Hi,
we have a customer, who has about 10 branch offices with each 5 to 50 users and a headquarter with about 50 users.
Every BO has its own XGS firewall, which is currently connected via IPSEC VPN and will later be connected via MPLS to the HQ.
In HQ there is a Citrix terminal server farm with about 25 app servers. Most applications the users use come from Citrix, some local applications exist because they aren't terminal server compatible.
Internet breakout is only via HQ firewall (local networks to Any policy based VPNs on the BO firewalls).
Every client and server has Sophos Endpoint/Server Protection installed.
Infrastructure is centralized (no servers in BO, BO firewalls are acting as DHCP relays.
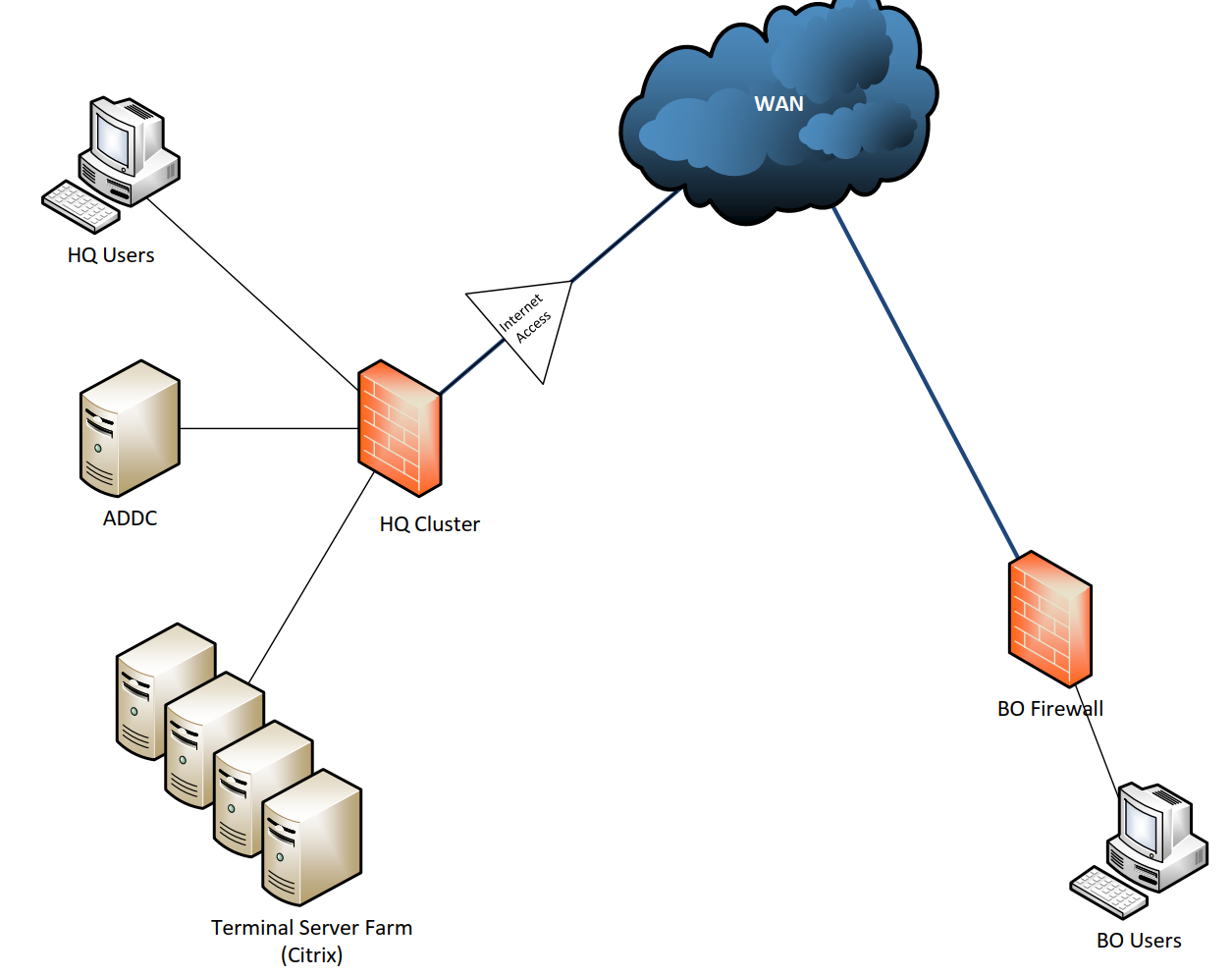
Currently only the HQ firewall is doing authentication. HQ's Sophos endpoints are authenticating automatically via heartbeat, the TS sessions via SATC. STAS is currently not in use.
I am looking for a way to optimize this because the BO clients for example are currently not authenticated automatically via heartbeat, only the HQ IP addresses show up for "Live users". So only the Citrix applications part for BO users is covered via authentication, but not the local applications part,
Any suggestions how to make this more admin friendly/secure?
My goal is to authenticate local AND remote users on the HQ firewall. Authenticating the users on the BO firewall would only be a bonus. *)
If more detailed informations are required feel free to ask!
Regards,
Kevin
*) Unfortunately the customer historically has 9 different sub-companies, each with it's own mail TLD.
Therefore I have 10 different authentication servers defined on the HQ's XG cluster, 1 for general Active Directory, plus another for each mail TLD, because otherwise the HB authentication didn't work properly.
This thread was automatically locked due to age.
