Special thanks to Vikas for creating this write up!
Overview
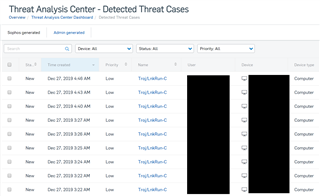
There have been times when an environment is laden with a massive amount of detection alerts similar to -
| Severity | When | Event | User | Device | IP Address |
|---|---|---|---|---|---|
| Medium | 2019-12-26T20:54:01+05:30 | Malware detected: 'Troj/LnkRun-C' at 'Q:\New Volume.lnk' | NA | NA | 10.0.100.3 |
| Medium | 2019-12-26T20:28:40+05:30 | Malware detected: 'Troj/LnkRun-C' at 'U:\New Volume.lnk' | NA | NA | 192.168.2.10 |
| Medium | 2019-12-26T18:37:00+05:30 | Malware detected: 'Troj/LnkRun-C' at 'L:\Loccal Disk.lnk' | NA | NA | 192.168.43.4 |
| Medium | 2019-12-24T21:24:26+05:30 | Malware detected: 'Troj/LnkRun-C' at 'I:\Loccal Disk.lnk' | NA | NA | 192.67.22.11 |
| Medium | 2019-12-24T21:17:44+05:30 | Malware detected: 'Troj/LnkRun-C' at 'Q:\New Volume.lnk' | NA | NA | 192.168.1.420 |
| Medium | 2019-12-24T21:04:56+05:30 | Malware detected: 'Troj/LnkRun-C' at 'O:\New Volume.lnk' | NA | NA | 10.10.10.11 |
Similar Detection Names:
- Troj/DownLnk-A
- Troj/DownLnk-B
- Mal/DownLnk-A
You might also see hundreds of Threat Cases generated in relation to the above detection alerts, and they might not prove to be helpful given the nature of this Malware.
This KBA should help our customers resolve this problem by using Microsoft Autoruns and Sophos Source of Infection Tool.
MITRE's ATT&CK framework calls this TTP as Shortcut Modification and documented under T0123
"Shortcuts or symbolic links are ways of referencing other files or programs that will be opened or executed when the shortcut is clicked or executed by a system startup process. Adversaries could use shortcuts to execute their tools for persistence. They may create a new shortcut as a means of indirection that may use Masquerading to look like a legitimate program. Adversaries could also edit the target path or entirely replace an existing shortcut so their tools will be executed instead of the intended legitimate program."
As expected, if we check the Property of the benign-looking shortcut, it seems to be particularly suspicious because:
- Most probably it has not been created by the customer.
- They do not recognize DriveMgr.exe as a legitimate business application.
Target: %windir%\system32\cmd.exe /c start __ & __\DriveMgr.exe & exit
This particular issue may not be devastating in nature but is particularly annoying due to the repeated detection in the form of Toast messages from Sophos. Hence the investigation needs to be done in a planned way. We'll try to keep this simple with a 3-Step-Approach.
Applies to the following Sophos products and versions
Sophos protected Endpoints and Servers
What to do
Identify
A detection like below can be seen on Sophos protected Endpoints:
Malware detected: 'Troj/LnkRun-C' at 'I:\Loccal Disk.lnk'
Malware detected: 'Troj/LnkRun-C' at 'Q:\New Volume.lnk'
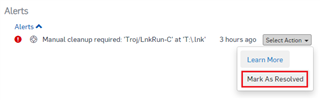
The detection is flagged in the drives I: and Q: which are hosted on a File Server. It's totally normal and by-design that Sophos Anti-Virus will only block the execution of a Malware present on a Shared Network Location. It will not clean the infection. These outstanding Alerts can be safely Marked as Resolved but this action should be performed at the end of the Remediation section.
For now, we should not conclude that this Endpoint is infected and shift our focus of the investigation to the Server which is hosting the share. In our demonstration, the file server is called P520-2016-1 which hosts a shared folder called TestShareOn2016.
Investigate
As you are aware, Sophos has a small utility called Source of Infection which can be used in situations where a typical cycle repeats:
- Malware is dropped in a particular location.
- Sophos detects and cleans the dropped Malware.
- Malware is again dropped in the aforementioned location.
More Information: Sophos source of infection tool (SOI): How to download and use
After running the SOI tool, we let the cycle complete on our P520-2016-1 and analyze the Source of Infection.csv generated in %temp%
| Date/Time | File path | Process/Network | Process path/Machine name |
|---|---|---|---|
| 27-12-19 11:30 | C:\TestShareOn2016\__\DriveMgr.exe | Network | 192.168.30.141 |
| 27-12-19 11:30 | C:\TestShareOn2016\.lnk | Network | 192.168.30.141 |
If the Source of Infection is run correctly i.e. a Sophos Detection/Cleanup cycle has completed, we will have positive confirmation of an IP which is possibly infected and needs remediation actions. In our case, we have successfully identified 192.168.30.141 to be dropping. LNK and DriveMgr.exe in a Share which is called TestShareOn2016
Remediation
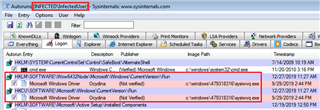
We will utilize a tool called Microsoft Autoruns to further investigate the machine we found in the above step.
NOTE: This malware can cleverly hide under different Users. It's advised that you switch into different users' context by clicking on the User option and check for the presence of any suspicious entries.
The tool can be downloaded from here: Autoruns for Windows
MITRE ATT&ACK documents this Persistence Tactic as Registry Run Keys / Startup Folder under T1060
We have seen LNK dropping malware to persist under User's RUN Keys:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunHKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
As suspected, this machine does not have a copy of Sophos Anti-Virus installed on it, and hence it's spreading on the network by dropping malicious Shortcut [.LNK] files. These seemingly genuine shortcut files are often executed by Users and spreading the infection even further.
At this point, the remediation actions consist of:
- Carefully archive the Malware into a ZIP and Submit a Sample
- Install Sophos Anti-Virus and initiate a Full System Scan
- Run Autoruns again to confirm if the file which the RUN Key points to has been detected/cleaned by Sophos
- After taking a full Registry Backup, carefully Right Click > Delete the malicious RUN Keys from Autoruns.
You can always Open a Support Case to contact Sophos Technical Support if you need any assistance.