Disclaimer: This information is provided as-is for the benefit of the Community. Please contact Sophos Professional Services if you require assistance with your specific environment.
With only 129 identified threat actors in the MITRE ATT&CK List https://attack.mitre.org/groups/ you would think it should not be hard to identify the particular nation state or criminal syndicate performing an attack. Unfortunately almost every defined Tactic and Technique is used by multiple threat actors and almost all of them use similar techniques.
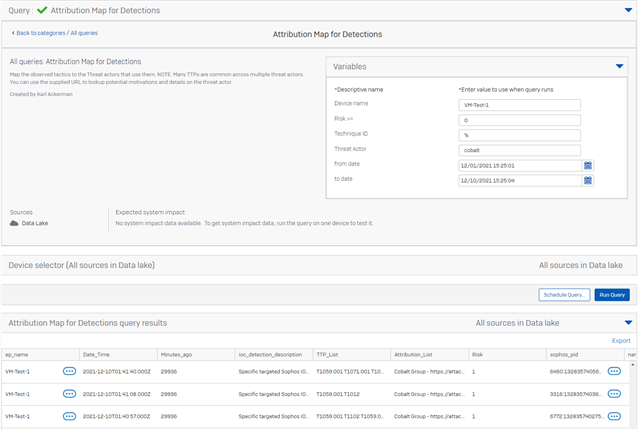
To demonstrate attribution of observed detections to threat actors required requires few steps to be performed in the query.
First we need to build the data base table of all the threat actors and the TTPs they have performed in the past. With that data we can then look at the detections in the system and create a map between the detection and the threat actors that have used the given technique.
The query below supports a few variables to make the exploration easier. With these you can look for particular threat actors by name. Check out the MITRE link above for the list of all threat actors. You can also set a filter by the device name, risk score and time range. What you are likely to discover is that each detection is attributed to multiple threat actors. In addition not all techniques used by a given threat actor have been attributed to them. For that to happen MITRE would require a reference document that identifies them.
In a real world attack from a given threat actor you will see that most of the observed techniques include attribution to that threat actor. Seeing a detection that does not have attribution to a threat actor does not mean that it was not performed by that actor so please use this attribution data with a grain of salt.
VARIABLES
| Variable | Type | Value |
|
Device name
|
DEVICE NAME | % |
|
Risk >=
|
STRING | 6 |
|
Technique ID
|
STRING | % |
|
Threat Actor
|
STRING | % |
|
from date
|
DATE | 12/01/2021 15:00:00 |
|
to date
|
DATE | 12/08/2021 15:00:00 |
SQL
-- MAP the Techniqe detection to the threat actors that it has been attributed to
-- VARIABLE $$Device name$$ DEVICE NAME
-- VARIABLE $$Risk >=$$ STRING
-- VARIABLE $$Technique ID$$ STRING
-- VARIABLE $$Threat Actor$$ STRING
-- VARIABLE $$from date$$ DATE
-- VARIABLE $$to date$$ DATE
--Attribution Map
WITH
-- Create some counters for unnesting the Tactic and Technique information in the detections xdr_ti_data table
Max_Tactics(x) AS ( VALUES ('0'),('1'),('2'),('3'),('4'),('5') ),
Max_Techniques(y) AS ( VALUES ('0'),('1'),('2'),('3'),('4'),('5') ),
-- Load the condensed list of TTPs by threat actor
TTP_Group_Map (Id, Name, Related_groups, TTPs) AS (
VALUES
('G0018','admin@338','','T1087.001T1059.003T1203T1083T1036.005T1069.001T1566.001T1082T1016T1049T1007T1204.002'),
('G0130','Ajax Security Team','Operation Woolen-Goldfish,AjaxTM,Rocket Kitten,Flying Kitten,Operation Saffron Rose','T1555.003T1105T1056.001T1566.001T1566.003T1204.002'),
('G0138','Andariel','Silent Chollima','T1005T1189T1203T1592.002T1590.005T1105T1027.003T1588.001T1566.001T1057T1049'),
('G0099','APT-C-36','Blind Eagle','T1059.005T1105T1036.004T1571T1027T1588.002T1566.001T1053.005T1204.002'),
('G0006','APT1','Comment Crew,Comment Group,Comment Panda','T1087.001T1583.001T1560.001T1119T1059.003T1584.001T1005T1114.001T1114.002T1585.002T1036.005T1135T1588.001T1588.002T1003.001T1566.001T1566.002T1057T1021.001T1016T1049T1007T1550.002'),
('G0005','APT12','IXESHE,DynCalc,Numbered Panda,DNSCALC','T1568.003T1203T1566.001T1204.002T1102.002'),
('G0023','APT16','','T1584.004'),
('G0025','APT17','Deputy Dog','T1583.006T1585'),
('G0026','APT18','TG-0416,Dynamite Panda,Threat Group-0416','T1071.001T1071.004T1547.001T1059.003T1133T1083T1070.004T1105T1027T1053.002T1082T1078'),
('G0073','APT19','Codoso,C0d0so0,Codoso Team,Sunshop Group','T1071.001T1547.001T1059T1059.001T1543.003T1132.001T1140T1189T1564.003T1574.002T1112T1027T1588.002T1566.001T1218.01T1218.011T1082T1016T1033T1204.002'),
('G0007','APT28','SNAKEMACKEREL,Swallowtail,Group 74,Sednit,Sofacy,Pawn Storm,Fancy Bear,STRONTIUM,Tsar Team,Threat Group-4127,TG-4127','T1134.001T1098.002T1583.001T1595.002T1071.001T1071.003T1560T1560.001T1119T1547.001T1037.001T1110T1110.001T1110.003T1059.001T1059.003T1092T1213T1213.002T1005T1039T1025T1001.001T1074.001T1074.002T1030T1140T1114.002T1573.001T1546.015T1048.002T1567T1190T1203T1211T1068T1210T1133T1083T1589.001T1564.001T1564.003T1070.001T1070.004T1070.006T1105T1056.001T1559.002T1036T1036.005T1498T1040T1027T1588.002T1137.002T1003T1003.001T1003.003T1120T1566.001T1566.002T1598T1542.003T1057T1090.002T1090.003T1021.002T1091T1014T1113T1505.003T1218.011T1528T1221T1199T1550.001T1550.002T1204.001T1204.002T1078T1078.004T1102.002'),
('G0016','APT29','NobleBaron,Dark Halo,StellarParticle,NOBELIUM,UNC2452,YTTRIUM,The Dukes,Cozy Bear,CozyDuke','T1548.002T1087T1098.001T1098.002T1583.001T1583.006T1595.002T1071.001T1560.001T1547.001T1547.009T1110.003T1059.001T1059.003T1059.005T1059.006T1584.001T1555T1213.003T1005T1001.002T1074.002T1140T1587.001T1587.003T1484.002T1482T1568T1114.002T1546.003T1546.008T1048.002T1190T1203T1133T1083T1606.001T1606.002T1562.001T1562.002T1562.004T1070T1070.004T1070.006T1105T1036T1036.004T1036.005T1095T1027T1027.001T1027.002T1588.002T1003.006T1069T1566.001T1566.002T1566.003T1057T1090.001T1090.003T1090.004T1021.006T1018T1053.005T1505.003T1218.011T1558.003T1553.002T1195.002T1082T1016.001T1199T1552.004T1550T1550.003T1550.004T1204.001T1204.002T1078T1078.002T1102.002T1047'),
('G0022','APT3','Gothic Panda,Pirpi,UPS Team,Buckeye,Threat Group-0110,TG-0110','T1087.001T1098T1560.001T1547.001T1110.002T1059.001T1059.003T1136.001T1543.003T1555.003T1005T1074.001T1546.008T1041T1203T1083T1564.003T1574.002T1070.004T1105T1056.001T1104T1095T1027.002.005T1003.001T1069T1566.002T1057T1090.002T1021.001T1021.002T1018T1053.005T1218.011T1082T1016T1049T1033T1552.001T1204.001T1078.002'),
('G0013','APT30','','T1566.001T1204.002'),
('G0050','APT32','SeaLotus,OceanLotus,APT-C-00','T1087.001T1583.001T1583.006T1071.001T1071.003T1560T1547.001T1059T1059.001T1059.003T1059.005T1059.007T1543.003T1189T1585.001T1048.003T1041T1203T1068T1083T1222.002T1589T1589.002T1564.001T1564.003T1564.004T1574.002T1070.001T1070.004T1070.006T1105T1056.001T1570T1036T1036.003T1036.004T1036.005T1112T1046T1135T1571T1027T1027.001T1588.002T1137T1003T1003.001T1566.001T1566.002T1598.003T1055T1012T1021.002T1018T1053.005T1505.003T1218.005T1218.01T1218.011T1216.001T1072T1608.001T1608.004T1082T1016T1049T1033T1569.002T1552.002T1550.002T1550.003T1204.001T1204.002T1078.003T1102T1047'),
('G0064','APT33','HOLMIUM,Elfin','T1071.001T1560.001T1547.001T1110.003T1059.001T1059.005T1555T1555.003T1132.001T1573.001T1546.003T1048.003T1203T1068T1105T1040T1571T1027T1588.002T1003.001T1003.004T1003.005T1566.001T1566.002T1053.005T1552.001T1552.006T1204.001T1204.002T1078T1078.004'),
('G0067','APT37','Richochet Chollima,InkySquid,ScarCruft,Reaper,Group123,TEMP.Reaper','T1548.002T1071.001T1123T1547.001T1059T1059.003T1059.005T1059.006T1555.003T1005T1561.002T1189T1203T1105T1559.002T1036.001T1106T1027T1027.003T1120T1566.001T1057T1055T1053.005T1082T1033T1529T1204.002T1102.002'),
('G0082','APT38','NICKEL GLADSTONE,BeagleBoyz,Bluenoroff,Stardust Chollima','T1071.001T1217T1110T1115T1059.001T1059.003T1059.005T1543.003T1485T1486T1005T1565.001T1565.002T1565.003T1561.002T1189T1083T1562.003T1562.004T1070.001T1070.004T1070.006T1105T1056.001T1112T1106T1135T1027.002T1588.002T1566.001T1057T1053.003T1053.005T1505.003T1218.011T1518.001T1082T1049T1033T1569.002T1529T1204.002'),
('G0087','APT39','REMIX KITTEN,ITG07,Chafer','T1071.001T1071.004T1560.001T1197T1547.001T1547.009T1110T1115T1059T1059.001T1059.005T1059.006T1136.001T1555T1005T1074.001T1140T1546.01T1041T1190T1083T1070.004T1105T1056T1056.001T1036.005T1046T1135T1027T1027.002T1588.002T1003T1003.001T1566.001T1566.002T1090.001T1090.002T1012T1021.001T1021.002T1021.004T1018T1053.005T1113T1505.003T1553.006T1033T1569.002T1204.001T1204.002T1078T1102.002'),
