Note: Please contact Sophos Professional Services if you require direct assistance with your specific environment.
To ensure successful delivery of Phish Threat emails and completion of Phish Threat campaigns, follow these steps to make necessary changes in Microsoft's Advanced delivery settings.
In Microsoft 365 admin center, go to ‘Security’
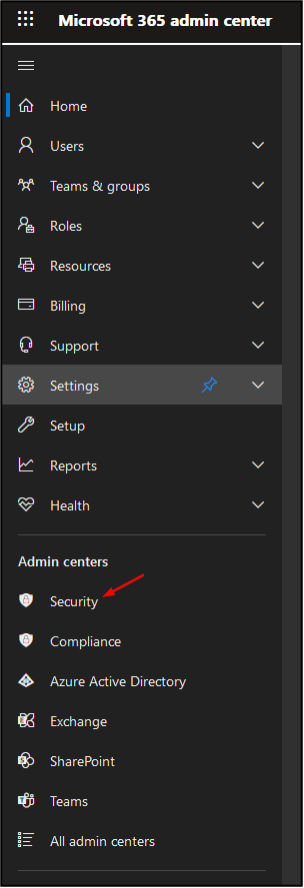
Then, under ‘Policies and Rules’, go to ‘Threat Policies’
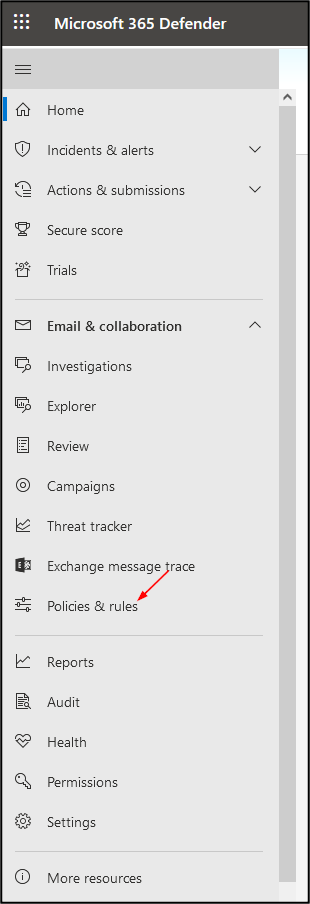
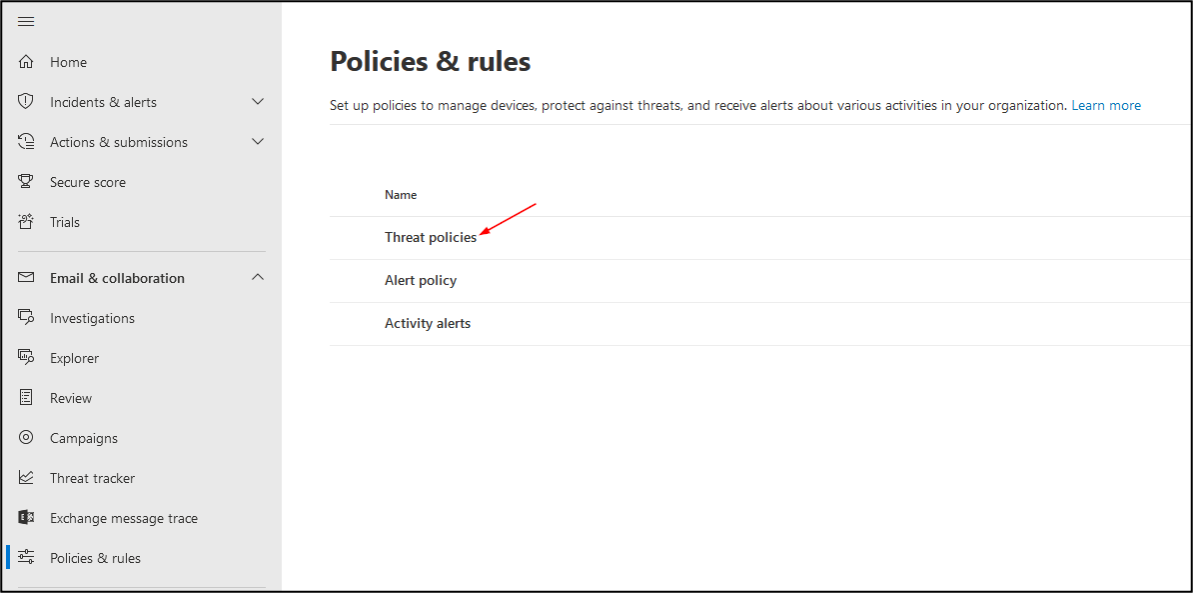
Click on ‘Advanced delivery’ and then ‘Phishing simulation’
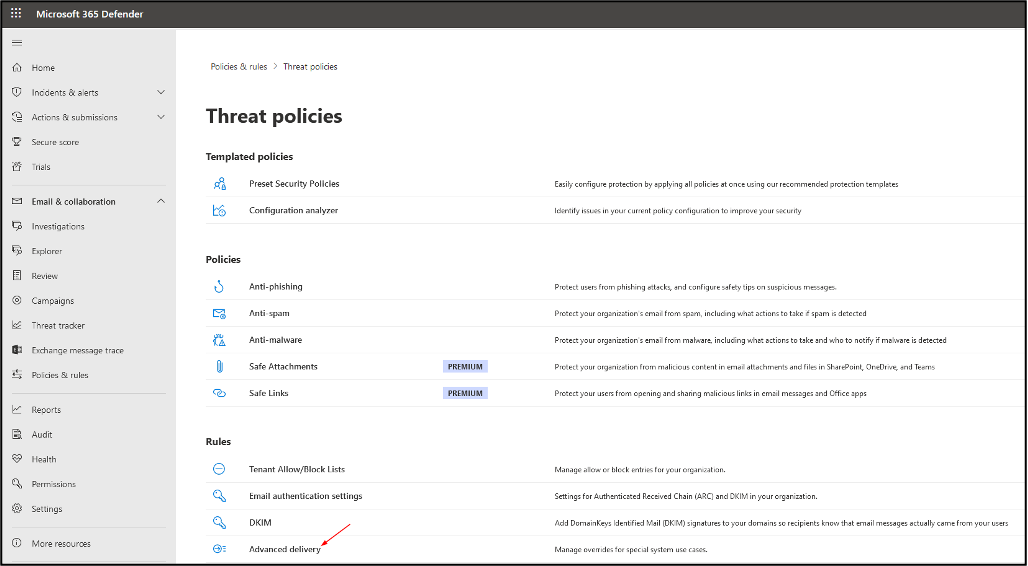
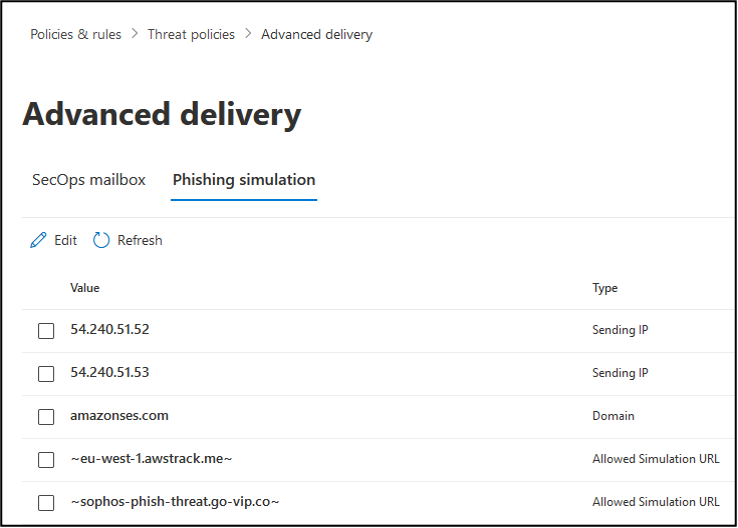
Under Phishing simulation, make the following additions:
Removed KB
[edited by: emmosophos at 12:22 AM (GMT -8) on 28 Jan 2023]


