Reaching out to kind, wonderful, HELPFUL community! (Buttering you guys up) :-)
IN all seriousness... I am hoping ANYONE can help me out answering a few (Possibly dumb) questions that I seem to not be able to get answers for. (been waiting over a week to get this answered from Sophos support).
TOPIC: STAS Suite on Windows Servers (In particular Multiple DC's)
Question:
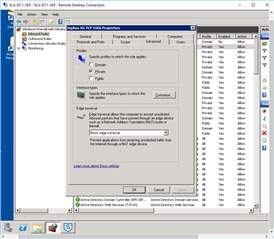
1. SHOULD I BE able to "TEST Connectivity" Between my 2 DC's (BOTH RUNNING SUITE)? YES / NO?
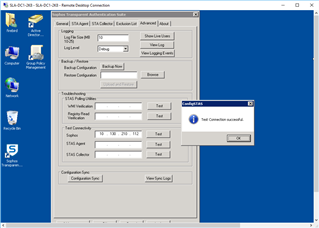
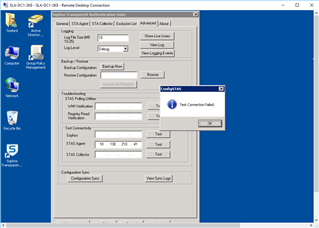
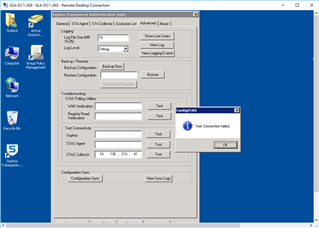
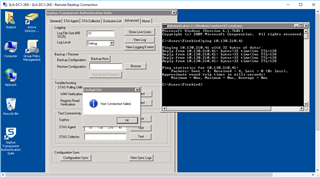
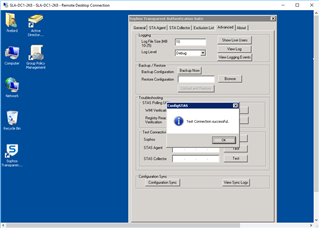
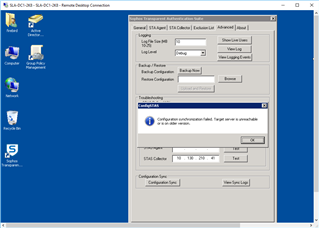
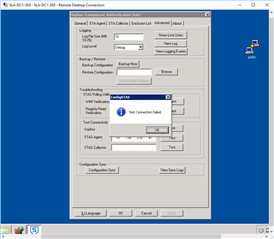
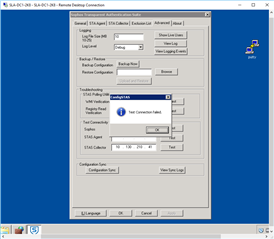
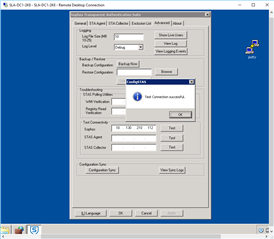
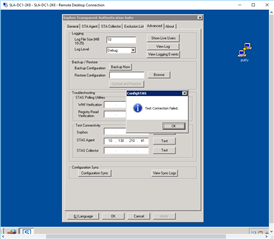
Referring to: STAS Suite "Advanced Tab" >"Test Connectivity"
What I see:
NOTE:
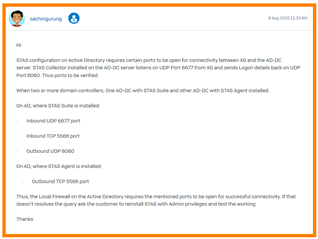
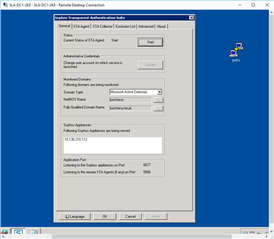
XG Firewall Appliance: 10.130.210.112
DC1: 10.130.210.40
DC2: 10.130.210.41
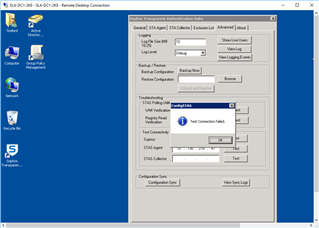
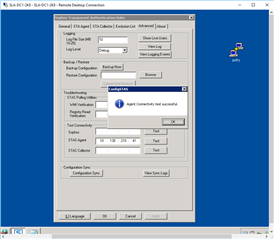
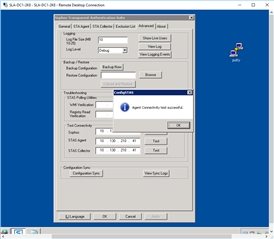
"Test Connectivity" on DC STAS Suite:
STAS Agent: From DC1 to DC1: (or DC2 to DC2) Success
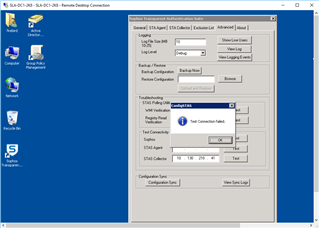
STAS Agent: From DC1 to DC2: FAILURE
STAS Collector: From DC1 to DC1 (or DC2 to DC2): Success
STAS Collector: From DC1 to DC2: Failure
ALSO:
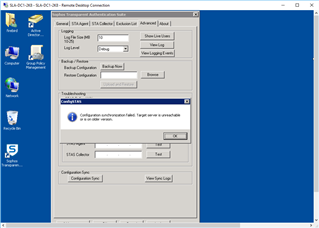
If I try and use the "Configuration Sync" to copy information between the 2 DC's... They both show FAILURE:
--------------------------
Question 2: (I REALLY appreciate WHOEVER takes the time to answer this... I know I can not repay you, but I will THANK YOU FOREVER... and pray for you to be BLESSED!)
