Hallo Zusammen,
ich habe folgendes Problem, das sich die VPN Verbindung zu einem Partner nicht aufbaut.
Die Vorraussetzungen sind wie folgt:
Einstellung Gegenseite: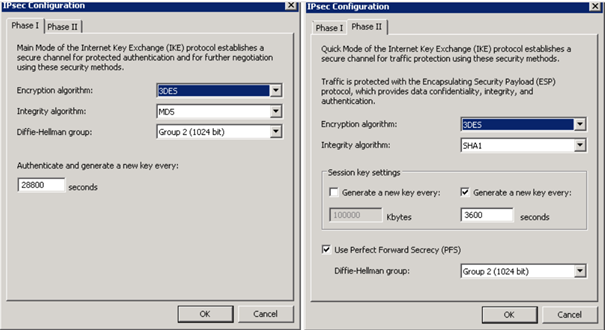
Meine Einstellung Sophos-Seite:



Teile aus dem LOG File:
2021-08-13 08:44:39 03[NET] received packet: from 154.14.X.X[500] to 217.86.Y.Y[500] on Port2_ppp
2021-08-13 08:44:39 03[NET] waiting for data on sockets
2021-08-13 08:44:39 21[NET] <27825> received packet: from 154.14.X.X[500] to 217.86.Y.Y[500] (228 bytes)
2021-08-13 08:44:39 21[ENC] <27825> parsed ID_PROT request 0 [ SA V V V V V V V ]
2021-08-13 08:44:39 21[CFG] <27825> looking for an ike config for 217.86.Y.Y...154.14.X.X
2021-08-13 08:44:39 21[CFG] <27825> candidate: 217.86.Y.Y...%any, prio 1052
2021-08-13 08:44:39 21[CFG] <27825> candidate: 217.86.Y.Y...%any, prio 1052
2021-08-13 08:44:39 21[CFG] <27825> candidate: 217.86.Y.Y...154.14.X.X, prio 3100
2021-08-13 08:44:39 21[CFG] <27825> found matching ike config: 217.86.Y.Y...154.14.X.X with prio 3100
2021-08-13 08:44:39 21[IKE] <27825> received MS NT5 ISAKMPOAKLEY vendor ID
2021-08-13 08:44:39 21[IKE] <27825> received NAT-T (RFC 3947) vendor ID
2021-08-13 08:44:39 21[IKE] <27825> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2021-08-13 08:44:39 21[IKE] <27825> received FRAGMENTATION vendor ID
2021-08-13 08:44:39 21[ENC] <27825> received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
2021-08-13 08:44:39 21[ENC] <27825> received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
2021-08-13 08:44:39 21[ENC] <27825> received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
2021-08-13 08:44:39 21[IKE] <27825> 154.14.X.X is initiating a Main Mode IKE_SA
2021-08-13 08:44:39 21[IKE] <27825> IKE_SA (unnamed)[27825] state change: CREATED => CONNECTING
2021-08-13 08:44:39 21[CFG] <27825> selecting proposal:
2021-08-13 08:44:39 21[CFG] <27825> proposal matches
2021-08-13 08:44:39 21[CFG] <27825> received proposals: IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024
2021-08-13 08:44:39 21[CFG] <27825> configured proposals: IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_8192/MODP_2048
2021-08-13 08:44:39 21[CFG] <27825> selected proposal: IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024
2021-08-13 08:44:39 21[IKE] <27825> sending XAuth vendor ID
2021-08-13 08:44:39 21[IKE] <27825> sending DPD vendor ID
2021-08-13 08:44:39 21[IKE] <27825> sending Cisco Unity vendor ID
2021-08-13 08:44:39 21[IKE] <27825> sending FRAGMENTATION vendor ID
2021-08-13 08:44:39 21[IKE] <27825> sending NAT-T (RFC 3947) vendor ID
2021-08-13 08:44:39 21[ENC] <27825> generating ID_PROT response 0 [ SA V V V V V ]
2021-08-13 08:44:39 21[NET] <27825> sending packet: from 217.86.Y.Y[500] to 154.14.X.X[500] (176 bytes)
2021-08-13 08:44:39 04[NET] sending packet: from 217.86.Y.Y[500] to 154.14.X.X[500]
2021-08-13 08:44:39 03[NET] received packet: from 154.14.X.X[500] to 217.86.Y.Y[500] on Port2_ppp
2021-08-13 08:44:39 03[NET] waiting for data on sockets
2021-08-13 08:44:39 22[NET] <27825> received packet: from 154.14.X.X[500] to 217.86.Y.Y[500] (252 bytes)
2021-08-13 08:44:39 22[ENC] <27825> parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
2021-08-13 08:44:39 22[IKE] <27825> remote host is behind NAT
2021-08-13 08:44:39 22[CFG] <27825> candidate "VPN_Iphone_Mac-1", match: 1/1/1052 (me/other/ike)
2021-08-13 08:44:39 22[CFG] <27825> candidate "L2TP_Schulzdialog-1", match: 1/1/1052 (me/other/ike)
2021-08-13 08:44:39 22[CFG] <27825> candidate "from_certis-1", match: 1/1/3100 (me/other/ike)
2021-08-13 08:44:39 22[ENC] <27825> generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
