I am testing a new XGS 136 (SFOS 20.0.0 GA-Build222) offsite to replace an onsite XG 135 (SFOS 19.0.2 MR-2-Build472). The backup of the XG 135 was used to setup the XGS 136.
We have never used the IPsec Site-to-Site connection before but may have a use for it further down the line. Therefore, before I put the new unit into production I thought I would take the opportunity to test the Site-to-Site feature. However, I cannot initiate the connection. Here are the settings that I have (note that the local and remote ID are the same email address on both ends).
Head Office Settings on XG 135
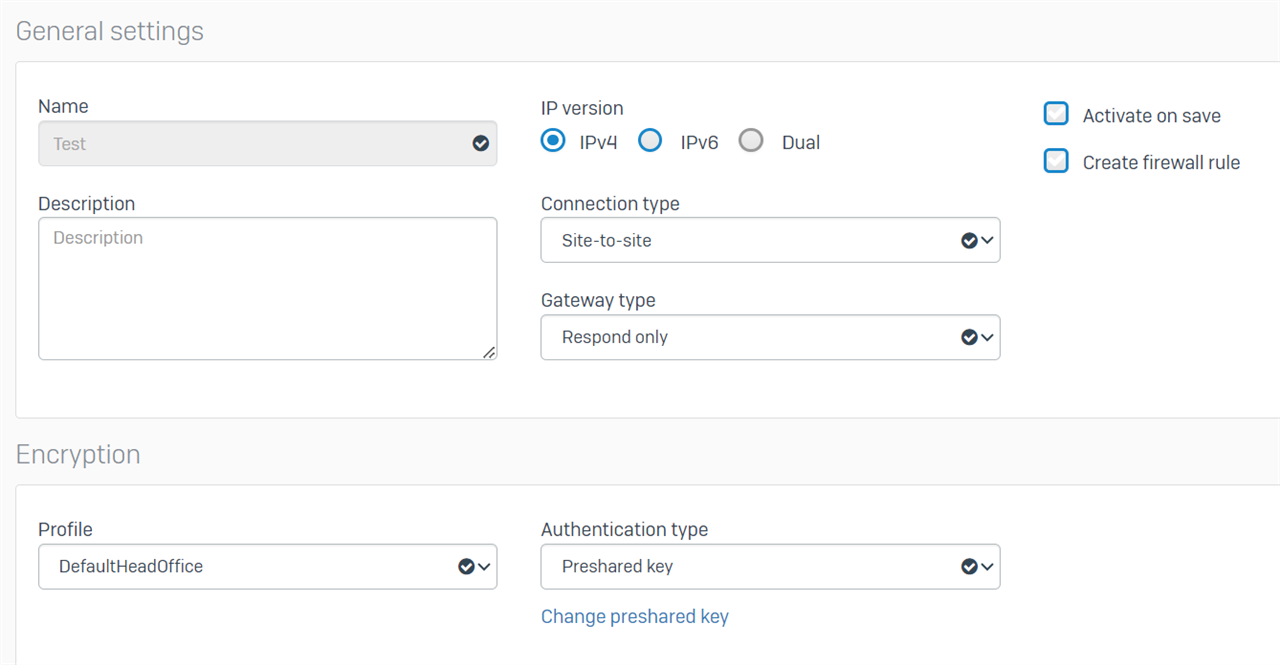
