Hello Community,
This Recommended Read goes over how to read an email header to understand better where it originated and what path (MTA servers) the email went through to arrive at its destination.
Overview
An email also follows a path to arrive at its destination; this path is recorded in every email in the form of headers; an email header consists of details to authenticate an email and contains information about the sender and recipient.
Headers use metadata to provide information about the email path.
Table of Contents
How to View an Email Header
GMAIL
Go to the email you want to examine and click the three-dotted icon next to the reply arrow on the Top right.
Select "Show Original"
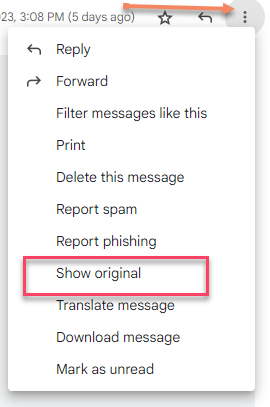
A new window will open, and you will see the Original Message Below the Headers.
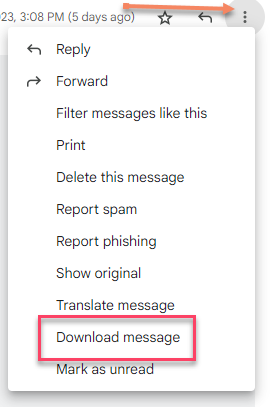
(You can also find the "Download Message" option at the bottom, which will download the email in .eml format)
Outlook
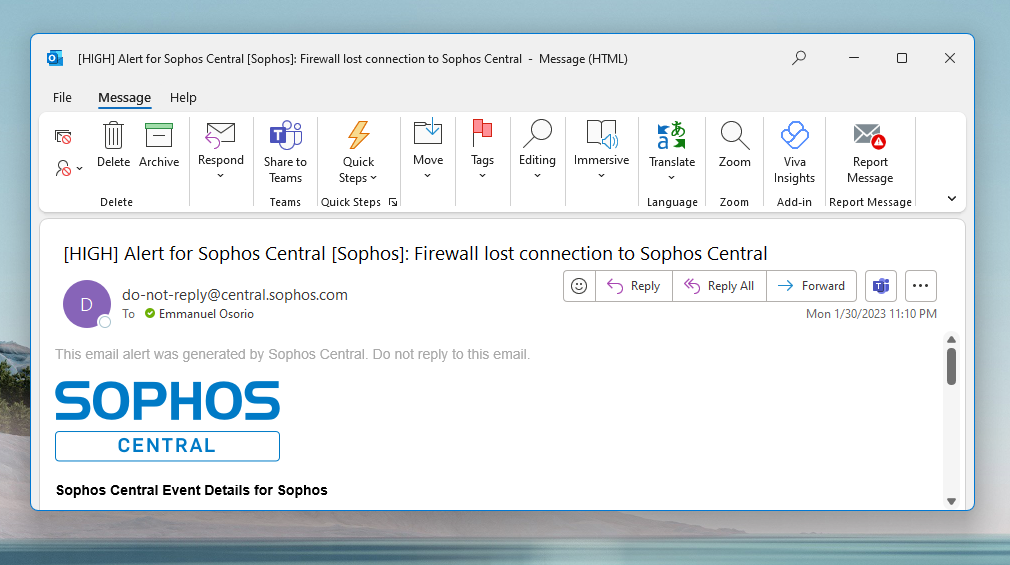
Double click the email in your Mailbox so it opens in a new window.