('G0096','APT41','WICKED PANDA','T1071.001T1071.002T1071.004T1560.001T1197T1547.001T1110.002T1059.001T1059.003T1059.004T1136.001T1543.003T1486T1005T1568.002T1546.008T1480.001T1190T1203T1133T1008T1083T1574.001T1574.002T1574.006T1070.001T1070.003T1070.004T1105T1056.001T1036.004T1036.005T1112T1104T1046T1135T1027T1588.002T1003.001T1566.001T1542.003T1055T1090T1021.001T1021.002T1496T1014T1053.005T1218.001T1218.011T1553.002T1195.002T1016T1049T1033T1569.002T1078T1102.001T1047'),
('G0001','Axiom','Group 72','T1001T1001.002T1546.008T1190T1003T1021.001'),
('G0135','BackdoorDiplomacy','','T1074.001T1190T1574.001T1105T1036.004T1036.005T1046T1095T1027T1588.001T1588.002T1120T1055.001T1505.003T1049'),
('G0063','BlackOasis','','T1027'),
('G0098','BlackTech','','T1190T1203T1574.002T1036.002T1566.001T1566.002T1204.001T1204.002'),
('G0108','Blue Mockingbird','','T1134T1059.001T1059.003T1543.003T1546.003T1190T1574.012T1036.005T1112T1027T1588.002T1003.001T1090T1021.001T1021.002T1496T1053.005T1218.01T1218.011T1082T1569.002T1047'),
('G0097','Bouncing Golf','','T1476T1444'),
('G0060','BRONZE BUTLER','REDBALDKNIGHT,Tick','T1548.002T1087.002T1071.001T1560.001T1547.001T1059.001T1059.003T1059.005T1059.006T1132.001T1005T1039T1140T1189T1573.001T1203T1083T1574.002T1562.001T1070.004T1105T1036T1036.002T1036.005T1027.001T1027.003T1588.002T1003.001T1566.001T1018T1053.002T1053.005T1113T1518T1007T1124T1080T1550.003T1204.002T1102.001'),
('G0008','Carbanak','Anunak','T1543.003T1562.004T1036.004T1036.005T1588.002T1219T1218.011T1078T1102.002'),
('G0114','Chimera','','T1087.001T1087.002T1071.001T1071.004T1560.001T1119T1217T1110.003T1110.004T1059.001T1059.003T1213.002T1039T1074.001T1074.002T1482T1114.001T1114.002T1041T1567.002T1133T1083T1589.001T1574.002T1070.001T1070.004T1070.006T1105T1570T1036.005T1556.001T1106T1046T1135T1027T1588.002T1003.003T1201T1069.001T1057T1572T1012T1021.001T1021.002T1021.006T1018T1053.005T1082T1016T1049T1033T1007T1569.002T1124T1111T1550.002T1078T1078.002T1047'),
('G0003','Cleaver','Threat Group 2889,TG-2889','T1557.002T1587.001T1585.001T1588.002T1003.001'),
('G0080','Cobalt Group','GOLD KINGSWOOD,Cobalt Gang,Cobalt Spider','T1548.002T1071.001T1071.004T1547.001T1037.001T1059.001T1059.003T1059.005T1059.007T1543.003T1573.002T1203T1068T1070.004T1105T1559.002T1046T1027T1588.002T1566.001.002T1055T1572T1219T1021.001T1053.005T1218.003T1218.008T1218.01T1518.001T1195.002T1204.001T1204.002T1220'),
('G0052','CopyKittens','','T1560.001T1560.003T1059.001T1564.003T1588.002T1218.011T1553.002'),
('G0132','CostaRicto','','T1046T1588.002T1572T1090.003T1053.005'),
('G0070','Dark Caracal','','T1071.001T1547.001T1059.003T1005T1189T1083T1027T1027.002T1566.003T1113T1218.001T1204.002T1476T1437'),
('G0012','Darkhotel','DUBNIUM','T1547.001T1547.009T1059.003T1140T1189T1573.001T1203T1083T1105T1056.001T1036.005T1027T1566.001T1057T1091T1518.001T1553.002T1082T1016T1124T1080T1204.002T1497T1497.001T1497.002'),
('G0079','DarkHydrus','','T1059.001T1187T1564.003T1588.002T1566.001T1221T1204.002'),
('G0105','DarkVishnya','','T1110T1059.001T1543.003T1200T1046T1135T1040T1571T1588.002T1219'),
('G0009','Deep Panda','Shell Crew,WebMasters,KungFu Kittens,PinkPanther,Black Vine','T1059.001T1546.008T1564.003T1027.005T1057T1021.002T1018T1505.003T1218.01T1047'),
('G0035','Dragonfly','TG-4192,Crouching Yeti,IRON LIBERTY,Energetic Bear','T1059.001T1546.008T1564.003T1027.005T1057T1021.002T1018T1505.003T1218.01T1047'),
('G0074','Dragonfly 2.0','IRON LIBERTY,DYMALLOY,Berserk Bear','T1087.002T1098T1071T1560T1547.001T1547.009T1110.002T1059T1059.001T1059.003T1059.006T1136.001T1005T1074.001T1189T1114.002T1133T1083T1187T1564.002T1562.004T1070.001T1070.004T1105T1036T1112T1135T1003.002T1003.003T1003.004T1069.002T1566.001T1566.002T1012T1021.001T1018T1053.005T1113T1505.003T1016T1033T1221T1204.001T1204.002T1078'),
('G0017','DragonOK','','T1087.002T1098T1071T1560T1547.001T1547.009T1110.002T1059T1059.001T1059.003T1059.006T1136.001T1005T1074.001T1189T1114.002T1133T1083T1187T1564.002T1562.004T1070.001T1070.004T1105T1036T1112T1135T1003.002T1003.003T1003.004T1069.002T1566.001T1566.002T1012T1021.001T1018T1053.005T1113T1505.003T1016T1033T1221T1204.001T1204.002T1078'),
('G0031','Dust Storm','','T1005T1083T1027'),
('G0066','Elderwood','Elderwood Gang,Beijing Group,Sneaky Panda','T1189T1203T1105T1027T1027.002T1566.001T1566.002T1204.001T1204.002'),
('G0020','Equation','','T1480.001T1564.005T1120T1542.002'),
('G0120','Evilnum','','T1548.002T1059.007T1555T1574.001T1070.004T1105T1566.002T1219T1539T1204.001T1497.001'),
('G0137','Ferocious Kitten','','T1583.001T1036.002T1036.005T1588.002T1566.001T1204.002'),
('G0051','FIN10','','T1547.001T1059.001T1059.003T1070.004T1570T1588.002T1021.001T1053.005T1033T1078T1078.003'),
('G0085','FIN4','','T1071.001T1059.005T1114.002T1564.008T1056.001T1056.002T1566.001T1566.002T1090.003T1204.001T1204.002T1078'),
('G0053','FIN5','','T1119T1110T1059T1074.001T1133T1070.001T1070.004T1588.002T1090.002T1018T1078'),
('G0037','FIN6','Magecart Group 6,SKELETON SPIDER,ITG08','T1134T1087.002T1560T1560.003T1119T1547.001T1110.002T1059T1059.001T1059.003T1059.007T1555T1555.003T1213T1005T1074.002T1573.002T1048.003T1068T1562.001T1070.004T1036.004T1046T1095T1027T1588.002T1003.001T1003.003T1566.001T1566.003T1572T1021.001T1018T1053.005T1553.002T1569.002T1204.002T1078T1102T1047'),
('G0046','FIN7','GOLD NIAGARA,ITG14,Carbon Spider','T1583.001T1071.004T1547.001T1059T1059.001T1059.003T1059.005T1059.007T1543.003T1486T1005T1587.001T1546.011T1567.002T1210T1008T1105T1559.002T1036.004T1036.005T1571T1027T1566.001T1566.002T1021.001T1021.004T1021.005T1053.005T1113T1218.005T1558.003T1553.002T1204.001T1204.002T1078T1125T1497.002T1102.002T1047'),
('G0061','FIN8','','T1134.001T1071.001T1560.001T1059.001T1059.003T1074.002T1482T1573.002T1546.003T1048.003T1068T1070.001T1070.004T1105T1112T1027T1003.001T1566.001T1566.002T1055.004T1021.001T1021.002T1018T1053.005T1518.001T1204.001T1204.002T1078T1102T1047'),
('G0117','Fox Kitten','UNC757,PIONEER KITTEN,Parisite','T1087.001T1087.002T1560.001T1217T1110T1059T1059.001T1059.003T1136.001T1555.005T1530T1213T1005T1039T1585T1585.001T1546.008T1190T1210T1083T1105T1036.004T1036.005T1046T1027T1003.001T1003.003T1572T1090T1012T1021.001T1021.002T1021.004T1021.005T1018T1053.005T1505.003T1552.001T1078T1102'),
('G0101','Frankenstein','','T1119T1020T1059.001T1059.003T1059.005T1005T1140T1573.001T1041T1203T1105T1027T1588.002T1003T1566.001T1057T1053.005T1518.001T1082T1016T1033T1221T1127.001T1204.002T1497.001T1047'),
('G0093','GALLIUM','Operation Soft Cell','T1583.004T1560.001T1059.001T1059.003T1136.002T1005T1074.001T1041T1190T1133T1574.002T1105T1570T1036.003T1027T1027.002T1027.005T1588.002T1003.001T1003.002T1090.002T1018T1053.005T1505.003T1553.002T1016T1049T1033T1550.002T1078T1047'),
('G0084','Gallmaker','','T1560.001T1059.001T1559.002T1027T1566.001T1204.002'),
('G0047','Gamaredon Group','','T1071.001T1119T1020T1547.001T1059.003T1059.005T1005T1039T1025T1140T1041T1083T1562.001T1070.004T1105T1559.001T1534T1112T1106T1027T1027.001T1027.004T1137T1120T1566.001T1053.005T1113T1218.011T1082T1033T1080T1221T1204.002T1102'),
('G0036','GCMAN','','T1021.004T1021.005'),
('G0115','GOLD SOUTHFIELD','','T1059.001T1190T1133T1027T1566T1219T1113T1195.002T1199'),
('G0078','Gorgon Group','','T1547.001T1547.009T1059.001T1059.003T1059.005T1140T1564.003T1562.001T1105T1112T1106T1588.002T1566.001T1055.002T1055.012T1204.002'),
('G0043','Group5','','T1070.004T1056.001T1027T1113'),
('G0125','HAFNIUM','Operation Exchange Marauder','T1583.003T1583.006T1071.001T1560.001T1059.001T1136.002T1132.001T1114.002T1567.002T1203T1592.004T1589.002T1590T1590.005T1105T1095T1003.001T1003.003T1505.003T1218.011T1078.003'),
('G0126','Higaisa','','T1071.001T1547.001T1059.003T1059.005T1059.007T1001.003T1140T1573.001T1041T1203T1564.003T1574.002T1036.004T1106T1027T1027.001T1566.001T1057T1090.001T1053.005T1029T1082T1016T1124T1204.002T1220'),