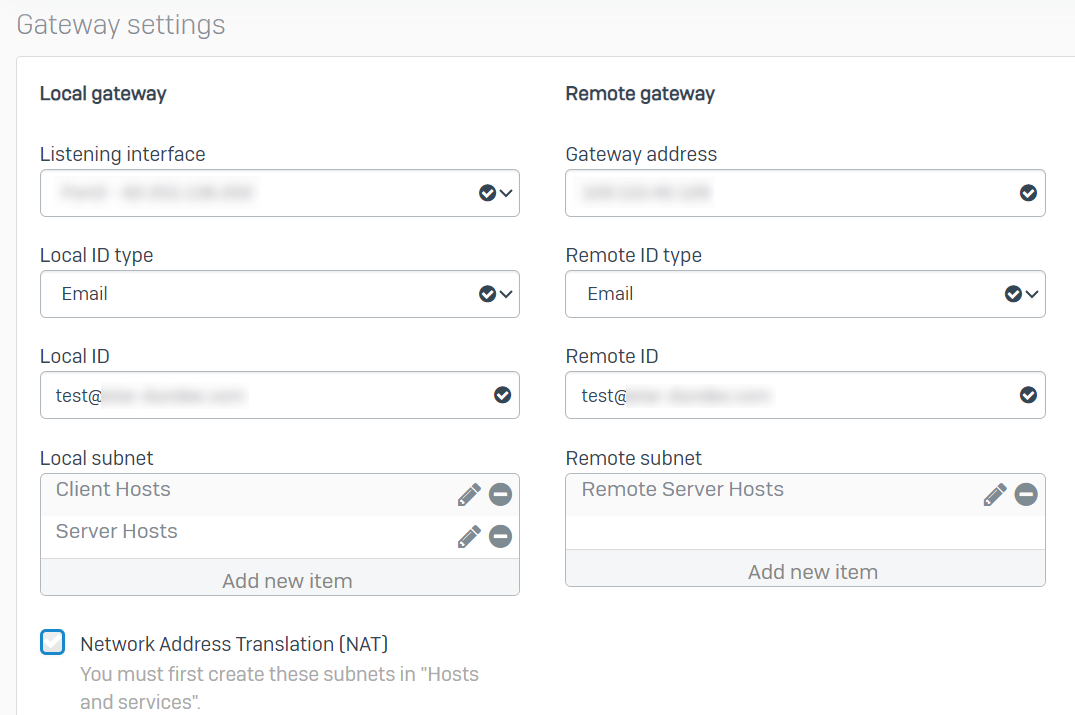
Branch Office Settings
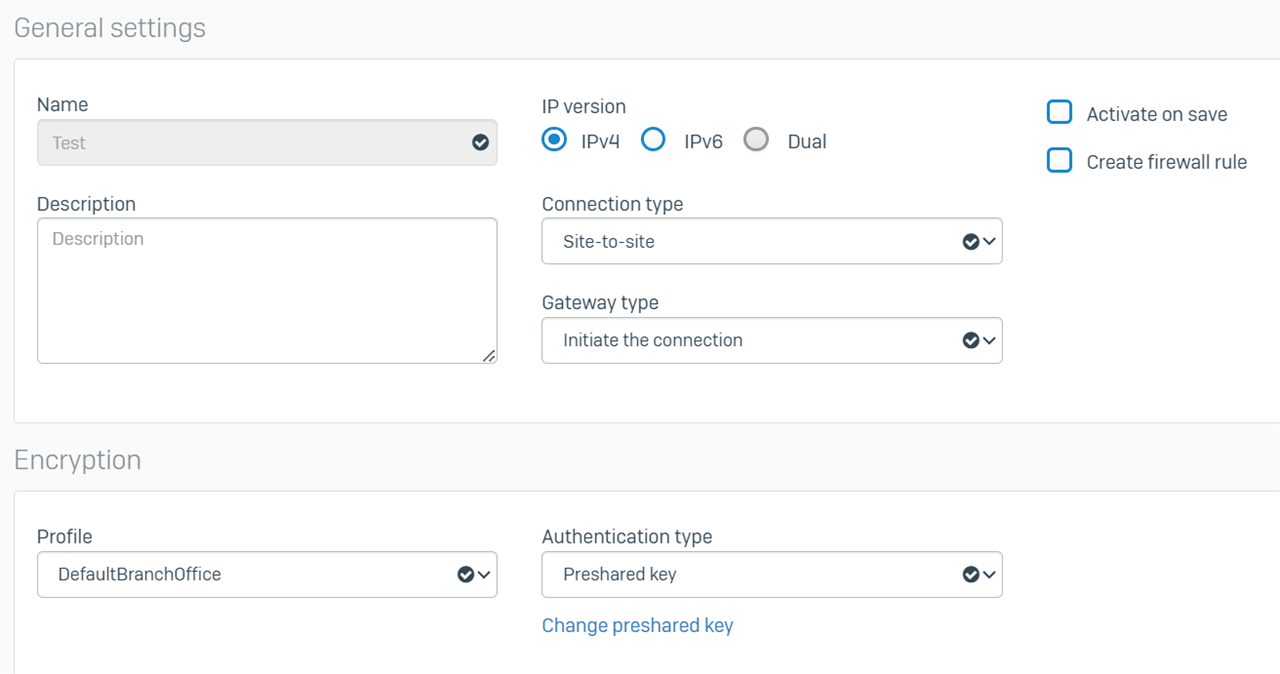
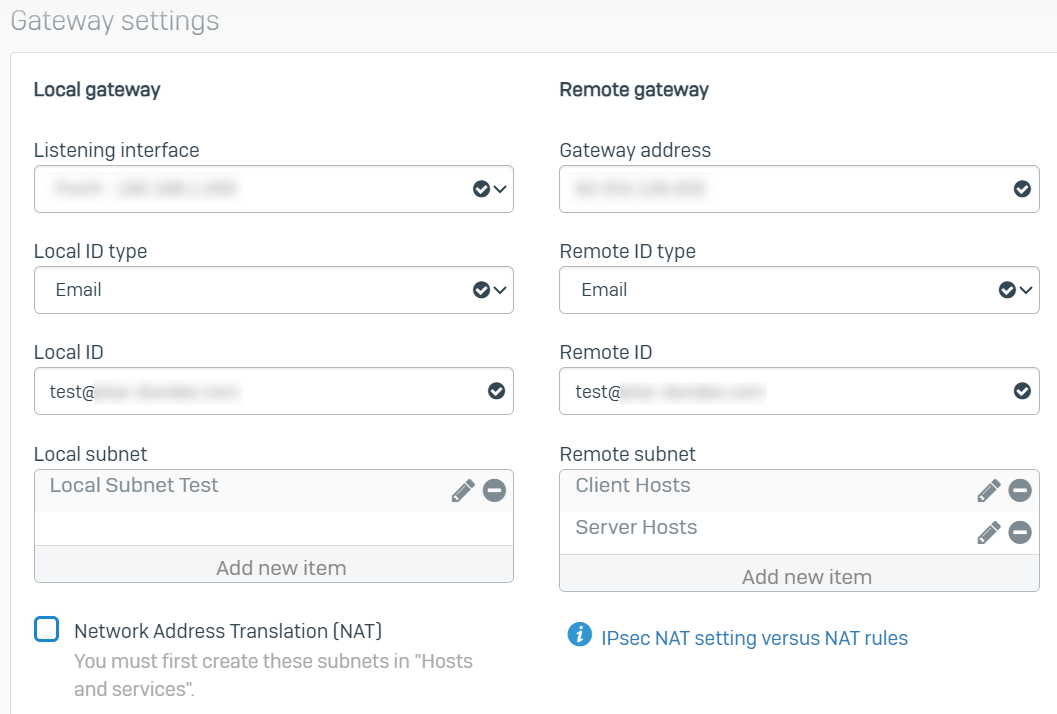
I can successfully activate both ends of the connection.
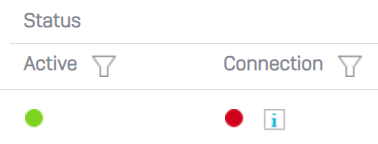
However, when I try to connect on either end, I get the following error.
