Up until recently we used the old Sophos Email Appliance, and were able to add a keyword to the subject line to force SPX encryption (where it would encrypt as a PDF with a password).
I'm having a hard time trying to replicate this now that we've moved to Sophos Email in Sophos Central. I would really like to utilize the Portal Encryption, but I don't see that option anywhere in Sophos Central. Is this a separate licensed product? I can't find much information about it.
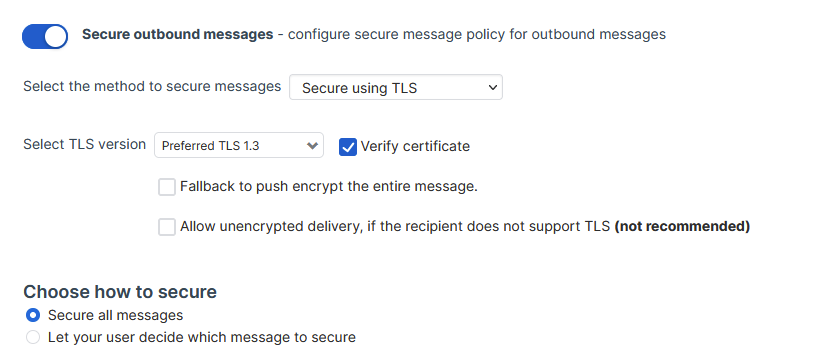
I also am having a hard time understanding the settings in the "Base Policy - Secure Message" area. Currently for outbound settings we have it set to Secure using TLS, Prefer TLS 1.3, and also "Allow unencrypted delivery". This was checked by default, even though it says "not recommended". In the logs, 90% of our outgoing emails say "Secure message", and the other 10% say "Legitimate". If I turn off "Allow unencrypted delivery", will those messages fail? I'm unsure really what the difference is here.
This thread was automatically locked due to age.