('G0072','Honeybee','','T1548.002T1071.002T1560T1020T1547.001T1059.003T1059.005T1543.003T1005T1074.001T1140T1546.009T1083T1070.004T1112T1027T1057T1055T1553.002T1082T1569.002'),
('G0100','Inception','Inception Framework,Cloud Atlas','T1071.001T1547.001T1059.001T1059.005T1555.003T1005T1573.001T1203T1083T1027T1588.002T1069.002T1566.001T1057T1090.003T1218.005T1218.01T1518T1082T1221T1204.002T1102'),
('G0136','IndigoZebra','','T1583.001T1583.006T1586.002T1105T1588.002T1566.001T1204.002'),
('G0119','Indrik Spider','Evil Corp','T1059.001T1059.003T1059.007T1584.004T1136T1486T1074.001T1484.001T1562.001T1070.001T1105T1036.005T1003.001T1018T1489T1007T1204.002T1078.002T1047'),
('G0004','Ke3chang','APT15,Mirage,Vixen Panda,GREF,Playful Dragon,RoyalAPT','T1087.001T1087.002T1071.001T1071.004T1560T1560.001T1547.001T1059T1059.003T1543.003T1213.002T1005T1114.002T1041T1133T1083T1056.001T1036.002T1588.002T1003.001T1003.002T1003.004T1069.002T1057T1021.002T1018T1558.001T1082T1016T1049T1007T1569.002'),
('G0094','Kimsuky','STOLEN PENCIL,Thallium,Black Banshee,Velvet Chollima','T1583.001T1557T1071.002T1071.003T1560.003T1547.001T1176T1059.001T1059.005T1059.006T1059.007T1586.002T1543.003T1555.003T1005T1074.001T1587T1114.003T1546.001T1041T1133T1083T1589.002T1562.001T1562.004T1070.004T1070.006T1105T1056.001T1036.004T1112T1040T1027T1027.002T1588.002T1003.001T1566.001T1566.002T1598.003T1055T1219T1021.001T1593.001T1505.003T1218.005T1553.002T1082T1552.001T1550.002T1204.002T1078.003'),
('G0032','Lazarus Group','HIDDEN COBRA,Guardians of Peace,ZINC,NICKEL ACADEMY','T1134.002T1098T1583.001T1583.006T1071.001T1010T1560T1560.002T1560.003T1547.001T1547.009T1110.003T1059.003T1543.003T1485T1132.001T1005T1001.003T1074.001T1491.001T1587.001T1561.001T1561.002T1189T1573.001T1048.003T1041T1203T1008T1083T1564.001T1562.001T1562.004T1070.004T1070.006T1105T1056.001T1036.005T1571T1027T1588.004T1566.001T1542.003T1057T1055.001T1090.002T1012T1021.001T1021.002T1489T1218.001T1082T1016T1033T1529T1124T1204.002T1047'),
('G0077','Leafminer','Raspite','T1110.003T1059.007T1136.001T1555T1555.003T1189T1114.002T1083T1046T1027T1588.002T1003.001T1003.004T1003.005T1055.013T1018T1552.001'),
('G0065','Leviathan','MUDCARP,Kryptonite Panda,Gadolinium,BRONZE MOHAWK,TEMP.Jumper,APT40,TEMP.Periscope','T1583.001T1560T1197T1547.001T1547.009T1059.001T1059.005T1586.001T1586.002T1074.001T1074.002T1140T1189T1585.001T1585.002T1546.003T1041T1567.002T1203T1133T1589.001T1105T1559.002T1534T1027T1027.001T1027.003T1003T1003.001T1566.001T1566.002T1055.001T1572T1090.003T1021.001T1021.004T1505.003T1218.01T1553.002T1204.001T1204.002T1078T1102.003T1047'),
('G0030','Lotus Blossom','DRAGONFISH,Spring Dragon',''),
('G0095','Machete','APT-C-43,El Machete','T1059.003T1059.005T1059.006T1189T1036.005T1566.001T1566.002T1053.005T1218.007T1204.001T1204.002'),
('G0059','Magic Hound','TA453,COBALT ILLUSION,Charming Kitten,ITG18,Phosphorus,Newscaster,APT35','T1098.002T1583.001T1071T1071.001T1560.001T1547.001T1059.001T1059.003T1059.005T1586.002T1584.001T1114T1114.001T1585.001T1585.002T1083T1589T1589.001T1589.002T1564.003T1070.004T1105T1056.001T1571T1027T1588.002T1003.001T1566.002.003T1598.003T1057T1113T1082T1016T1033T1204.001T1204.002T1102.002'),
('G0045','menuPass','Cicada,POTASSIUM,Stone Panda,APT10,Red Apollo,CVNX,HOGFISH','T1087.002T1583.001T1560T1560.001T1119T1059.001T1059.003T1005T1039T1074.001T1074.002T1140T1568.001T1190T1210T1083T1574.001T1574.002T1070.003T1070.004T1105T1056.001T1036T1036.003T1036.005T1106T1046T1027T1588.002T1003.002T1003.003T1003.004T1566.001T1055.012T1090.002T1021.001T1021.004T1018T1053.005T1218.004T1553.002T1016T1049T1199T1204.002T1078T1047'),
('G0002','Moafee','','T1027.001'),
('G0103','Mofang','','T1027T1566.001T1566.002T1204.001T1204.002'),
('G0021','Molerats','Operation Molerats,Gaza Cybergang','T1547.001T1059.001T1059.005T1059.007T1555.003T1140T1105T1027T1566.001T1566.002T1057T1053.005T1218.007T1553.002T1204.001T1204.002'),
('G0069','MuddyWater','Earth Vetala,MERCURY,Static Kitten,Seedworm,TEMP.Zagros','T1548.002T1087.002T1583.006T1071.001T1560.001T1547.001T1059.001T1059.003T1059.005T1059.006T1059.007T1555T1555.003T1132.001T1140T1041T1203T1083T1589.002T1562.001T1105T1559.001T1559.002T1036.005T1104T1027T1027.003T1027.004T1588.002T1137.001T1003.001T1003.004T1003.005T1566.001T1566.002T1057T1090.002T1219T1053.005T1113T1218.003T1218.005T1218.011T1518T1518.001T1082T1016T1049T1033T1552.001T1204.001T1204.002T1102.002T1047'),
('G0129','Mustang Panda','TA416,RedDelta,BRONZE PRESIDENT','T1583.001T1071.001T1560.001T1560.003T1119T1547.001T1059.001T1059.003T1059.005T1074.001T1573.001T1546.003T1052.001T1203T1083T1564.001T1574.002T1070.004T1105T1036.005T1036.007T1027T1027.001T1003.003T1566.001T1566.002T1057T1219T1091T1053.005T1218.004T1218.005T1518T1082T1016T1049T1204.001T1204.002T1047'),
('G0019','Naikon','','T1547.001T1574.002T1036.004T1036.005T1046T1137.006T1566.001T1018T1053.005T1518.001T1016T1204.002T1078.002T1047'),
('G0055','NEODYMIUM','',''),
('G0014','Night Dragon','','T1071.001T1074.002T1587.001T1190T1133T1562.001T1027T1027.002T1588.002T1003.002T1566.002T1219T1550.002T1204.001T1078'),
('G0133','Nomadic Octopus','DustSquad','T1059.001T1059.003T1564.003T1105T1036T1566.001T1204.002'),
('G0049','OilRig','COBALT GYPSY,IRN2,HELIX KITTEN,APT34','T1087.001T1087.002T1071.001T1071.004T1119T1110T1059T1059.001T1059.003T1059.005T1555T1555.003T1555.004T1140T1573.002T1048.003T1133T1008T1070.004T1105T1056.001T1036T1046T1027T1027.005T1137.004T1003.001T1003.004T1003.005T1201T1120T1069.001T1069.002T1566.001T1566.002T1566.003T1566T1572T1012T1021.001.004T1053.005T1113T1505.003T1218.001T1082T1016T1049T1033T1007T1552.001T1204.001T1204.002T1078T1497.001T1047'),
('G0116','Operation Wocao','','T1087.002T1560.001T1119T1115T1059.001T1059.003T1059.005T1059.006T1555.005T1005T1001T1074.001T1573.002T1041T1190T1133T1083T1562.004T1070.001T1070.004T1105T1056.001T1570T1112T1106T1046T1135T1095T1027T1027.005T1003.001T1003.006T1120T1069.001T1057T1055T1090T1090.001T1090.003T1012T1021.002T1018T1053.005T1505.003T1518T1518.001T1558.003T1082T1016T1049T1033T1007T1569.002T1124T1111T1552.004T1078T1078.002T1078.003T1047'),
('G0071','Orangeworm','','T1071.001T1021.002'),
('G0040','Patchwork','Hangover Group,Dropping Elephant,Chinastrats,MONSOON,Operation Hangover','T1548.002T1560T1119T1197T1547.001T1059.001T1059.003T1059.005T1555.003T1132.001T1005T1074.001T1587.002T1189T1203T1083T1574.002T1070.004T1105T1559.002T1036.005T1112T1027T1027.001T1027.002T1027.005T1588.002T1566.001T1566.002T1055.012T1021.001T1053.005T1518.001T1553.002T1082T1033T1204.001T1204.002T1102.001'),
('G0011','PittyTiger','','T1588.002T1078'),
('G0068','PLATINUM','','T1189T1068T1105T1056.001T1056.004T1036T1095T1003.001T1566.001T1055T1204.002'),
('G0033','Poseidon Group','','T1087.001T1087.002T1059.001T1036.005T1003T1057T1049T1007'),
('G0056','PROMETHIUM','StrongPity','T1547.001T1543.003T1587.002T1587.003T1189T1036.004T1036.005T1553.002T1205.001T1204.002T1078.003'),
('G0024','Putter Panda','APT2,MSUpdater','T1547.001T1562.001T1027T1055.001'),
('G0075','Rancor','','T1071.001T1059.003T1059.005T1105T1566.001T1053.005T1218.007T1204.002'),
('G0106','Rocke','','T1071T1071.001T1547.001T1037T1059.004T1059.006T1543.002T1140T1190T1222.002T1564.001T1574.006T1562.001T1562.004T1070.002T1070.004T1070.006T1105T1036.005T1046T1571T1027T1027.002T1027.004T1057T1055.002T1021.004T1018T1496T1014T1053.003T1518.001T1082T1552.004T1102T1102.001'),
('G0048','RTM','','T1547.001T1189T1574.001T1566.001T1219T1204.002T1102.001'),
('G0034','Sandworm Team','ELECTRUM,Telebots,IRON VIKING,BlackEnergy (Group),Quedagh,VOODOO BEAR','T1087.002T1087.003T1098T1583.001T1583.004T1595.002T1071.001T1110.003T1059.001T1059.003T1059.005T1136T1136.002T1555.003T1485T1132.001T1005T1491.002T1140T1587.001T1561.002T1499T1585.001T1585.002T1041T1203T1133T1083T1592.002T1589.002T1589.003T1590.001T1591.002T1562.002T1070.004T1105T1056.001T1570T1036.005T1040T1571T1027T1027.002T1588.002T1588.006T1003.001T1566.001T1566.002T1598.003T1090T1219T1021.002T1018T1593T1594T1505.001T1505.003T1218.011T1195.002T1082T1016T1049T1033T1199T1204.001T1204.002T1078T1078.002T1102.002T1047'),