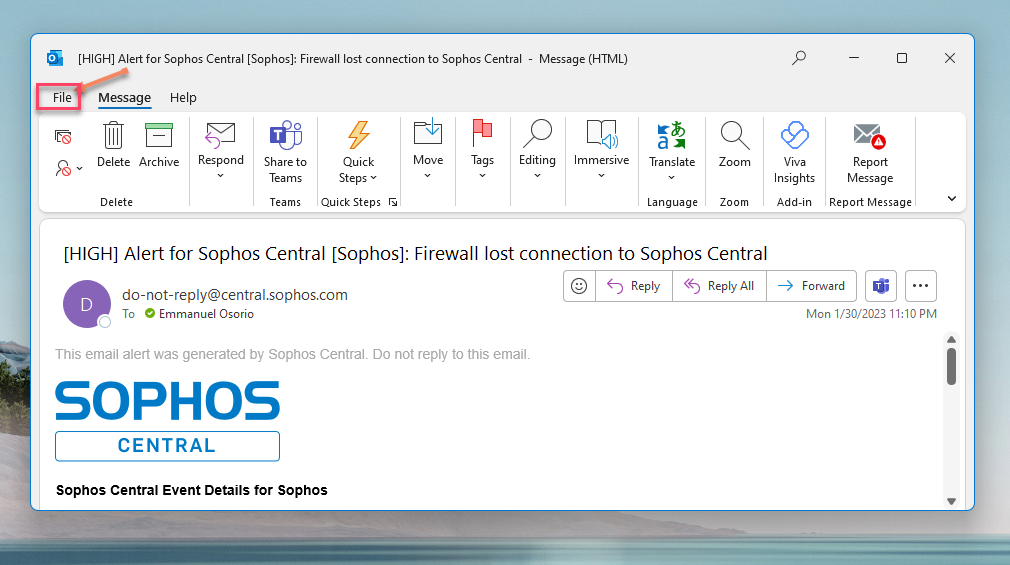
Click File, and a side menu called "info" will show; go to and click the Properties option down at the bottom
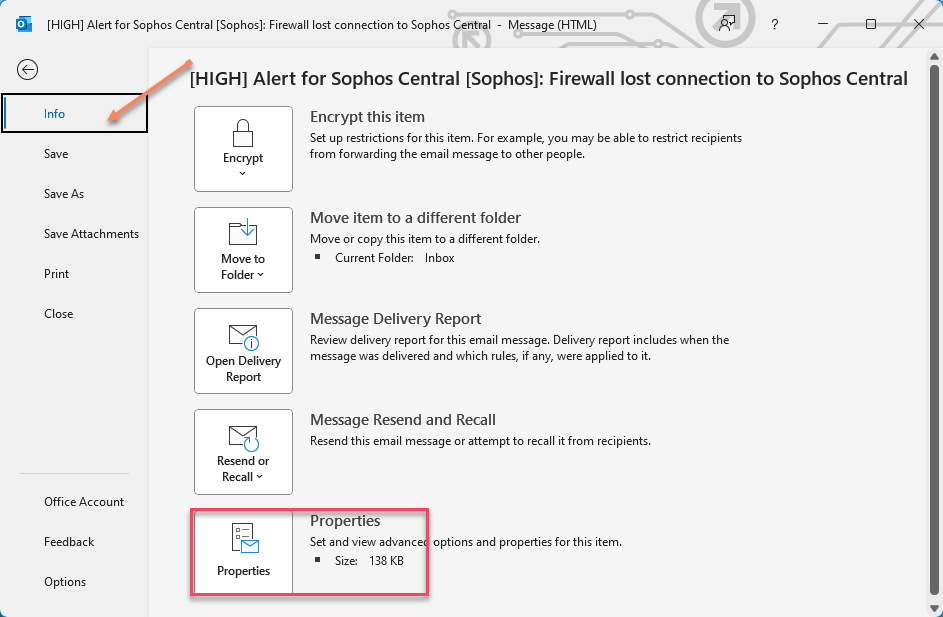
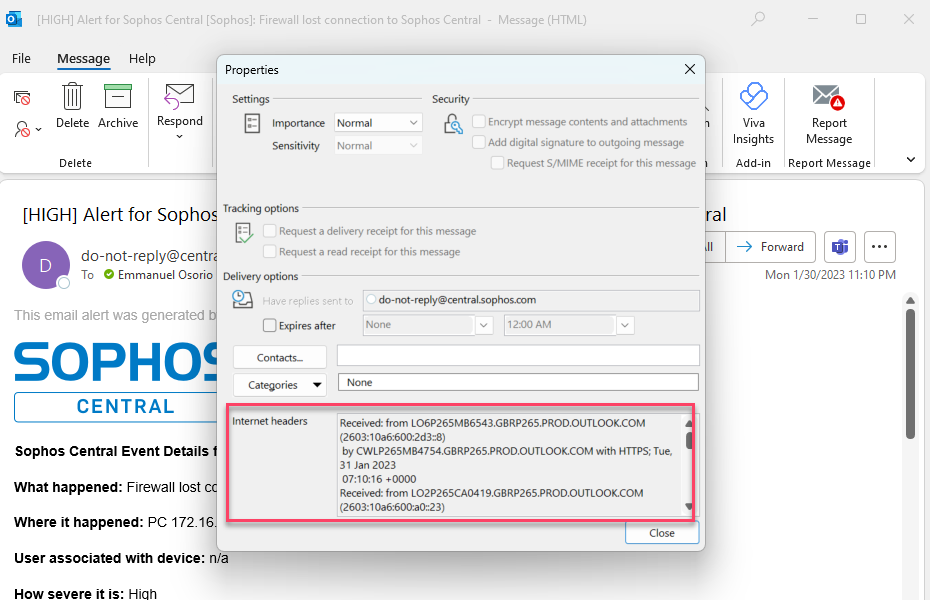
The Headers are located in the "Internet Headers" window.