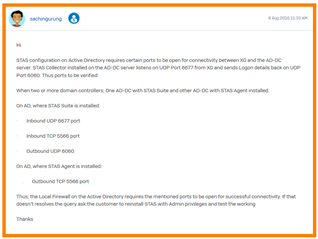
2. How would you "Recommend" opening communication Between these servers: Sophos Documentation only stats:
"Make sure that the AD Server has the UDP port 6677 open for communication between STAS and SF.
Make sure that the AD Server has the TCP port 5566 open for communication between the STA Collector and STA Agent."
I have also read elsewhere to open TCP/UDP ports: 6677, 5566, 6060... Are these the right ports?
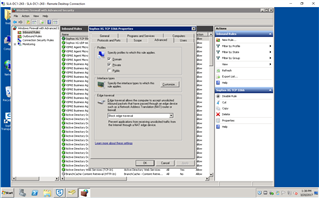
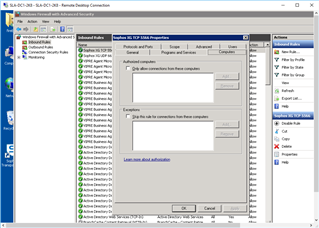
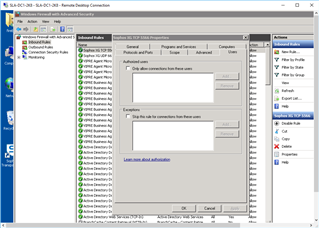
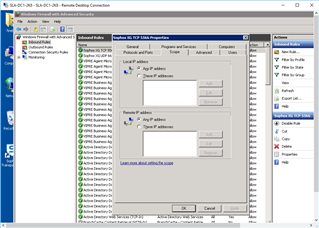
I am FAR from a Server/Network expert (I wear to many hats(jobs) here to get GOOD at anything). But this is what I did to "Open Ports" for these needed connections (PLEASE correct my errors). any Step-by-Step or tips WELCOME!
Example of Step by step I am looking for:
STEPS:
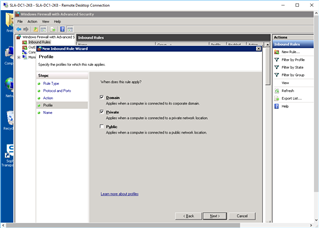
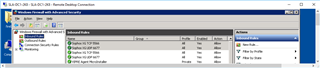
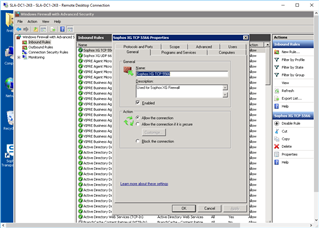
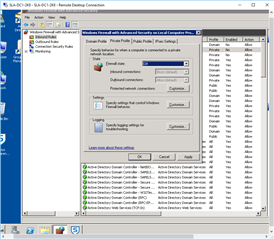
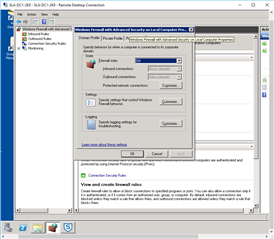
- ON BOTH DC's (Administrative Tools>Windows Firewall with Advanced Security):
- Inbound Rules: "New Rule"
After this I repeated it w/ - Inbound: UDP:6677
Then I configured: "Outbound Rules"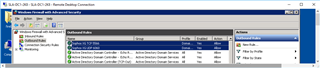
I did this on BOTH DC's... but STILL can not communicate between the two (as far as testing like above: w/ STAS "Test Connectivity".
NOTE: I can PING between the DC's w/ no problem
Any help WILL NOT go unappreciated... I thank the community (especially individual) for ALL THE HELP they provide!
This thread was automatically locked due to age.