('G0029','Scarlet Mimic','','T1036.002'),
('G0104','Sharpshooter','','T1547.001T1059.005T1105T1559.002T1106T1566.001T1055T1204.002'),
('G0121','Sidewinder','T-APT-04,Rattlesnake','T1071.001T1119T1020T1547.001T1059.001T1059.005T1059.007T1074.001T1203T1083T1574.002T1105T1559.002T1036.005T1027T1566.001T1566.002T1598.002T1598.003T1057T1218.005T1518T1518.001T1082T1016T1033T1124T1204.001T1204.002'),
('G0091','Silence','WHISPER SPIDER','T1547.001T1059.001T1059.003T1059.005T1059.007T1070.004T1105T1036.005T1112T1106T1571T1027T1588.002T1003.001T1566.001T1055T1090.002T1021.001T1018T1053.005T1113T1218.001T1072T1553.002T1569.002T1204.002T1078T1125'),
('G0122','Silent Librarian','TA407,COBALT DICKENS','T1583.001T1110.003T1114T1114.003T1585.002T1589.002T1589.003T1588.002T1588.004T1598.003T1594T1608.005T1078'),
('G0083','SilverTerrier','','T1071.001T1071.002T1071.003'),
('G0054','Sowbug','','T1560.001T1059.003T1039T1083T1056.001T1036.005T1135T1003T1082'),
('G0038','Stealth Falcon','','T1071.001T1059T1059.001T1555T1555.003T1555.004T1005T1573.001T1041T1057T1012T1053.005T1082T1016T1033T1047'),
('G0041','Strider','ProjectSauron','T1564.005T1556.002T1090.001'),
('G0039','Suckfly','','T1059.003T1046T1003T1553.002T1078'),
('G0062','TA459','','T1059.001T1059.005T1203T1566.001T1204.002'),
('G0092','TA505','Hive0065','T1087.003T1071.001T1059.001T1059.003T1059.005T1059.007T1555.003T1486T1568.001T1105T1559.002T1027T1027.002T1069T1566.001T1566.002T1055.001T1218.007T1218.011T1553.002T1553.005T1552.001T1204.001T1204.002T1078.002'),
('G0127','TA551','GOLD CABIN,Shathak','T1071.001T1059.003T1132.001T1568.002T1589.002T1105T1036T1027T1027.003T1566.001T1218.005T1218.01T1218.011T1204.002'),
('G0139','TeamTNT','','T1098.004T1583.001T1595.001T1595.002T1071T1071.001T1547.001T1059.001T1059.003T1059.004T1609T1613T1136.001T1543.002T1543.003T1610T1587.001T1611T1133T1222.002T1562.001T1562.004T1070.002T1070.003T1070.004T1105T1046T1027T1027.002T1057T1219T1021.004T1496T1014T1518.001T1608.001T1082T1016T1049T1552.001T1552.004T1552.005T1204.003T1102'),
('G0088','TEMP.Veles','XENOTIME','T1583.003T1059.001T1074.001T1546.012T1133T1070.004T1070.006T1036.005T1571T1027.005T1588.002T1003.001T1021.001T1021.004T1053.005T1505.003T1078'),
('G0089','The White Company','','T1203T1070.004T1027.002T1566.001T1518.001T1124T1204.002'),
('G0028','Threat Group-1314','TG-1314','T1059.003T1021.002T1072T1078.002'),
('G0027','Threat Group-3390','TG-3390,Emissary Panda,BRONZE UNION,APT27,Iron Tiger,LuckyMouse','T1548.002T1087.001T1071.001T1560.002T1119T1547.001T1059.001T1059.003T1543.003T1005T1074.001T1074.002T1030T1140T1189T1203T1068T1210T1133T1574.001T1574.002T1562.002T1070.004T1070.005T1105T1056.001T1112T1046T1027T1588.002T1003.001T1003.002T1003.004T1055.012T1012T1021.006T1018T1053.002T1505.003T1608.002T1608.004T1016T1049T1078T1047'),
('G0076','Thrip','','T1059.001T1048.003T1588.002T1219'),
('G0131','Tonto Team','Earth Akhlut,BRONZE HUNTLEY,CactusPete,Karma Panda','T1059.001T1059.006T1203T1068T1210T1574.001T1105T1056.001T1135T1003T1069.001T1566.001T1090.002T1505.003T1204.002'),
('G0134','Transparent Tribe','COPPER FIELDSTONE,APT36,Mythic Leopard,ProjectM','T1583.001T1059.005T1584.001T1189T1568T1203T1564.001T1036.005T1027T1566.001T1566.002T1608.004T1204.001T1204.002'),
('G0081','Tropic Trooper','Pirate Panda,KeyBoy','T1071.001T1071.004T1119T1020T1547.001T1547.004T1059.003T1543.003T1132.001T1140T1573T1573.002T1052.001T1203T1083T1564.001T1574.002T1070.004T1105T1036.005T1106T1046T1135T1027T1027.003T1566.001T1057T1055.001T1091T1505.003T1518T1518.001T1082T1016T1049T1033T1221T1204.002T1078.003'),
('G0010','Turla','Group 88,Belugasturgeon,Waterbug,WhiteBear,VENOMOUS BEAR,Snake,Krypton','T1134.002T1087.001T1087.002T1583.006T1071.001T1071.003T1560.001T1547.001T1547.004T1110T1059.001T1059.003T1059.005T1059.006T1059.007T1584.003T1584.004T1584.006T1555.004T1213T1005T1025T1140T1587.001T1189T1546.003T1546.013T1567.002T1068T1083T1615T1562.001T1105T1570T1112T1106T1027T1027.005T1588.001T1588.002T1201T1120T1069.001T1069.002T1566.002T1057T1055T1055.001T1090T1012T1021.002T1018T1518.001T1553.006T1082T1016T1016.001T1049T1007T1124T1204.001T1078.003T1102T1102.002'),
('G0123','Volatile Cedar','Lebanese Cedar','T1595.002T1190T1105T1505.003'),
('G0107','Whitefly','','T1059T1068T1574.001T1105T1036.005T1027T1588.002T1003.001T1204.002'),
('G0124','Windigo','','T1059T1005T1189T1083T1090T1518T1082'),
('G0112','Windshift','Bahamut','T1071.001T1547.001T1059.005T1189T1105T1036T1036.001T1027T1566.001T1566.002T1566.003T1057T1518T1518.001T1082T1033T1204.001T1204.002T1047T1432T1429T1512T1412T1533T1475T1476T1407T1523T1420T1581T1417T1478T1430T1406T1521T1426'),
('G0044','Winnti Group','Blackfly','T1057T1014T1553.002'),
('G0090','WIRTE','','T1071.001T1059.001T1059.005T1140T1105T1588.002T1218.01'),
('G0102','Wizard Spider','UNC1878,TEMP.MixMaster,Grim Spider','T1087.002T1557.001T1071.001T1547.001T1547.004T1059.001T1059.003T1543.003T1074T1048.003T1041T1210T1133T1222.001T1562.001T1070.004T1570T1036.004T1112T1135T1027T1588.002T1588.003T1003.002T1003.003T1566.001T1566.002T1055.001T1021.001T1021.002T1021.006T1018T1053.005T1489T1518.001T1558.003T1553.002T1082T1016T1033T1569.002T1204.001T1204.002T1078T1078.002T1047'),
('G0128','ZIRCONIUM','APT31','T1583.001T1583.006T1547.001T1059.003T1059.006T1555.003T1140T1573.001T1041T1567.002T1068T1105T1036T1036.004T1027.002T1566.002T1598T1012T1218.007T1082T1016T1033T1124T1204.001T1102.002')
),
-- Expand the threat actor map out for each TTP they are associated with
Expanded_Group_Map AS (
SELECT
Id,
Name,
'https://attack.mitre.org/groups/'||id URL,
REPLACE(Related_groups,',',CHR(10)) Related_Groups,
'T'||TTP.Single_TTP TTP
FROM TTP_Group_Map CROSS JOIN UNNEST(SPLIT(LTRIM(TTP_Group_Map.TTPs,'T'),'T')) AS TTP (Single_TTP)
),
-- Extract a list of TTPs for all detections
Detection_TTP_LIST AS (
SELECT
detection_id_dedup,
ARRAY_JOIN(ARRAY_AGG(CAST(JSON_EXTRACT(ioc_detection_mitre_attack,'$['||x||'].tactic.techniques['||y||'].id') AS VARCHAR)),',') TTP_List
FROM xdr_ti_data, Max_Tactics, Max_Techniques
WHERE ioc_detection_category IN ('Classifier','Threat')
AND ioc_detection_weight >= $$Risk >=$$
AND LOWER(meta_hostname) LIKE LOWER('%$$Device name$$%')
GROUP BY detection_id_dedup
)
-- Now we can list all Detections with the attribution information to one or more threat actors
SELECT
x2.meta_hostname ep_name,
x2.calendar_time Date_Time,
CAST((TO_UNIXTIME(NOW())-TO_UNIXTIME(x2.calendar_time))/60 AS INT) Minutes_ago,
x2.ioc_detection_description,
REPLACE(Detection_TTP_LIST.TTP_List,',',CHR(10)) TTP_List,
ARRAY_JOIN(ARRAY_AGG(DISTINCT Expanded_Group_Map.Name||' - '||Expanded_Group_Map.url),CHR(10)) Attribution_List,
x2.ioc_detection_weight Risk,
x2.sophos_pid,
x2.name,
x2.cmdline,
x2.user_name,
x2.ioc_detection_id
FROM xdr_ti_data X2
JOIN Detection_TTP_LIST ON Detection_TTP_LIST.detection_id_dedup = x2.detection_id_dedup
JOIN Expanded_Group_Map ON TTP_List LIKE '%'||TTP||'%'
WHERE LOWER(Detection_TTP_LIST.TTP_List) LIKE LOWER('%$$Technique ID$$%')
AND LOWER(Expanded_Group_Map.Name) LIKE LOWER('%$$Threat Actor$$%')
AND TO_UNIXTIME(x2.Calendar_time) >= $$from date$$
AND TO_UNIXTIME(x2.Calendar_time) <= $$to date$$
GROUP BY x2.meta_hostname,
x2.ioc_detection_category,
x2.ioc_detection_id,
x2.ioc_detection_description,
Detection_TTP_LIST.TTP_List,
x2.ioc_detection_weight,
x2.sophos_pid,
x2.name,
x2.cmdline,
x2.calendar_time,
x2.user_name
ORDER BY x2.calendar_time DESCExample output
Threat Actor Details
The query below provides the public description from the MITRE ATT&CK website for the threat actor. Most current information would be available directly from the MTIRE Site.