Mozilla
Go to the email you want to examine and click the three-line icon on the top right.
Click on View > Headers > All.
This will show the Headers at the Top of the Email
OR
You can press Ctrl + U within the e-mail and it’ll open a new window with all the headers and some extra metadata.
Reading an Email Header
To read an email header first we need to know what the important parts of an Email Header are.
* Received: Shows all the addresses that the email passed through while being sent from one computer to another. It has the hostname, IP address, timestamp information.
Received: from ip-172-17-102-161.us-west-2.compute.internal (ip-172-17-102-161.us-west-2.compute.internal [127.0.0.1])
* Message ID: Unique ID for tracking emails (no mail has the same ID)
* Authentication - Results: provides information sender check status for SPF, DMARC, DKIM
* Content Type: Indicates the type of email format. If using Sophos Email this important if using SmartBanners
* X-Lased: If the email passed trough Sophos, it will show the results from Sophos Anti-spam Scanning
*for <email Address> (whithin the Received header): Shows to whom the email was sent to
* ESMTPS ID: is a unique queue ID, Support usually use this ID to find your email in the logs (This IDs are assigned by the recipient email relay/host when confirming TO the sender that is has accepted the email.
Now that we know what headers are important for our use case, let's read the following header:
==========================================================================================================================
Return-Path: msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca
Received: from mail.noXXXXXXXX.ca (noXXXXXXXX.ca [172.16.15.254])
by localhost with ESMTP
; Wed, 4 Jan 2023 15:04:51 -0800
Received: from inbound-50-112-39-248-us-west-2.prod.hydra.sophos.com ([50.112.39.248]:42054)
by mail.noXXXXXXXX.ca with esmtps (TLS1.2) tls TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
(Exim 4.94.2)
(envelope-from <msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca>)id 1pDCoI-0006A8-LB
for emmanuel@noXXXXXXXX.ca; Wed, 04 Jan 2023 15:04:38 -0800
Received: from ip-172-17-102-161.us-west-2.compute.internal (ip-172-17-102-161.us-west-2.compute.internal [127.0.0.1])
by inbound-50-112-39-248-us-west-2.prod.hydra.sophos.com (Postfix) with ESMTP id 4NnQCp1J20zsR4j
for <emmanuel@noXXXXXXX.ca>; Wed, 4 Jan 2023 23:04:38 +0000 (UTC)
Authentication-Results: mx-01-us-west-2.prod.hydra.sophos.com; spf=pass smtp.mailfrom=msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca; dkim=pass header.d=e.crave.ca header.from=e.crave.ca; dmarc=pass (recordpolicy=reject) header.from=e.crave.ca
Received-SPF: pass receiver=mx-01-us-west-2.prod.hydra.sophos.com; client-ip=223.165.116.245; envelope-from=<msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca>; helo=223.165.116.245.jfk.braze.com;
X-Sophos-Product-Type: Gateway
X-Sophos-Email-ID: 364b0b2d38564861ad98f112c9af9628
Received: from 223.165.116.245.jfk.braze.com (223.165.116.245.jfk.braze.com [223.165.116.245])
(using TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits))
(No client certificate requested)
by mx-01-us-west-2.prod.hydra.sophos.com (Postfix) with ESMTPS id 4NnQCd3fmyzRhQs
for <emmanuel@noXXXXXXXXX.ca>; Wed, 4 Jan 2023 23:04:29 +0000 (UTC)
X-MSFBL: k7Y7hVhHpRwiEFdm7Sg4p5rVUPU5/cJt55MYKCkaXjs=|eyJjdXN0b21lcl9pZCI
6IjI2NjY5MyIsIm1lc3NhZ2VfaWQiOiI2M2I1ZmMwNWI2NjNlN2EwNGU0YSIsInR
lbmFudF9pZCI6InNwYyIsInIiOiJlbW1hbnVlbEBub2lwYWRkcmVzcy5jYSIsInN
1YmFjY291bnRfaWQiOiI1NyJ9
DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=e.crave.ca;
s=scph1020; t=1672873468; i=@e.crave.ca;
bh=c0YCm8Ivmmc6Jsk7FZNLJpnsp3uLFGRfpJjfdQzs5uQ=;
h=To:Message-ID:Date:Content-Type:Subject:From:From:To:Cc:Subject;
b=PAt/55UOCmYQIaLClrEaCaRritueKU9uUQRLkhf4n/tpg0dyRJ+YTXtFb/np+j+N0
yZmdFwATy9opP4VLX84UitW6+Ad4jyJsVlrlXbTffLaKzETf+v+qIRdR7uS//ft0E9
0/wbTAJAya3J962lNMhSpUdPB6IZkRJtYuOWpywA=
To: emmanuel@noXXXXXXXXXX.ca