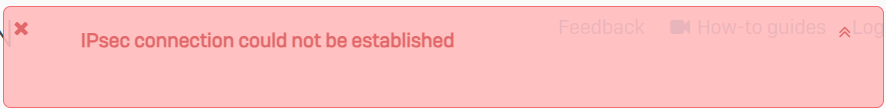
I checked /log/strongswan.log on the branch end and got the following "KE payload missing in message" and UNSUPPORTED_CRITICAL_PAYLOAD errors:
2024-04-10 07:55:02Z 06[CFG] vici initiate 'Test-1'
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> ### queue_child invoking quick_mode_create
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> ### quick_mode_create: 0x7fe3a4002650 config 0x7fe3bc0038c0
2024-04-10 07:55:02Z 15[IKE] <Test-1|55> initiating Main Mode IKE_SA Test-1[55] to HEAD_OFFICE_IP_ADDRESS
2024-04-10 07:55:02Z 15[ENC] <Test-1|55> generating ID_PROT request 0 [ SA V V V V V V ]
2024-04-10 07:55:02Z 15[NET] <Test-1|55> sending packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (548 bytes)
2024-04-10 07:55:02Z 17[NET] <56> received packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (548 bytes)
2024-04-10 07:55:02Z 17[ENC] <56> parsed ID_PROT request 0 [ SA V V V V V V ]
2024-04-10 07:55:02Z 17[IKE] <56> received XAuth vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received DPD vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received Cisco Unity vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received FRAGMENTATION vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received NAT-T (RFC 3947) vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
2024-04-10 07:55:02Z 17[IKE] <56> BRANCH_IP_ADDRESS is initiating a Main Mode IKE_SA
2024-04-10 07:55:02Z 17[ENC] <56> generating ID_PROT response 0 [ SA V V V V V ]
2024-04-10 07:55:02Z 17[NET] <56> sending packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (180 bytes)
2024-04-10 07:55:02Z 16[NET] <56> received packet: from HEAD_OFFICE_IP_ADDRESS[500] to BRANCH_IP_ADDRESS[500] (180 bytes)
2024-04-10 07:55:02Z 16[ENC] <56> parsed ID_PROT request 0 [ SA V V V V V ]
2024-04-10 07:55:02Z 16[IKE] <56> received XAuth vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received DPD vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received Cisco Unity vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received FRAGMENTATION vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> received NAT-T (RFC 3947) vendor ID
2024-04-10 07:55:02Z 16[IKE] <56> KE payload missing in message
2024-04-10 07:55:02Z 16[ENC] <56> generating INFORMATIONAL_V1 request 102214803 [ N(CRIT) ]
2024-04-10 07:55:02Z 16[NET] <56> sending packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (56 bytes)
2024-04-10 07:55:02Z 27[NET] <Test-1|55> received packet: from BRANCH_IP_ADDRESS[500] to HEAD_OFFICE_IP_ADDRESS[500] (56 bytes)
2024-04-10 07:55:02Z 27[ENC] <Test-1|55> parsed INFORMATIONAL_V1 request 102214803 [ N(CRIT) ]
2024-04-10 07:55:02Z 27[IKE] <Test-1|55> informational: received UNSUPPORTED_CRITICAL_PAYLOAD error notify
2024-04-10 07:55:02Z 27[IKE] <Test-1|55> ### destroy: 0x7fe3a4002650
Can anyone spot any obvious issues?
Hey Alan Spark ,
Thank you for reaching out to the community, here it seems we are receiving from the remote end site, maybe the peer wasn't able to decrypt the message properly, or it didn't like one of the payloads (e.g. because it was configured not to use PFS and didn't expect a KE payload). Can you please share the IPsec policy being used both at the local and remote end here ?
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Hi Vivek,
Thanks for your quick response. I assume by policy, you mean profile? Here are the settings of the DefaultHeadOffice and DefaultBranchOffice profiles that I am using at each end.
