Hi all,
As you will have read in the Recommended Read from last week; we released an update to Intercept X, 2.0.23. This week we will start enabling new features that are part of the update for devices that are running in the New Endpoint/Server Protection Features EAPs.
CryptoGuard 5:
A new policy option now sets the default action on detection of ransomware to terminate the process. We have kept the option to only isolate a process should you wish to keep using the setting from CryptoGuard 4.
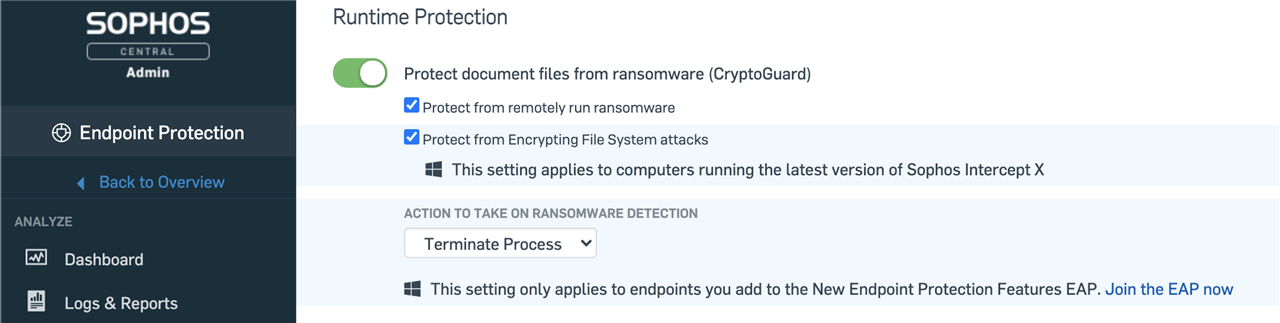
This new release is a design change in how our ransomware detection works; resulting in Sophos detecting more ransomware families and protecting more file types and sizes.
This feature is enabled for all devices in the EAP
Registry Credential Theft Protection:
An extension to our existing credential theft protection, we will now protect the SAM database when it is accessed via the registry
This feature is enabled for all devices in the EAP
Over the coming weeks we plan to enable one further mitigation which is browser MFA cookie protection.
Browser Cookie Protection:
Browser cookies have sensitive data in them, and whilst the cookies are encrypted, the encryption key is then further encrypted, attackers can abuse programs to decrypt the key and decrypt the cookies and read its content.
MITRE ATT&CK ID: T1539 – Steal Web Session Cookie
MITRE ATT&CK ID: T1550/004– Use Alternate Authentication Material: Web Session Cookie
This new mitigation protects the contents of the browser cookies by preventing malware, shell-code, loaded modules and debuggers from decrypting the AES key in order to decrypt the cookie.
Please do provide your feedback about these new protections in Intercept X.
Regards,
Stephen

