I am tearing my hair out.
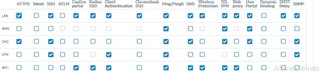
I have configured my XG for SSL remote access I configured all the needed settings as below but the traffic is dropped with status violation local_ACL :
the traffic is dropped no matter where I connect from (LAN WAN DMZ), the user portal is working on all the zones
not only the vpn ssl but also the ssh is dropped even if it is allowed it for example on WAN or DMZ, I can only log from LAN (I know this is how it should be, but I was checking the local ACL to see if they would allow another traffic other than user portal)
I have created ACL exception with different settings ( any any allow ssl vpn for example) (any wan allow ssl vpn...etc) with no success, I have changed the ssl vpn port, restarted the vpn services and the xg but with no vain
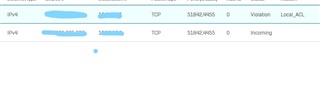
this is the packet capture
2020-01-29 03:00:44 0103021 IP x.x.x.x > y.y.y.y.4455 : proto TCP: S 4204178191:4204178191(0) win 64240 checksum : 14118
0x0000: 4500 0034 1780 4000 6b06 3d5a d5ef cdec E..4..@.k.=Z....
0x0010: 0a0d 0d01 cb09 1167 fa96 ab0f 0000 0000 .......g........
0x0020: 8002 faf0 3726 0000 0204 05ac 0103 0308 ....7&..........
0x0030: 0101 0402 ....
Date=2020-01-29 Time=03:00:44 log_id=0103021 log_type=Firewall log_component=Local_ACLs log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev =Port2.50 out_dev= inzone_id=2 outzone_id=4 source_mac=44:e4:e9:er:0e:7b dest_mac=00:0c:e3:2r:7a l3_protocol=IP source_ip=x.x.x.x dest_ip=y.y.y.y l4_protocol=TCP source_port=51977 dest_port=4455 fw_rule_id=0 policytype=0 live_ userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 proxy_flags=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 source_nat_id=0 cluster_node=0 inmark=0x8002 nfqueue=0 scanflags=0 gateway_offset=0 max_session_bytes=0 drop_fix=0 ctflags=0 connid=379496600 masterid=0 status=256 state=1 sent_pkts=N/A recv_pkts=N/A sent_bytes=N/A recv_bytes=N/A tran_src_ip=N/A tran_src_port=N/A tran_dst_ip=N/A tran_dst_port=N/A
Please help :(((
This thread was automatically locked due to age.