2021-08-13 08:44:39 22[NET] <27825> sending packet: from 217.86.Y.Y[500] to 154.14.X.X[500] (236 bytes)
2021-08-13 08:44:39 04[NET] sending packet: from 217.86.Y.Y[500] to 154.14.X.X[500]
2021-08-13 08:44:39 03[NET] received packet: from 154.14.X.X[4500] to 217.86.Y.Y[4500] on Port2_ppp
2021-08-13 08:44:39 03[NET] waiting for data on sockets
2021-08-13 08:44:39 18[NET] <27825> received packet: from 154.14.X.X[4500] to 217.86.Y.Y[4500] (68 bytes)
2021-08-13 08:44:39 18[ENC] <27825> parsed ID_PROT request 0 [ ID HASH ]
2021-08-13 08:44:39 18[CFG] <27825> looking for pre-shared key peer configs matching 217.86.Y.Y...154.14.X.X[10.48.15.2]
2021-08-13 08:44:39 18[CFG] <27825> candidate "VPN_Iphone_Mac-1", match: 1/1/1052 (me/other/ike)
2021-08-13 08:44:39 18[CFG] <27825> candidate "L2TP_Schulzdialog-1", match: 1/1/1052 (me/other/ike)
2021-08-13 08:44:39 18[CFG] <27825> selected peer config "L2TP_Schulzdialog-1"
2021-08-13 08:44:39 18[IKE] <L2TP_Schulzdialog-1|27825> IKE_SA L2TP_Schulzdialog-1[27825] established between 217.86.Y.Y[217.86.Y.Y]...154.14.X.X[10.48.15.2]
2021-08-13 08:44:39 18[IKE] <L2TP_Schulzdialog-1|27825> IKE_SA L2TP_Schulzdialog-1[27825] state change: CONNECTING => ESTABLISHED
2021-08-13 08:44:39 18[IKE] <L2TP_Schulzdialog-1|27825> DPD not supported by peer, disabled
2021-08-13 08:44:39 18[ENC] <L2TP_Schulzdialog-1|27825> generating ID_PROT response 0 [ ID HASH ]
2021-08-13 08:44:39 18[NET] <L2TP_Schulzdialog-1|27825> sending packet: from 217.86.Y.Y[4500] to 154.14.X.X[4500] (68 bytes)
2021-08-13 08:44:39 04[NET] sending packet: from 217.86.Y.Y[4500] to 154.14.X.X[4500]
2021-08-13 08:44:39 03[NET] received packet: from 154.14.X.X[4500] to 217.86.Y.Y[4500] on Port2_ppp
2021-08-13 08:44:39 03[NET] waiting for data on sockets
2021-08-13 08:44:39 31[NET] <L2TP_Schulzdialog-1|27825> received packet: from 154.14.X.X[4500] to 217.86.Y.Y[4500] (324 bytes)
2021-08-13 08:44:39 31[ENC] <L2TP_Schulzdialog-1|27825> parsed QUICK_MODE request 1 [ HASH SA KE No ID ID ]
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> ### process_request invoking quick_mode_create
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> ### quick_mode_create: 0x7fedf4005930 config (nil)
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> ### process_r: 0x7fedf4005930 QM_INIT
2021-08-13 08:44:39 31[CFG] <L2TP_Schulzdialog-1|27825> looking for a child config for 192.0.0.0/24 === 10.48.15.2/32
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> trying other candidates from phase 1
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> no matching CHILD_SA config found
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> queueing INFORMATIONAL task, already 0 tasks queued
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> flush_queue(IKE_NATD)
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> ### destroy: 0x7fedf4005930
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> activating new tasks
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> activating INFORMATIONAL task
2021-08-13 08:44:39 31[ENC] <L2TP_Schulzdialog-1|27825> generating INFORMATIONAL_V1 request 1799460334 [ HASH N(INVAL_ID) ]
2021-08-13 08:44:39 31[NET] <L2TP_Schulzdialog-1|27825> sending packet: from 217.86.Y.Y[4500] to 154.14.X.X[4500] (68 bytes)
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> activating new tasks
2021-08-13 08:44:39 31[IKE] <L2TP_Schulzdialog-1|27825> nothing to initiate
2021-08-13 08:44:39 04[NET] sending packet: from 217.86.Y.Y[4500] to 154.14.X.X[4500]
Added TAGs
[edited by: Erick Jan at 5:12 AM (GMT -7) on 29 May 2023]