Head Office
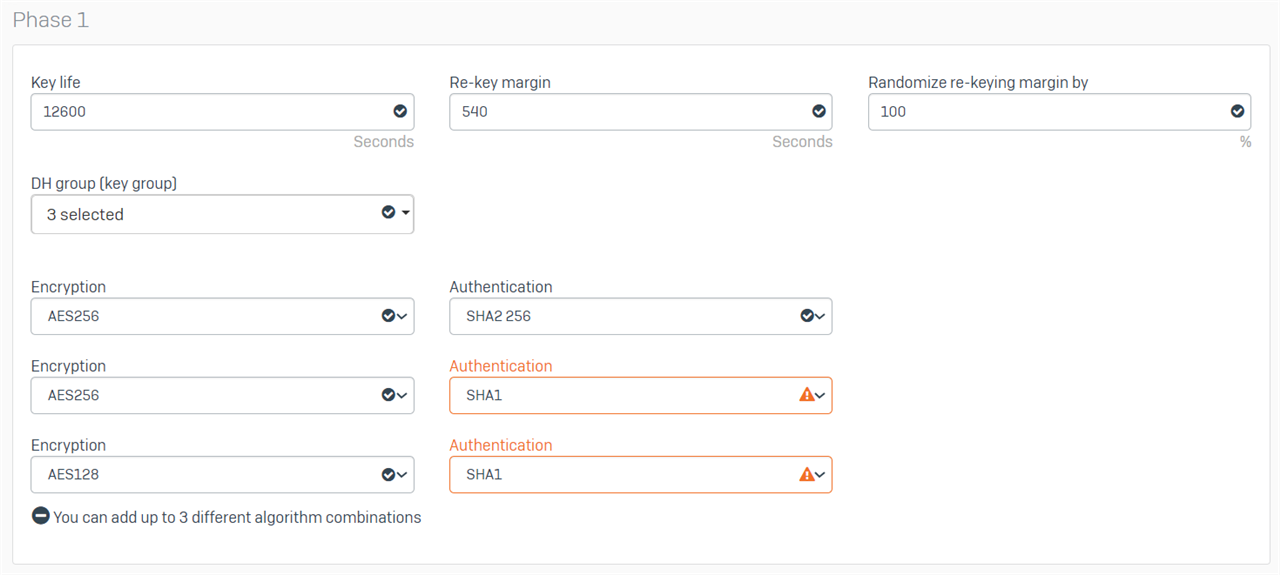
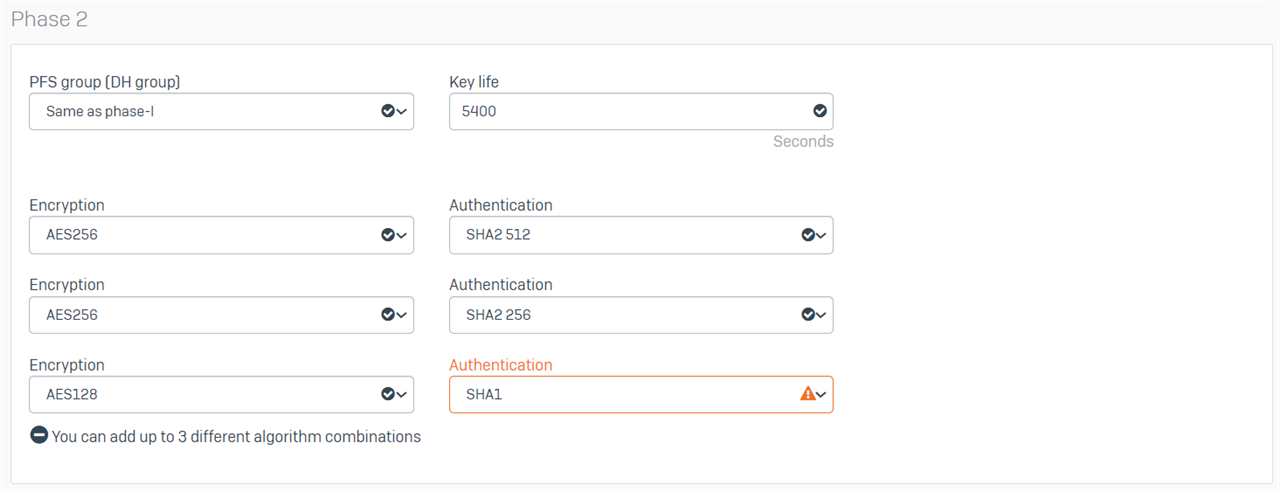
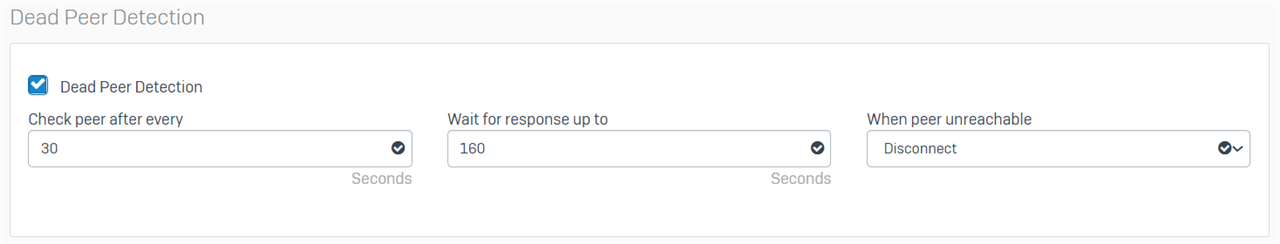