VARIABLES
| Variable | Type | Value |
|
Threat Actor name
|
STRING | % |
SQL
-- Threat Actor Details
-- VARIABLE $$Threat Actor name$$ STRING
WITH Threat_Group_Info(ID, Name, Related_Groups, Description) AS ( VALUES
('G0018','admin@338','','admin@338 is a China-based cyber threat group. It has previously used newsworthy events as lures to deliver malware and has primarily targeted organizations involved in financial, economic, and trade policy, typically using publicly available RATs such as PoisonIvy, as well as some non-public backdoors.'),
('G0130','Ajax Security Team','Operation Woolen-Goldfish, AjaxTM, Rocket Kitten, Flying Kitten, Operation Saffron Rose','Ajax Security Team is a group that has been active since at least 2010 and believed to be operating out of Iran. By 2014 Ajax Security Team transitioned from website defacement operations to malware-based cyber espionage campaigns targeting the US defense industrial base and Iranian users of anti-censorship technologies.'),
('G0138','Andariel','Silent Chollima','Andariel is a North Korean state-sponsored threat group that has been active since at least 2009. Andariel has primarily focused its operations--which have included destructive attacks--against South Korean government agencies, military organizations, and a variety of domestic companies; they have also conducted cyber financial operations against ATMs, banks, and cryptocurrency exchanges. Andariels notable activity includes Operation Black Mine, Operation GoldenAxe, and Campaign Rifle. Andariel is considered a sub-set of Lazarus Group, and has been attributed to North Koreas Reconnaissance General Bureau. North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups.'),
('G0099','APT-C-36','Blind Eagle','APT-C-36 is a suspected South America espionage group that has been active since at least 2018. The group mainly targets Colombian government institutions as well as important corporations in the financial sector, petroleum industry, and professional manufacturing.'),
('G0006','APT1','Comment Crew, Comment Group, Comment Panda','APT1 is a Chinese threat group that has been attributed to the 2nd Bureau of the People’s Liberation Army (PLA) General Staff Department’s (GSD) 3rd Department, commonly known by its Military Unit Cover Designator (MUCD) as Unit 61398.'),
('G0005','APT12','IXESHE, DynCalc, Numbered Panda, DNSCALC','APT12 is a threat group that has been attributed to China. The group has targeted a variety of victims including but not limited to media outlets, high-tech companies, and multiple governments.'),
('G0023','APT16','','APT16 is a China-based threat group that has launched spearphishing campaigns targeting Japanese and Taiwanese organizations.'),
('G0025','APT17','Deputy Dog','APT17 is a China-based threat group that has conducted network intrusions against U.S. government entities, the defense industry, law firms, information technology companies, mining companies, and non-government organizations.'),
('G0026','APT18','TG-0416, Dynamite Panda, Threat Group-0416','APT18 is a threat group that has operated since at least 2009 and has targeted a range of industries, including technology, manufacturing, human rights groups, government, and medical.'),
('G0073','APT19','Codoso, C0d0so0, Codoso Team, Sunshop Group','APT19 is a Chinese-based threat group that has targeted a variety of industries, including defense, finance, energy, pharmaceutical, telecommunications, high tech, education, manufacturing, and legal services. In 2017, a phishing campaign was used to target seven law and investment firms. Some analysts track APT19 and Deep Panda as the same group, but it is unclear from open source information if the groups are the same.'),
('G0007','APT28','SNAKEMACKEREL, Swallowtail, Group 74, Sednit, Sofacy, Pawn Storm, Fancy Bear, STRONTIUM, Tsar Team, Threat Group-4127, TG-4127','APT28 is a threat group that has been attributed to Russias General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS) military unit 26165. This group has been active since at least 2004. APT28 reportedly compromised the Hillary Clinton campaign, the Democratic National Committee, and the Democratic Congressional Campaign Committee in 2016 in an attempt to interfere with the U.S. presidential election. In 2018, the US indicted five GRU Unit 26165 officers associated with APT28 for cyber operations (including close-access operations) conducted between 2014 and 2018 against the World Anti-Doping Agency (WADA), the US Anti-Doping Agency, a US nuclear facility, the Organization for the Prohibition of Chemical Weapons (OPCW), the Spiez Swiss Chemicals Laboratory, and other organizations. Some of these were conducted with the assistance of GRU Unit 74455, which is also referred to as Sandworm Team.'),
('G0016','APT29','NobleBaron, Dark Halo, StellarParticle, NOBELIUM, UNC2452, YTTRIUM, The Dukes, Cozy Bear, CozyDuke','APT29 is threat group that has been attributed to Russias Foreign Intelligence Service (SVR). They have operated since at least 2008, often targeting government networks in Europe and NATO member countries, research institutes, and think tanks. APT29 reportedly compromised the Democratic National Committee starting in the summer of 2015. In April 2021, the US and UK governments attributed the SolarWinds supply chain compromise cyber operation to the SVR; public statements included citations to APT29, Cozy Bear, and The Dukes. Victims of this campaign included government, consulting, technology, telecom, and other organizations in North America, Europe, Asia, and the Middle East. Industry reporting referred to the actors involved in this campaign as UNC2452, NOBELIUM, StellarParticle, and Dark Halo.'),
('G0022','APT3','Gothic Panda, Pirpi, UPS Team, Buckeye, Threat Group-0110, TG-0110','APT3 is a China-based threat group that researchers have attributed to Chinas Ministry of State Security. This group is responsible for the campaigns known as Operation Clandestine Fox, Operation Clandestine Wolf, and Operation Double Tap. As of June 2015, the group appears to have shifted from targeting primarily US victims to primarily political organizations in Hong Kong. In 2017, MITRE developed an APT3 Adversary Emulation Plan.'),
('G0013','APT30','','APT30 is a threat group suspected to be associated with the Chinese government. While Naikon shares some characteristics with APT30, the two groups do not appear to be exact matches.'),
('G0050','APT32','SeaLotus, OceanLotus, APT-C-00','APT32 is a suspected Vietnam-based threat group that has been active since at least 2014. The group has targeted multiple private sector industries as well as foreign governments, dissidents, and journalists with a strong focus on Southeast Asian countries like Vietnam, the Philippines, Laos, and Cambodia. They have extensively used strategic web compromises to compromise victims.'),
('G0064','APT33','HOLMIUM, Elfin','APT33 is a suspected Iranian threat group that has carried out operations since at least 2013. The group has targeted organizations across multiple industries in the United States, Saudi Arabia, and South Korea, with a particular interest in the aviation and energy sectors.'),
('G0067','APT37','Richochet Chollima, InkySquid, ScarCruft, Reaper, Group123, TEMP.Reaper','APT37 is a North Korean state-sponsored cyber espionage group that has been active since at least 2012. The group has targeted victims primarily in South Korea, but also in Japan, Vietnam, Russia, Nepal, China, India, Romania, Kuwait, and other parts of the Middle East. APT37 has also been linked to the following campaigns between 2016-2018: Operation Daybreak, Operation Erebus, Golden Time, Evil New Year, Are you Happy?, FreeMilk, North Korean Human Rights, and Evil New Year 2018. North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups.'),
('G0082','APT38','NICKEL GLADSTONE, BeagleBoyz, Bluenoroff, Stardust Chollima','APT38 is a North Korean state-sponsored threat group that specializes in financial cyber operations; it has been attributed to the Reconnaissance General Bureau. Active since at least 2014, APT38 has targeted banks, financial institutions, casinos, cryptocurrency exchanges, SWIFT system endpoints, and ATMs in at least 38 countries worldwide. Significant operations include the 2016 Bank of Bangladesh heist, during which APT38 stole $81 million, as well as attacks against Bancomext (2018) and Banco de Chile (2018); some of their attacks have been destructive. North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups.'),
('G0087','APT39','REMIX KITTEN, ITG07, Chafer','APT39 is one of several names for cyberespionage activity conducted by the Iranian Ministry of Intelligence and Security (MOIS) through the front company Rana Intelligence Computing since at least 2014. APT39 has primarily targeted the travel, hospitality, academic, and telecommunications industries in Iran and across Asia, Africa, Europe, and North America to track individuals and entities considered to be a threat by the MOIS.'),
('G0096','APT41','WICKED PANDA','APT41 is a threat group that researchers have assessed as Chinese state-sponsored espionage group that also conducts financially-motivated operations. Active since at least 2012, APT41 has been observed targeting healthcare, telecom, technology, and video game industries in 14 countries. APT41 overlaps at least partially with public reporting on groups including BARIUM and Winnti Group.'),
('G0001','Axiom','Group 72','Axiom is a cyber espionage group suspected to be associated with the Chinese government. It is responsible for the Operation SMN campaign. Though both this group and Winnti Group use the malware Winnti for Windows, the two groups appear to be distinct based on differences in reporting on the groups TTPs and targeting.'),
('G0135','BackdoorDiplomacy','','BackdoorDiplomacy is a cyber espionage threat group that has been active since at least 2017. BackdoorDiplomacy has targeted Ministries of Foreign Affairs and telecommunication companies in Africa, Europe, the Middle East, and Asia.'),
('G0063','BlackOasis','','BlackOasis is a Middle Eastern threat group that is believed to be a customer of Gamma Group. The group has shown interest in prominent figures in the United Nations, as well as opposition bloggers, activists, regional news correspondents, and think tanks. A group known by Microsoft as NEODYMIUM is reportedly associated closely with BlackOasis operations, but evidence that the group names are aliases has not been identified.'),
('G0098','BlackTech','','BlackTech is a cyber espionage group operating against targets in East Asia, particularly Taiwan, and occasionally, Japan and Hong Kong.'),
('G0108','Blue Mockingbird','','Blue Mockingbird is a cluster of observed activity involving Monero cryptocurrency-mining payloads in dynamic-link library (DLL) form on Windows systems. The earliest observed Blue Mockingbird tools were created in December 2019.'),
('G0097','Bouncing Golf','','Bouncing Golf is a cyberespionage campaign targeting Middle Eastern countries.'),
('G0060','BRONZE BUTLER','REDBALDKNIGHT, Tick','BRONZE BUTLER is a cyber espionage group with likely Chinese origins that has been active since at least 2008. The group primarily targets Japanese organizations, particularly those in government, biotechnology, electronics manufacturing, and industrial chemistry.'),
('G0008','Carbanak','Anunak','Carbanak is a cybercriminal group that has used Carbanak malware to target financial institutions since at least 2013. Carbanak may be linked to groups tracked separately as Cobalt Group and FIN7 that have also used Carbanak malware.'),
('G0114','Chimera','','Chimera is a suspected China-based threat group that has been active since at least 2018 targeting the semiconductor industry in Taiwan as well as data from the airline industry.'),
