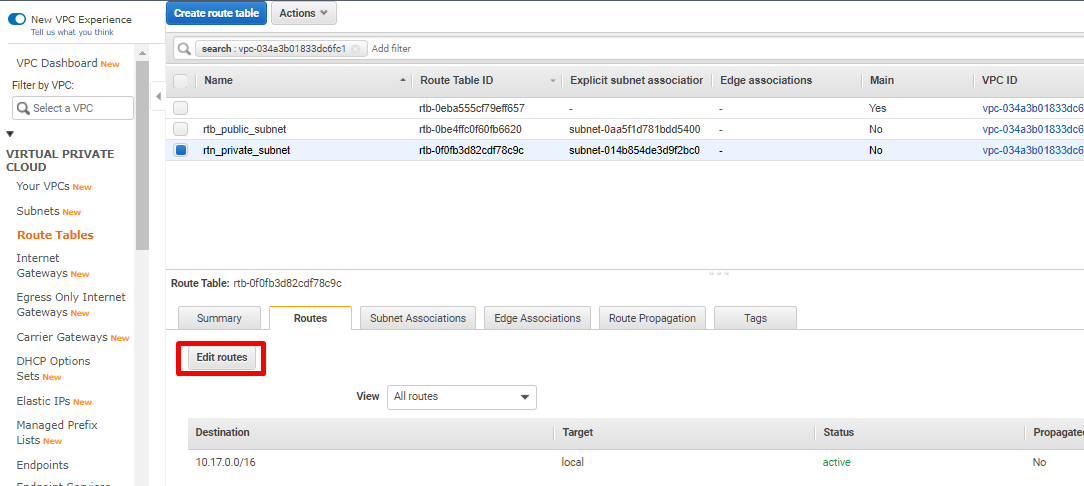
-
Click on Add Route.
Destination :0.0.0.0/0
Target: Select the eni interface ID as noted from Step2(e).
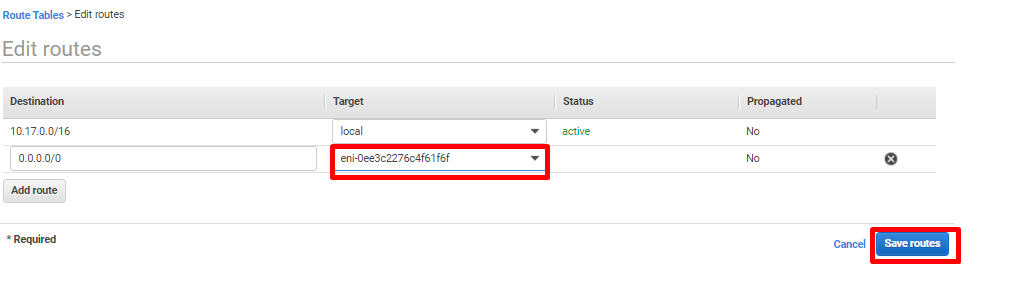
- Click on Save routes.
Added TAGs
[edited by: Raphael Alganes at 7:38 AM (GMT -7) on 17 Sep 2024]