Branch Office
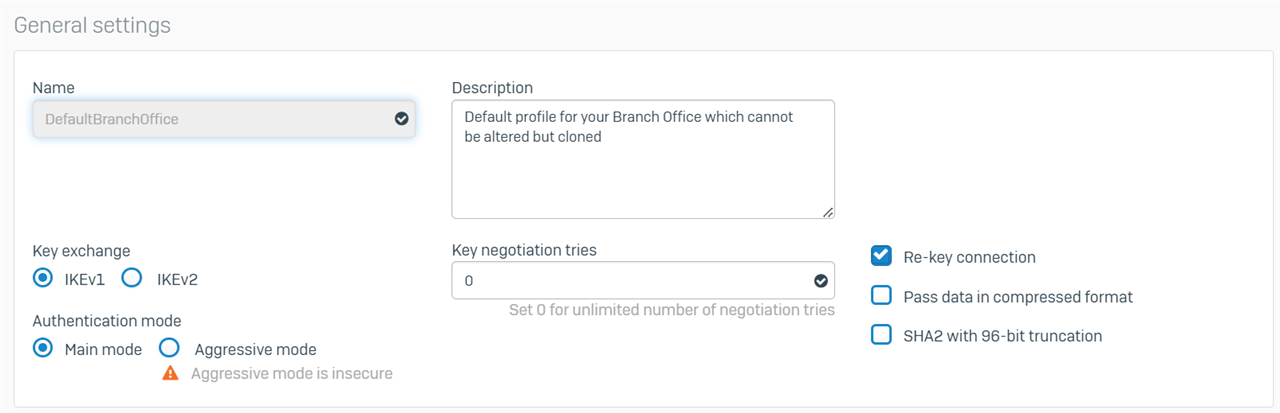
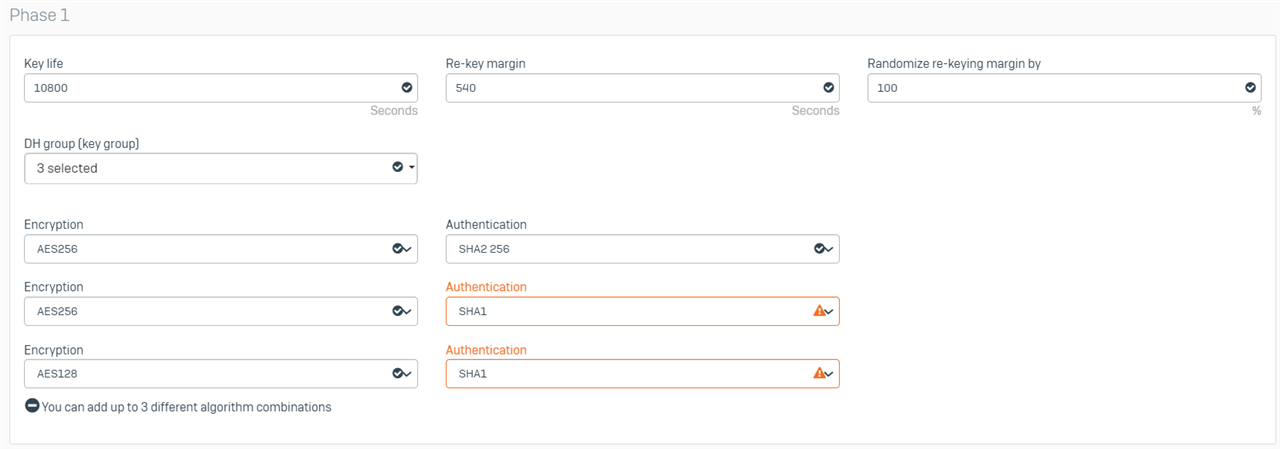
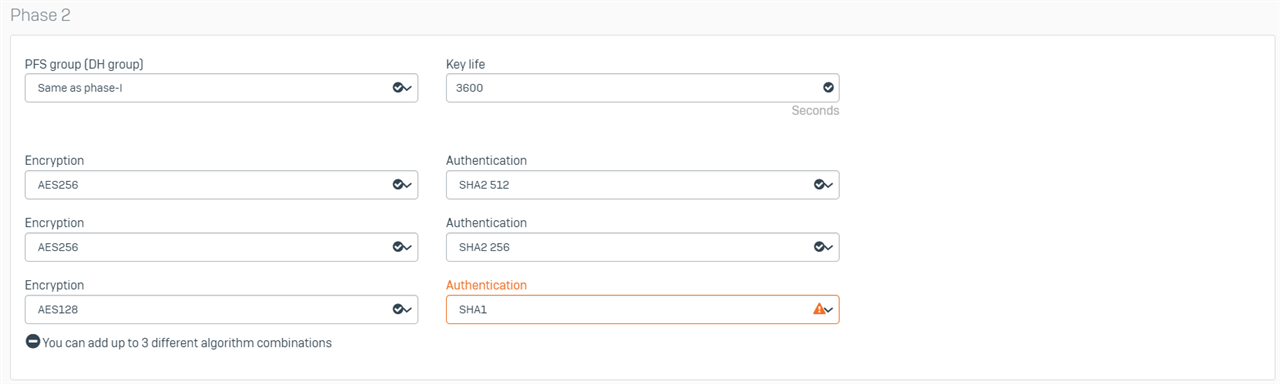
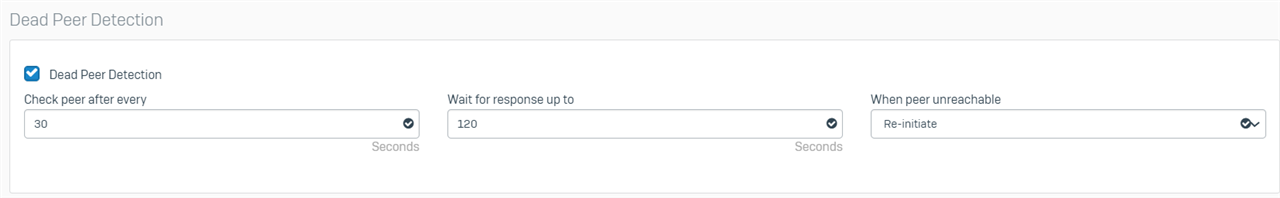
Regards,
Alan
Awesome Alan Spark cheers. Thank you for your contribution Bharat J keep it up !!