('G0003','Cleaver','Threat Group 2889, TG-2889','Cleaver is a threat group that has been attributed to Iranian actors and is responsible for activity tracked as Operation Cleaver. Strong circumstantial evidence suggests Cleaver is linked to Threat Group 2889 (TG-2889).'),
('G0080','Cobalt Group','GOLD KINGSWOOD, Cobalt Gang, Cobalt Spider','Cobalt Group is a financially motivated threat group that has primarily targeted financial institutions since at least 2016. The group has conducted intrusions to steal money via targeting ATM systems, card processing, payment systems and SWIFT systems. Cobalt Group has mainly targeted banks in Eastern Europe, Central Asia, and Southeast Asia. One of the alleged leaders was arrested in Spain in early 2018, but the group still appears to be active. The group has been known to target organizations in order to use their access to then compromise additional victims. Reporting indicates there may be links between Cobalt Group and both the malware Carbanak and the group Carbanak.'),
('G0052','CopyKittens','','CopyKittens is an Iranian cyber espionage group that has been operating since at least 2013. It has targeted countries including Israel, Saudi Arabia, Turkey, the U.S., Jordan, and Germany. The group is responsible for the campaign known as Operation Wilted Tulip.'),
('G0132','CostaRicto','','CostaRicto is a suspected hacker-for-hire cyber espionage campaign that has targeted multiple industries worldwide since at least 2019. CostaRictos targets, a large portion of which are financial institutions, are scattered across Europe, the Americas, Asia, Australia, and Africa, with a large concentration in South Asia.'),
('G0070','Dark Caracal','','Dark Caracal is threat group that has been attributed to the Lebanese General Directorate of General Security (GDGS) and has operated since at least 2012.'),
('G0012','Darkhotel','DUBNIUM','Darkhotel is a suspected South Korean threat group that has targeted victims primarily in East Asia since at least 2004. The groups name is based on cyber espionage operations conducted via hotel Internet networks against traveling executives and other select guests. Darkhotel has also conducted spearphishing campaigns and infected victims through peer-to-peer and file sharing networks.'),
('G0079','DarkHydrus','','DarkHydrus is a threat group that has targeted government agencies and educational institutions in the Middle East since at least 2016. The group heavily leverages open-source tools and custom payloads for carrying out attacks.'),
('G0105','DarkVishnya','','DarkVishnya is a financially motivated threat actor targeting financial institutions in Eastern Europe. In 2017-2018 the group attacked at least 8 banks in this region.'),
('G0009','Deep Panda','Shell Crew, WebMasters, KungFu Kittens, PinkPanther, Black Vine','Deep Panda is a suspected Chinese threat group known to target many industries, including government, defense, financial, and telecommunications. The intrusion into healthcare company Anthem has been attributed to Deep Panda. This group is also known as Shell Crew, WebMasters, KungFu Kittens, and PinkPanther. Deep Panda also appears to be known as Black Vine based on the attribution of both group names to the Anthem intrusion. Some analysts track Deep Panda and APT19 as the same group, but it is unclear from open source information if the groups are the same.'),
('G0035','Dragonfly','TG-4192, Crouching Yeti, IRON LIBERTY, Energetic Bear','Dragonfly is a cyber espionage group that has been active since at least 2011. They initially targeted defense and aviation companies but shifted to focus to include the energy sector in early 2013. They have also targeted companies related to industrial control systems. A similar group emerged in 2015 and was identified by Symantec as Dragonfly 2.0. There is debate over the extent of the overlap between Dragonfly and Dragonfly 2.0, but there is sufficient evidence to lead to these being tracked as two separate groups.'),
('G0074','Dragonfly 2.0','IRON LIBERTY, DYMALLOY, Berserk Bear','Dragonfly 2.0 is a suspected Russian group that has targeted government entities and multiple U.S. critical infrastructure sectors since at least December 2015. There is debate over the extent of overlap between Dragonfly 2.0 and Dragonfly, but there is sufficient evidence to lead to these being tracked as two separate groups.'),
('G0017','DragonOK','','DragonOK is a threat group that has targeted Japanese organizations with phishing emails. Due to overlapping TTPs, including similar custom tools, DragonOK is thought to have a direct or indirect relationship with the threat group Moafee. It is known to use a variety of malware, including Sysget/HelloBridge, PlugX, PoisonIvy, FormerFirstRat, NFlog, and NewCT.'),
('G0031','Dust Storm','','Dust Storm is a threat group that has targeted multiple industries in Japan, South Korea, the United States, Europe, and several Southeast Asian countries.'),
('G0066','Elderwood','Elderwood Gang, Beijing Group, Sneaky Panda','Elderwood is a suspected Chinese cyber espionage group that was reportedly responsible for the 2009 Google intrusion known as Operation Aurora. The group has targeted defense organizations, supply chain manufacturers, human rights and nongovernmental organizations (NGOs), and IT service providers.'),
('G0020','Equation','','Equation is a sophisticated threat group that employs multiple remote access tools. The group is known to use zero-day exploits and has developed the capability to overwrite the firmware of hard disk drives.'),
('G0120','Evilnum','','Evilnum is a financially motivated threat group that has been active since at least 2018.'),
('G0137','Ferocious Kitten','','Ferocious Kitten is a threat group that has primarily targeted Persian-speaking individuals in Iran since at least 2015.'),
('G0051','FIN10','','FIN10 is a financially motivated threat group that has targeted organizations in North America since at least 2013 through 2016. The group uses stolen data exfiltrated from victims to extort organizations.'),
('G0085','FIN4','','FIN4 is a financially-motivated threat group that has targeted confidential information related to the public financial market, particularly regarding healthcare and pharmaceutical companies, since at least 2013. FIN4 is unique in that they do not infect victims with typical persistent malware, but rather they focus on capturing credentials authorized to access email and other non-public correspondence.'),
('G0053','FIN5','','FIN5 is a financially motivated threat group that has targeted personally identifiable information and payment card information. The group has been active since at least 2008 and has targeted the restaurant, gaming, and hotel industries. The group is made up of actors who likely speak Russian.'),
('G0037','FIN6','Magecart Group 6, SKELETON SPIDER, ITG08','FIN6 is a cyber crime group that has stolen payment card data and sold it for profit on underground marketplaces. This group has aggressively targeted and compromised point of sale (PoS) systems in the hospitality and retail sectors.'),
('G0046','FIN7','GOLD NIAGARA, ITG14, Carbon Spider','FIN7 is a financially-motivated threat group that has been active since 2013 primarily targeting the U.S. retail, restaurant, and hospitality sectors, often using point-of-sale malware. A portion of FIN7 was run out of a front company called Combi Security. Since 2020 FIN7 shifted operations to a big game hunting (BGH) approach including use of REvil ransomware and their own Ransomware as a Service (RaaS), Darkside. FIN7 may be linked to the Carbanak Group, but there appears to be several groups using Carbanak malware and are therefore tracked separately.'),
('G0061','FIN8','','FIN8 is a financially motivated threat group known to launch tailored spearphishing campaigns targeting the retail, restaurant, and hospitality industries.'),
('G0117','Fox Kitten','UNC757, PIONEER KITTEN, Parisite','Fox Kitten is threat actor with a suspected nexus to the Iranian government that has been active since at least 2017 against entities in the Middle East, North Africa, Europe, Australia, and North America. Fox Kitten has targeted multiple industrial verticals including oil and gas, technology, government, defense, healthcare, manufacturing, and engineering.'),
('G0101','Frankenstein','','Frankenstein is a campaign carried out between January and April 2019 by unknown threat actors. The campaign name comes from the actors ability to piece together several unrelated components.'),
('G0093','GALLIUM','Operation Soft Cell','GALLIUM is a group that has been active since at least 2012, primarily targeting high-profile telecommunications networks. GALLIUM has been identified in some reporting as likely a Chinese state-sponsored group, based in part on tools used and TTPs commonly associated with Chinese threat actors.'),
('G0084','Gallmaker','','Gallmaker is a cyberespionage group that has targeted victims in the Middle East and has been active since at least December 2017. The group has mainly targeted victims in the defense, military, and government sectors.'),
('G0047','Gamaredon Group','','Gamaredon Group is a threat group that has been active since at least 2013 and has targeted individuals likely involved in the Ukrainian government. The name Gamaredon Group comes from a misspelling of the word Armageddon, which was detected in the adversarys early campaigns.'),
('G0036','GCMAN','','GCMAN is a threat group that focuses on targeting banks for the purpose of transferring money to e-currency services.'),
('G0115','GOLD SOUTHFIELD','','GOLD SOUTHFIELD is a financially motivated threat group active since at least 2019 that operates the REvil Ransomware-as-a Service (RaaS). GOLD SOUTHFIELD provides backend infrastructure for affiliates recruited on underground forums to perpetrate high value deployments.'),
('G0078','Gorgon Group','','Gorgon Group is a threat group consisting of members who are suspected to be Pakistan-based or have other connections to Pakistan. The group has performed a mix of criminal and targeted attacks, including campaigns against government organizations in the United Kingdom, Spain, Russia, and the United States.'),
('G0043','Group5','','Group5 is a threat group with a suspected Iranian nexus, though this attribution is not definite. The group has targeted individuals connected to the Syrian opposition via spearphishing and watering holes, normally using Syrian and Iranian themes. Group5 has used two commonly available remote access tools (RATs), njRAT and NanoCore, as well as an Android RAT, DroidJack.'),
('G0125','HAFNIUM','Operation Exchange Marauder','HAFNIUM is a likely state-sponsored cyber espionage group operating out of China that has been active since at least January 2021. HAFNIUM primarily targets entities in the US across a number of industry sectors, including infectious disease researchers, law firms, higher education institutions, defense contractors, policy think tanks, and NGOs.'),
('G0126','Higaisa','','Higaisa is a threat group suspected to have South Korean origins. Higaisa has targeted government, public, and trade organizations in North Korea; however, they have also carried out attacks in China, Japan, Russia, Poland, and other nations. Higaisa was first disclosed in early 2019 but is assessed to have operated as early as 2009.'),
('G0072','Honeybee','','Honeybee is a campaign led by an unknown actor that targets humanitarian aid organizations and has been active in Vietnam, Singapore, Argentina, Japan, Indonesia, and Canada. It has been an active operation since August of 2017 and as recently as February 2018.'),