Message-ID: <E4.A4.32672.CF506B36@ju.mta1vrest.cc.prd.sparkpost>
Date: Wed, 04 Jan 2023 23:04:28 +0000
Content-Type: multipart/alternative; boundary="_----L8ZbYC4p16FauAb3UzJvZA===_73/A4-32672-CF506B36"
MIME-Version: 1.0
Reply-To: noreply@crave.ca
Subject: =?utf-8?B?4o+wIFRpbWUgaXMgQWxtb3N0IFVwOiBHZXQgJDI1IG9mZiBvdXIg?=
=?utf-8?B?JDEwMCBDcmF2ZSBHaWZ0IENhcmQ=?=
From: "Crave" <Crave@e.crave.ca>
Content-Transfer-Encoding: 8bit
X-Sophos-Email-Scan-Details: 27140d1e1540510e7e771140550e7d75
X-Sophos-Email: [us-west-2] Antispam-Engine: 5.1.1, AntispamData: 2023.1.4.224518
X-Sophos-SenderHistory: ip=223.165.116.245,fs=60156141,fso=63530891,da=166332083,mc=8605,sc=6,hc=8599,sp=0,re=4,sd=0,hd=30
X-Sophos-DomainHistory: d=crave.ca,fs=21769422,fso=21769422,da=27074907,mc=3672,sc=0,hc=3672,sp=0,re=0,sd=0,hd=18
X-LASED-SpamProbability: 0.095349
============================================================================================
Headers are read from Bottom to TOP; bottom means where the original originated until it gets to its final destination (TOP) (Your mailbox)
In this case, the email has 4 Received headers, which means it traversed 4 MTA (Mail Transfer Agents) to get to us (the recipient).
The 4 of them are:
Received: from 223.165.116.245.jfk.braze.com (223.165.116.245.jfk.braze.com [223.165.116.245]) (The email originated from this IP)
Received: from ip-172-17-102-161.us-west-2.compute.internal (ip-172-17-102-161.us-west-2.compute.internal [127.0.0.1]) (then it was received by this MTA (by the FQDN we can see is Sophos Email)
Received: from inbound-50-112-39-248-us-west-2.prod.hydra.sophos.com ([50.112.39.248]:42054) (Sophos Email sent it out to our Email Server from this MTA.
Received: from mail.noXXXXXXXXX.ca (noXXXXXXX.ca [172.16.15.254]) (Finally made it to our inbox after being sent by our Mail Server (For the Private IP We can deduct a DNAT rule is configured in the Firewall infront of our Email Server)
1. X-LASED Spamprobability says it is 0.09 (A probability of 9% to be SPAM)
2. Message ID <E4.A4.32672.CF506B36@ju.mta1vrest.cc.prd.sparkpost>: The sender should have this ID in their sender MTA
3. ESMTP(s) id : 4NnQCp1J20zsR4j
4. Content Type: multipart/alternative (An email can be broken in different parts, (multipart) you can scroll to find all the parts marked in the email as "Content-Type" in this case this email had 3
Content-Type: text/plain; charset="UTF-8"
Content-Type: text/html; charset="UTF-8"
Content-Type" content=3D"text/html
We can conclude the email got a banner
5. Authentication-Results: mx-01-us-west-2.prod.hydra.sophos.com; spf=pass smtp.mailfrom=msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca; dkim=pass header.d=e.crave.ca header.from=e.crave.ca; dmarc=pass (recordpolicy=reject) header.from=e.crave.ca
This show us that the SPF, DKIM and DMARC passed the checks, so most likely the sender is whoever they say they are
6. Return Path: msprvs1=19368dx8krbzn=bounces-266693-57@e.crave.ca
If a user press Replies to this email that is the address that will received the email
What information to provide to Support
1. The email direction (Inbound or outbound)
2. Domain/mailbox involved
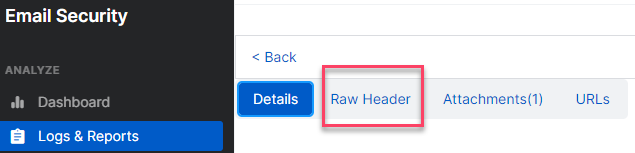
3. The Email ESMTPS (If you are the Sophos Email Admin, you can find this too, in Central under the Raw Header (Log & Reports > Message History> Subject > Raw Header) provide the ones closer to the Top
4. What mode is Sophos Email Deployed (Gateway/Mailflow)
5. Sample Email (Original Email) * (More info below on how to submit)
6. Any screenshots
7. If your organization policy allows it Enable Remote Assistance and share the Unique ID (A copy and Paste instead of a screenshot is appreciated)
How to submit an email sample (Original Email)
In most cases, Support will ask you to submit the email in question, (original email) when doing this, the email needs to preserve the original headers, the only way to achieve this is by sending the Original Email recieved.