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Just to close this off Vivek Jagad , I have been chatting to Bharat J and it turned out I had the wrong LAN address in the branch and head office configuration. I can now receive replies to the pings and browse the network from the branch office.
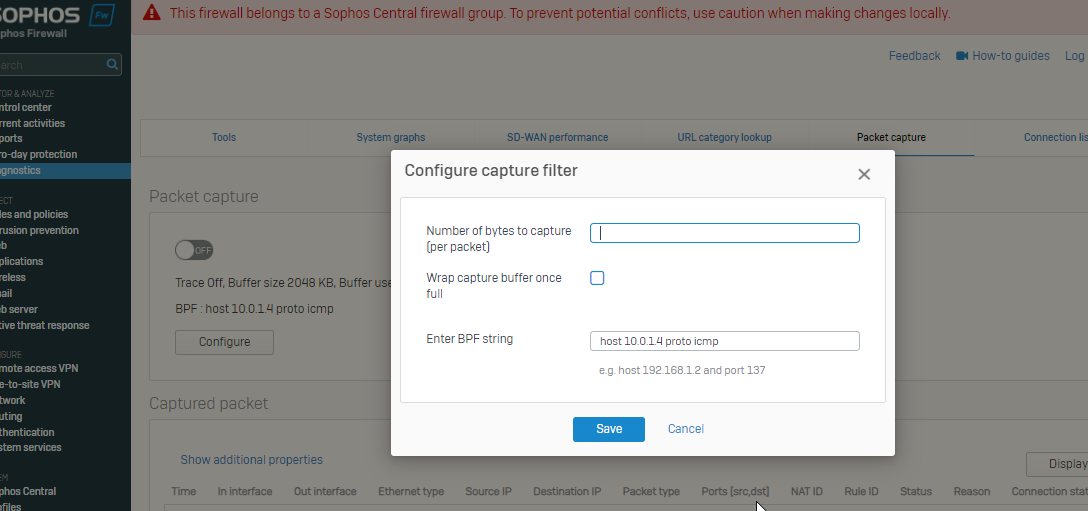
Please post the firewall rules you have configured for VPN with packet capture as per the below step
"Sophos Partner: Networkkings Pvt Ltd".
If a post solves your question please use the 'Verify Answer' button.
I did a packet capture from the branch office and saw the ping with status unreplied. The rule ID is 0 which is the default drop all rule?
Monitor traffic using packet capture, see if the packets are detecting the correct rule now...
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Thanks for confirming, I have changed the NAT hosts to use 255.255.192.0 and now the ping is timing out.
subnet mask should be the same...
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.
Ok, if for example the original IP address is 192.168.2.1 and the branch tries to ping that, they would ping 192.168.1.1?
I have tried the equivelent but the ping still fails. Note that our LAN IPs use subnet 255.255.192.0 but the NAT is configured with 255.255.255.0. Is this an issue?
Ping with subnets mentioned in here: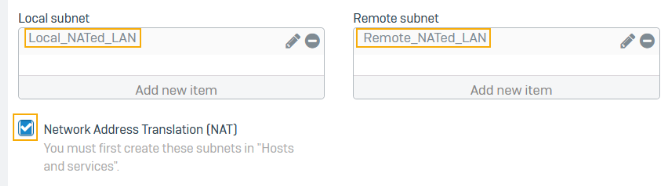
Thanks & Regards,
_______________________________________________________________
Vivek Jagad | Team Lead, Technical Support, Global Customer Experience
Log a Support Case | Sophos Service Guide
Best Practices – Support Case | Security Advisories
Compare Sophos next-gen Firewall | Fortune Favors the prepared
Sophos Community | Product Documentation | Sophos Techvids | SMS
If a post solves your question please use the 'Verify Answer' button.