('G0100','Inception','Inception Framework, Cloud Atlas','Inception is a cyber espionage group active since at least 2014. The group has targeted multiple industries and governmental entities primarily in Russia, but has also been active in the United States and throughout Europe, Asia, Africa, and the Middle East.'),
('G0136','IndigoZebra','','IndigoZebra is a suspected Chinese cyber espionage group that has been targeting Central Asian governments since at least 2014.'),
('G0119','Indrik Spider','Evil Corp','Indrik Spider is a Russia-based cybercriminal group that as been active since at least 2014. Indrik Spider initially started with the Dridex banking Trojan, and then by 2017 they began running ransomware operations using BitPaymer, WastedLocker, and Hades ransomware.'),
('G0004','Ke3chang','APT15, Mirage, Vixen Panda, GREF, Playful Dragon, RoyalAPT','Ke3chang is a threat group attributed to actors operating out of China. Ke3chang has targeted several industries, including oil, government, military, and more.'),
('G0094','Kimsuky','STOLEN PENCIL, Thallium, Black Banshee, Velvet Chollima','Kimsuky is a North Korea-based cyber espionage group that has been active since at least 2012. The group initially focused on targeting South Korean government entities, think tanks, and individuals identified as experts in various fields, and expanded its operations to include the United States, Russia, Europe, and the UN. Kimsuky has focused its intelligence collection activities on foreign policy and national security issues related to the Korean peninsula, nuclear policy, and sanctions. Kimsuky was assessed to be responsible for the 2014 Korea Hydro & Nuclear Power Co. compromise; other notable campaigns include Operation STOLEN PENCIL (2018), Operation Kabar Cobra (2019), and Operation Smoke Screen (2019). North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups.'),
('G0032','Lazarus Group','HIDDEN COBRA, Guardians of Peace, ZINC, NICKEL ACADEMY','Lazarus Group is a North Korean state-sponsored cyber threat group that has been attributed to the Reconnaissance General Bureau. The group has been active since at least 2009 and was reportedly responsible for the November 2014 destructive wiper attack against Sony Pictures Entertainment as part of a campaign named Operation Blockbuster by Novetta. Malware used by Lazarus Group correlates to other reported campaigns, including Operation Flame, Operation 1Mission, Operation Troy, DarkSeoul, and Ten Days of Rain. North Korean group definitions are known to have significant overlap, and some security researchers report all North Korean state-sponsored cyber activity under the name Lazarus Group instead of tracking clusters or subgroups, such as Andariel, APT37, APT38, and Kimsuky.'),
('G0077','Leafminer','Raspite','Leafminer is an Iranian threat group that has targeted government organizations and business entities in the Middle East since at least early 2017.'),
('G0065','Leviathan','MUDCARP, Kryptonite Panda, Gadolinium, BRONZE MOHAWK, TEMP.Jumper, APT40, TEMP.Periscope','Leviathan is a Chinese state-sponsored cyber espionage group that has been attributed to the Ministry of State Securitys (MSS) Hainan State Security Department and an affiliated front company. Active since at least 2009, Leviathan has targeted the following sectors: academia, aerospace/aviation, biomedical, defense industrial base, government, healthcare, manufacturing, maritime, and transportation across the US, Canada, Europe, the Middle East, and Southeast Asia.'),
('G0030','Lotus Blossom','DRAGONFISH, Spring Dragon','Lotus Blossom is a threat group that has targeted government and military organizations in Southeast Asia.'),
('G0095','Machete','APT-C-43, El Machete','Machete is a suspected Spanish-speaking cyber espionage group that has been active since at least 2010. It has primarily focused its operations within Latin America, with a particular emphasis on Venezuela, but also in the US, Europe, Russia, and parts of Asia. Machete generally targets high-profile organizations such as government institutions, intelligence services, and military units, as well as telecommunications and power companies.'),
('G0059','Magic Hound','TA453, COBALT ILLUSION, Charming Kitten, ITG18, Phosphorus, Newscaster, APT35','Magic Hound is an Iranian-sponsored threat group that conducts long term, resource-intensive cyber espionage operations, likely on behalf of the Islamic Revolutionary Guard Corps. They have targeted U.S. and Middle Eastern government and military personnel, academics, journalists, and organizations such as the World Health Organization (WHO), via complex social engineering campaigns since at least 2014.'),
('G0045','menuPass','Cicada, POTASSIUM, Stone Panda, APT10, Red Apollo, CVNX, HOGFISH','menuPass is a threat group that has been active since at least 2006. Individual members of menuPass are known to have acted in association with the Chinese Ministry of State Securitys (MSS) Tianjin State Security Bureau and worked for the Huaying Haitai Science and Technology Development Company. menuPass has targeted healthcare, defense, aerospace, finance, maritime, biotechnology, energy, and government sectors globally, with an emphasis on Japanese organizations. In 2016 and 2017, the group is known to have targeted managed IT service providers (MSPs), manufacturing and mining companies, and a university.'),
('G0002','Moafee','','Moafee is a threat group that appears to operate from the Guandong Province of China. Due to overlapping TTPs, including similar custom tools, Moafee is thought to have a direct or indirect relationship with the threat group DragonOK.'),
('G0103','Mofang','','Mofang is a likely China-based cyber espionage group, named for its frequent practice of imitating a victims infrastructure. This adversary has been observed since at least May 2012 conducting focused attacks against government and critical infrastructure in Myanmar, as well as several other countries and sectors including military, automobile, and weapons industries.'),
('G0021','Molerats','Operation Molerats, Gaza Cybergang','Molerats is an Arabic-speaking, politically-motivated threat group that has been operating since 2012. The groups victims have primarily been in the Middle East, Europe, and the United States.'),
('G0069','MuddyWater','Earth Vetala , MERCURY, Static Kitten, Seedworm, TEMP.Zagros','MuddyWater is an Iranian threat group that has primarily targeted Middle Eastern nations, and has also targeted European and North American nations. The groups victims are mainly in the telecommunications, government (IT services), and oil sectors. Activity from this group was previously linked to FIN7, but the group is believed to be a distinct group possibly motivated by espionage.'),
('G0129','Mustang Panda','TA416, RedDelta, BRONZE PRESIDENT','Mustang Panda is a China-based cyber espionage threat actor that was first observed in 2017 but may have been conducting operations since at least 2014. Mustang Panda has targeted government entities, nonprofits, religious, and other non-governmental organizations in the U.S., Germany, Mongolia, Myanmar, Pakistan, and Vietnam, among others.'),
('G0019','Naikon','','Naikon is assessed to be a state-sponsored cyber espionage group attributed to the Chinese People’s Liberation Army’s (PLA) Chengdu Military Region Second Technical Reconnaissance Bureau (Military Unit Cover Designator 78020). Active since at least 2010, Naikon has primarily conducted operations against government, military, and civil organizations in Southeast Asia, as well as against international bodies such as the United Nations Development Programme (UNDP) and the Association of Southeast Asian Nations (ASEAN). While Naikon shares some characteristics with APT30, the two groups do not appear to be exact matches.'),
('G0055','NEODYMIUM','','NEODYMIUM is an activity group that conducted a campaign in May 2016 and has heavily targeted Turkish victims. The group has demonstrated similarity to another activity group called PROMETHIUM due to overlapping victim and campaign characteristics. NEODYMIUM is reportedly associated closely with BlackOasis operations, but evidence that the group names are aliases has not been identified.'),
('G0014','Night Dragon','','Night Dragon is a campaign name for activity involving a threat group that has conducted activity originating primarily in China.'),
('G0133','Nomadic Octopus','DustSquad','Nomadic Octopus is a Russian-speaking cyberespionage threat group that has primarily targeted Central Asia, including local governments, diplomatic missions, and individuals, since at least 2014. Nomadic Octopus has been observed conducting campaigns involving Android and Windows malware, mainly using the Delphi programming language, and building custom variants.'),
('G0049','OilRig','COBALT GYPSY, IRN2, HELIX KITTEN, APT34','OilRig is a suspected Iranian threat group that has targeted Middle Eastern and international victims since at least 2014. The group has targeted a variety of sectors, including financial, government, energy, chemical, and telecommunications. It appears the group carries out supply chain attacks, leveraging the trust relationship between organizations to attack their primary targets. FireEye assesses that the group works on behalf of the Iranian government based on infrastructure details that contain references to Iran, use of Iranian infrastructure, and targeting that aligns with nation-state interests.'),
('G0116','Operation Wocao','','Operation Wocao described activities carried out by a China-based cyber espionage adversary. Operation Wocao targeted entities within the government, managed service providers, energy, health care, and technology sectors across several countries, including China, France, Germany, the United Kingdom, and the United States. Operation Wocao used similar TTPs and tools to APT20, suggesting a possible overlap.'),
('G0071','Orangeworm','','Orangeworm is a group that has targeted organizations in the healthcare sector in the United States, Europe, and Asia since at least 2015, likely for the purpose of corporate espionage.'),
('G0040','Patchwork','Hangover Group, Dropping Elephant, Chinastrats, MONSOON, Operation Hangover','Patchwork is a cyberespionage group that was first observed in December 2015. While the group has not been definitively attributed, circumstantial evidence suggests the group may be a pro-Indian or Indian entity. Patchwork has been seen targeting industries related to diplomatic and government agencies. Much of the code used by this group was copied and pasted from online forums. Patchwork was also seen operating spearphishing campaigns targeting U.S. think tank groups in March and April of 2018.'),
('G0011','PittyTiger','','PittyTiger is a threat group believed to operate out of China that uses multiple different types of malware to maintain command and control.'),
('G0068','PLATINUM','','PLATINUM is an activity group that has targeted victims since at least 2009. The group has focused on targets associated with governments and related organizations in South and Southeast Asia.'),
('G0033','Poseidon Group','','Poseidon Group is a Portuguese-speaking threat group that has been active since at least 2005. The group has a history of using information exfiltrated from victims to blackmail victim companies into contracting the Poseidon Group as a security firm.'),
('G0056','PROMETHIUM','StrongPity','PROMETHIUM is an activity group focused on espionage that has been active since at least 2012. The group has conducted operations globally with a heavy emphasis on Turkish targets. PROMETHIUM has demonstrated similarity to another activity group called NEODYMIUM due to overlapping victim and campaign characteristics.'),
