When trying to create a connection using the CloudHub architecture: https://docs.aws.amazon.com/vpn/latest/s2svpn/VPN_CloudHub.html
We are using BGP as instructed by AWS:
- We create the VPN (OK).
- BGP starts announcing the route (OK).
- We create the /30 gateway with the IP 169.254.x.x, and our firewall stops responding until the previously created VPN goes offline. Only then we can access the firewall and delete the gateway.
This causes downtime, and eventually the VPN gets disabled. We are unable to close the tunnel, and it also disrupts all other active VPNs, making it take a long time to reconnect to them.
I would like to know if anyone has experienced a similar scenario involving AWS connection with multiple Sophos locations, including more than one firewall, and what solution you are using, even if it's not BGP.
Alternatively, is there any guide or manual to set this up in a way that avoids errors?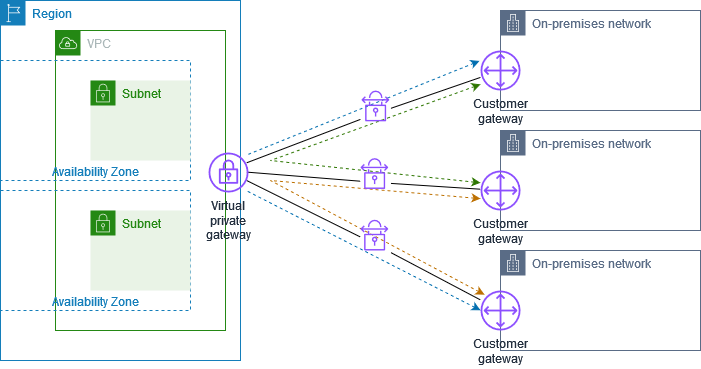
For this scenario, follow these steps:
-
Create a single virtual private gateway.
-
Create multiple customer gateways, each with the public IP address of the gateway. You should use a unique Border Gateway Protocol (BGP) Autonomous System Number (ASN) for each customer gateway.
-
Create a dynamically routed Site-to-Site VPN connection from each customer gateway to the common virtual private gateway.
-
Configure the customer gateway devices to advertise a specific site prefix (such as 10.0.0.0/24, 10.0.1.0/24) to the virtual private gateway. These routing announcements are received and re-advertised to each BGP peer, allowing each site to send and receive data from the other sites. This is done using the network instructions in the VPN configuration files for the Site-to-Site VPN connection. The network instructions vary slightly depending on the type of router you use.
-
Configure the routes in your subnet route tables to enable instances in your VPC to communicate with your sites. For more information, refer to (Virtual Private Gateway) Enable route propagation in your route table. You can configure an aggregated route in your route table (e.g., 10.0.0.0/16). Use more specific prefixes between customer gateway devices and the virtual private gateway.
Edited TAGs
[edited by: Erick Jan at 12:23 AM (GMT -8) on 22 Jan 2025]