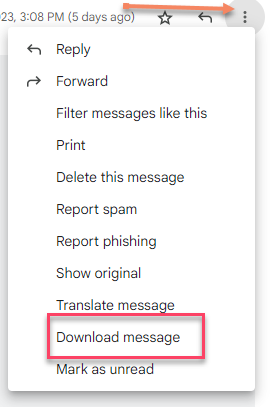
If using Gmail: Click the email you want to submit, (a new window open) Click the ... Dots on the Top Right (ellipsis?) then Click "Download Message", this will download a .eml file, this is the file you need to submit
if using Outlook:
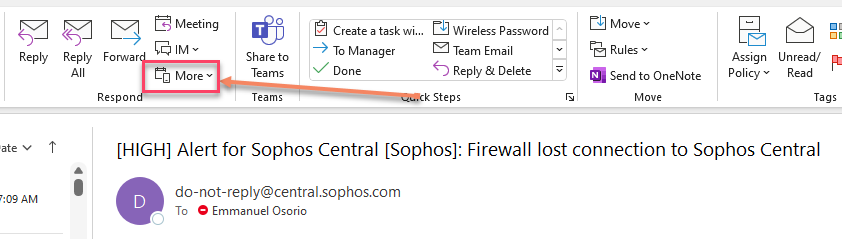
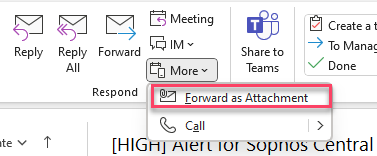
1. Click the email you want to submit, next to the Forward envelope finf the "More" option, click an a submenu will show, click "Forward as Attachment" and a new empty Email will be created with the email attached (note you can select several emails)
Note: Dont drag the email to your desktop, this changes the format of the email from .eml to .msg which is not useful if the sample is submited to Labs for further analysis.
If using Mozilla:
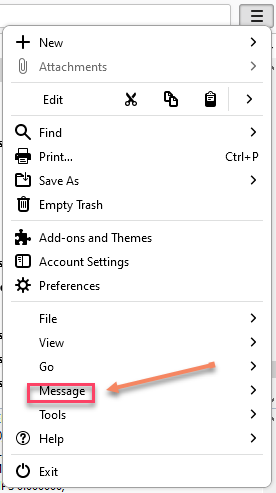
1. Click the Email you want to submit, Right Click > Click "Forward As" > Attachment, a new empty email with the email in .eml format will be attached
2. Click the Email you want to submit, Right Click > Click "Save As" > save it in your preferred location, the email will be download as .eml
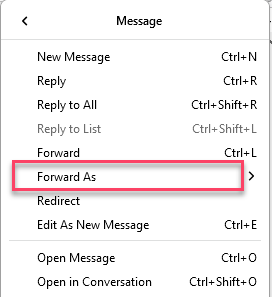
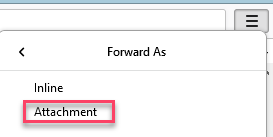
Important: In any of the emails, if you click "Forward" directly within the email you want to submit, it’ll override the Original Headers making it useless.
Note: If you only provide the headers (txt) and not the email, Support/Labs will not be able to check all the information need it when investigating the email.
Formatting
[edited by: emmosophos at 12:07 AM (GMT -8) on 1 Feb 2023]