('G0024','Putter Panda','APT2, MSUpdater','Putter Panda is a Chinese threat group that has been attributed to Unit 61486 of the 12th Bureau of the PLA’s 3rd General Staff Department (GSD).'),
('G0075','Rancor','','Rancor is a threat group that has led targeted campaigns against the South East Asia region. Rancor uses politically-motivated lures to entice victims to open malicious documents.'),
('G0106','Rocke','','Rocke is an alleged Chinese-speaking adversary whose primary objective appeared to be cryptojacking, or stealing victim system resources for the purposes of mining cryptocurrency. The name Rocke comes from the email address rocke@live.cn used to create the wallet which held collected cryptocurrency. Researchers have detected overlaps between Rocke and the Iron Cybercrime Group, though this attribution has not been confirmed.'),
('G0048','RTM','','RTM is a cybercriminal group that has been active since at least 2015 and is primarily interested in users of remote banking systems in Russia and neighboring countries. The group uses a Trojan by the same name (RTM).'),
('G0034','Sandworm Team','ELECTRUM, Telebots, IRON VIKING, BlackEnergy (Group), Quedagh, VOODOO BEAR','Sandworm Team is a destructive threat group that has been attributed to Russias General Staff Main Intelligence Directorate (GRU) Main Center for Special Technologies (GTsST) military unit 74455. This group has been active since at least 2009. In October 2020, the US indicted six GRU Unit 74455 officers associated with Sandworm Team for the following cyber operations: the 2015 and 2016 attacks against Ukrainian electrical companies and government organizations, the 2017 worldwide NotPetya attack, targeting of the 2017 French presidential campaign, the 2018 Olympic Destroyer attack against the Winter Olympic Games, the 2018 operation against the Organisation for the Prohibition of Chemical Weapons, and attacks against the country of Georgia in 2018 and 2019. Some of these were conducted with the assistance of GRU Unit 26165, which is also referred to as APT28.'),
('G0029','Scarlet Mimic','','Scarlet Mimic is a threat group that has targeted minority rights activists. This group has not been directly linked to a government source, but the groups motivations appear to overlap with those of the Chinese government. While there is some overlap between IP addresses used by Scarlet Mimic and Putter Panda, it has not been concluded that the groups are the same.'),
('G0104','Sharpshooter','','Operation Sharpshooter is the name of a cyber espionage campaign discovered in October 2018 targeting nuclear, defense, energy, and financial companies. Though overlaps between this adversary and Lazarus Group have been noted, definitive links have not been established.'),
('G0121','Sidewinder','T-APT-04, Rattlesnake','Sidewinder is a suspected Indian threat actor group that has been active since at least 2012. They have been observed targeting government, military, and business entities throughout Asia, primarily focusing on Pakistan, China, Nepal, and Afghanistan.'),
('G0091','Silence','WHISPER SPIDER','Silence is a financially motivated threat actor targeting financial institutions in different countries. The group was first seen in June 2016. Their main targets reside in Russia, Ukraine, Belarus, Azerbaijan, Poland and Kazakhstan. They compromised various banking systems, including the Russian Central Banks Automated Workstation Client, ATMs, and card processing.'),
('G0122','Silent Librarian','TA407, COBALT DICKENS','Silent Librarian is a group that has targeted research and proprietary data at universities, government agencies, and private sector companies worldwide since at least 2013. Members of Silent Librarian are known to have been affiliated with the Iran-based Mabna Institute which has conducted cyber intrusions at the behest of the government of Iran, specifically the Islamic Revolutionary Guard Corps (IRGC).'),
('G0083','SilverTerrier','','SilverTerrier is a Nigerian threat group that has been seen active since 2014. SilverTerrier mainly targets organizations in high technology, higher education, and manufacturing.'),
('G0054','Sowbug','','Sowbug is a threat group that has conducted targeted attacks against organizations in South America and Southeast Asia, particularly government entities, since at least 2015.'),
('G0038','Stealth Falcon','','Stealth Falcon is a threat group that has conducted targeted spyware attacks against Emirati journalists, activists, and dissidents since at least 2012. Circumstantial evidence suggests there could be a link between this group and the United Arab Emirates (UAE) government, but that has not been confirmed.'),
('G0041','Strider','ProjectSauron','Strider is a threat group that has been active since at least 2011 and has targeted victims in Russia, China, Sweden, Belgium, Iran, and Rwanda.'),
('G0039','Suckfly','','Suckfly is a China-based threat group that has been active since at least 2014.'),
('G0062','TA459','','TA459 is a threat group believed to operate out of China that has targeted countries including Russia, Belarus, Mongolia, and others.'),
('G0092','TA505','Hive0065','TA505 is a financially motivated threat group that has been active since at least 2014. The group is known for frequently changing malware and driving global trends in criminal malware distribution.'),
('G0127','TA551','GOLD CABIN, Shathak','TA551 is a financially-motivated threat group that has been active since at least 2018. The group has primarily targeted English, German, Italian, and Japanese speakers through email-based malware distribution campaigns.'),
('G0139','TeamTNT','','TeamTNT is a threat group that has primarily targeted cloud and containerized environments. The group as been active since at least October 2019 and has mainly focused its efforts on leveraging cloud and container resources to deploy cryptocurrency miners in victim environments.'),
('G0088','TEMP.Veles','XENOTIME','TEMP.Veles is a Russia-based threat group that has targeted critical infrastructure. The group has been observed utilizing TRITON, a malware framework designed to manipulate industrial safety systems.'),
('G0089','The White Company','','The White Company is a likely state-sponsored threat actor with advanced capabilities. From 2017 through 2018, the group led an espionage campaign called Operation Shaheen targeting government and military organizations in Pakistan.'),
('G0028','Threat Group-1314','TG-1314','Threat Group-1314 is an unattributed threat group that has used compromised credentials to log into a victims remote access infrastructure.'),
('G0027','Threat Group-3390','TG-3390, Emissary Panda, BRONZE UNION, APT27, Iron Tiger, LuckyMouse','Threat Group-3390 is a Chinese threat group that has extensively used strategic Web compromises to target victims. The group has been active since at least 2010 and has targeted organizations in the aerospace, government, defense, technology, energy, and manufacturing sectors.'),
('G0076','Thrip','','Thrip is an espionage group that has targeted satellite communications, telecoms, and defense contractor companies in the U.S. and Southeast Asia. The group uses custom malware as well as living off the land techniques.'),
('G0131','Tonto Team','Earth Akhlut, BRONZE HUNTLEY, CactusPete, Karma Panda','Tonto Team is a suspected Chinese state-sponsored cyber espionage threat group that has primarily targeted South Korea, Japan, Taiwan, and the United States since at least 2009; by 2020 they expanded operations to include other Asian as well as Eastern European countries. Tonto Team has targeted government, military, energy, mining, financial, education, healthcare, and technology organizations, including through the Heartbeat Campaign (2009-2012) and Operation Bitter Biscuit (2017).'),
('G0134','Transparent Tribe','COPPER FIELDSTONE, APT36, Mythic Leopard, ProjectM','Transparent Tribe is a suspected Pakistan-based threat group that has been active since at least 2013, primarily targeting diplomatic, defense, and research organizations in India and Afghanistan.'),
('G0081','Tropic Trooper','Pirate Panda, KeyBoy','Tropic Trooper is an unaffiliated threat group that has led targeted campaigns against targets in Taiwan, the Philippines, and Hong Kong. Tropic Trooper focuses on targeting government, healthcare, transportation, and high-tech industries and has been active since 2011.'),
('G0010','Turla','Group 88, Belugasturgeon, Waterbug, WhiteBear, VENOMOUS BEAR, Snake, Krypton','Turla is a Russian-based threat group that has infected victims in over 45 countries, spanning a range of industries including government, embassies, military, education, research and pharmaceutical companies since 2004. Heightened activity was seen in mid-2015. Turla is known for conducting watering hole and spearphishing campaigns and leveraging in-house tools and malware. Turla’s espionage platform is mainly used against Windows machines, but has also been seen used against macOS and Linux machines.'),
('G0123','Volatile Cedar','Lebanese Cedar','Volatile Cedar is a Lebanese threat group that has targeted individuals, companies, and institutions worldwide. Volatile Cedar has been operating since 2012 and is motivated by political and ideological interests.'),
('G0107','Whitefly','','Whitefly is a cyber espionage group that has been operating since at least 2017. The group has targeted organizations based mostly in Singapore across a wide variety of sectors, and is primarily interested in stealing large amounts of sensitive information. The group has been linked to an attack against Singapore’s largest public health organization, SingHealth.'),
('G0124','Windigo','','The Windigo group has been operating since at least 2011, compromising thousands of Linux and Unix servers using the Ebury SSH backdoor to create a spam botnet. Despite law enforcement intervention against the creators, Windigo operators continued updating Ebury through 2019.'),
('G0112','Windshift','Bahamut','Windshift is a threat group that has been active since at least 2017, targeting specific individuals for surveillance in government departments and critical infrastructure across the Middle East.'),
('G0044','Winnti Group','Blackfly','Winnti Group is a threat group with Chinese origins that has been active since at least 2010. The group has heavily targeted the gaming industry, but it has also expanded the scope of its targeting. Some reporting suggests a number of other groups, including Axiom, APT17, and Ke3chang, are closely linked to Winnti Group.'),
('G0090','WIRTE','','WIRTE is a threat group that has been active since at least August 2018. The group focuses on targeting Middle East defense and diplomats.'),
('G0102','Wizard Spider','UNC1878, TEMP.MixMaster, Grim Spider','Wizard Spider is a Russia-based financially motivated threat group originally known for the creation and deployment of TrickBot since at least 2016. Wizard Spider possesses a diverse arsenal of tools and has conducted ransomware campaigns against a variety of organizations, ranging from major corporations to hospitals.'),
('G0128','ZIRCONIUM','APT31','ZIRCONIUM is a threat group operating out of China, active since at least 2017, that has targeted individuals associated with the 2020 US presidential election and prominent leaders in the international affairs community.')
)
SELECT
'https://attack.mitre.org/groups/'||ID MITRE_LINK, Name, Description, Related_Groups
FROM Threat_Group_Info
WHERE LOWER(Name) LIKE LOWER('%$$Threat Actor name$$%')EXAMPLE Output
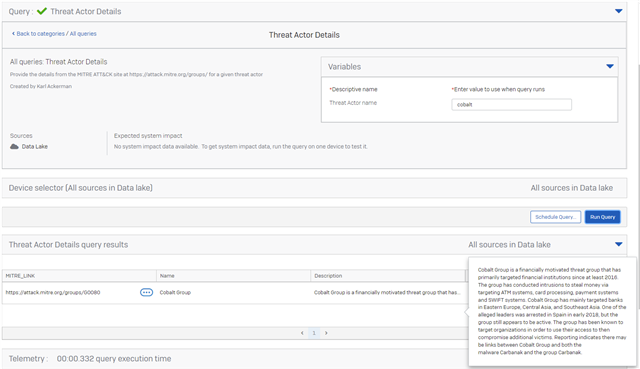
Updated disclaimer
[edited by: Qoosh at 9:45 PM (GMT -7) on 31 Mar 2023]
